This webinar discusses local name resolution protocols in Windows networks. It focuses on Link Local Multicast Name Resolution (LLMNR) and Peer Name Resolution Protocol (PNRP). LLMNR provides serverless name resolution on the local subnet using multicast queries. PNRP is a peer-to-peer name resolution protocol that operates over IPv6 or IPv4-IPv6 tunnels. The webinar explains how these protocols work, how to configure and use them, and potential security issues to be aware of when using them. It also advertises upcoming Men & Mice training courses on DNS and name resolution topics.









![PNRP
• PNRP is a Peer-to-Peer name resolution protocol designed
by Microsoft
• The PNRP specification is open[1], but so far, only Windows
Systems since Windows Vista implement this protocol
• PNRP requires IPv6 to work, but on an IPv4 only network,
the Windows system will automatically create a Teredo
IPv6-over-IPv4 tunnel to make PNRP work
• PNRP can resolve IPv6 and IPv4 addresses
16
[1] https://msdn.microsoft.com/en-us/library/cc239047.aspx](https://image.slidesharecdn.com/part2-alternative-name-resolution-in-ms-networks-171122105950/85/Part-2-Local-Name-Resolution-in-Windows-Networks-16-320.jpg)
![PNRP cloud
• PNRP is implemented as multiple distributed hash tables
(DHT)[1]
• Every PNRP node "knows" the addresses of it's
"neighbours" in the PNRP cloud
• By default, a local and a public (global) PNRP-Cloud exists
17
[1] https://en.wikipedia.org/wiki/Distributed_hash_table](https://image.slidesharecdn.com/part2-alternative-name-resolution-in-ms-networks-171122105950/85/Part-2-Local-Name-Resolution-in-Windows-Networks-17-320.jpg)









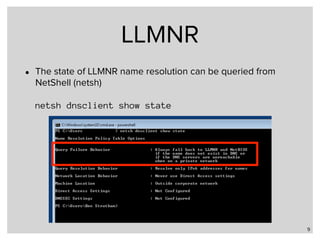
![Register a name in PNRP
• The tool "PNRP-
Beacon"[1] can be
used to register a
PNRP-name inside
a GUI
27
[1] http://ftp.gwdg.de/pub/magazine/ct/listings/0904-098.zip](https://image.slidesharecdn.com/part2-alternative-name-resolution-in-ms-networks-171122105950/85/Part-2-Local-Name-Resolution-in-Windows-Networks-27-320.jpg)
![Registering PNRP names
• PNRP names registered as shown via NetShell or PNRP-
Beacon are not persistent
• They are gone after a reboot of the system
• Persistent PNRP names can be generated using the
Windows Internet Computer Name service (WICN)[1],
which can also be controlled via NetShell
netsh p2p pnrp peer set machinename name="0.mypnrpname" publish=start autopublish=enable
28
[1] https://technet.microsoft.com/en-us/library/bb962088.aspx](https://image.slidesharecdn.com/part2-alternative-name-resolution-in-ms-networks-171122105950/85/Part-2-Local-Name-Resolution-in-Windows-Networks-28-320.jpg)












