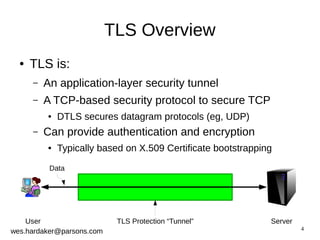
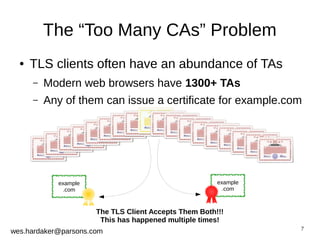
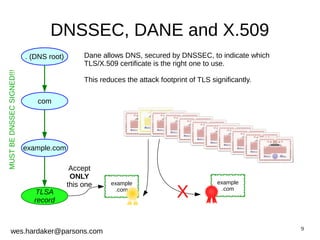
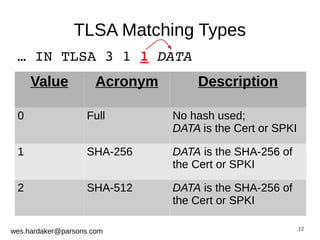
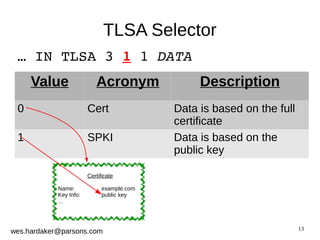
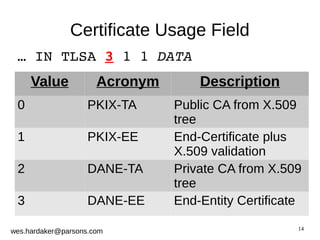
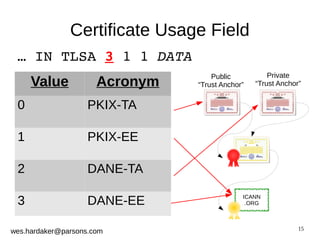
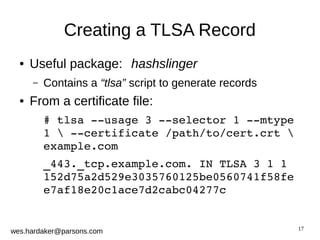
This document provides an introduction to DNSSEC and DANE based security for TLS. It discusses how DANE uses DNSSEC-signed TLSA records to bind TLS certificates to domain names, solving problems with the traditional PKIX trust model. The document outlines how DANE works, how to create TLSA records, and how DANE can secure protocols like HTTPS, SMTP, and XMPP that currently rely on PKIX certificates. It also introduces the Bloodhound browser that includes DANE support to validate TLS connections using DNSSEC and DANE.