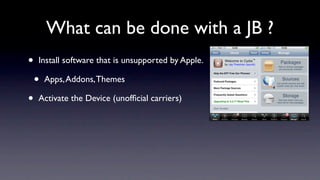
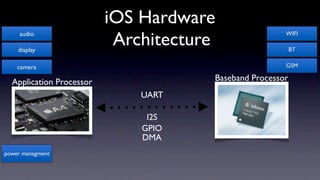
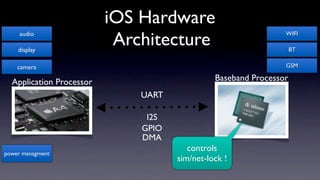
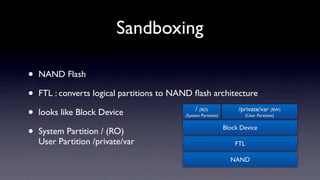
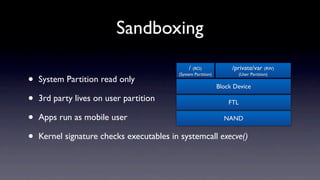
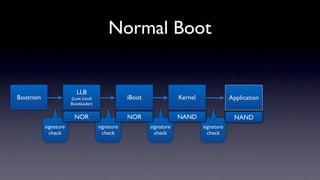
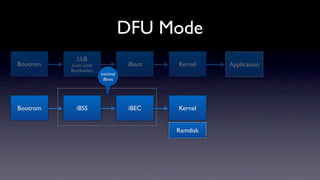
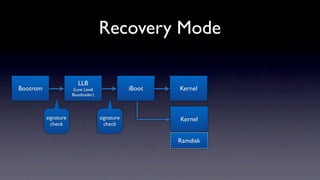
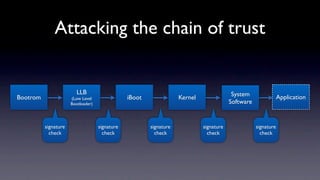
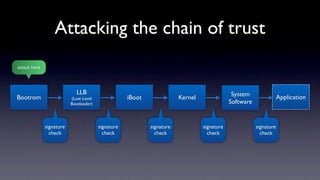
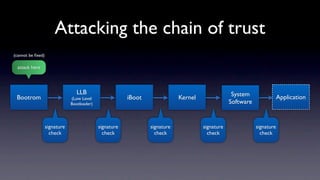
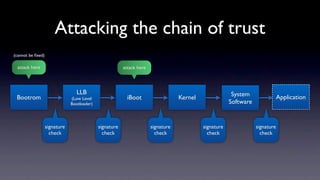
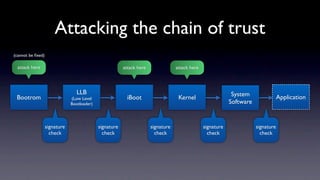
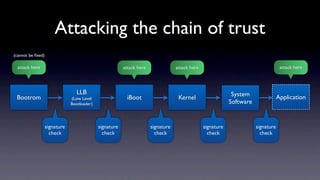
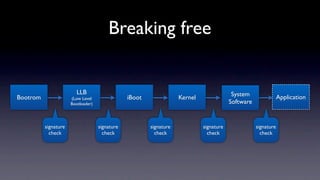
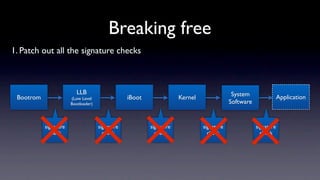
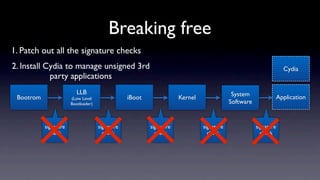
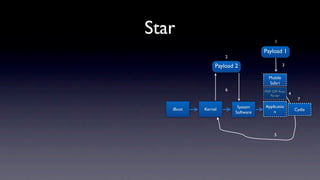
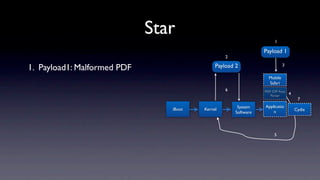
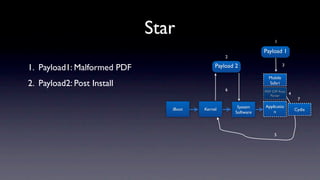
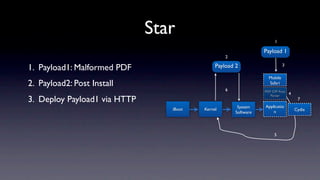
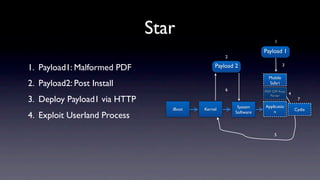
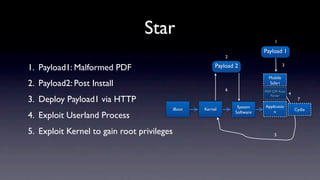
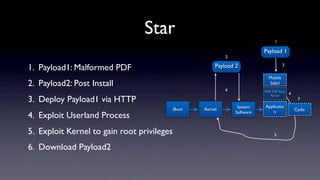
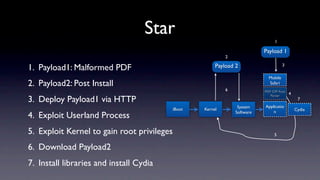
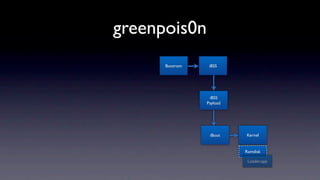
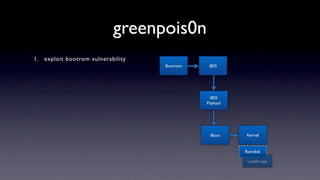
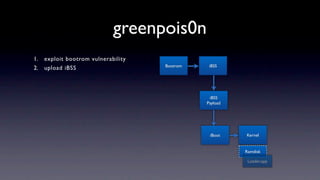
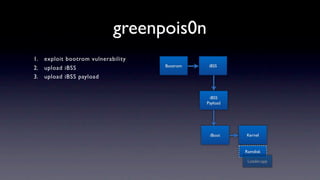
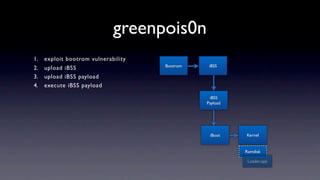
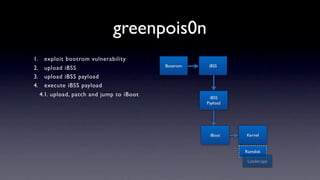
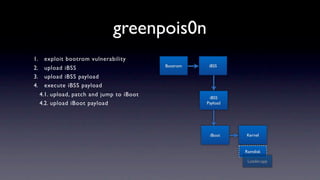
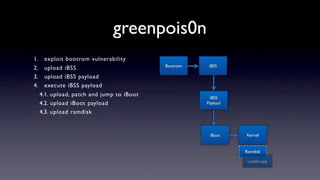
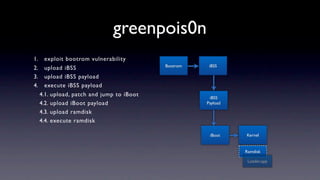
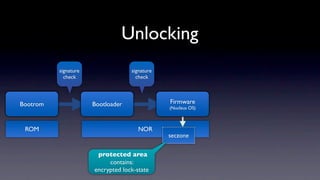
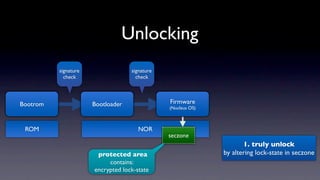
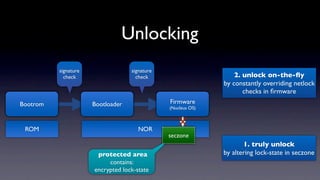
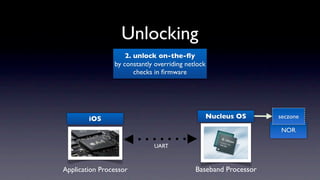
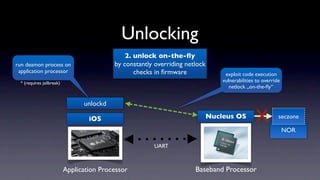
The document discusses jailbreaking iOS devices. It explains that jailbreaking removes security restrictions to allow installation of unauthorized third-party apps. It describes various jailbreaking tools and techniques, including exploiting vulnerabilities in the bootrom, iBoot, and kernel to bypass signature checks and install Cydia for managing third-party apps. Specific jailbreaking methods covered include the web-based Star jailbreak and the PC-based greenpois0n jailbreak.