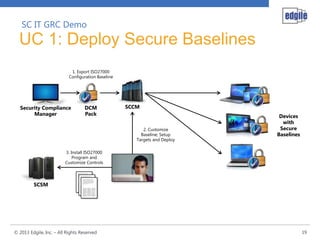
The document provides an overview of Edgile's IT Governance, Risk, and Compliance (GRC) solutions, emphasizing the importance of aligning security with business strategy and objectives. It highlights the transition from reactive to integrated GRC approaches and discusses the automation of compliance processes for greater efficiency. Additionally, it outlines the features of the System Center IT GRC management pack and its capabilities in managing and securing IT devices in line with established compliance standards.