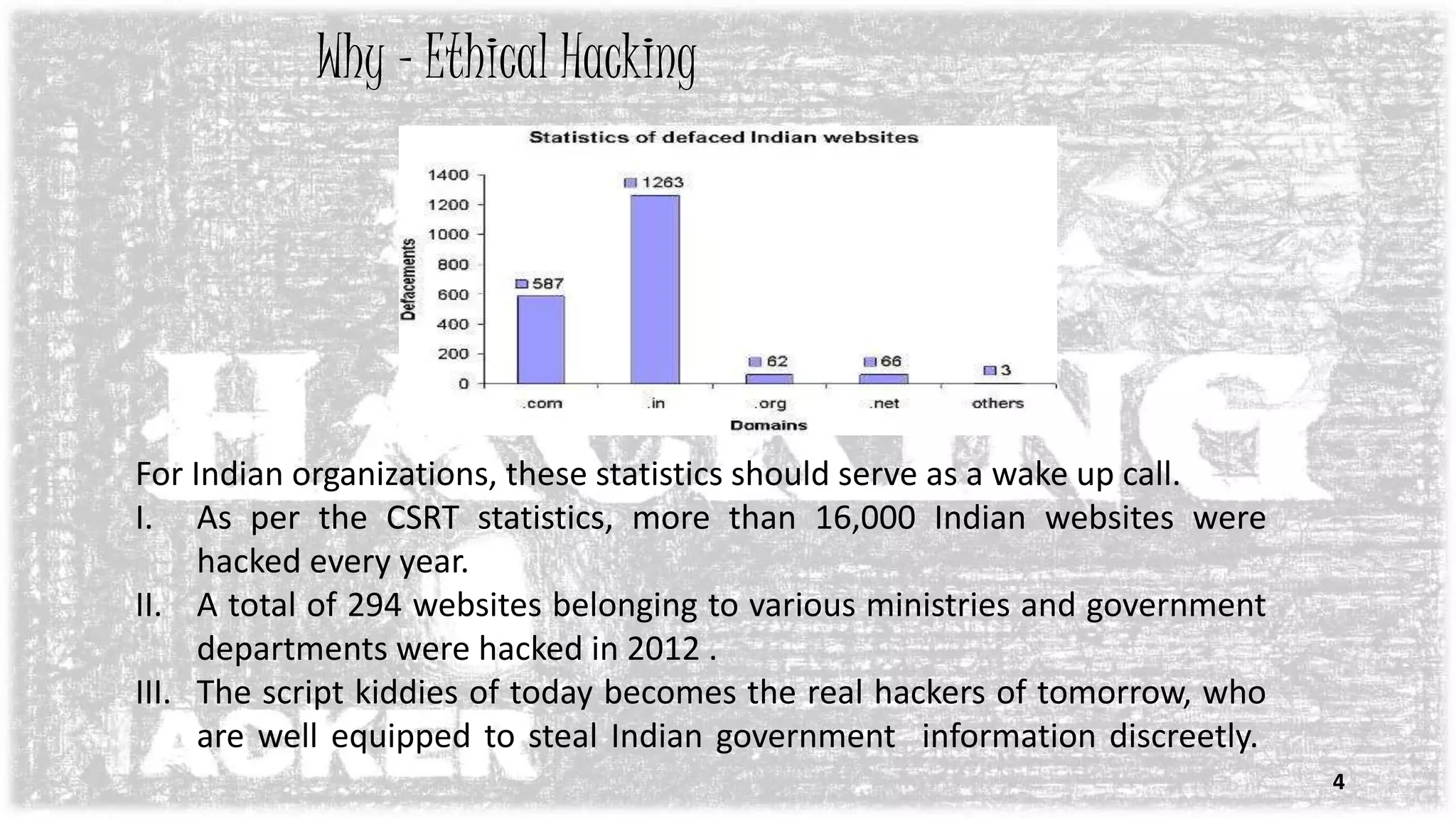
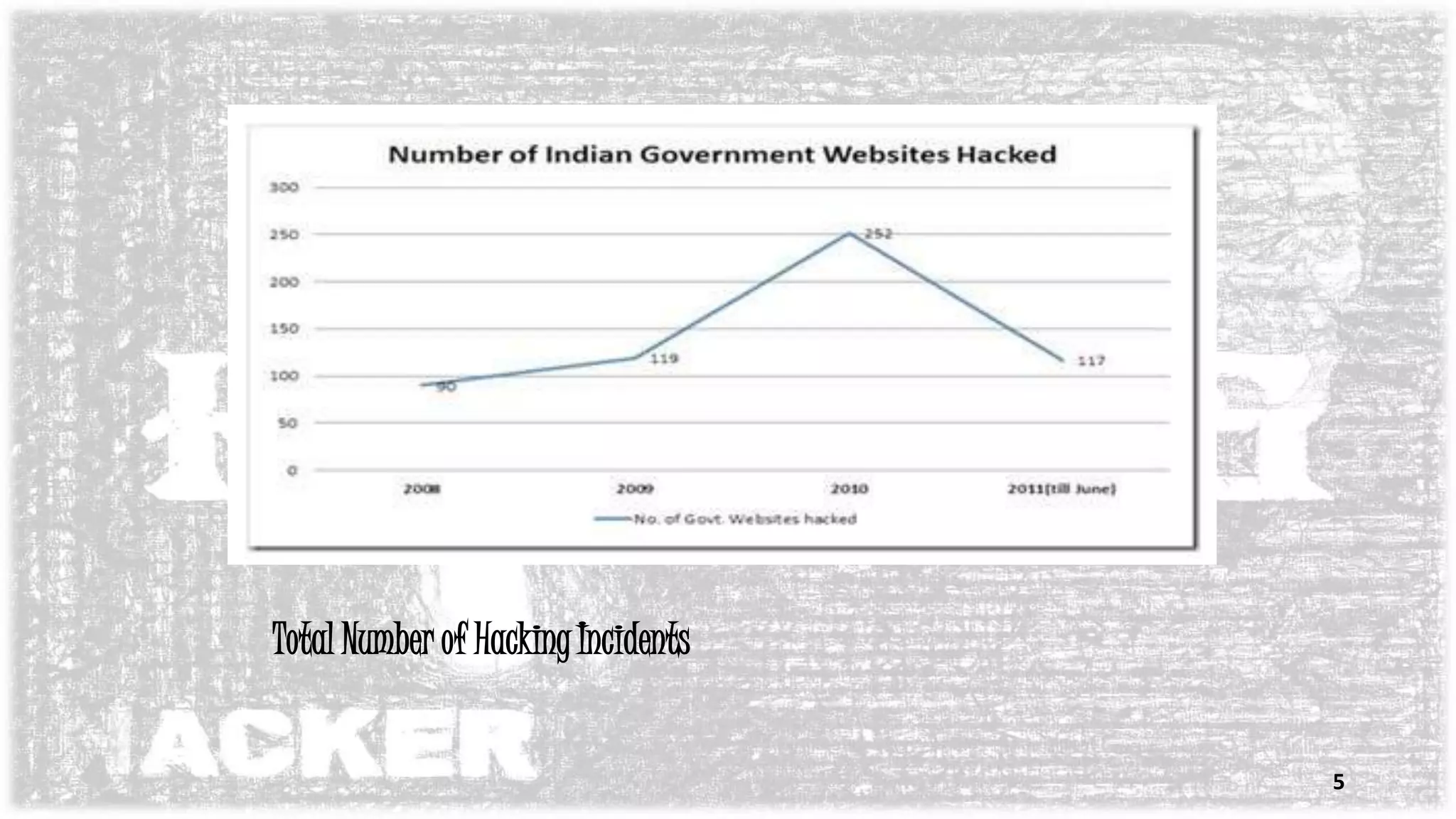
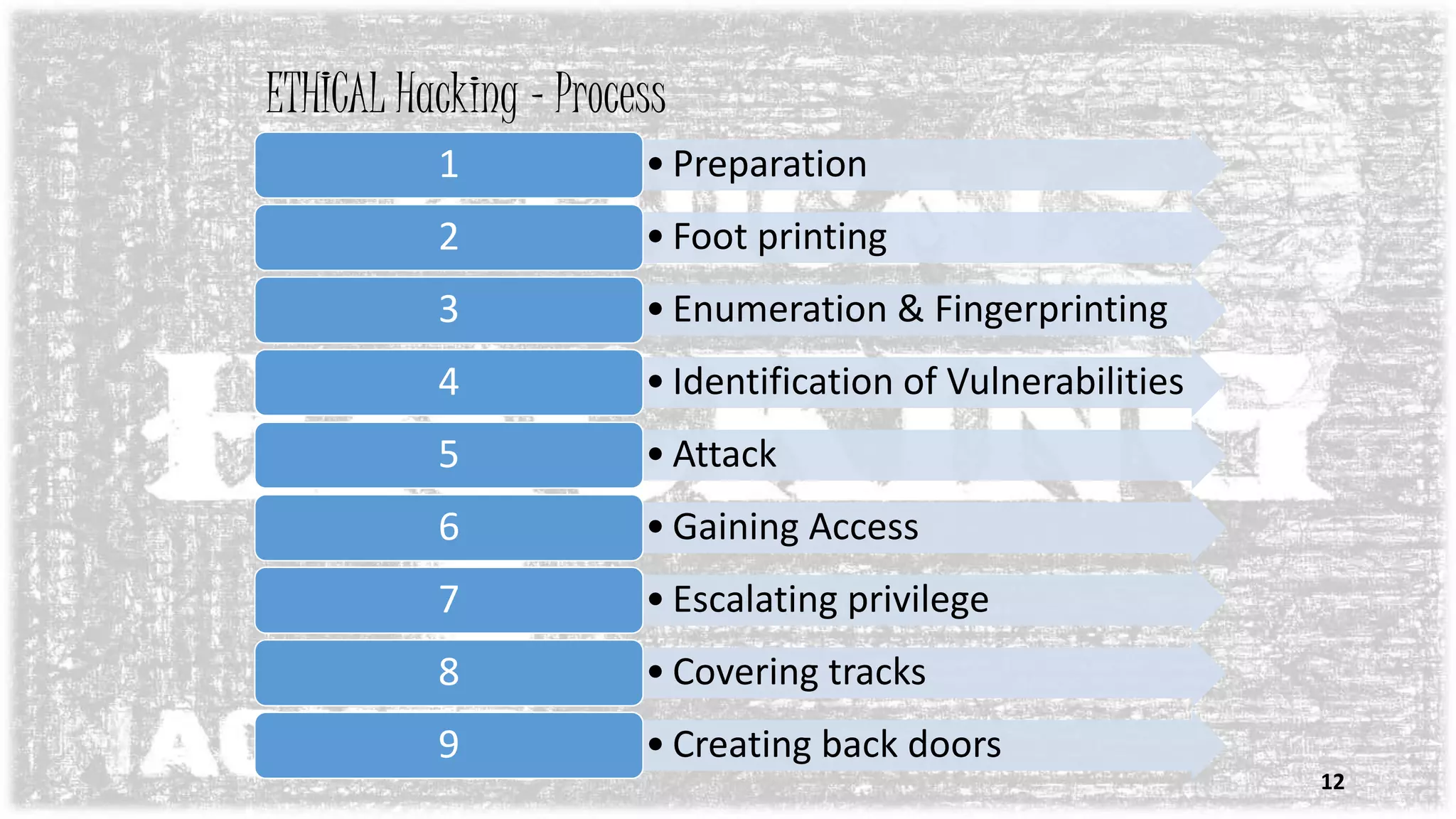
The document discusses ethical hacking, which involves authorized attempts to penetrate networks to identify security vulnerabilities. An ethical hacker has permission to hack into a system to find weaknesses that could be exploited by other hackers. The process of ethical hacking involves footprinting, scanning for vulnerabilities, exploiting them to gain access, escalating privileges, and creating backdoors while covering tracks. The goal is to strengthen security by identifying threats before malicious hackers can.