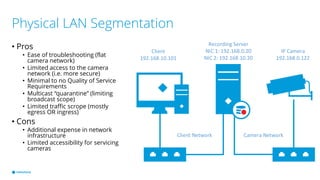
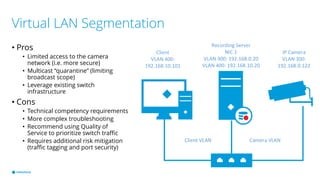
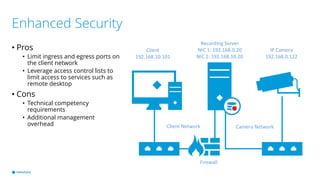
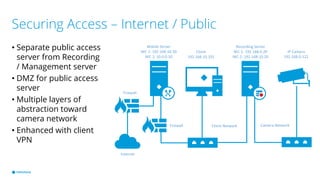
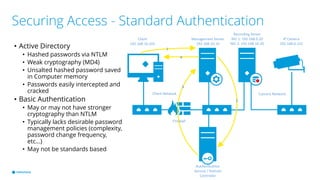
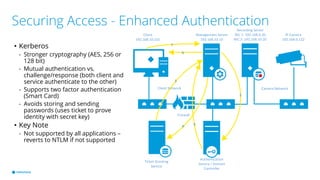
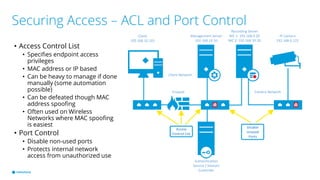
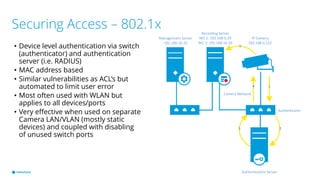
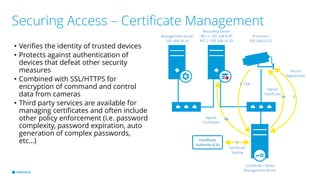
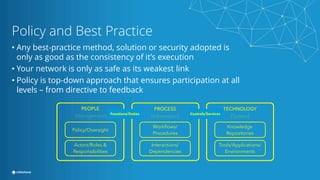
This document provides best practices for network design and security for surveillance camera systems. It recommends a layered approach using physical or virtual segmentation to limit access between networks like the camera and client networks. It discusses strategies for securing access like authentication, access control lists, encryption of data in transit, and policy-based management. Overall the document emphasizes applying security consistently according to standards and assessing risks to establish effective policies.