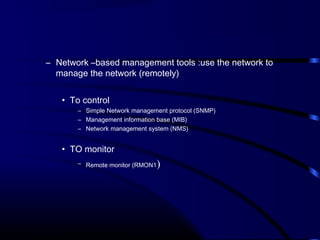
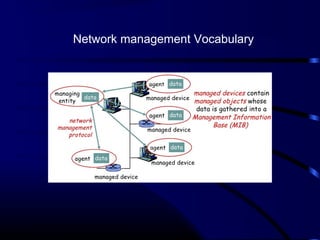
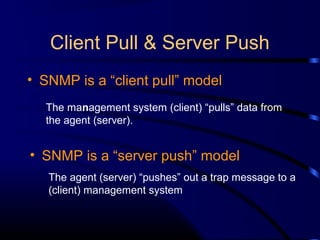
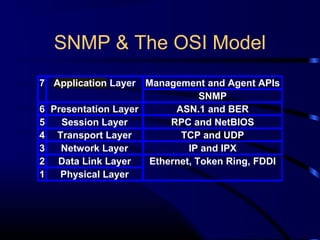
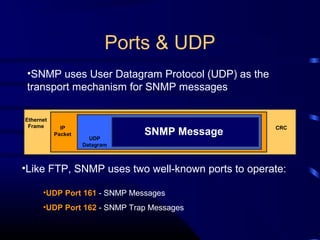
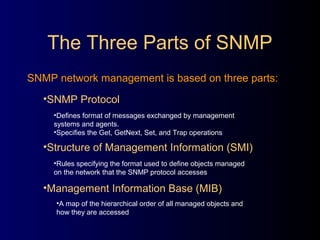
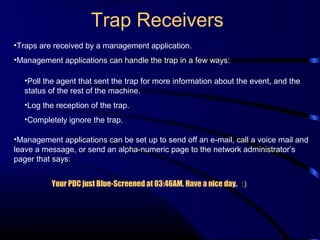
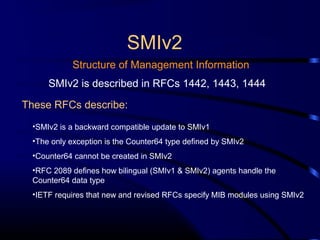
The document provides a comprehensive overview of network management, focusing on the Simple Network Management Protocol (SNMP) and its components, including managed devices, agents, and managing entities. It discusses the evolution of network management roles, the necessity for management tools, and the core functions of SNMP along with its advantages and architectural framework. Additionally, it covers operational details, such as message formats and commercial SNMP applications available today.