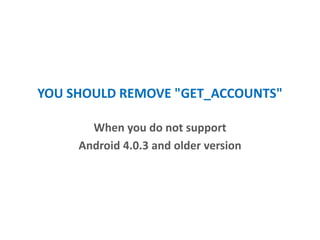
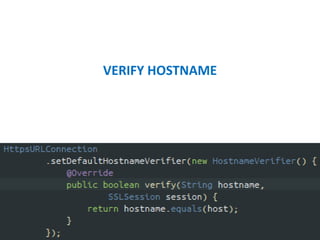
This document discusses various aspects of securing Android development including permissions, encryption, API management, and more. It addresses securing the USB, screen, clipboard, and databases. It recommends using Android NDK for cryptography to make analysis harder. API access should use randomly generated access tokens that are tied to the user ID and hardware ID and refreshed periodically. Encryption should be done with keys derived from random, hardware ID, and user-provided values.














![GETWINDOW().SETFLAGS(LAYOUTPARAMS.F
LAG_SECURE,
LAYOUTPARAMS.FLAG_SECURE);
It disable screen capture
• [POWER] + [VOL-DWN]
• OEM feature like SAMSUNG / HTC](https://image.slidesharecdn.com/androidsecuritydevelopment-141021010448-conversion-gate01/85/Android-Security-Development-16-320.jpg)