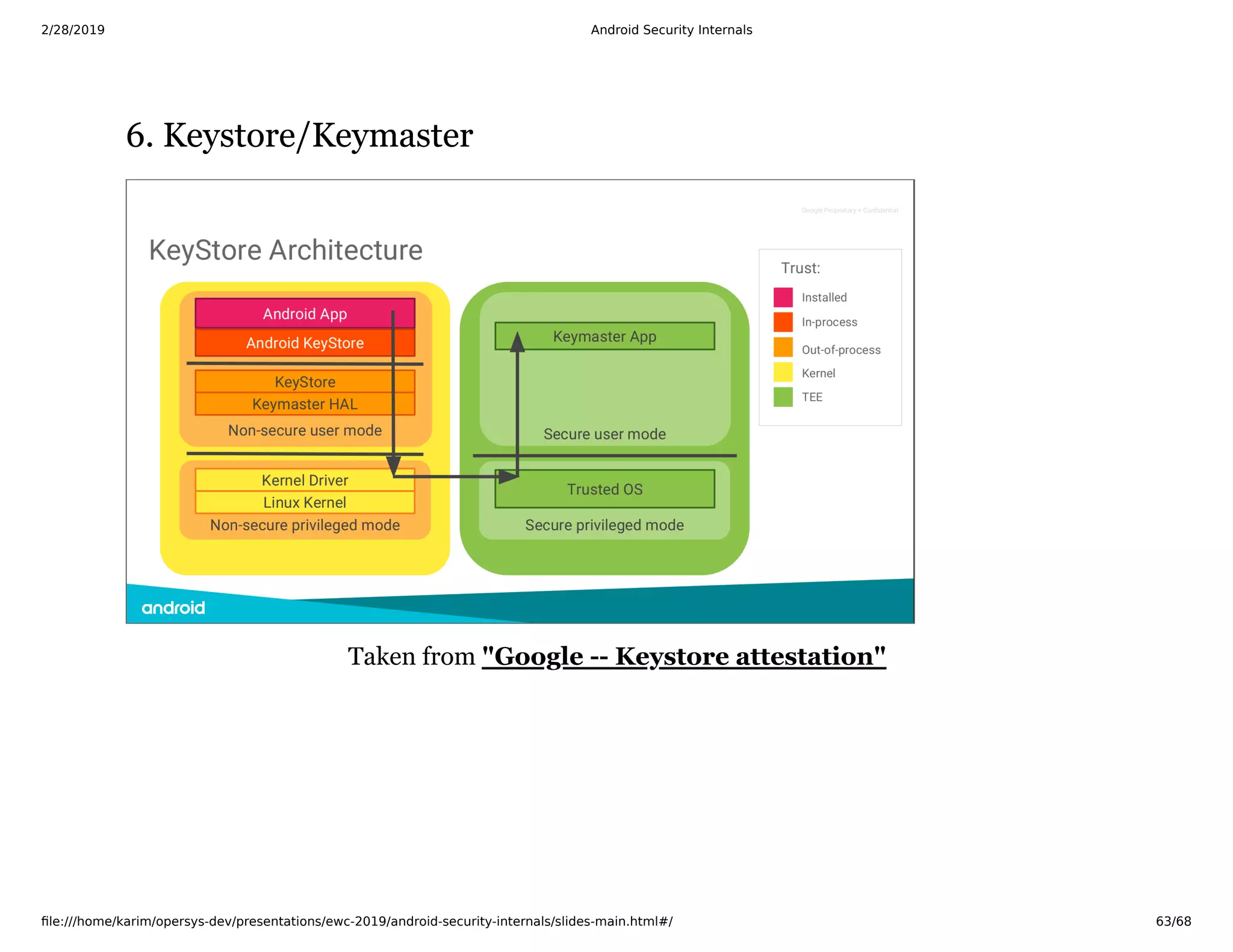
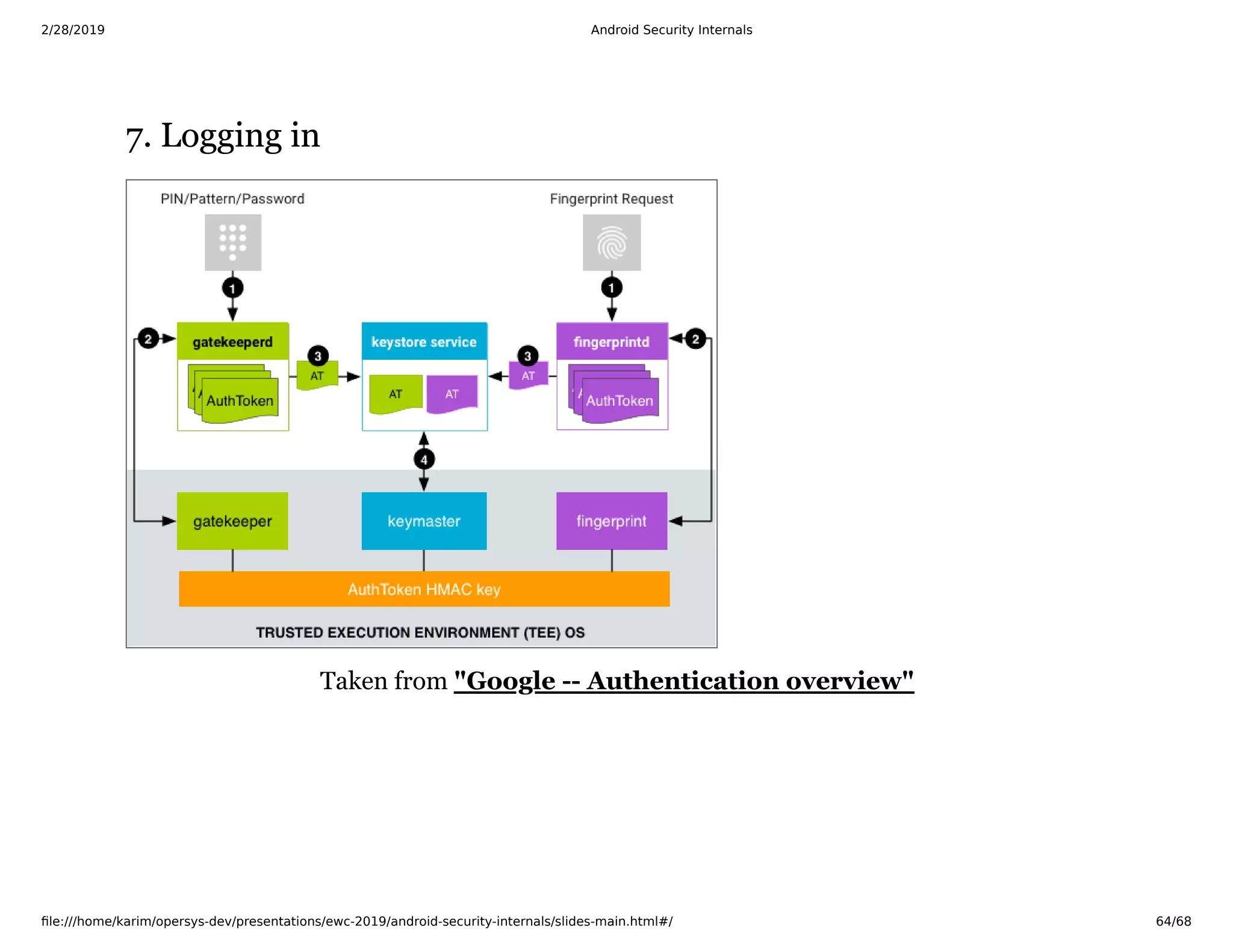
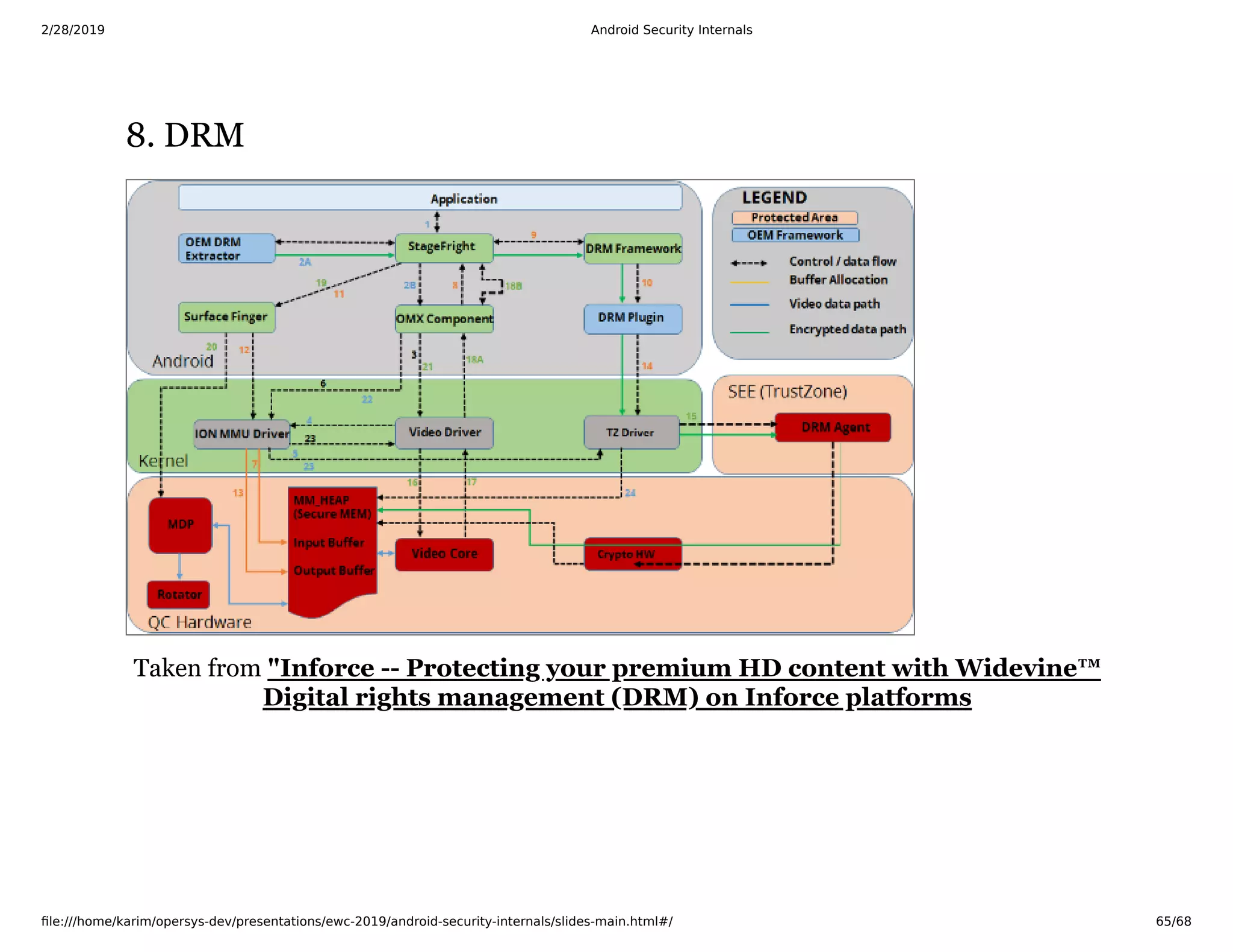
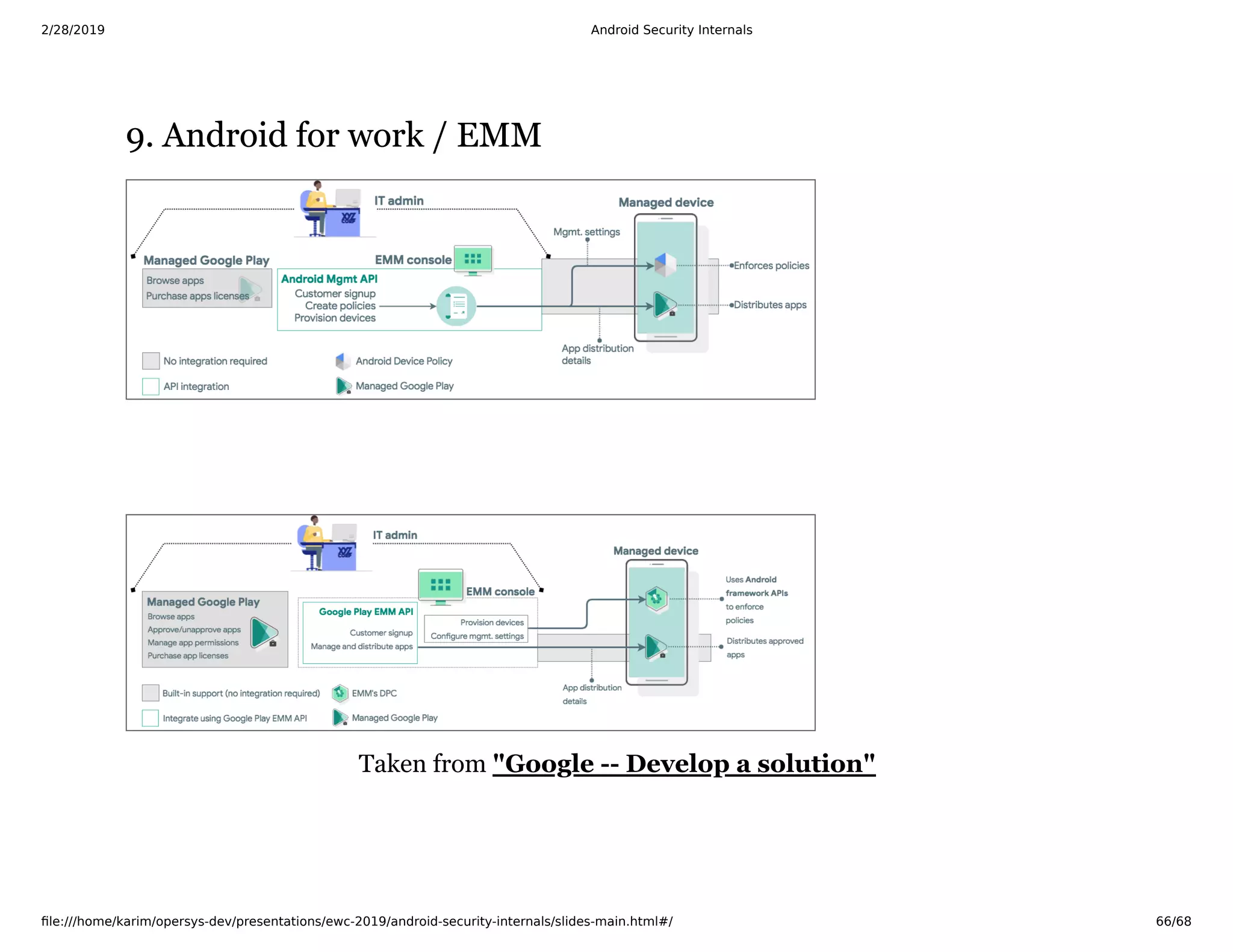
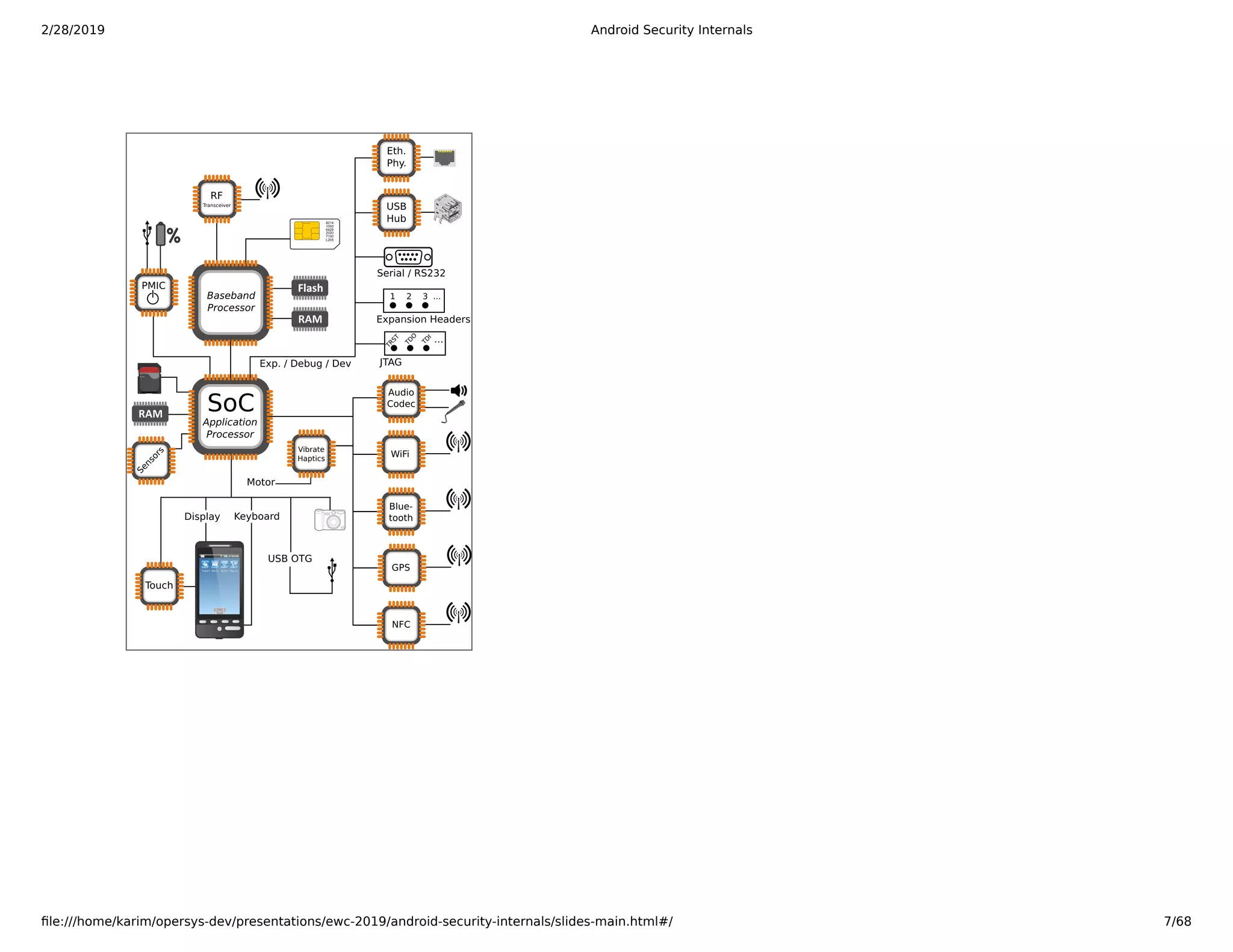
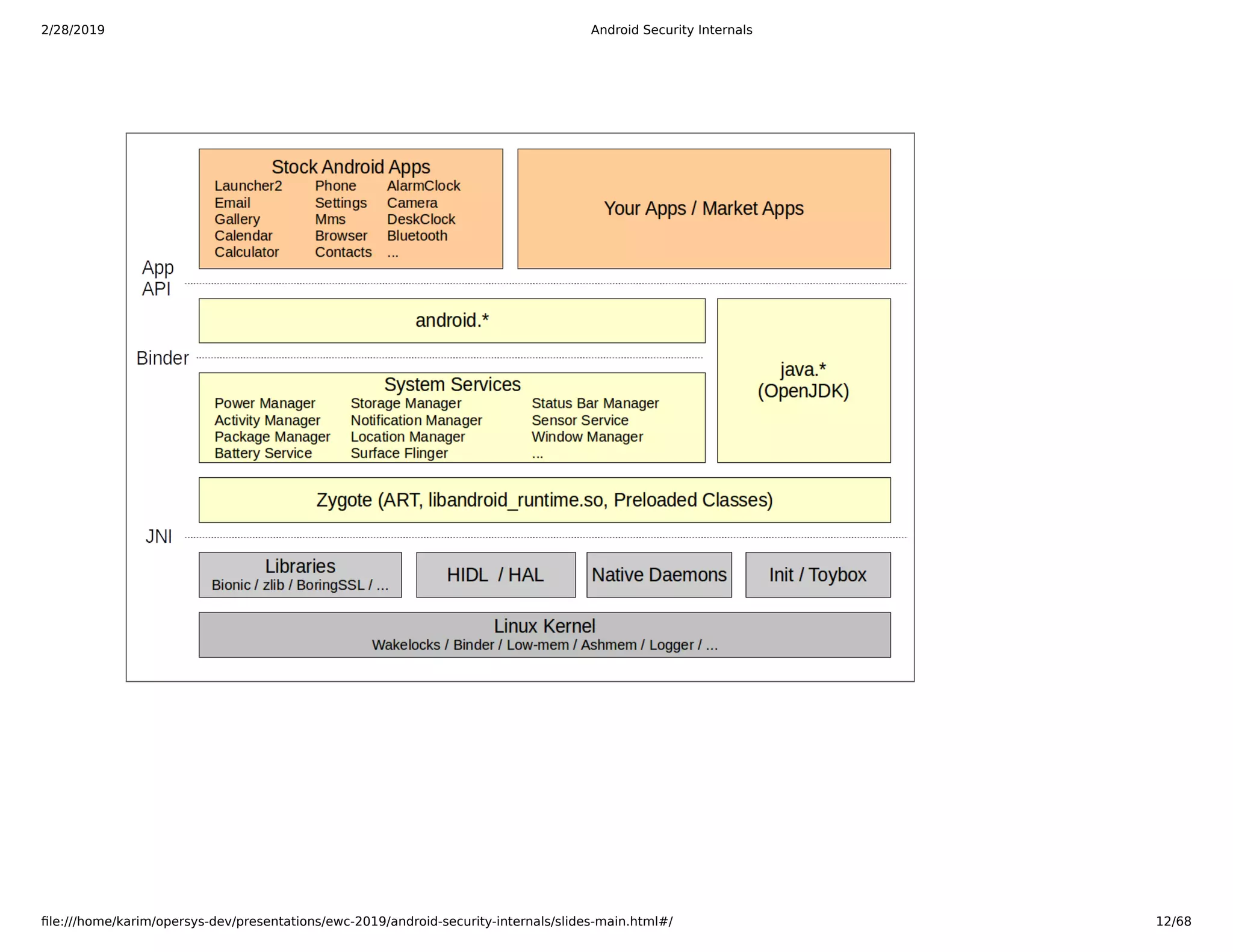
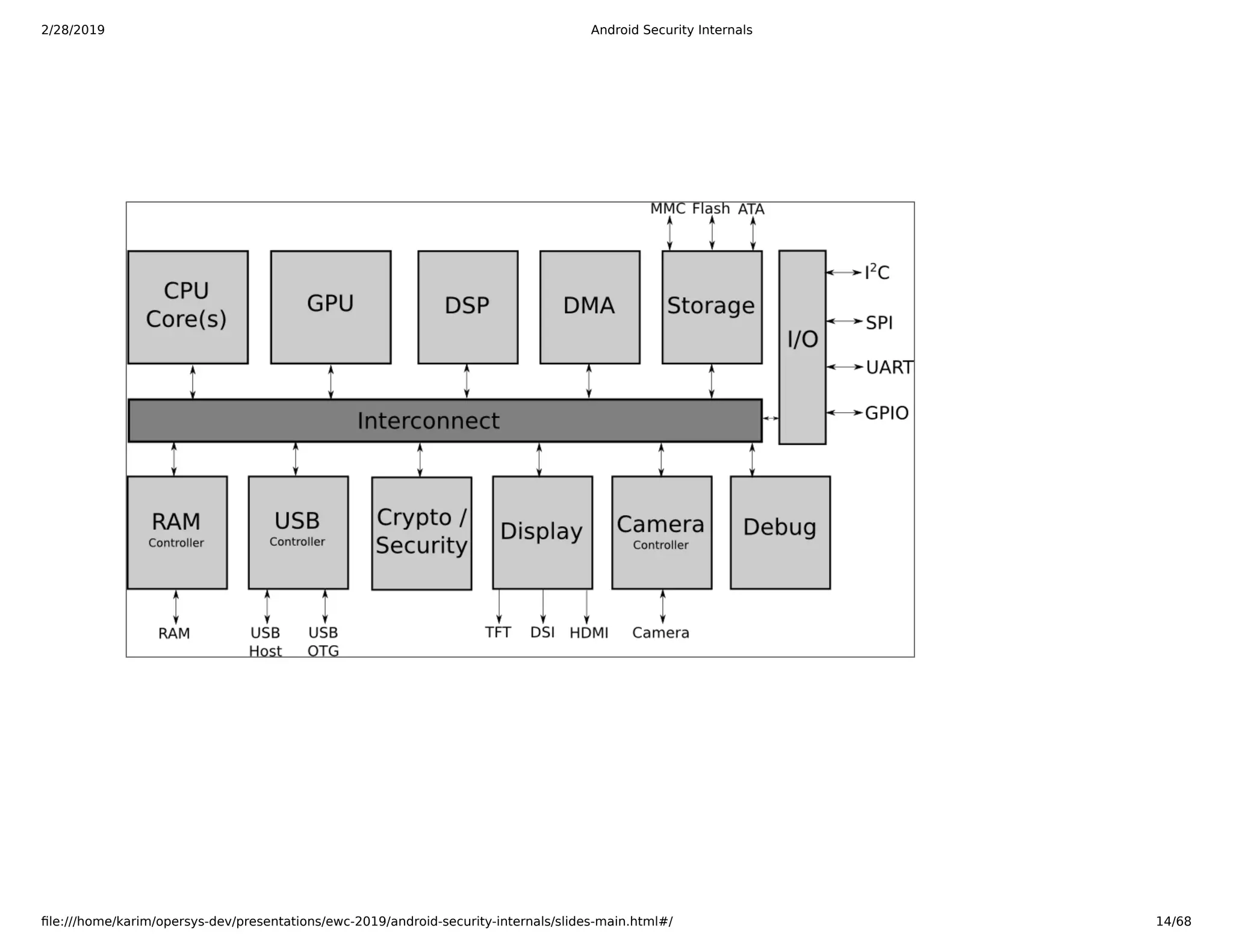
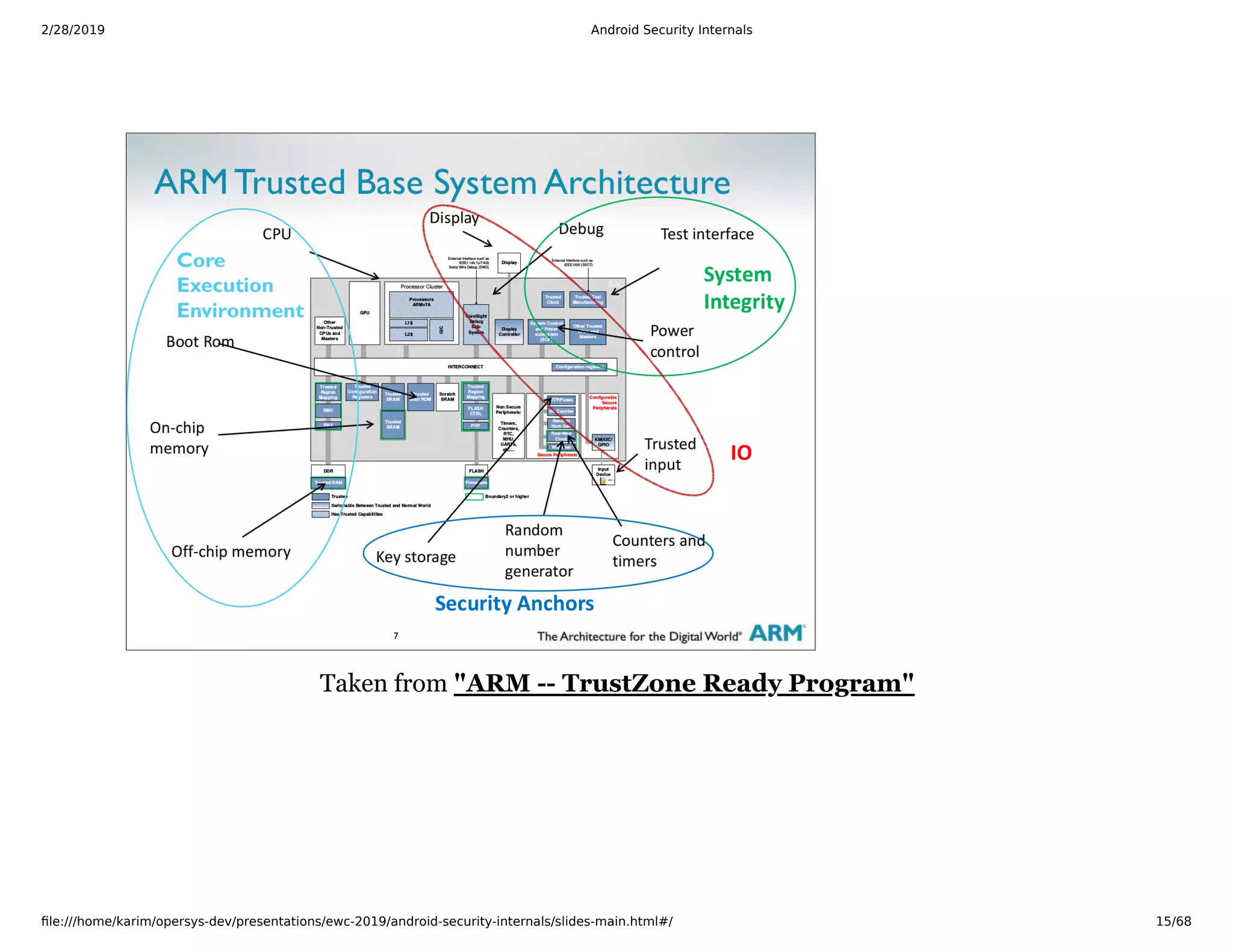
The document is a slide deck on Android security internals. It covers many topics related to Android security like the chain of trust, SoC internals, secure booting, TrustZone, the Linux kernel, SELinux, and more. The slides provide explanations, diagrams, and references to documentation from ARM and other sources to explain the low-level details of how Android security works from the hardware up.
























![2/28/2019 Android Security Internals
file:///home/karim/opersys-dev/presentations/ewc-2019/android-security-internals/slides-main.html#/ 47/68
From: Linus Torvalds
Newsgroups: fa.linux.kernel
Subject: Re: Security fix for remapping of page 0 (was [PATCH] Change
Date: Wed, 03 Jun 2009 16:48:28 UTC
Message-ID:
On Wed, 3 Jun 2009, Rik van Riel wrote:
>
> Would anybody paranoid run their system without SELinux?
You make two very fundamental mistakes.
The first is to assume that this is about "paranoid" people. Security is
_not_ about people who care deeply about security. It's about everybody.
Look at viruses and DDoS attacks - the "paranoid" people absolutely depend
on the _non_paranoid people being secure too!
The other mistake is to think that SELinux is sane, or should be the
default. It's a f*cking complex disaster, and makes performance plummet on
some things. I turn it off, and I know lots of other sane people do too.
So the !SElinux case really does need to work.
Linus](https://image.slidesharecdn.com/androidsecurityinternals-190228101714/75/Android-Security-Internals-47-2048.jpg)