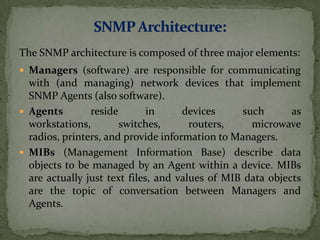
Simple Network Management Protocol (SNMP) allows network administrators to monitor nodes on a network from a central management station. It uses agents residing on devices that provide information to managers. SNMP uses a management information base (MIB) to define objects that agents expose and managers can query using get, getnext, and set commands. SNMPv1 uses community strings for security while SNMPv3 adds authentication, encryption, and access control to securely manage large, complex networks.