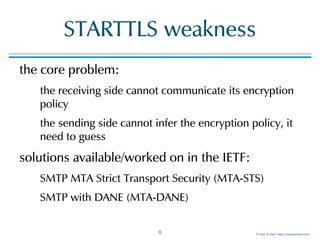
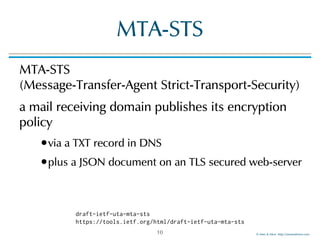
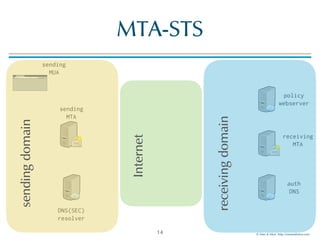
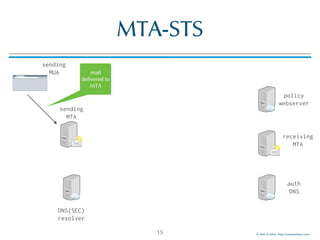
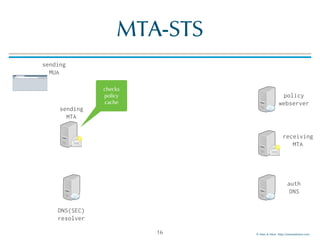
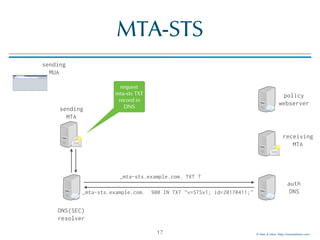
The document discusses email transport security, focusing on two major protocols: MTA-STS (Mail Transfer Agent Strict Transport Security) and DANE (Domain-based Authentication of Named Entities). It highlights the need for these protocols to improve email encryption policies and prevent interception vulnerabilities in SMTP communication. Additionally, it addresses SMTP TLS reporting as a mechanism for reporting encryption failures and ensuring secure email transmission.





![© Men & Mice http://menandmice.com
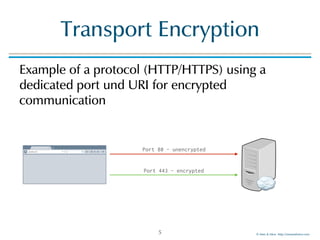
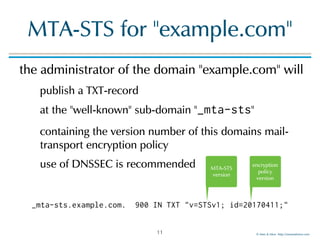
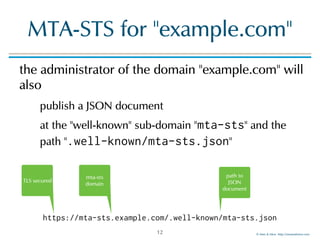
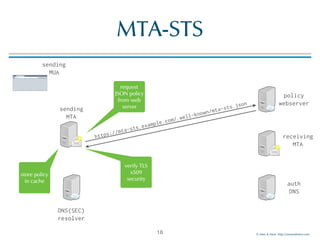
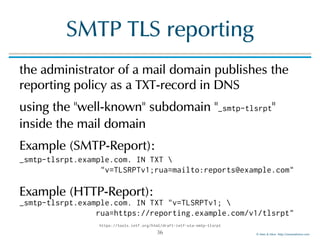
MTA-STS for "example.com"
example content of the JSON document
13
{
"version": "STSv1",
"mode": "enforce",
"mx": [".mail.example.com"],
"max_age": 123456
}
MTA-STS
version
"enforce" or
"report"
Common Name
or Subject
Alternative Name
DNS-ID present in
the X.509
certificate
presented by any
MX receiving mail
for this domain
max
lifetime of
the policy](https://image.slidesharecdn.com/mta-sts-daneslides-170419161100/85/SMTP-STS-Strict-Transport-Security-vs-SMTP-with-DANE-13-320.jpg)

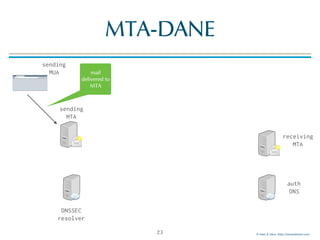
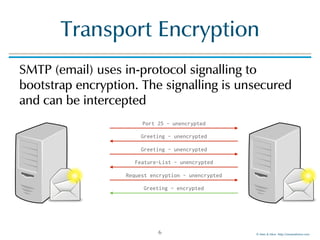
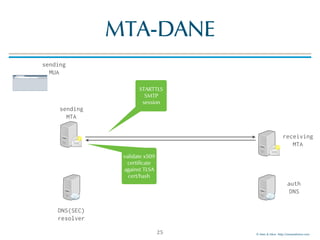
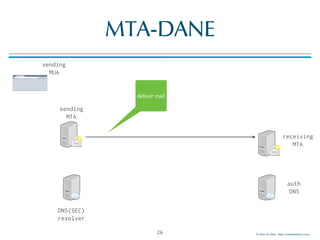
![© Men & Mice http://menandmice.com
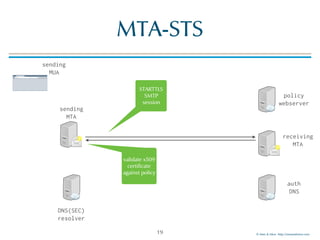
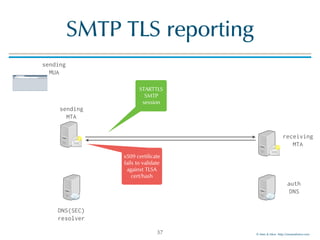
MTA-DANE
24
sending
MTA
sending
MUA
DNSSEC
resolver
auth
DNS
receiving
MTA
MTA
requests
TLSA record
_25._tcp.mail01.example.com. TLSA
_25._tcp.mail01.example.com. TLSA 3 1 1 (
BDC6A9F8312BF24C81D[..]387A147 )
validate
DNSSEC
chain of
trust](https://image.slidesharecdn.com/mta-sts-daneslides-170419161100/85/SMTP-STS-Strict-Transport-Security-vs-SMTP-with-DANE-24-320.jpg)




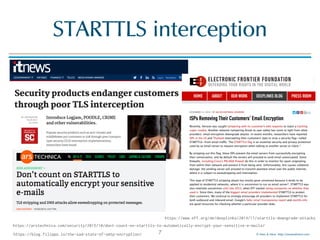
![© Men & Mice http://menandmice.com
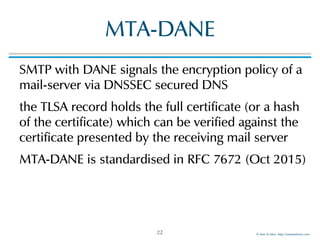
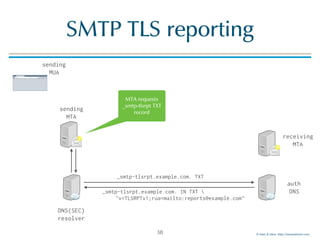
SMTP TLS reporting
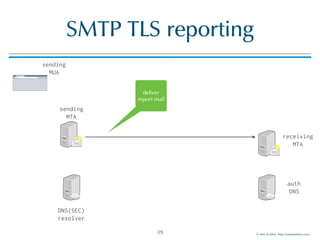
Example JSON-Report
40
https://tools.ietf.org/html/draft-ietf-uta-smtp-tlsrpt
{
"organization-name": "Company-X",
"date-range": {
"start-datetime": "2016-04-01T00:00:00Z", "end-datetime": "2016-04-01T23:59:59Z"
},
"contact-info": "sts-reporting@company-x.com", "report-id": "5065427c-23d3-47ca-b6e0-946ea0e8c4be",
"policy": {
"policy-type": "sts",
"policy-string": "{ "version": "STSv1","mode": "report", "mx": ["*.example.com"], "max_age": 86400 }",
"policy-domain": "company-y.com", "mx-host": "*.mail.company-y.com"
},
"summary": {
"success-aggregate": 5326, "failure-aggregate": 303
}
"failure-details": [{
"result-type": "certificate-expired", "sending-mta-ip": "98.136.216.25",
"receiving-mx-hostname": "mx1.mail.company-y.com", "session-count": 100
}, {
"result-type": "starttls-not-supported", "sending-mta-ip": "98.22.33.99",
"receiving-mx-hostname": "mx2.mail.company-y.com", "session-count": 200,
"additional-information": "hxxps://reports.company-x.com/report_info?id=5065427c-23d3#StarttlsNotSupported"
}]
}
reporting
company
report time-
range
(24 hours)
contact
information
used policy
report
summary
failure
details](https://image.slidesharecdn.com/mta-sts-daneslides-170419161100/85/SMTP-STS-Strict-Transport-Security-vs-SMTP-with-DANE-40-320.jpg)