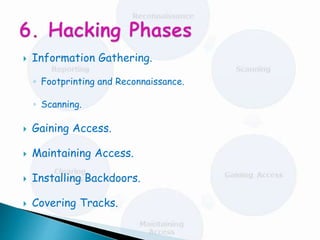
The document discusses ethical hacking and penetration testing. It defines hacking and different types of hackers such as black hat, white hat, grey hat, and script kiddies. It then explains the differences between ethical hackers and crackers. The document outlines the phases of hacking including information gathering, gaining access, maintaining access, and covering tracks. It also discusses the importance of ethical hackers for performing security testing and penetration testing to evaluate systems for vulnerabilities.