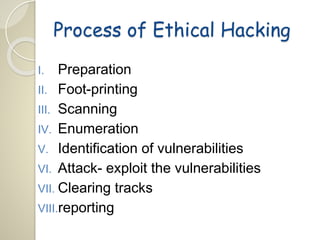
This document discusses ethical hacking and provides an overview of the topic. It defines ethical hacking as illegally accessing a computer system, but doing so for legitimate purposes such as testing security vulnerabilities. The summary outlines the 8 step process of ethical hacking: preparation, footprinting, scanning, enumeration, vulnerability identification, attack/exploitation, clearing tracks, and reporting. It also notes some of the advantages of ethical hacking like preventing security breaches and closing network holes, as well as the skills needed to become an ethical hacker like coding ability and network/security knowledge.