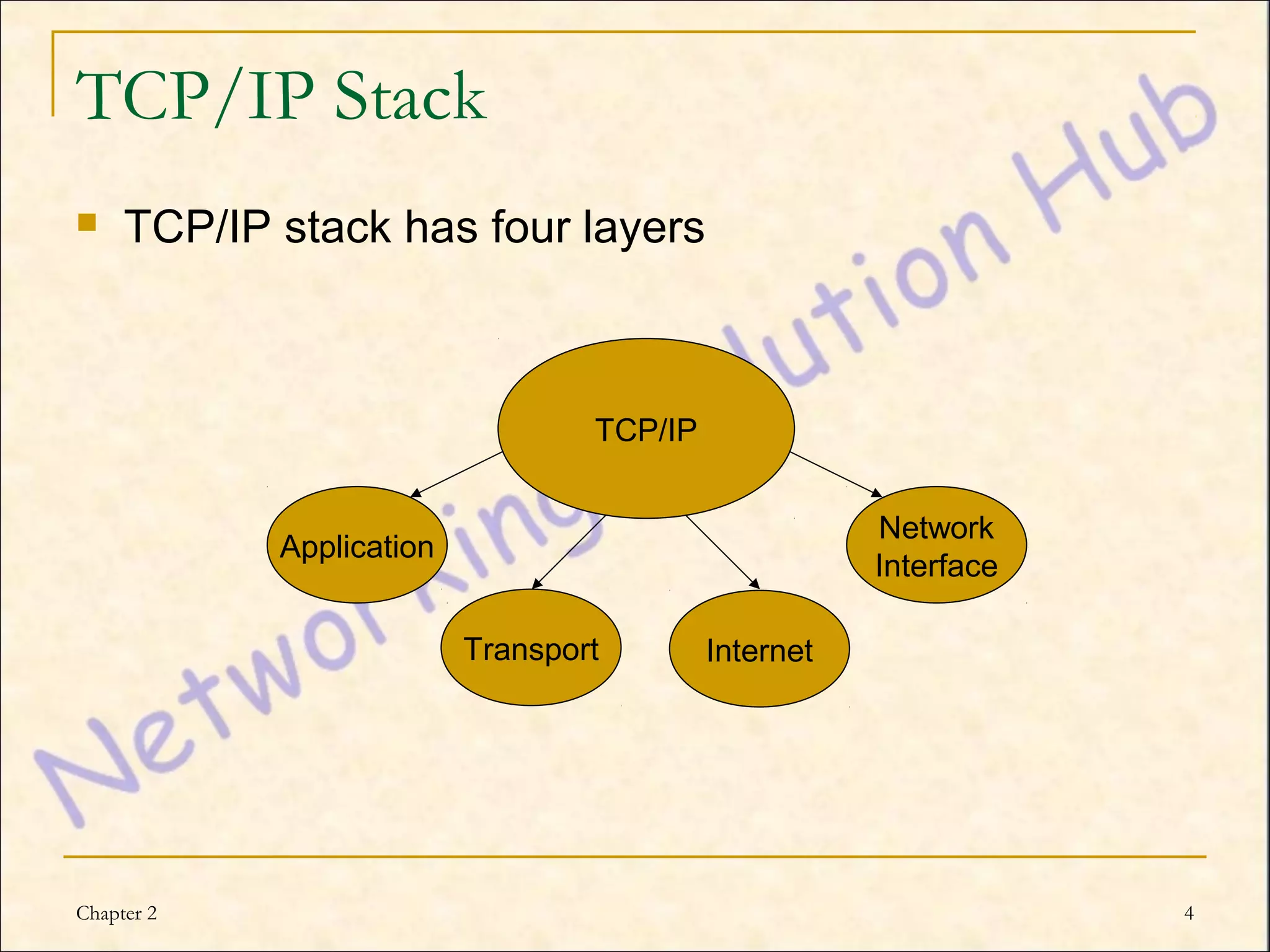
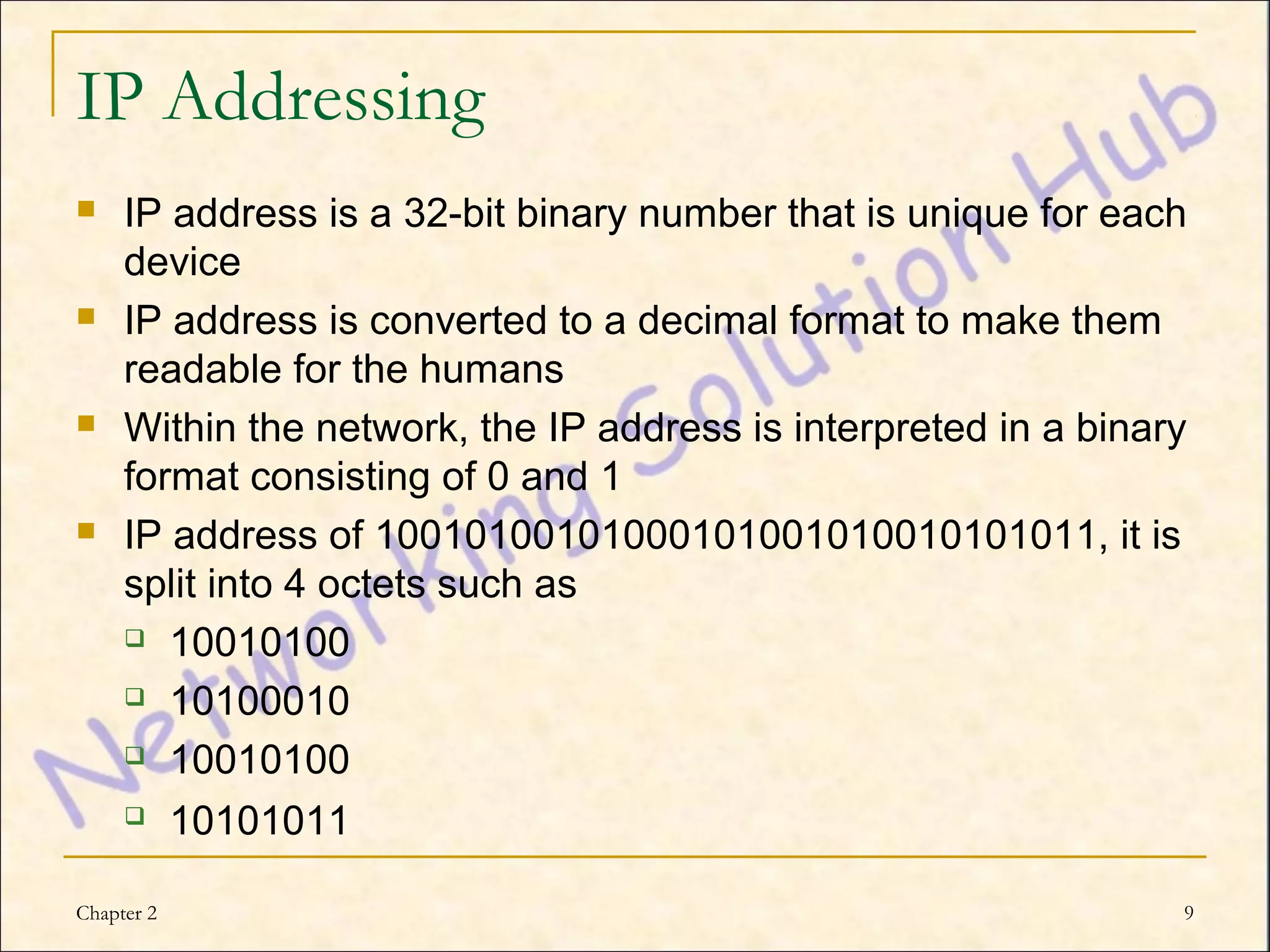
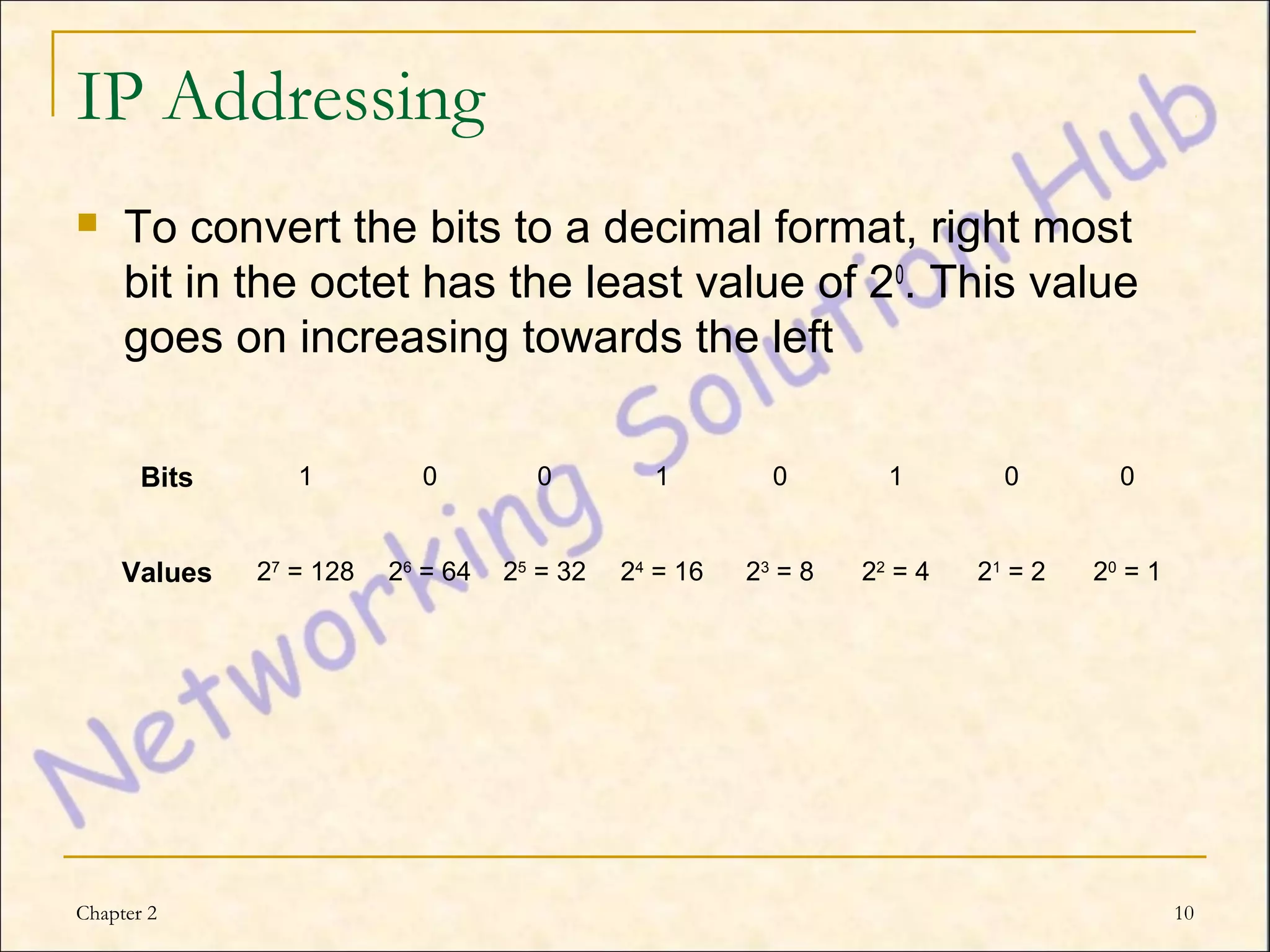
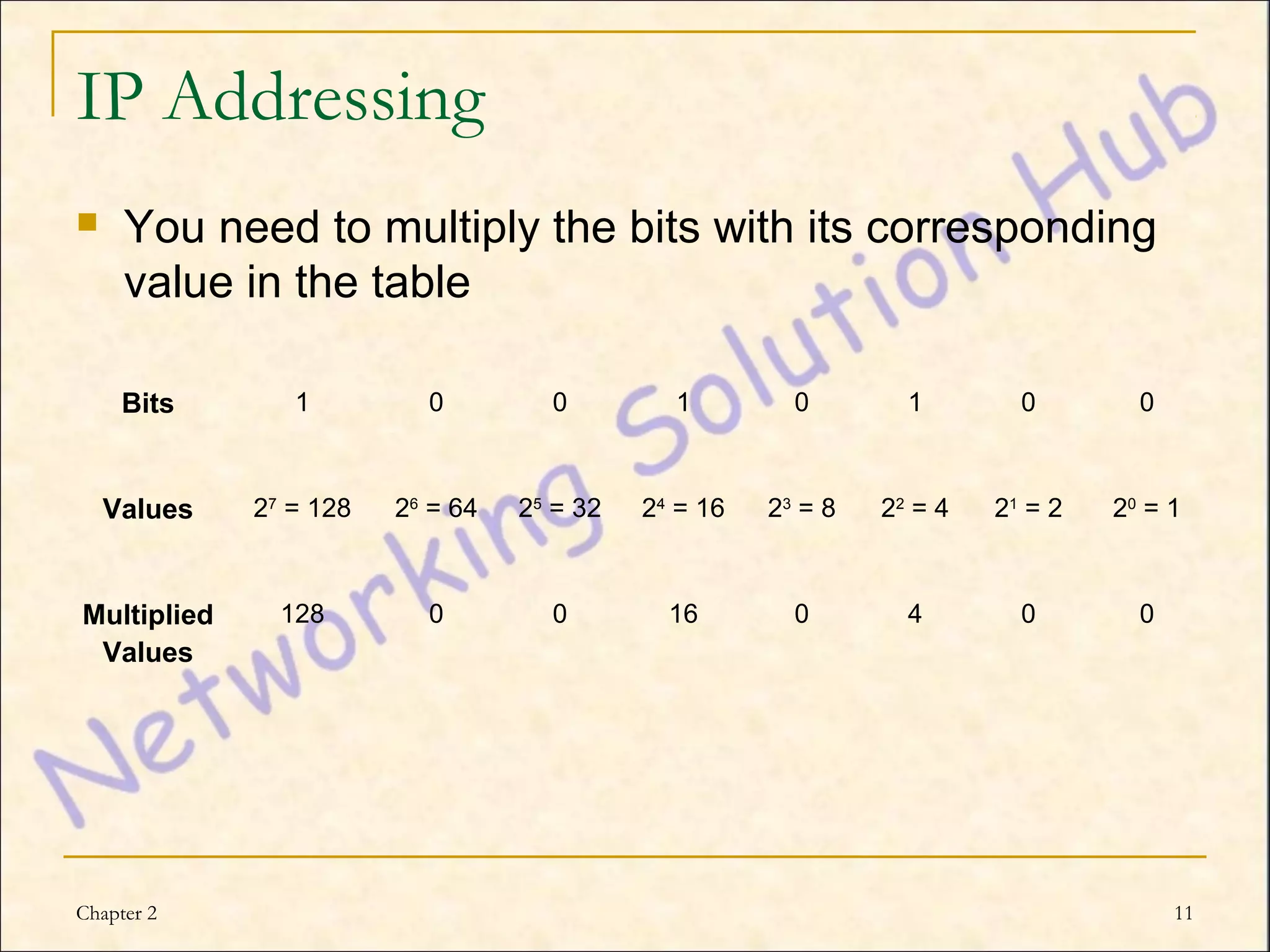
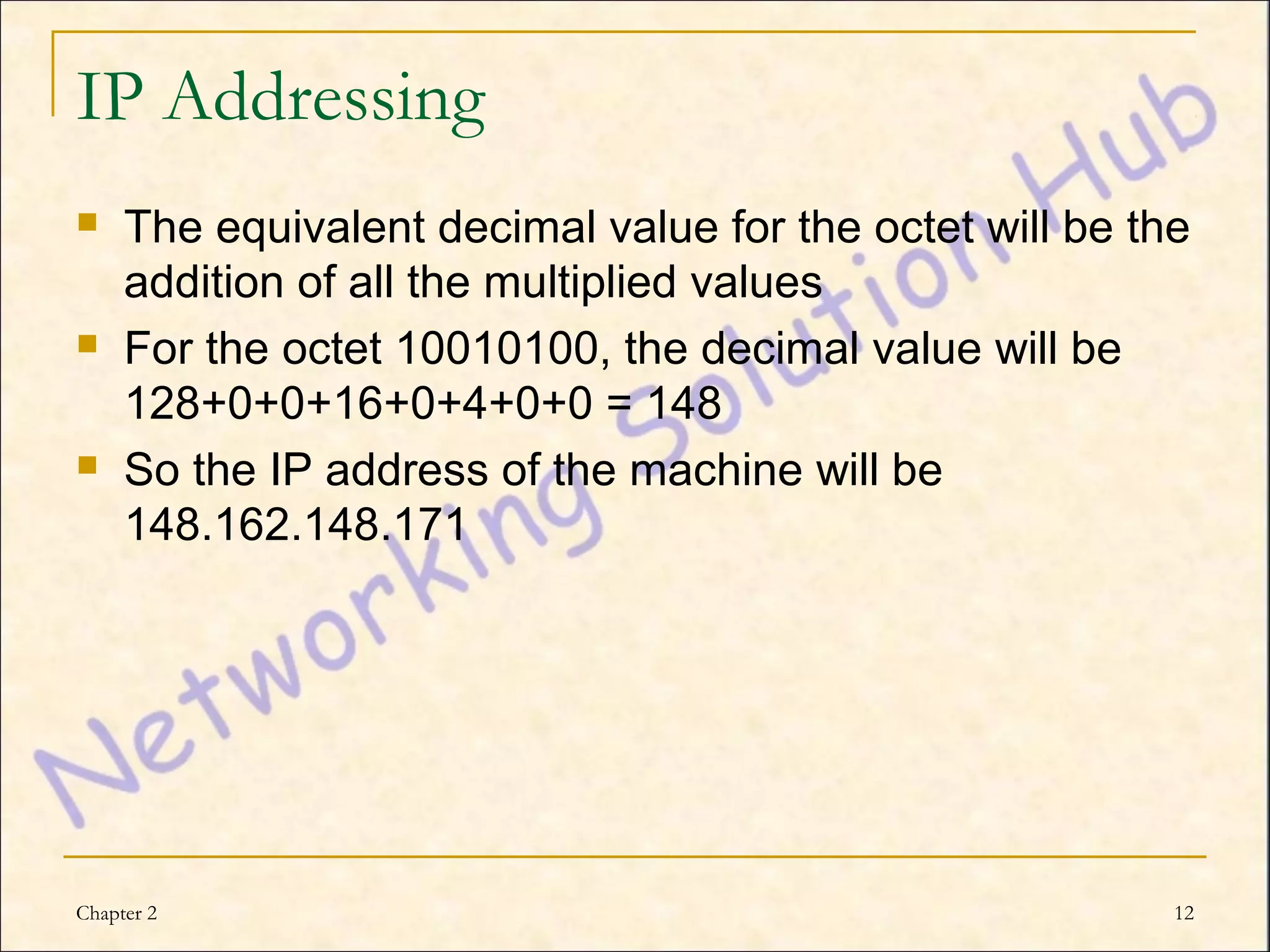
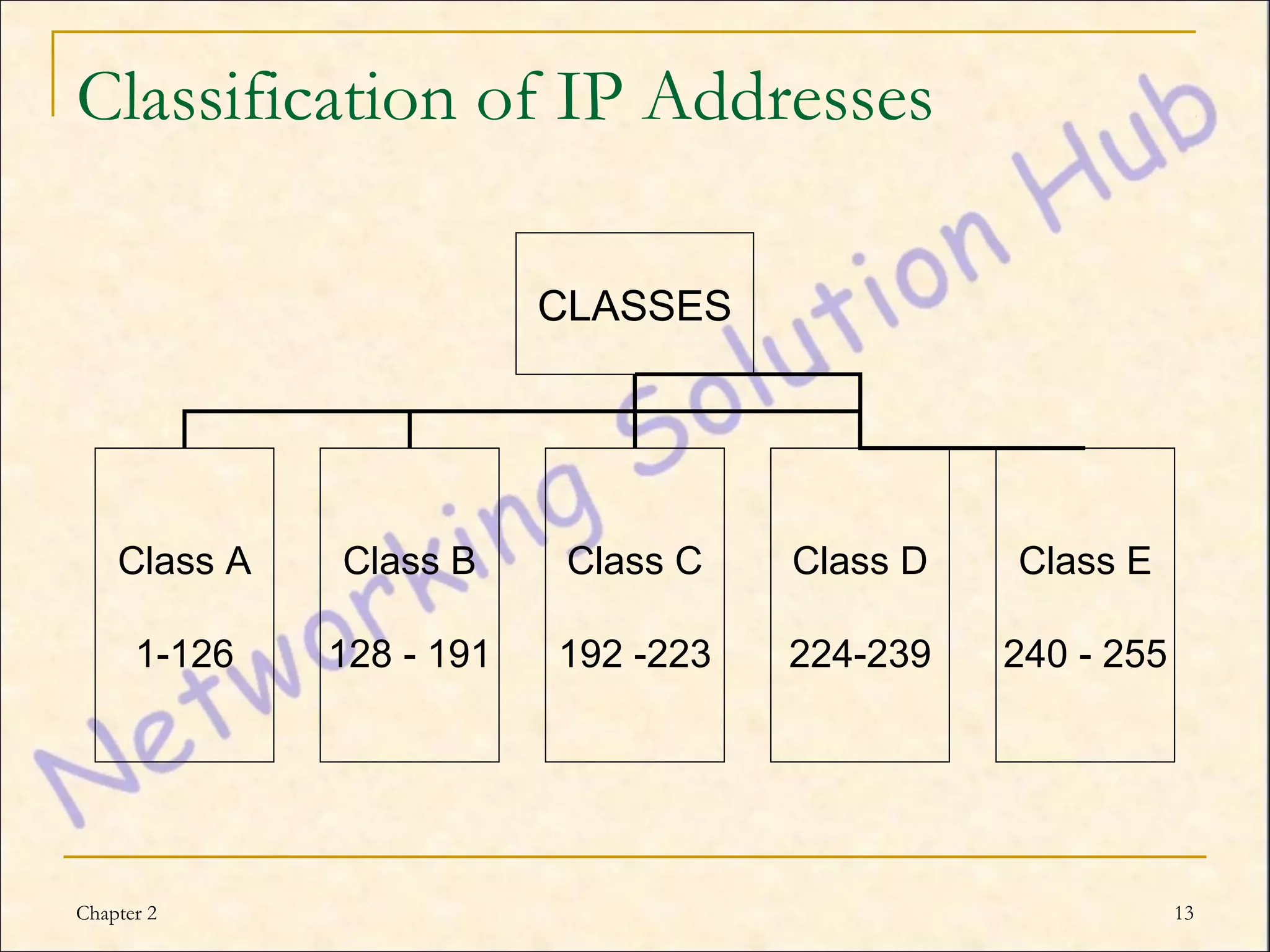
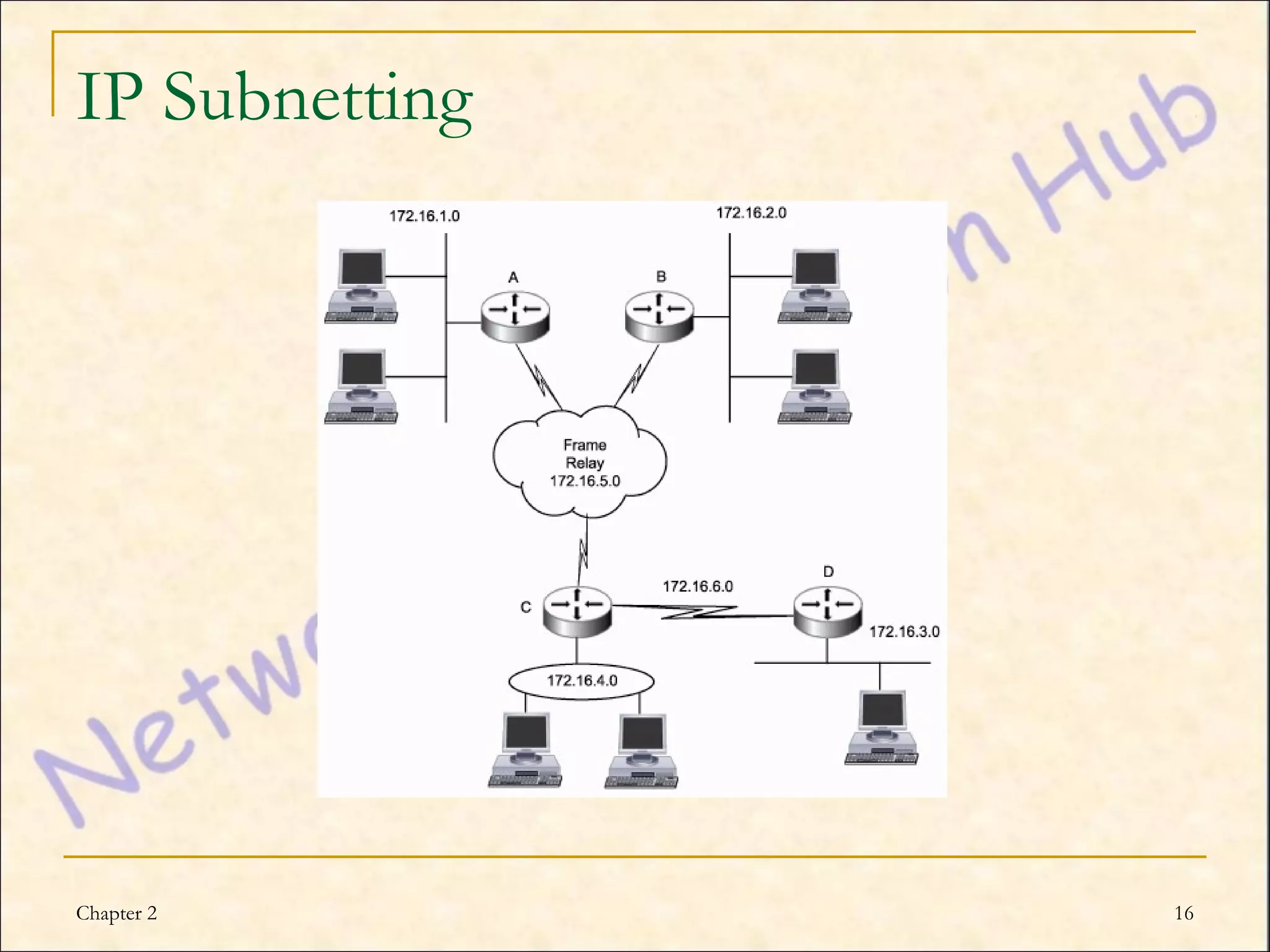
This chapter discusses IP addressing and subnetting. It explains the TCP/IP protocol stack, which has four layers - application, transport, internet and network interface layers. It describes IP addressing, where every device has a unique 32-bit IP address represented as four octets. The chapter also covers subnet masks, which identify the network and host bits in an IP address, and how to calculate the number of subnets and hosts using subnetting.