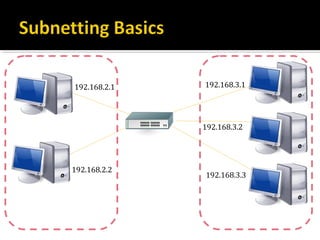
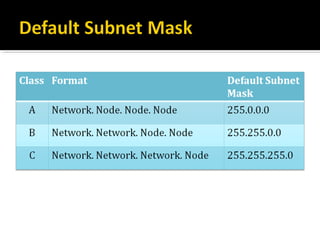
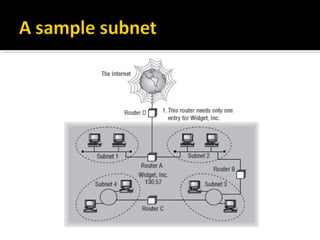
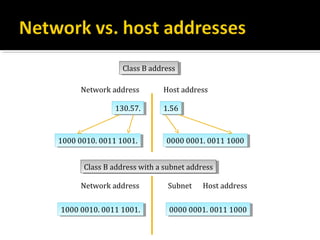
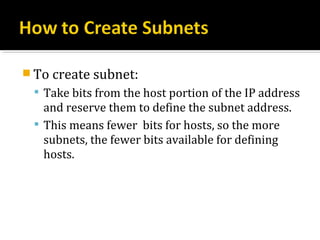
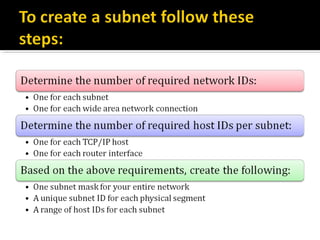
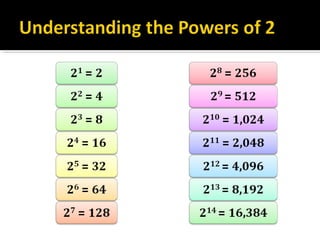
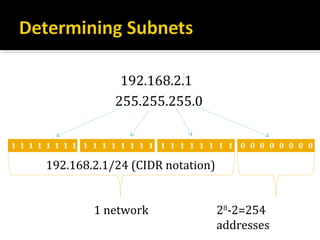
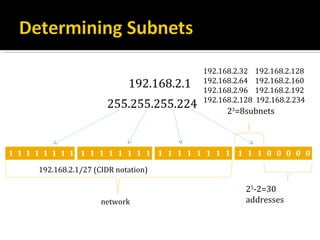
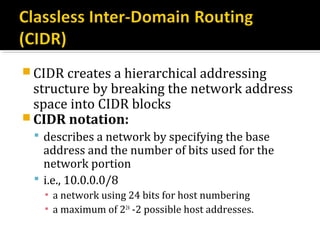
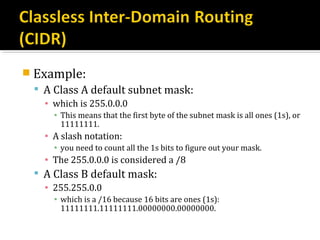
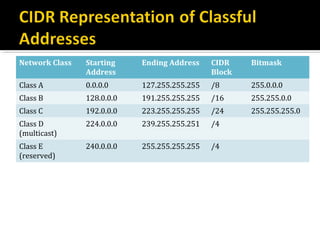
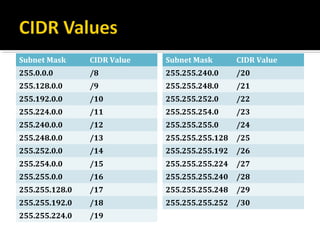
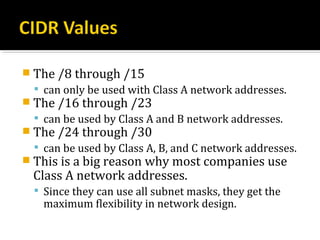
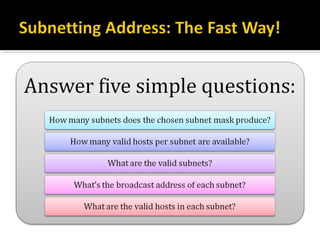
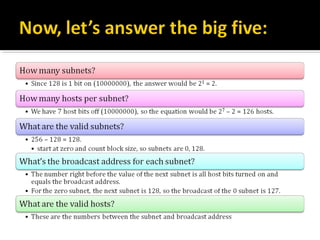
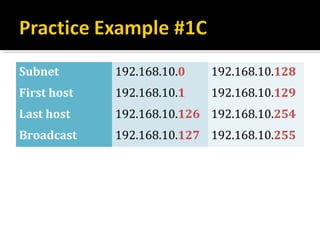
The document discusses subnetting and CIDR notation. It provides information on the benefits of subnetting such as reduced network traffic, optimized performance, simplified management, and facilitating large geographical distances. It defines subnet masks and CIDR notation. It also discusses how to calculate the number of subnets and hosts in a subnet for a given subnet mask in CIDR notation. Finally, it provides an example of how to subnet the Class C network 192.168.10.0/25 into two subnets.