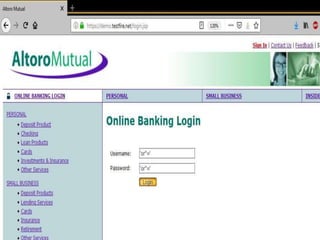
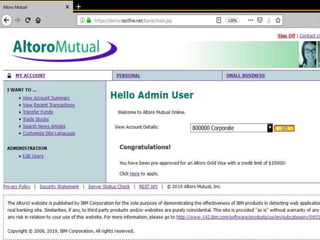
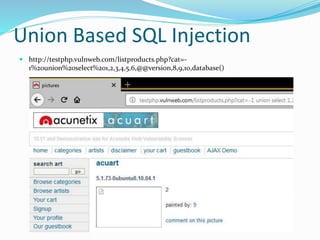
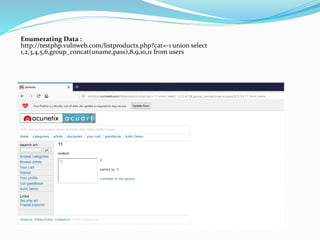
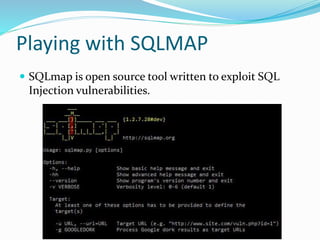
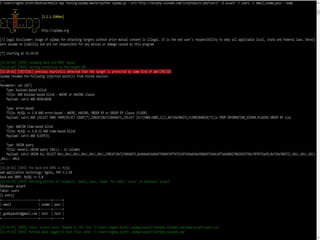
SQL injection is a code injection technique where malicious SQL statements are inserted into an entry field for execution, allowing a hacker to interfere with a database-driven application's interaction with backend databases. There are different types of SQL injections, including union-based, error-based, and blind SQL injections. Authentication can also be bypassed through SQL injection by making logical conditions like 1=1 or ""="" always true. The document provides examples of SQL injection payloads and demo websites to practice SQL injection techniques.