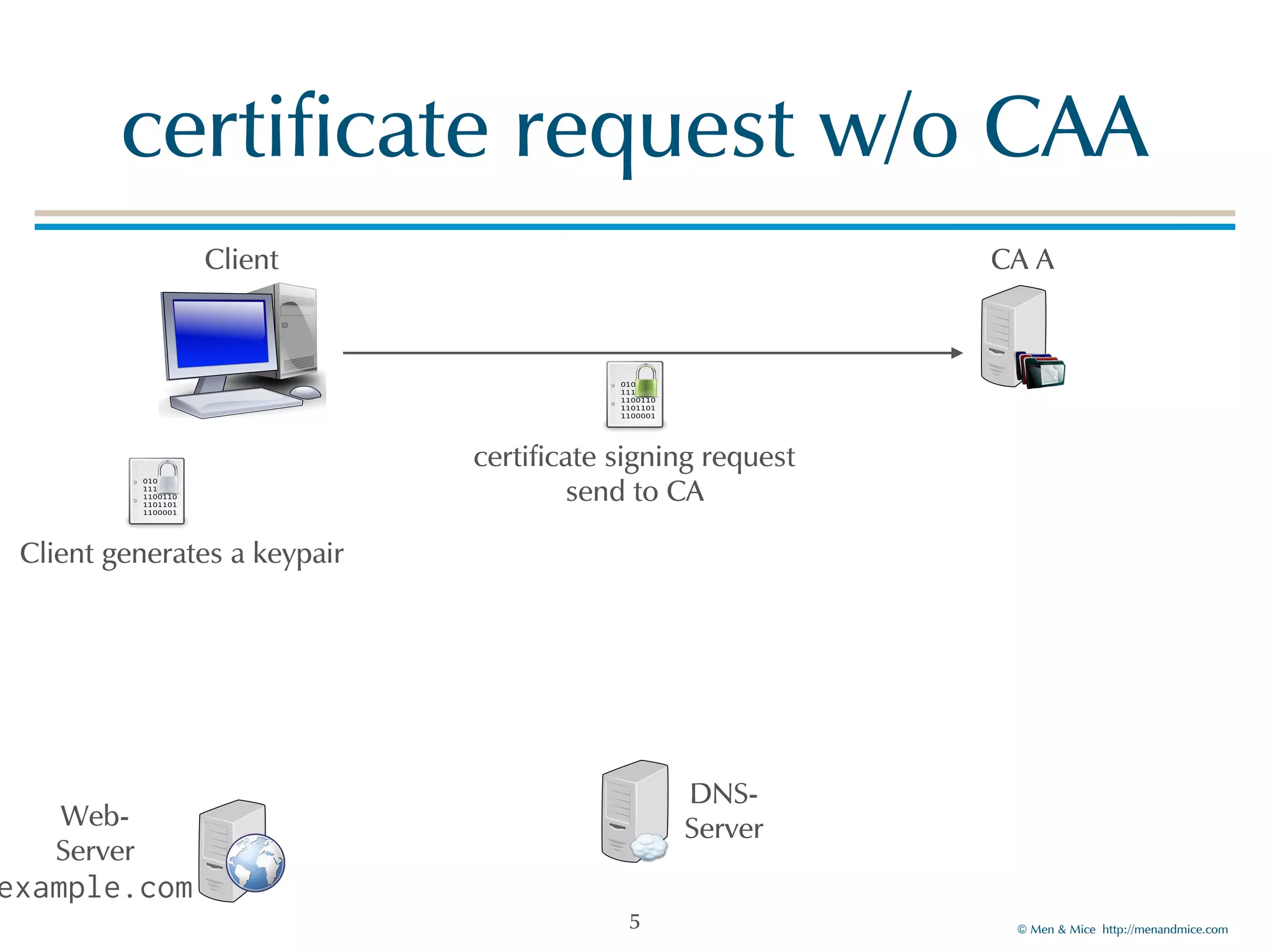
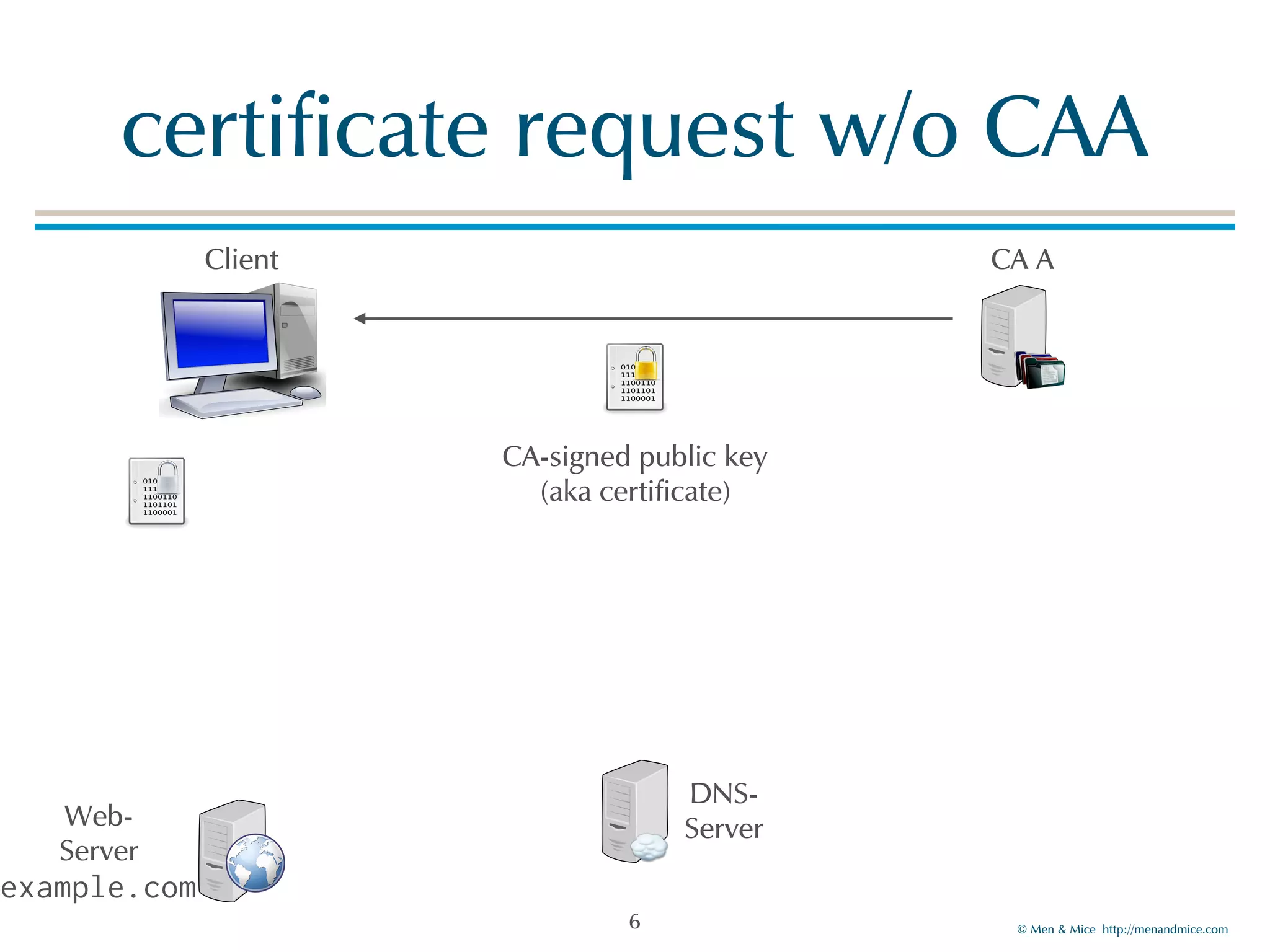
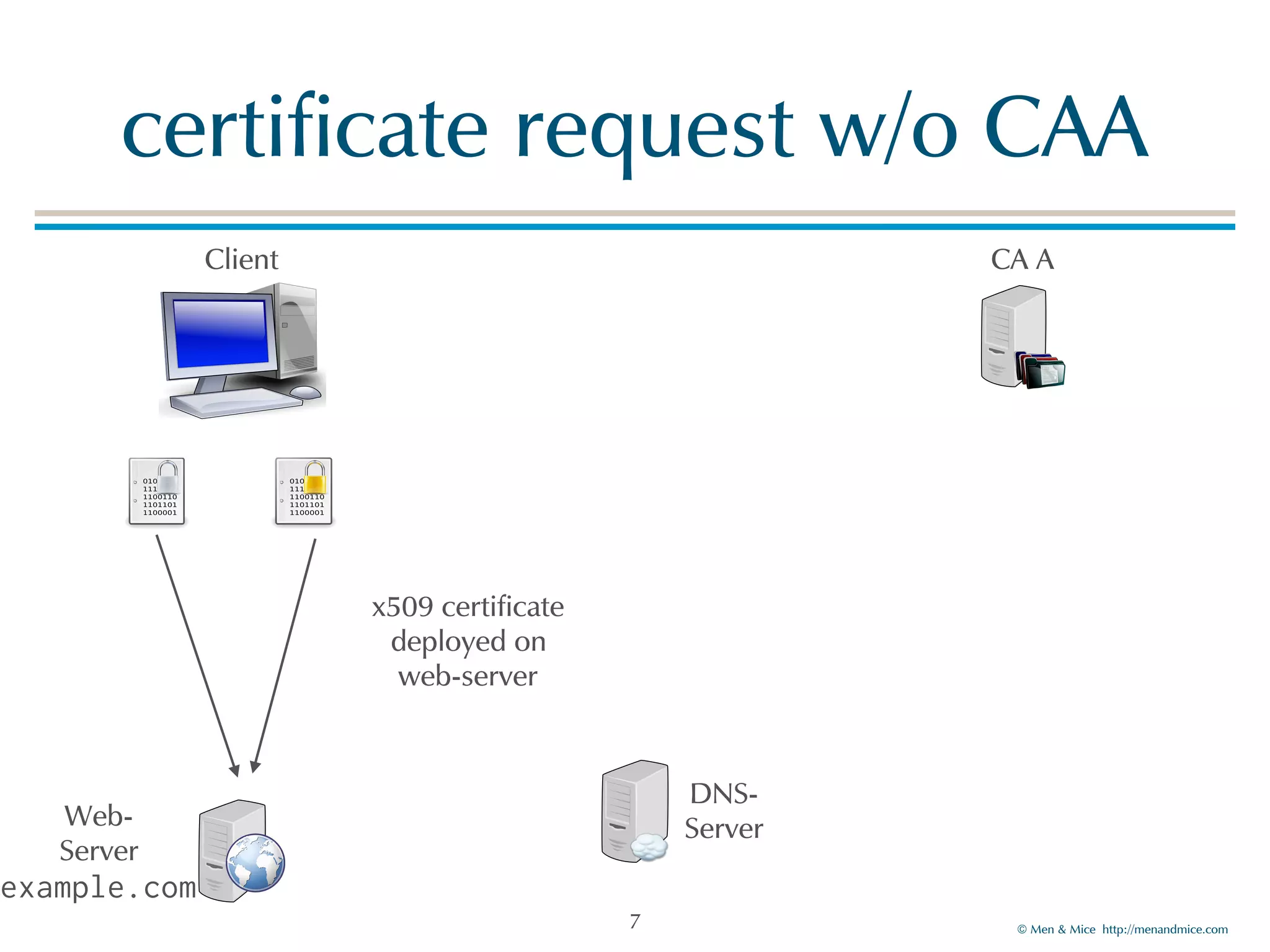
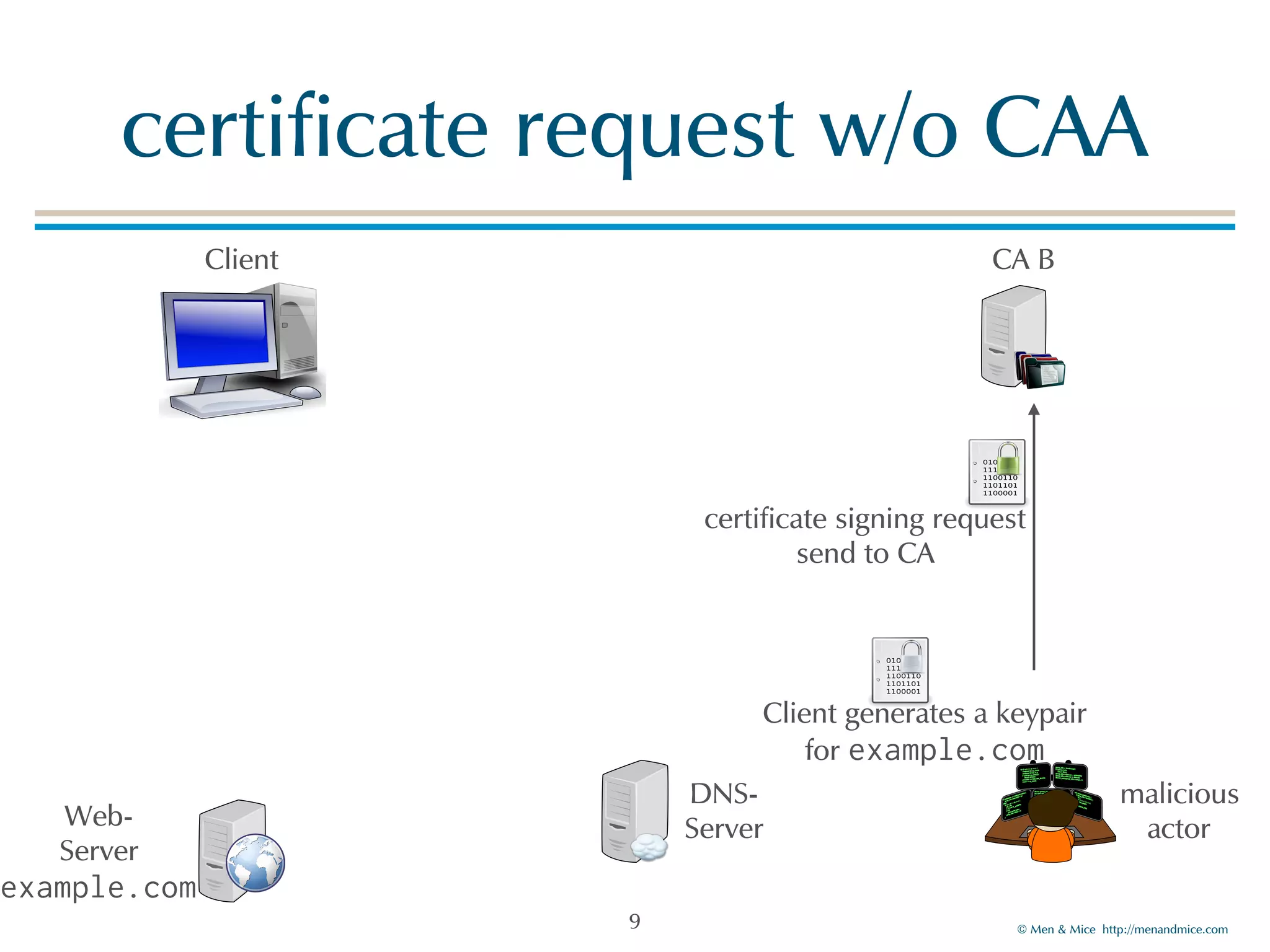
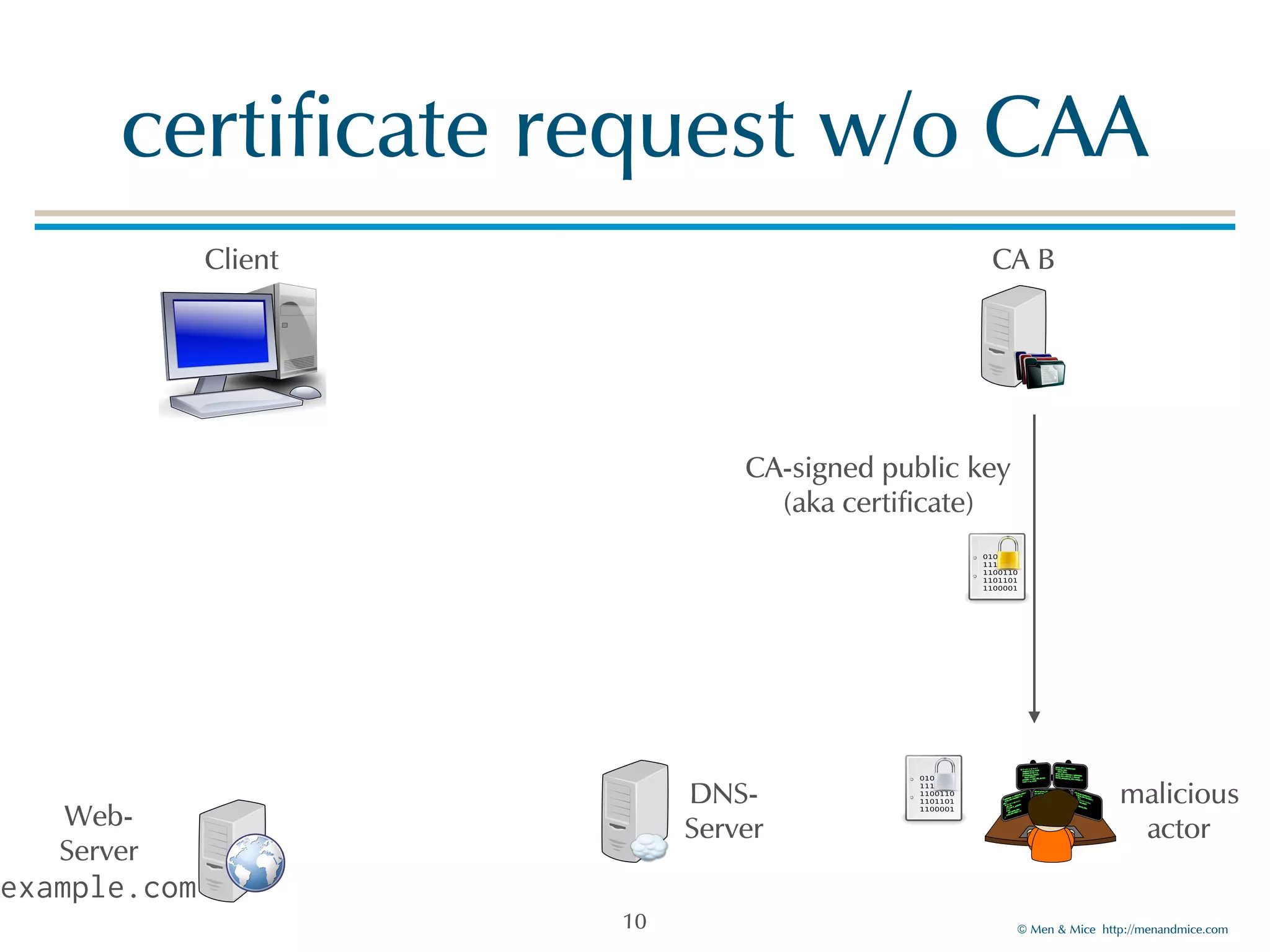
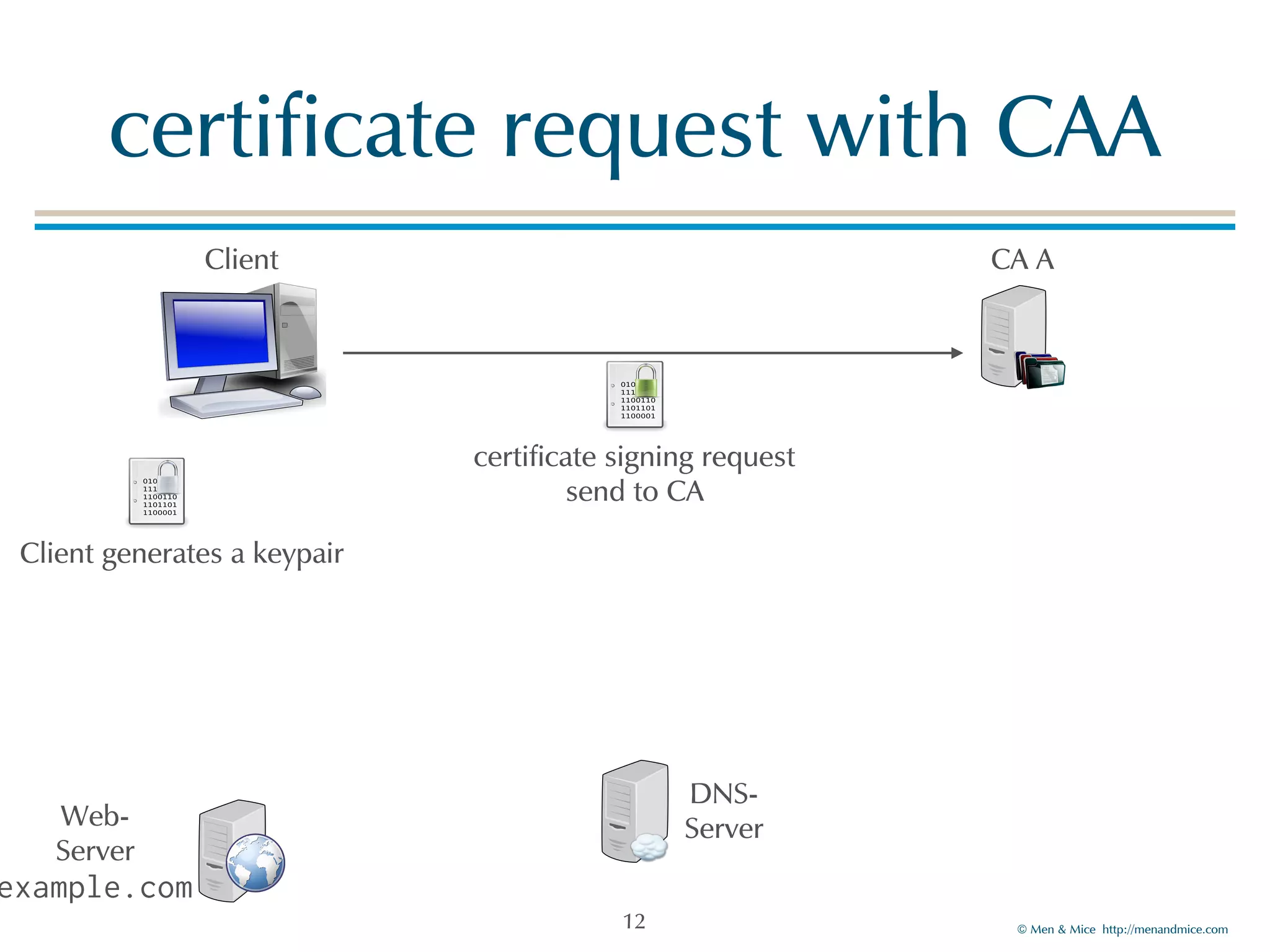
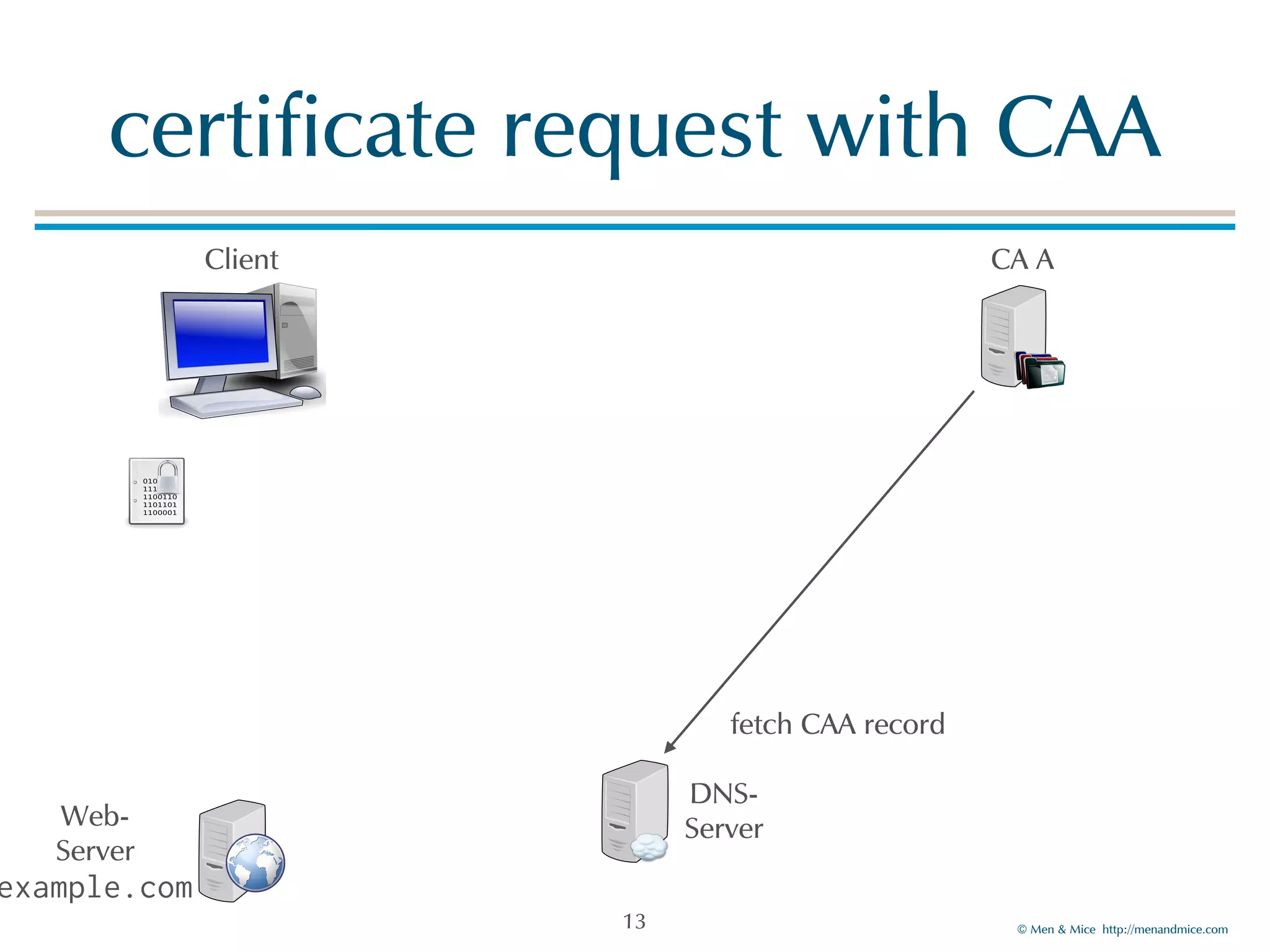
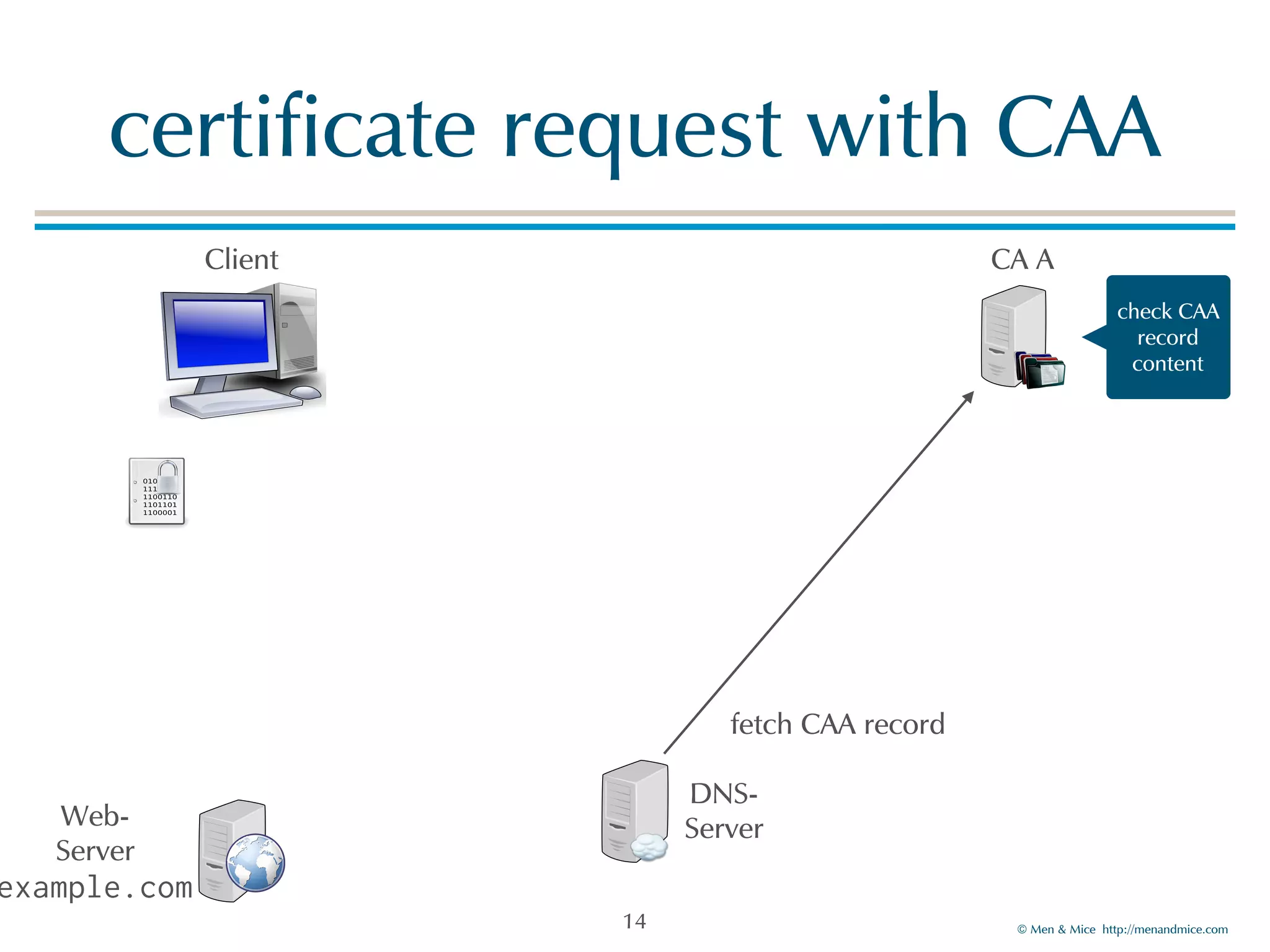
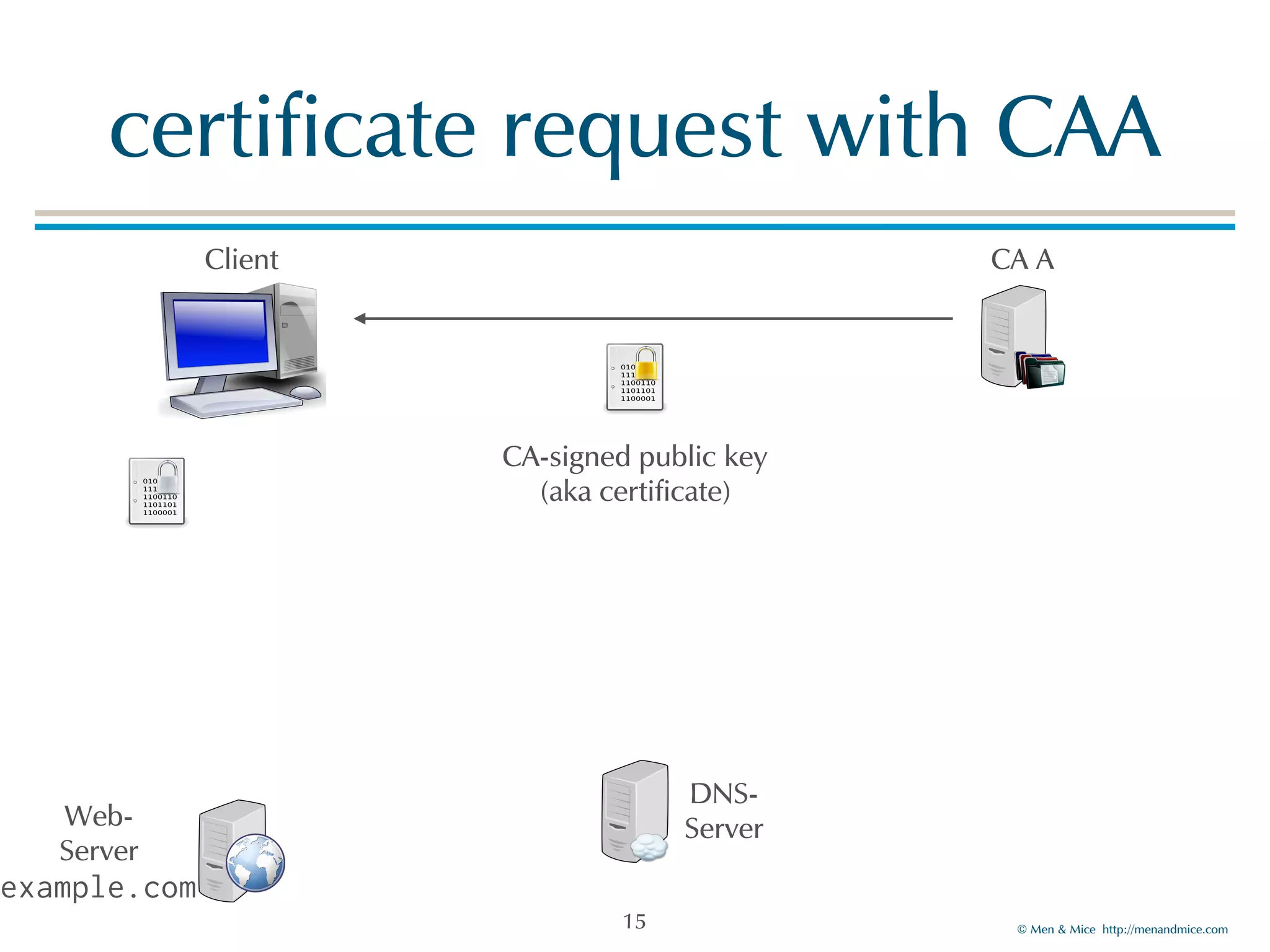
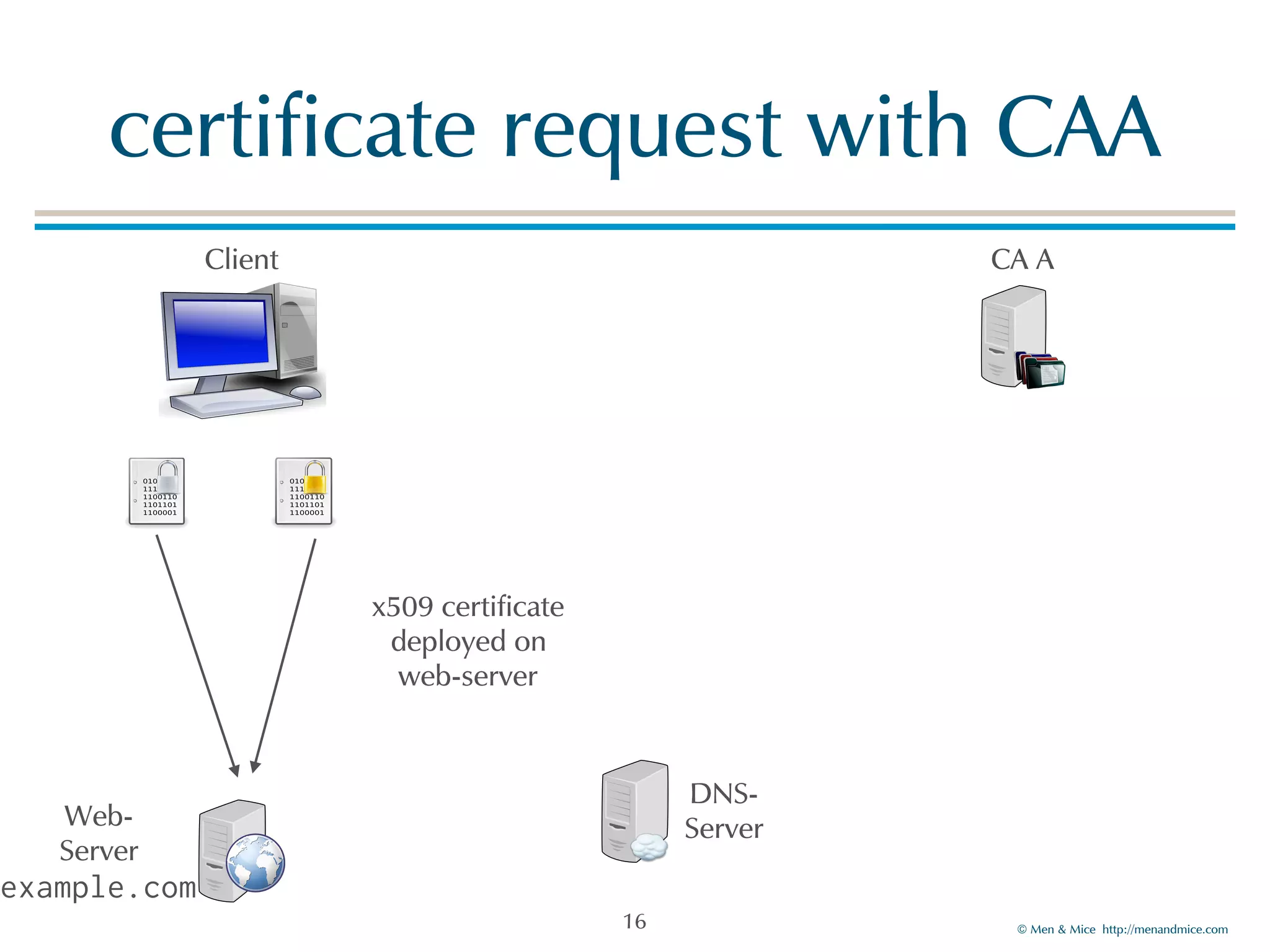
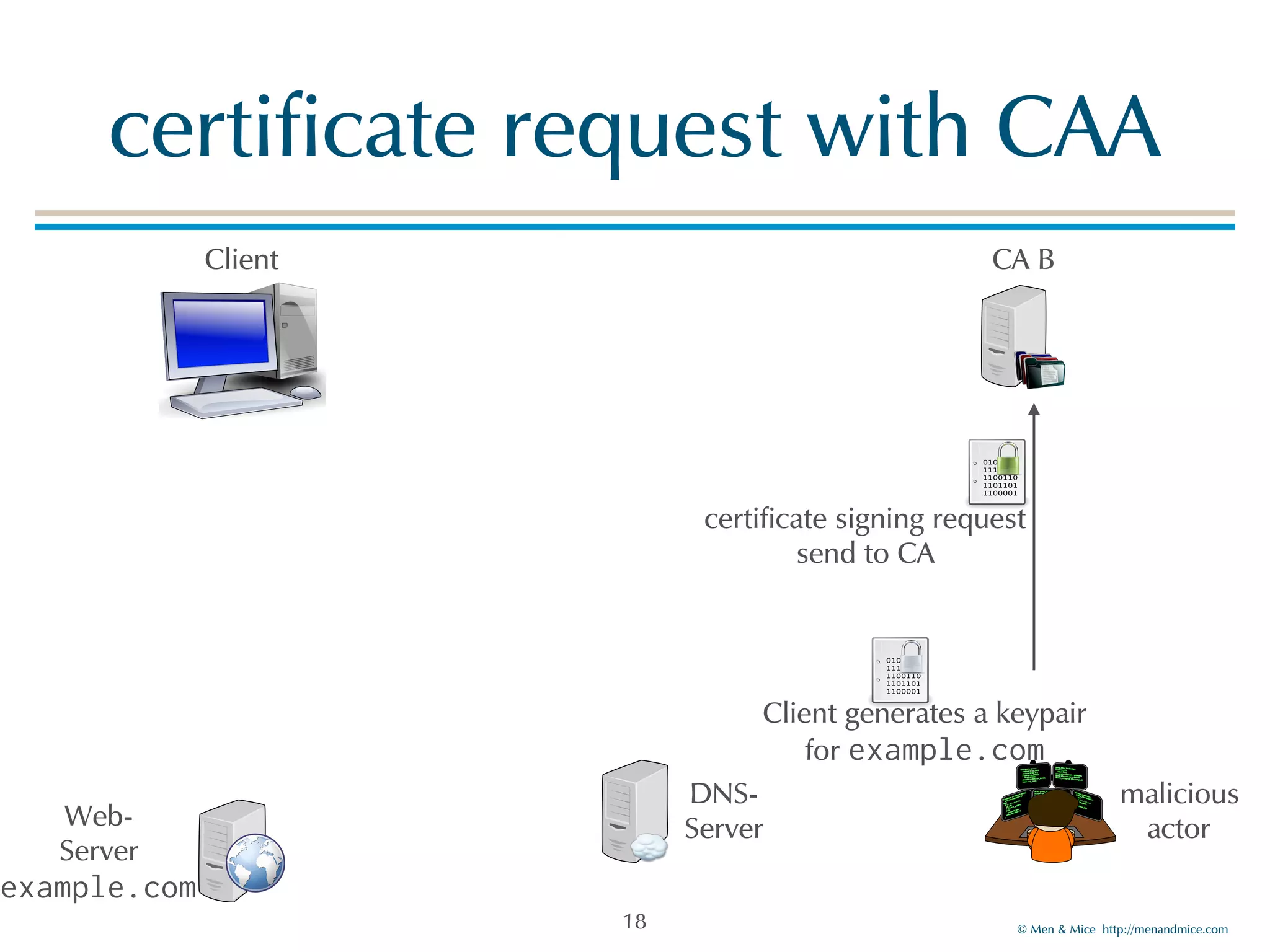
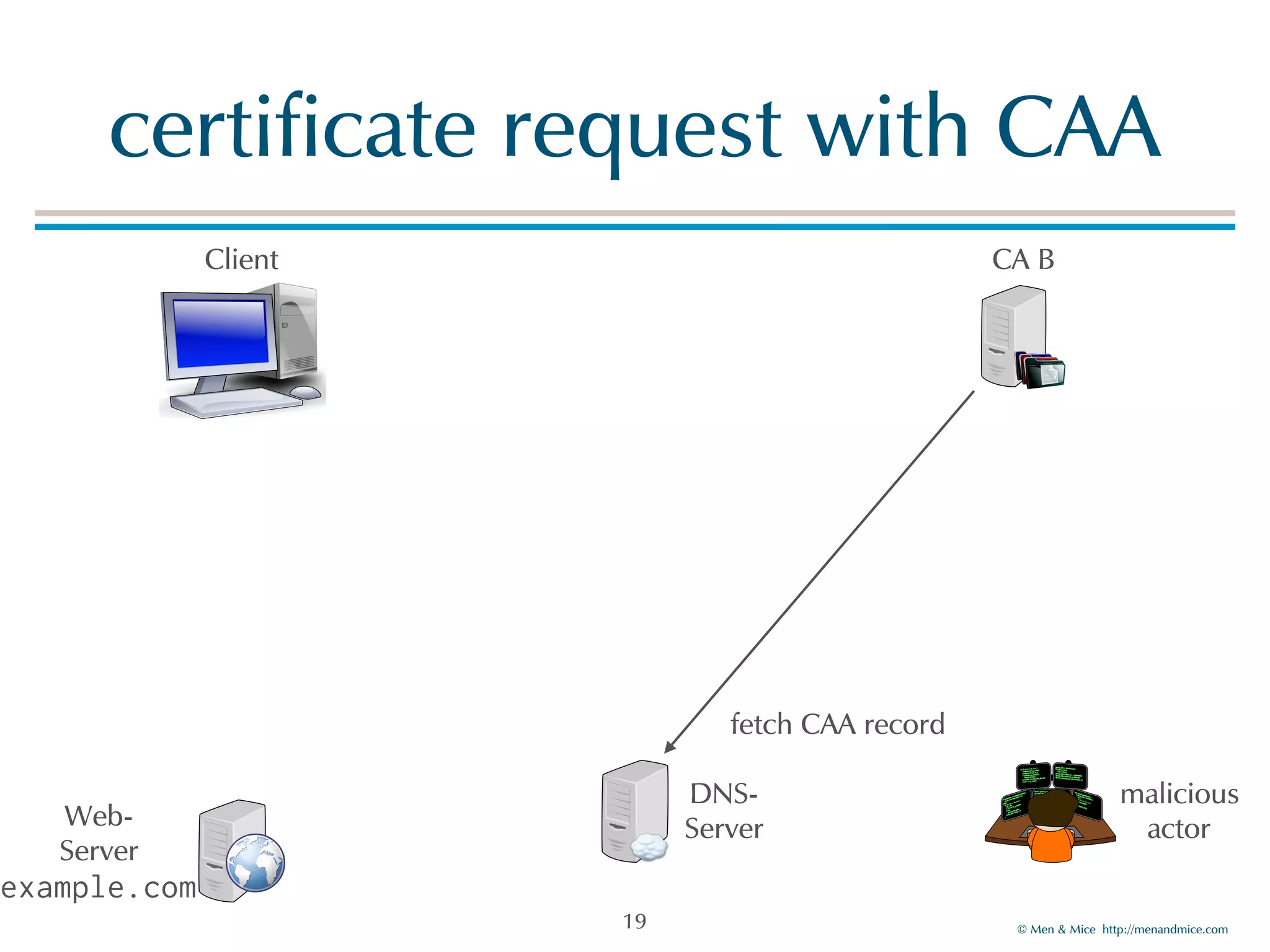
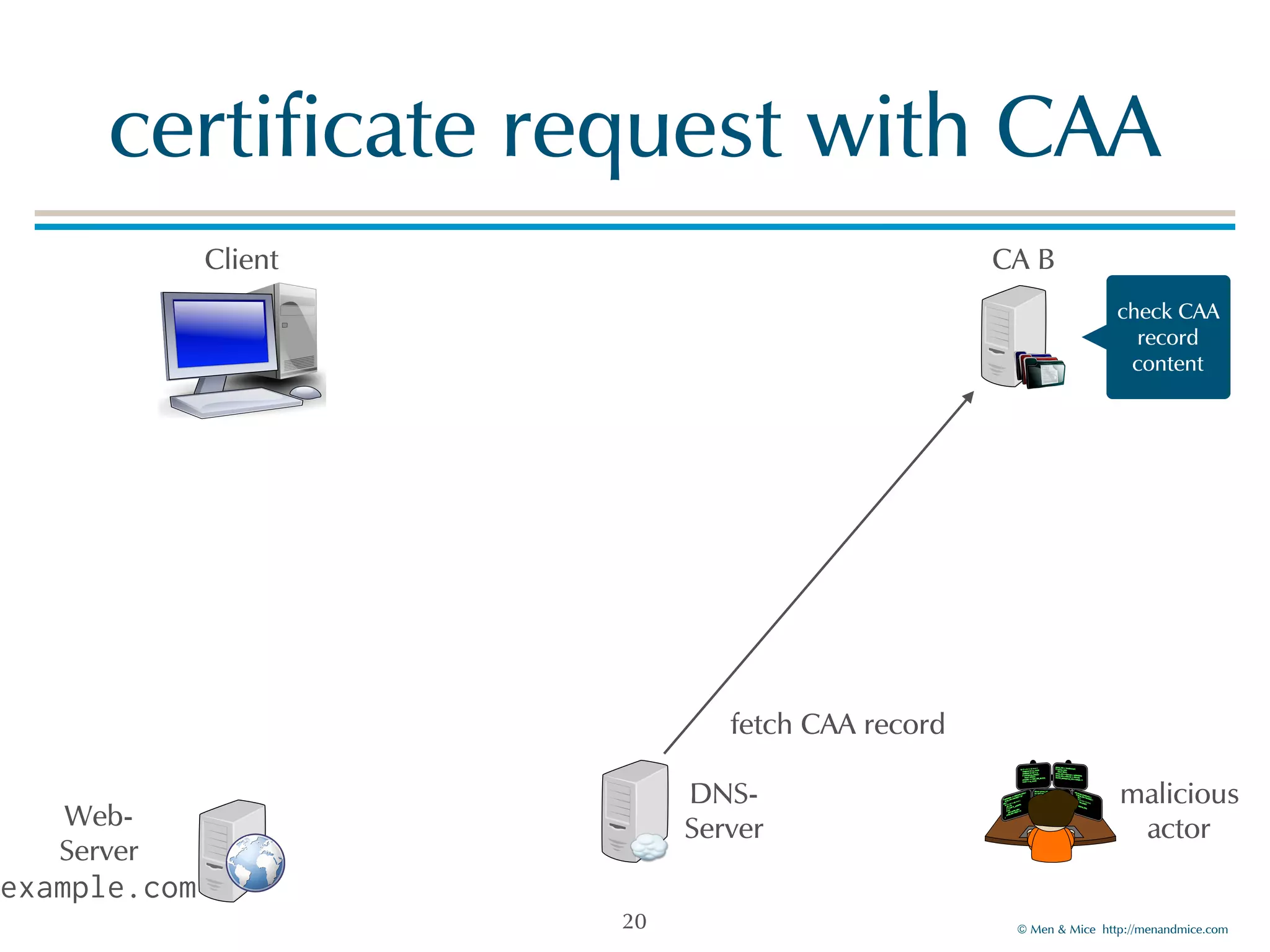
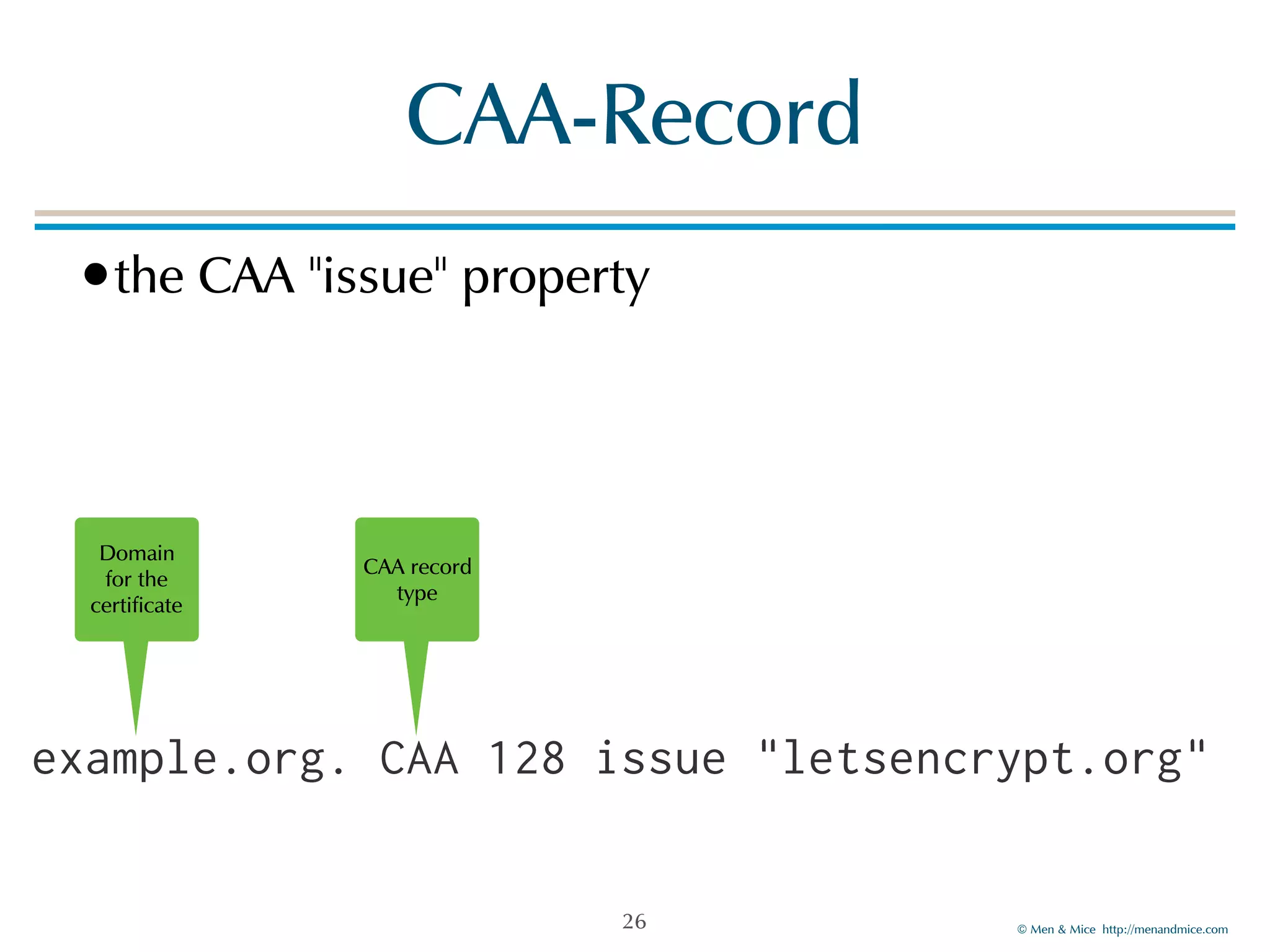
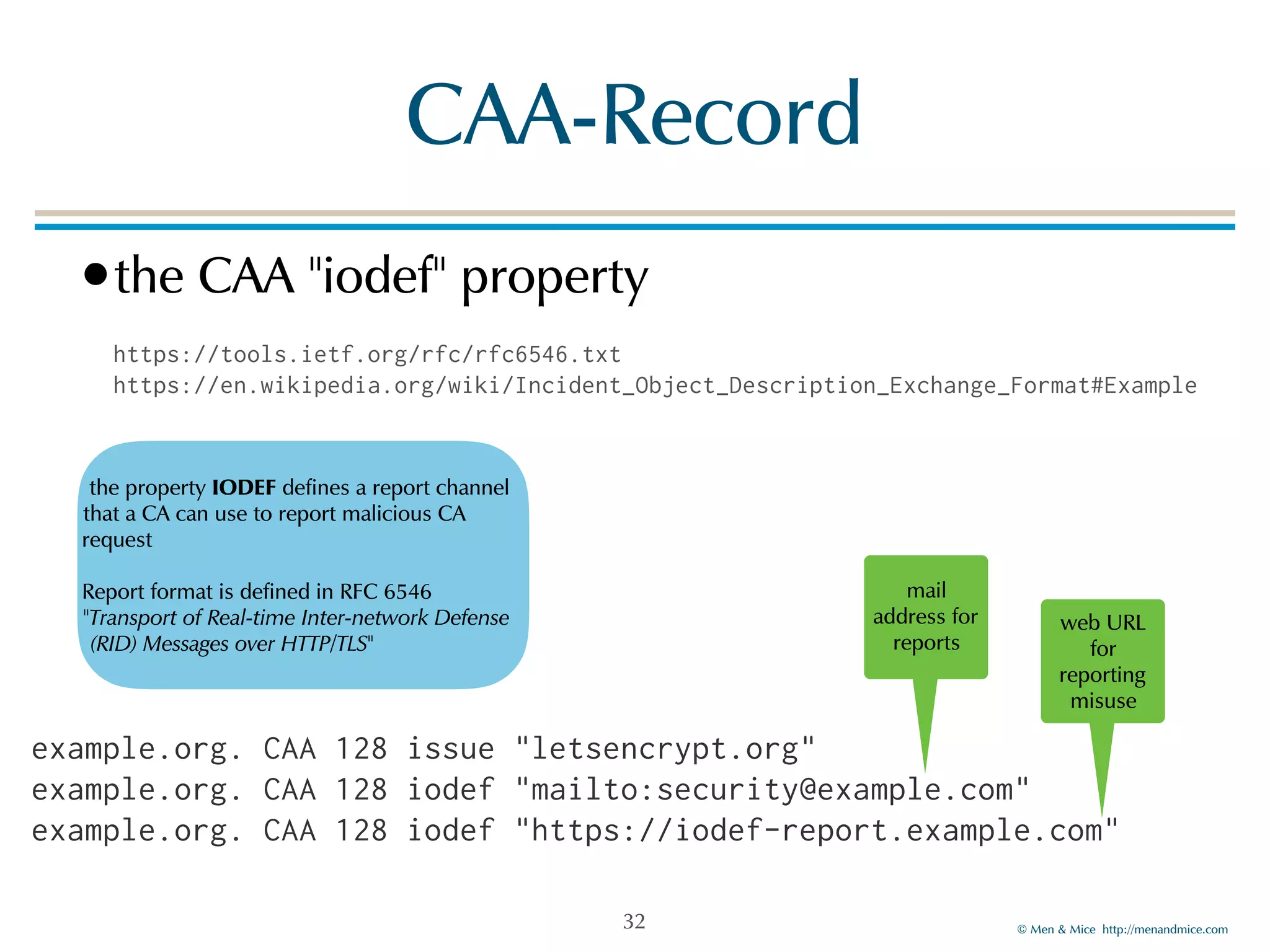
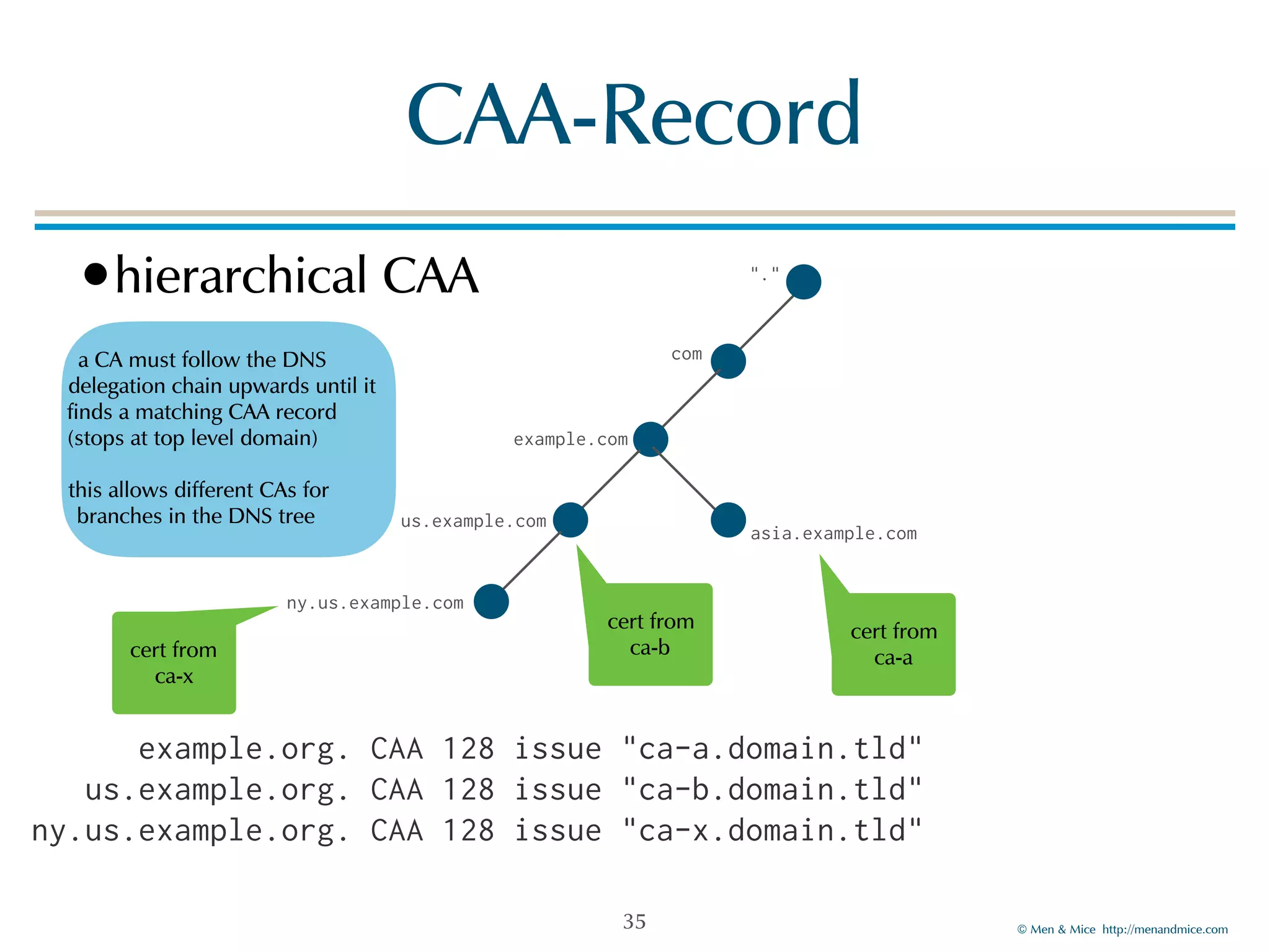
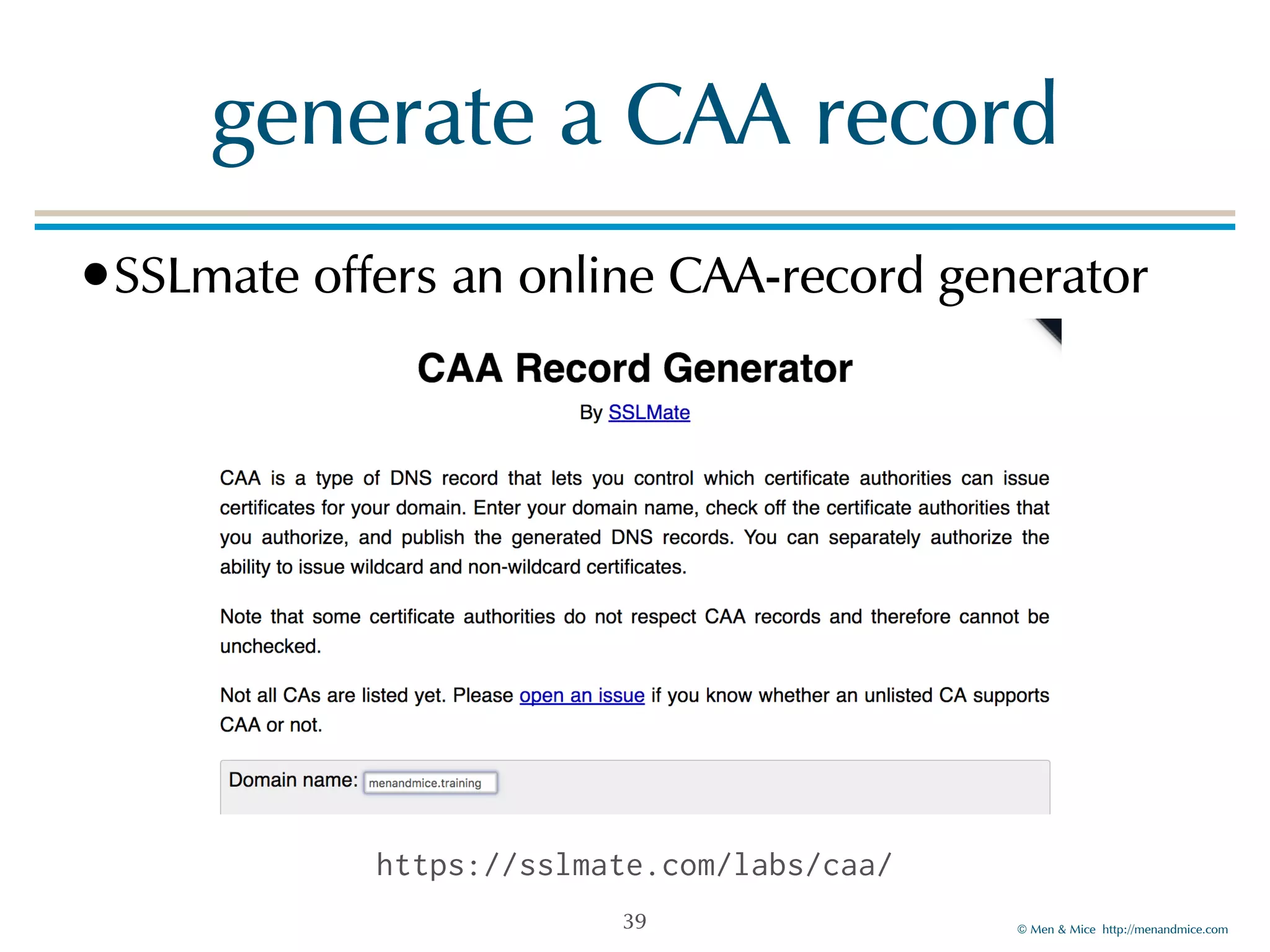
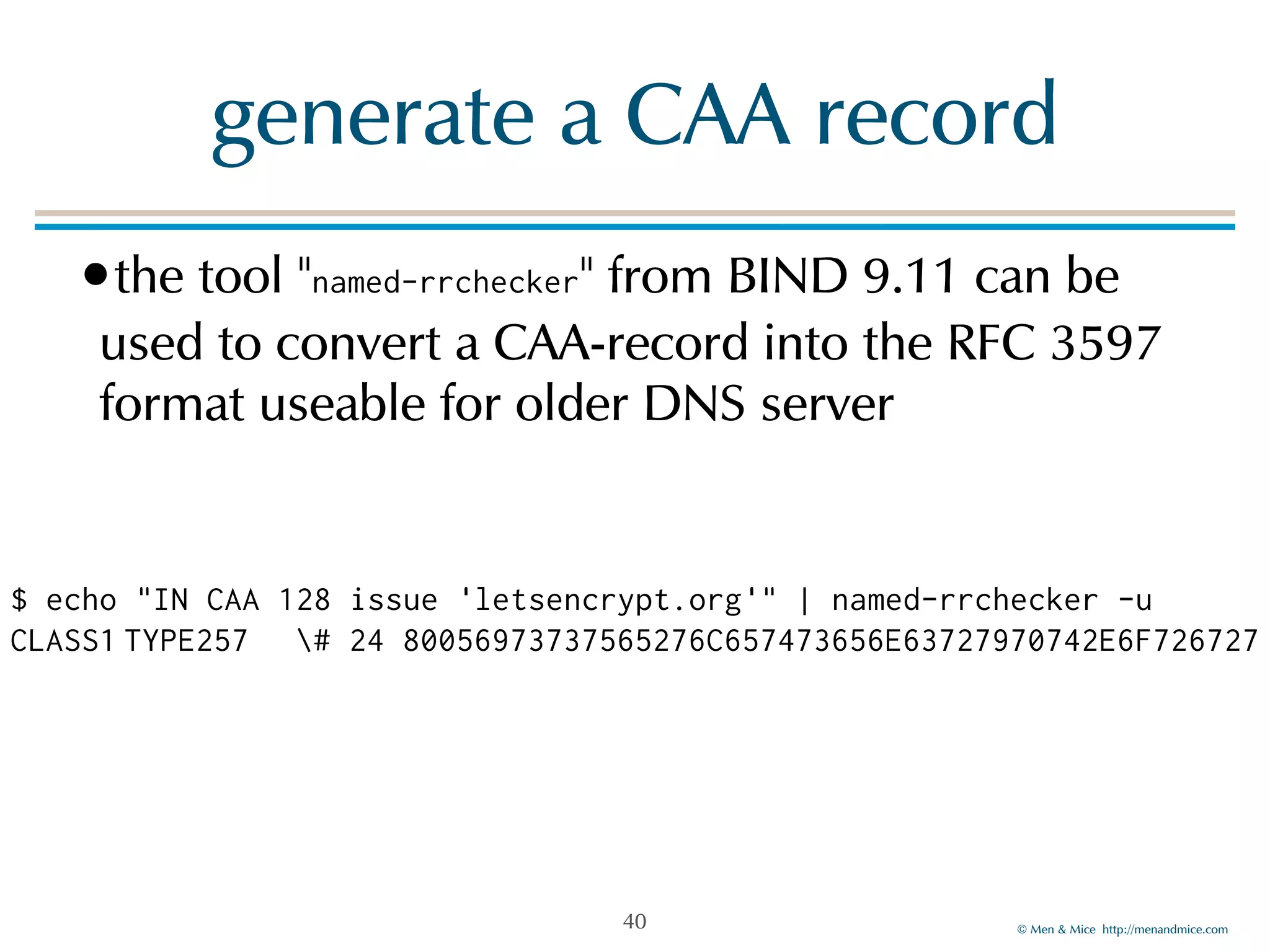
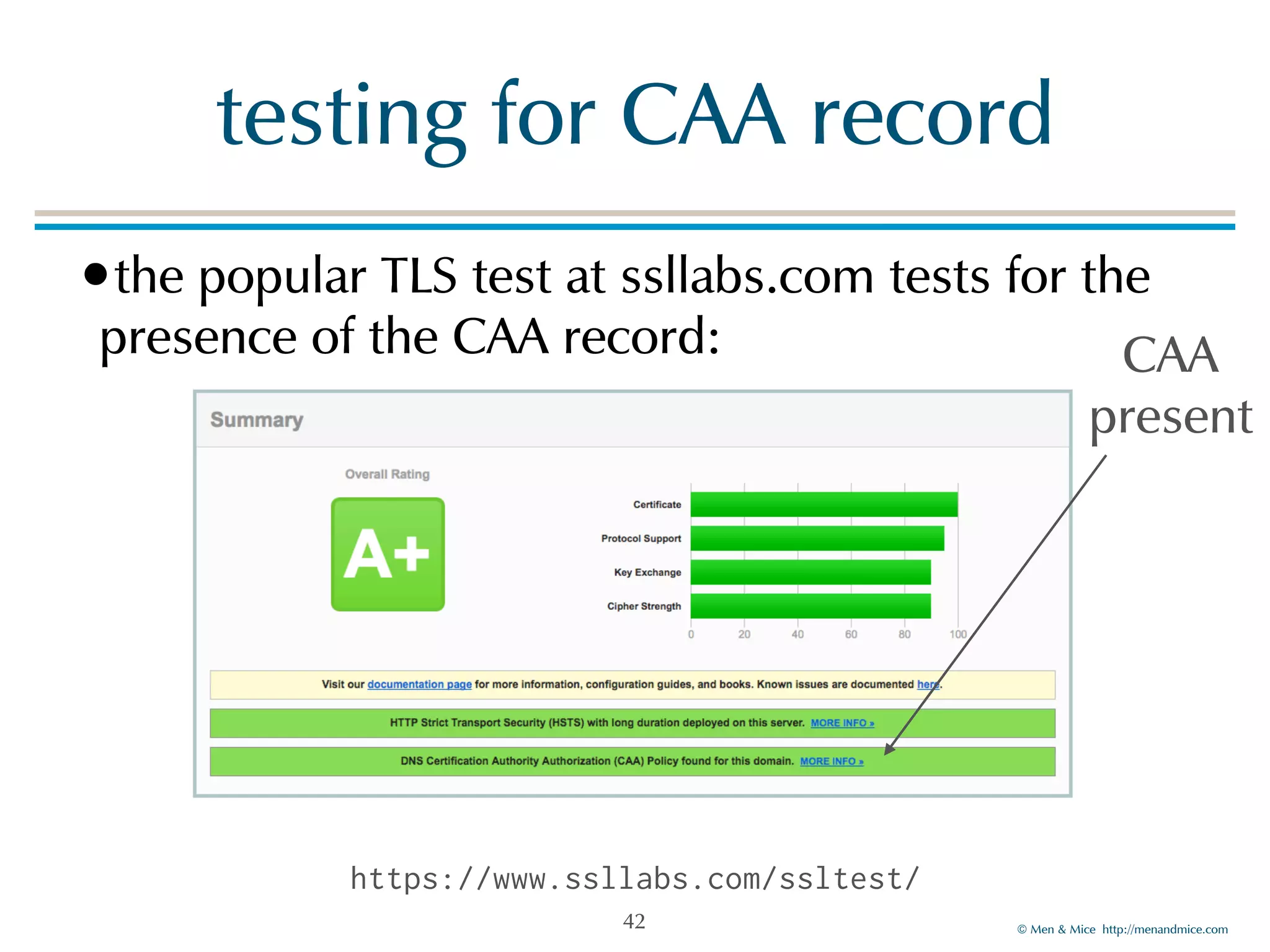
The document discusses the Certification Authority Authorization (CAA) record, which allows domain owners to specify which Certificate Authorities (CAs) can issue certificates for their domains. Starting September 2017, CAs are required to check for CAA records prior to issuing certificates, enhancing security against mis-issuance. The document also details various CAA properties and their functions, deployment considerations, and the importance of securing CAA records with DNSSEC.