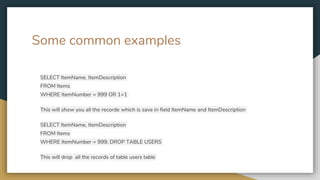
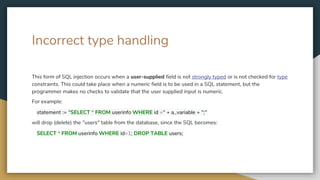
SQL injection is a web security vulnerability that allows attackers to interfere with or gain access to a database through a web application. It occurs when user input is not validated for SQL keywords and special characters that could modify the intended SQL queries. Attackers can use SQL injection to read sensitive data from the database, modify database contents, or even execute administrative operations. Proper input validation and output encoding can help prevent SQL injection attacks.


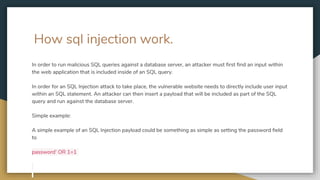
![Pseudo-code
# Define POST variables
uname = request.POST['username']
passwd = request.POST['password']
# SQL query vulnerable to SQLi
sql = “SELECT id FROM users WHERE username=’” + uname + “’ AND password=’” + passwd + “’”
# Execute the SQL statement
database.execute(sql)
This would result in the following SQL query being run against the database server.
SELECT id FROM users WHERE username=’username’ AND password=’password’ OR 1=1’](https://image.slidesharecdn.com/sqlinjection-180425112457/85/Sql-injection-4-320.jpg)


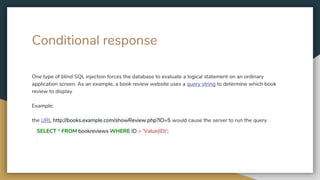
![Blind sql Injection
Blind SQL Injection is used when a web application is vulnerable to an SQL injection but the results of the
injection are not visible to the attacker. The page with the vulnerability may not be one that displays data
but will display differently depending on the results of a logical statement injected into the legitimate SQL
statement called for that page. This type of attack has traditionally been considered time-intensive because
a new statement needed to be crafted for each bit recovered, and depending on its structure, the attack
may consist of many unsuccessful requests. Recent advancements have allowed each request to recover
multiple bits, with no unsuccessful requests, allowing for more consistent and efficient extraction.] There are
several tools that can automate these attacks once the location of the vulnerability and the target
information has been established.](https://image.slidesharecdn.com/sqlinjection-180425112457/85/Sql-injection-9-320.jpg)