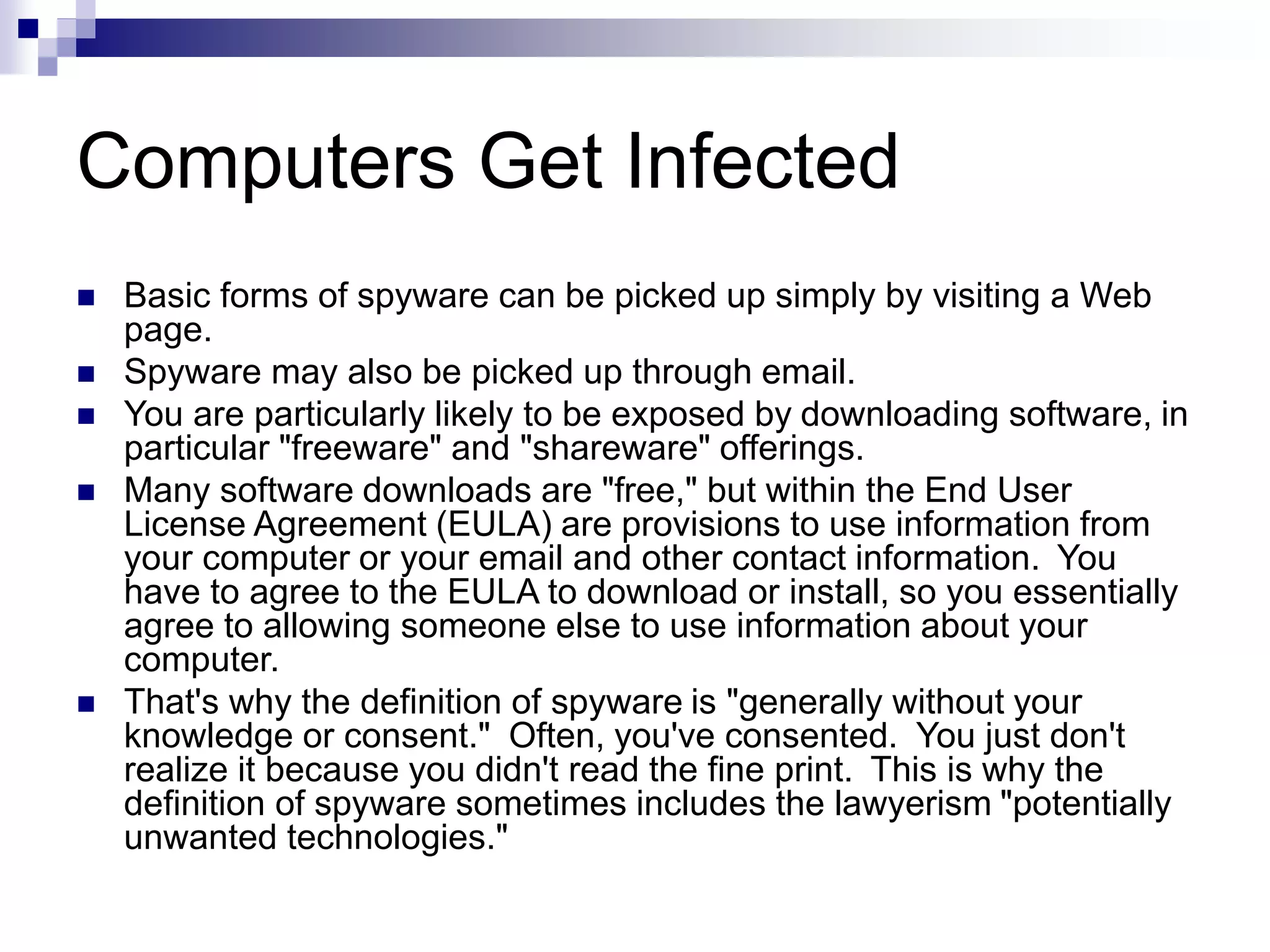
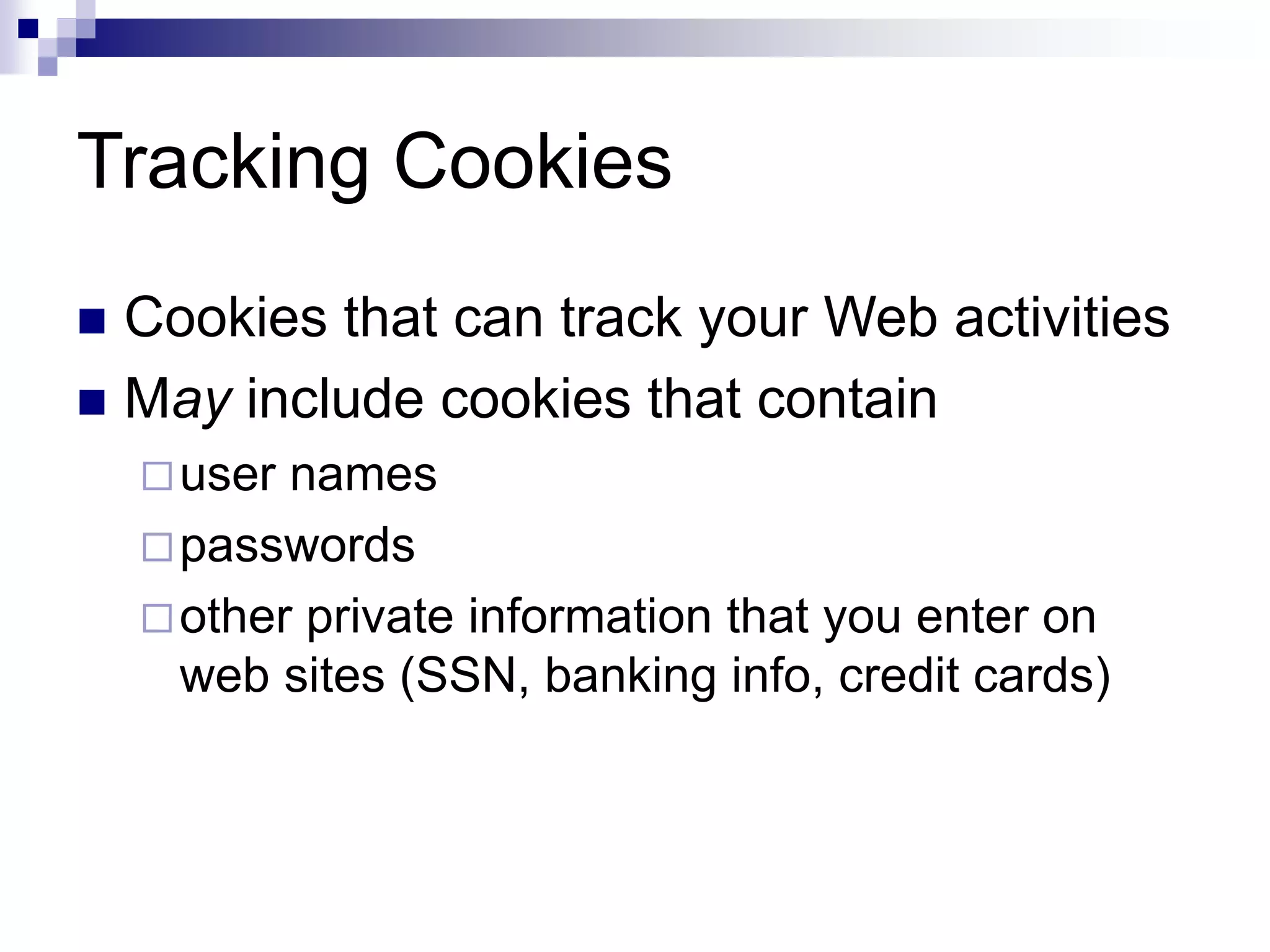
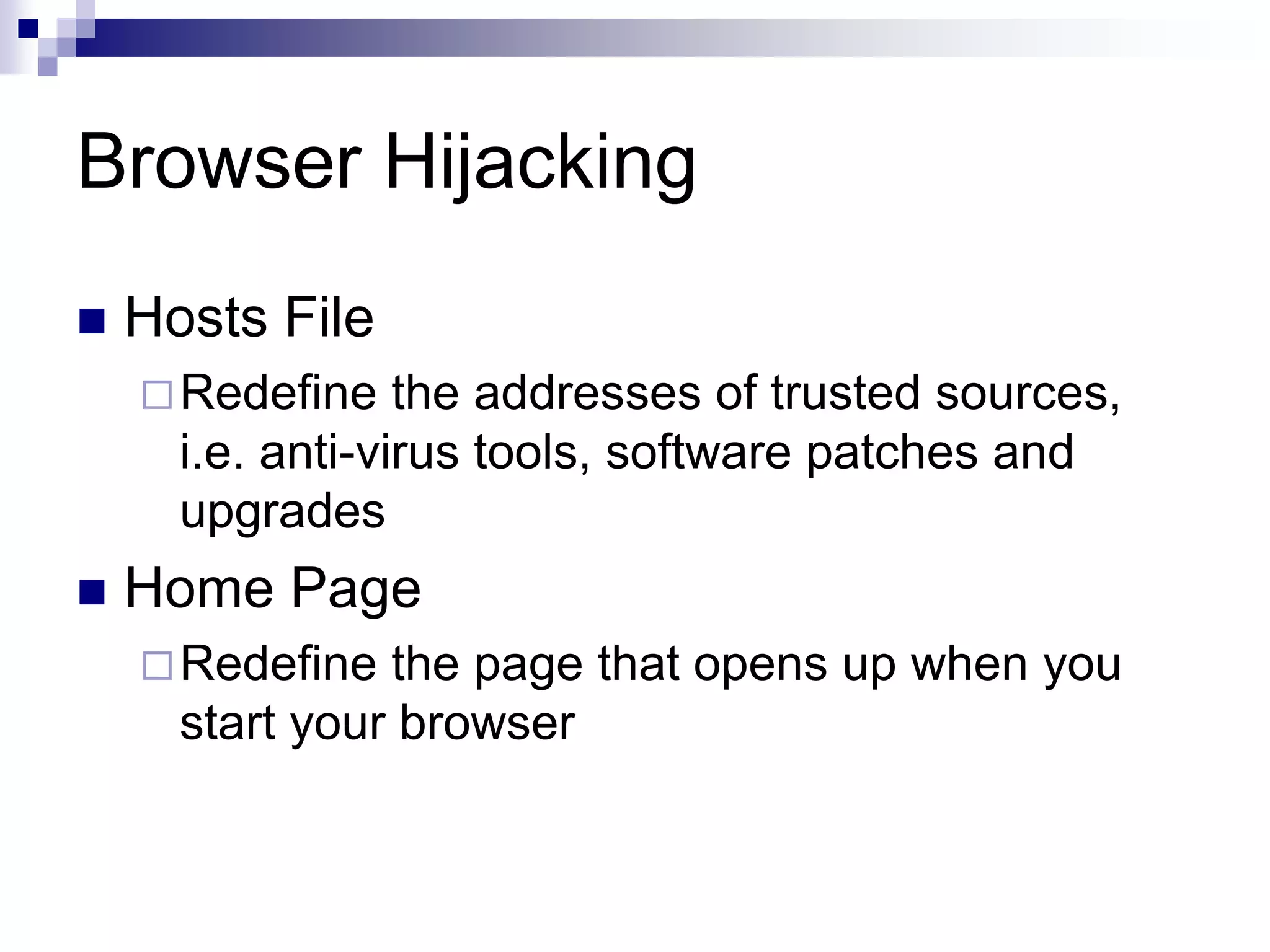
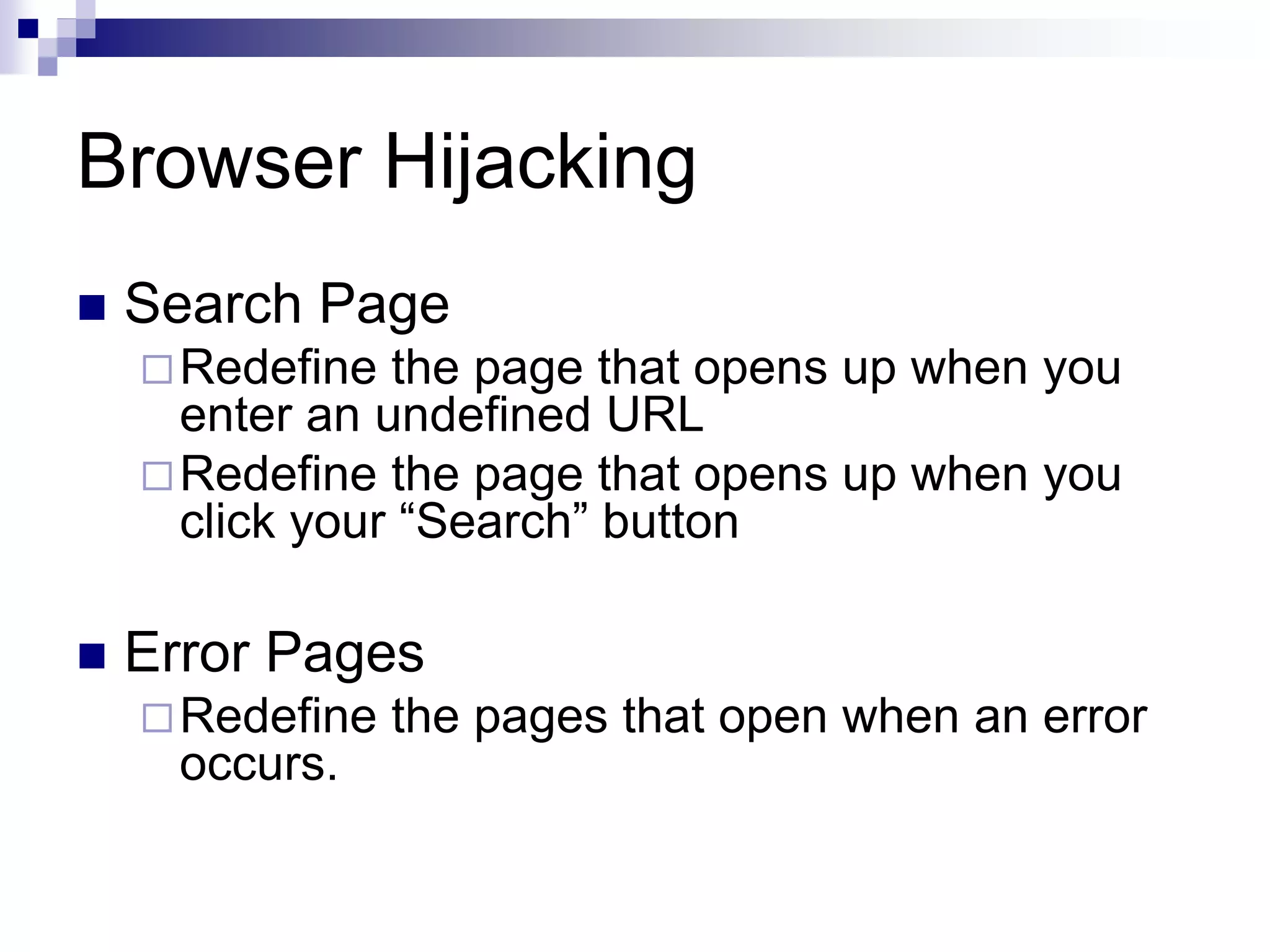
Spyware is software installed without the user's consent that collects information about the user's computer activities and transmits it to a third party. Common types of spyware include tracking cookies, browser hijacking software that changes browser settings, keyloggers that record keystrokes, and spybots that monitor user behavior and transmit logs of activity. A survey found 80% of computers tested had spyware, with the average being 93 spyware components per infected computer. Common spyware programs discussed are Gator, Cydoor, and eZula, which collect user information and display targeted advertisements.