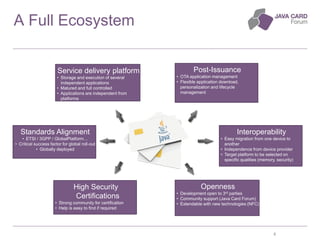
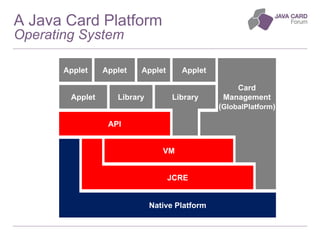
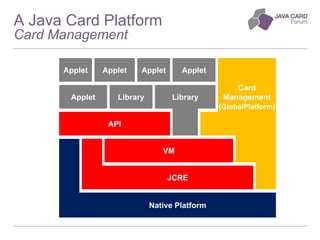
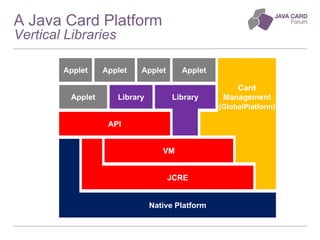
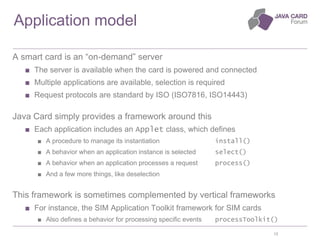
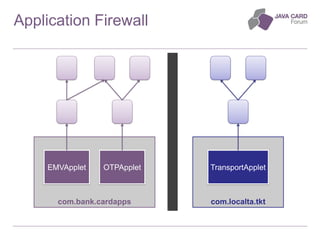
The document discusses the fundamentals of Java Card technology, emphasizing its role in providing secure applications on smart cards resistant to various types of attacks. It highlights the need for security awareness in application design while noting that Java Card simplifies certain aspects of security management. Additionally, it outlines the ecosystem, specifications, application models, and certification needs associated with Java Card platforms.