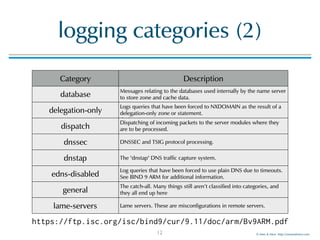
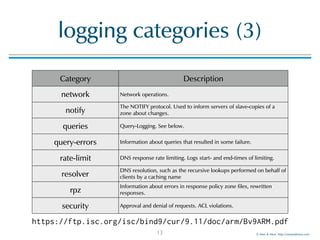
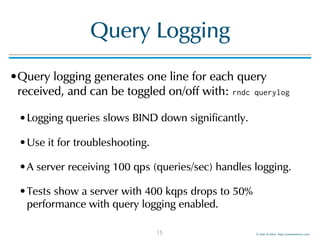
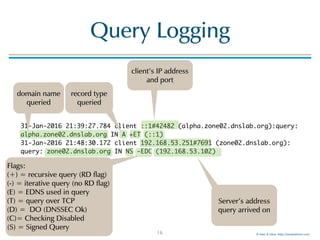
The document provides an overview of best practices for configuring logging in BIND 9, including various logging categories, command examples, and template configurations for both DNS resolver and authoritative servers. It covers the sophisticated log infrastructure of BIND 9, detailing log destinations, rotation, severity levels, and specific categories of logging information. Additionally, it introduces Men & Mice's LogEater tools for further log file management.


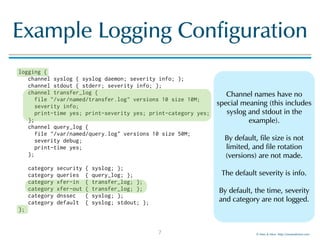



![© Men & Mice http://menandmice.com
rndc trace
> rndc trace 15
> dig +noall slaveme.dnslab.org soa
> cat named.run
25-Nov-2015 09:56:11.012 debug level is now 15
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: UDP request
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: using view '_default'
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: request is not signed
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: recursion not available
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: query
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): ns_client_attach: ref = 1
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): query 'slaveme.dnslab.org/
SOA/IN' approved
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): send
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): sendto
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): senddone
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): next
25-Nov-2015 09:56:34.168 client 192.168.53.251#49360 (slaveme.dnslab.org): ns_client_detach: ref = 0
25-Nov-2015 09:56:34.168 client 192.168.53.251#49360 (slaveme.dnslab.org): endrequest
25-Nov-2015 09:56:34.168 client @0xb7430868: udprecv
[...]
18
The commands were run on the
authoritative server for the
queried zone.](https://image.slidesharecdn.com/bind9-logging-170202171405/85/BIND-9-logging-best-practices-18-320.jpg)
![© Men & Mice http://menandmice.com
rndc trace
> rndc trace 15
> dig +noall slaveme.dnslab.org soa
> cat named.run
25-Nov-2015 09:56:11.012 debug level is now 15
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: UDP request
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: using view '_default'
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: request is not signed
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: recursion not available
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360: query
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): ns_client_attach: ref = 1
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): query 'slaveme.dnslab.org/
SOA/IN' approved
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): send
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): sendto
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): senddone
25-Nov-2015 09:56:34.167 client 192.168.53.251#49360 (slaveme.dnslab.org): next
25-Nov-2015 09:56:34.168 client 192.168.53.251#49360 (slaveme.dnslab.org): ns_client_detach: ref = 0
25-Nov-2015 09:56:34.168 client 192.168.53.251#49360 (slaveme.dnslab.org): endrequest
25-Nov-2015 09:56:34.168 client @0xb7430868: udprecv
[...]
19
original query name. use to
group all messages for one
query, on a busy server](https://image.slidesharecdn.com/bind9-logging-170202171405/85/BIND-9-logging-best-practices-19-320.jpg)







![© Men & Mice http://menandmice.com
Men & Mice "logeater" tools
logeater-queries Example - printing network classes and query types of queries:
$ cat query.log | ./logeater-queries -c -t | column -t
Query-Network-Classes
21379 : IN
6 : CH
Query-Network-Types
8514 : A
4060 : AAAA
3079 : SOA
2372 : DNSKEY
927 : PTR
658 : MX
543 : NS
312 : DS
286 : TXT
186 : NSEC
129 : ANY
115 : CNAME
[…]
27](https://image.slidesharecdn.com/bind9-logging-170202171405/85/BIND-9-logging-best-practices-27-320.jpg)
![© Men & Mice http://menandmice.com
Men & Mice "logeater" tools
logeater-queries Example - printing the top ten query IP addresses
with reverse name resolution (can be slow):
$ cat query.log | ./logeater-queries -i | head | column -t
Query-IP-Addresses
1571 : 212.114.206.217 [muc.example.de.]
821 : 2620:74:13:4400::41 [dnsviz-db.verisignlabs.com.]
794 : 72.13.58.112 [dnsviz-db.verisignlabs.com.]
704 : 54.234.42.241 [241.compute-1.amazonaws.com.]
682 : 2001:19f0:5001:df:76d7:5703:ba0a:e220 []
565 : 185.92.221.212 [185.92.221.212.vultr.com.]
467 : 185.22.143.29 [b9168f1d.cgn.dg-w.de.]
314 : 91.51.184.46 [3b82e.dip0.t-ipconnect.de.]
28](https://image.slidesharecdn.com/bind9-logging-170202171405/85/BIND-9-logging-best-practices-28-320.jpg)





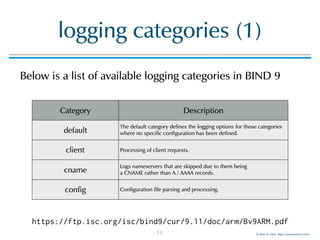
![© Men & Mice http://menandmice.com
logtemplater
logtemplater example:
$ cat named.log | tmpltr - | sort -n | sed -e 's/%s.*||//' | tail
Opening [-] for read
121 27-Jan-2017 00:51:38.574 client @0x7a0d47b0 2001:19f0::76d7:5703:ba0a:e220#49188 (menandmice.training): transfer of
'menandmice.training/IN': IXFR ended
121 27-Jan-2017 00:51:38.415 zone menandmice.training/IN: sending notifies (serial 315)
170 26-Jan-2017 23:00:37.060 client @0x7bf057b0 192.0.2.197#33796 (1.1.1.1.in-addr.arpa): query failed (REFUSED) for 1.1.1.1.in-
addr.arpa/IN/PTR at query.c:6899
216 26-Jan-2017 22:57:22.482 zone _openpgpkey.example.de/IN: next key event: 26-Jan-2017 23:57:22.480
216 26-Jan-2017 22:57:22.480 zone _openpgpkey.example.de/IN: reconfiguring zone keys
5184 26-Jan-2017 22:57:21.702 zone 6.b.2.0.8.9.1.0.1.0.a.2.ip6.arpa/IN: next key event: 26-Jan-2017 23:57:21.675
5184 26-Jan-2017 22:57:21.675 zone 6.b.2.0.8.9.1.0.1.0.a.2.ip6.arpa/IN: reconfiguring zone keys
6495 26-Jan-2017 22:11:20.136 client @0x7bf057b0 192.0.2.217#47130/key dyn.example.de: signer "dyn.example.de" approved
6495 26-Jan-2017 22:11:20.137 client @0x7bf057b0 192.0.2.217#47130/key dyn.example.de: updating […]
6496 26-Jan-2017 22:10:20.765 client @0x7bf057b0 192.0.2.217#42821/key dyn.example.de: updating […]
34
Date and time of 1st
occurrence of this type of
message
Number of
messages of this type
inside the file
Content of 1st occurrence of
this type of message](https://image.slidesharecdn.com/bind9-logging-170202171405/85/BIND-9-logging-best-practices-34-320.jpg)





