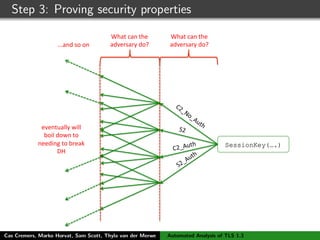
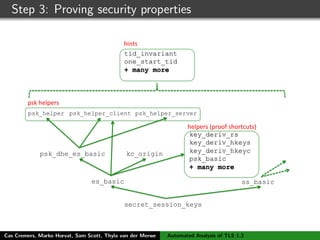
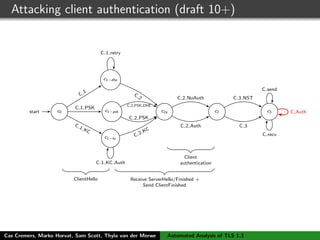
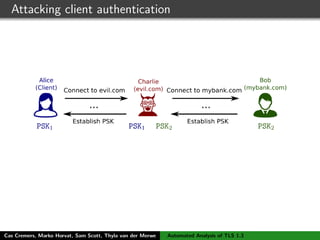
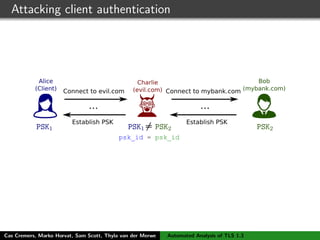
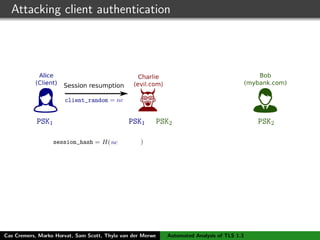
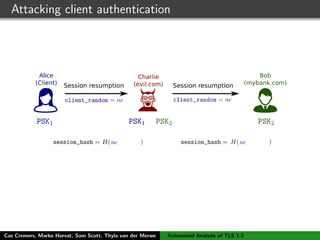
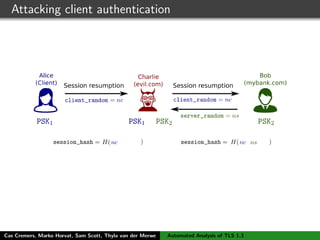
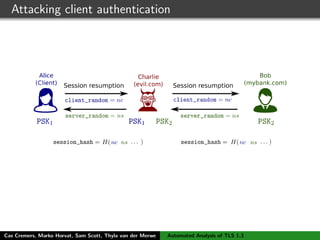
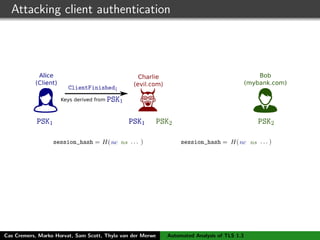
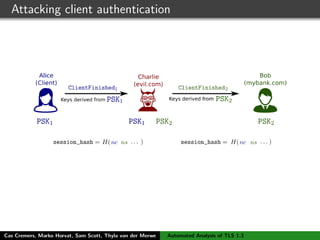
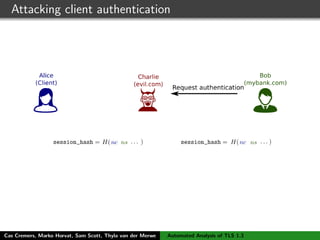
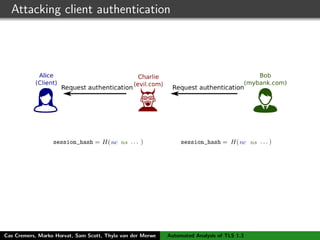
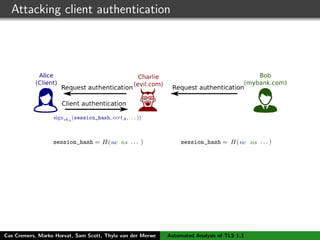
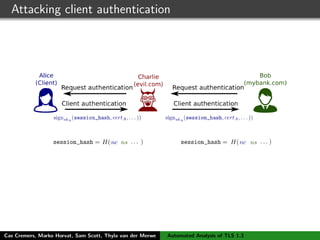
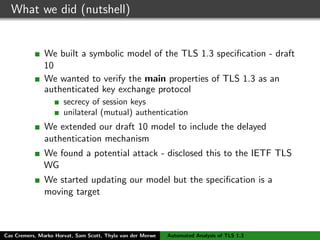
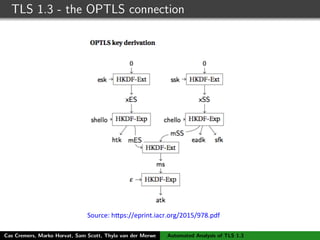
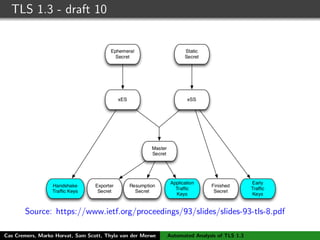
The authors built a symbolic model of the TLS 1.3 specification (draft 10) using the Tamarin prover to verify key properties like secrecy of session keys and unilateral/mutual authentication. They found a potential attack during this analysis and disclosed it to the IETF TLS working group. As the specification continued evolving, they started updating their model but noted it was a moving target.


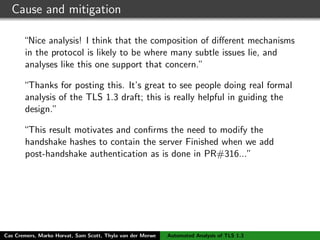
![TLS 1.3 - draft 10
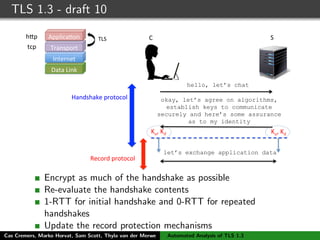
C S
ClientHello, ClientKeyShare
HelloRetryRequest
ClientHello, ClientKeyShare
ServerHello, ServerKeyShare, {EncryptedExtensions},
{ServerConfiguration*},{Certificate}, {CertificateRequest*},
{CertificateVerify}, {Finished}
{Certificate*}, {CertificateVerify*}, {Finished}
[Application data]
Initial (EC)DHE handshake
Cas Cremers, Marko Horvat, Sam Scott, Thyla van der Merwe Automated Analysis of TLS 1.3](https://image.slidesharecdn.com/tlsautomatedanalysis-160502175748/85/Automated-Analysis-of-TLS-1-3-10-320.jpg)
![TLS 1.3 - draft 10
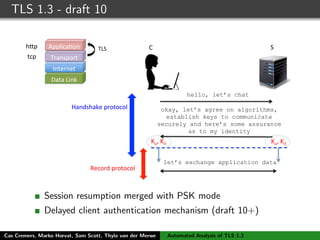
C S
ClientHello, ClientKeyShare, EarlyDataIndication,
(EncryptedExtensions), (Certificate*), (Certificate Verify*),
(ApplicationData)
ServerHello, ServerKeyShare, EarlyDataIndication,
{EncryptedExtensions}, {ServerConfiguration*},{Certificate}
{CertificateRequest*}, {CertificateVerify}, {Finished}
{Finished}
[Application data]
0-RTT handshake
Cas Cremers, Marko Horvat, Sam Scott, Thyla van der Merwe Automated Analysis of TLS 1.3](https://image.slidesharecdn.com/tlsautomatedanalysis-160502175748/85/Automated-Analysis-of-TLS-1-3-11-320.jpg)
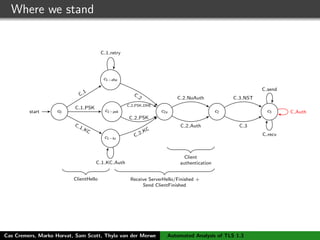
![TLS 1.3 - draft 10
C S
Initial handshake (see Figure (a))
[NewSessionTicket]
[Application data]
ClientHello, ClientKeyShare, PreSharedKeyExtension
ServerHello, PreSharedKeyExtension,
{EncryptedExtensions}, {Finished}
{Finished}
[Application data]
PSK-resumption handshake
Cas Cremers, Marko Horvat, Sam Scott, Thyla van der Merwe Automated Analysis of TLS 1.3](https://image.slidesharecdn.com/tlsautomatedanalysis-160502175748/85/Automated-Analysis-of-TLS-1-3-12-320.jpg)
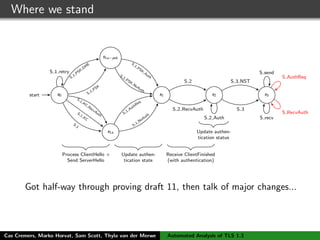
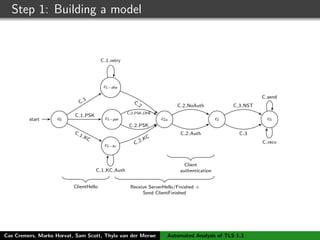
![TLS 1.3 - draft 10
C S
ClientHello, ClientKeyShare
HelloRetryRequest
ClientHello, ClientKeyShare
ServerHello, ServerKeyShare, {EncryptedExtensions},
{ServerConfiguration*},{Certificate}, {CertificateRequest*},
{CertificateVerify}, {Finished}
{Certificate*}, {CertificateVerify*}, {Finished}
[Application data]
(a) Initial (EC)DHE handshake
C S
ClientHello, ClientKeyShare, EarlyDataIndication,
(EncryptedExtensions), (Certificate*), (Certificate Verify*),
(ApplicationData)
ServerHello, ServerKeyShare, EarlyDataIndication,
{EncryptedExtensions}, {ServerConfiguration*},{Certificate}
{CertificateRequest*}, {CertificateVerify}, {Finished}
{Finished}
[Application data]
(b) 0-RTT handshake
C S
Initial handshake (see Figure (a))
[NewSessionTicket]
[Application data]
ClientHello, ClientKeyShare, PreSharedKeyExtension
ServerHello, PreSharedKeyExtension,
{EncryptedExtensions}, {Finished}
{Finished}
[Application data]
(c) PSK-resumption handshake
(+ PSK-DHE)
Look at the full interaction of all these components!
Cas Cremers, Marko Horvat, Sam Scott, Thyla van der Merwe Automated Analysis of TLS 1.3](https://image.slidesharecdn.com/tlsautomatedanalysis-160502175748/85/Automated-Analysis-of-TLS-1-3-15-320.jpg)
![TLS 1.3 - draft 10
C S
ClientHello, ClientKeyShare
HelloRetryRequest
ClientHello, ClientKeyShare
ServerHello, ServerKeyShare, {EncryptedExtensions},
{ServerConfiguration*},{Certificate}, {CertificateRequest*},
{CertificateVerify}, {Finished}
{Certificate*}, {CertificateVerify*}, {Finished}
[Application data]
(a) Initial (EC)DHE handshake
C S
ClientHello, ClientKeyShare, EarlyDataIndication,
(EncryptedExtensions), (Certificate*), (Certificate Verify*),
(ApplicationData)
ServerHello, ServerKeyShare, EarlyDataIndication,
{EncryptedExtensions}, {ServerConfiguration*},{Certificate}
{CertificateRequest*}, {CertificateVerify}, {Finished}
{Finished}
[Application data]
(b) 0-RTT handshake
C S
Initial handshake (see Figure (a))
[NewSessionTicket]
[Application data]
ClientHello, ClientKeyShare, PreSharedKeyExtension
ServerHello, PreSharedKeyExtension,
{EncryptedExtensions}, {Finished}
{Finished}
[Application data]
(c) PSK-resumption handshake
(+ PSK-DHE)
Look at the full interaction of all these components!
Cas Cremers, Marko Horvat, Sam Scott, Thyla van der Merwe Automated Analysis of TLS 1.3](https://image.slidesharecdn.com/tlsautomatedanalysis-160502175748/85/Automated-Analysis-of-TLS-1-3-16-320.jpg)



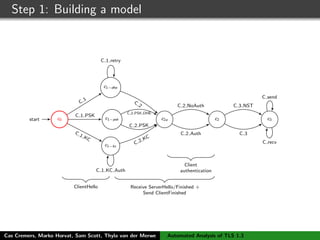
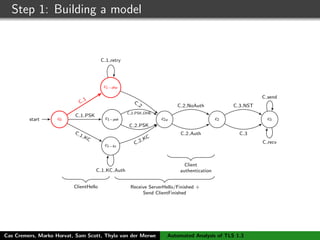
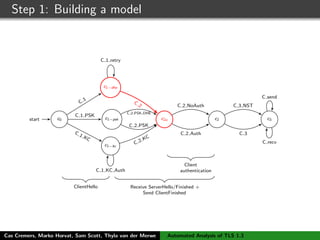
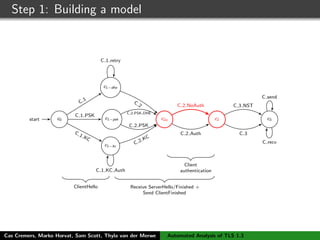
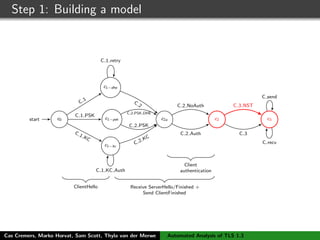
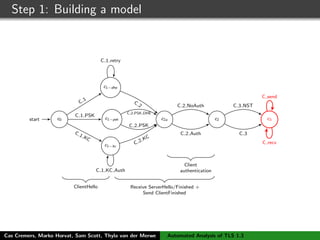
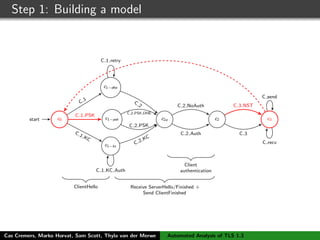
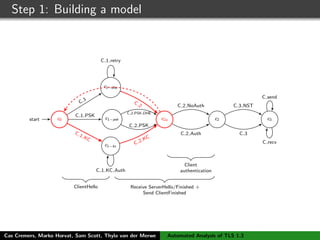
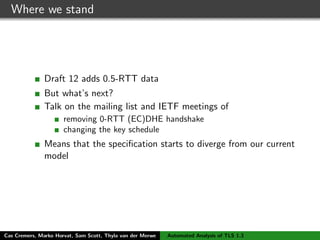
![Step 1: Building a model
rule C_1:
let
// Default C1 values
tid = ~nc
// Client Hello
C = $C
nc = ~nc
pc = $pc
S = $S
// Client Key Share
ga = ’g’^~a
messages = <nc, pc,ga>
in
[ Fr(nc)
, Fr(~a)
]
--[ C1(tid)
, Start(tid, C, ’client’)
, Running(C, S, ’client’, nc)
, DH(C, ~a)
]->
[ St_C_1_init(tid, C, nc, pc, S, ~a, messages, ’no_auth’)
, Out(<C,nc, pc,ga>)
]
Cas Cremers, Marko Horvat, Sam Scott, Thyla van der Merwe Automated Analysis of TLS 1.3](https://image.slidesharecdn.com/tlsautomatedanalysis-160502175748/85/Automated-Analysis-of-TLS-1-3-33-320.jpg)