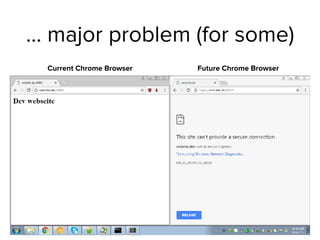
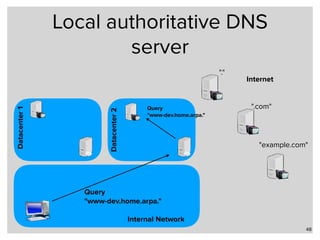
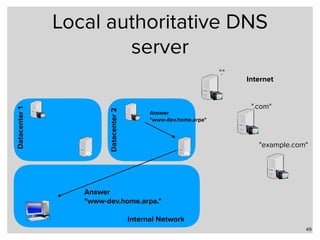
Google has changed Chrome's code to enforce HTTPS encryption on all ".dev" domains by default. This causes problems for developers who use ".dev" locally without HTTPS. Alternatives for local domain names include subdomains of owned domains, reserved domains like ".test", or protocols besides DNS like LLMNR and mDNS. Unbound and BIND can configure local zones to resolve names without internet access.