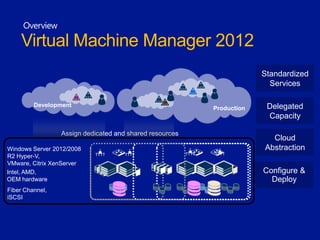
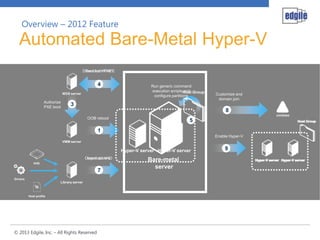
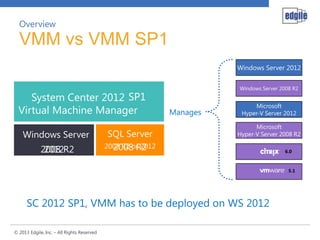
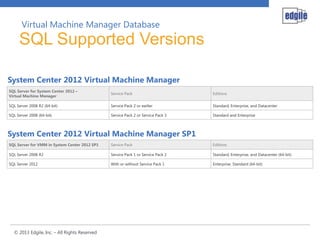
This document discusses System Center 2012 Virtual Machine Manager. It provides an overview of VMM, including its key components and benefits. It also covers the VMM database, including supported SQL Server versions and hardware requirements. High availability and clustering options for VMM are also summarized. The document concludes with an overview of next steps, such as planning design sessions.