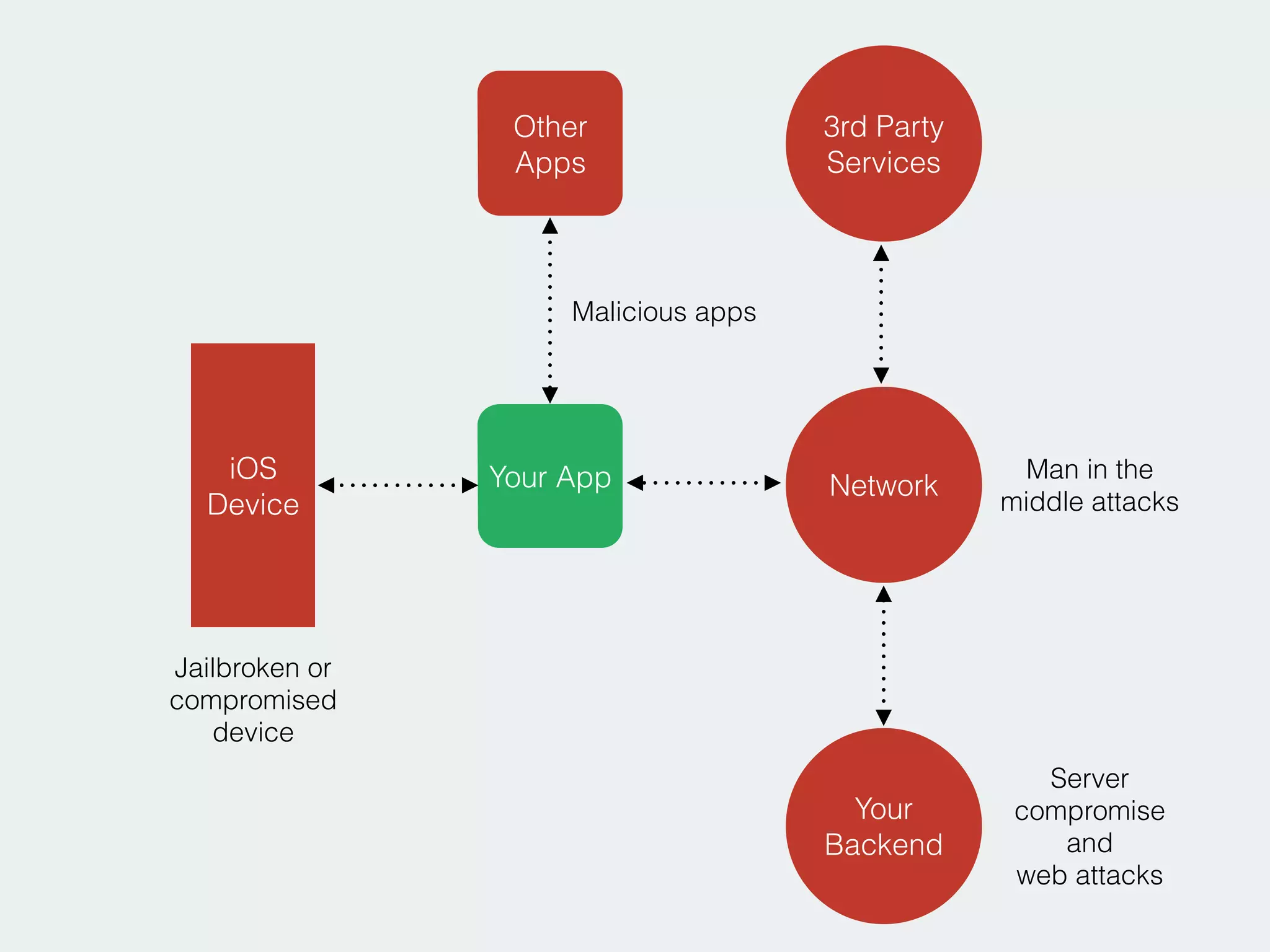
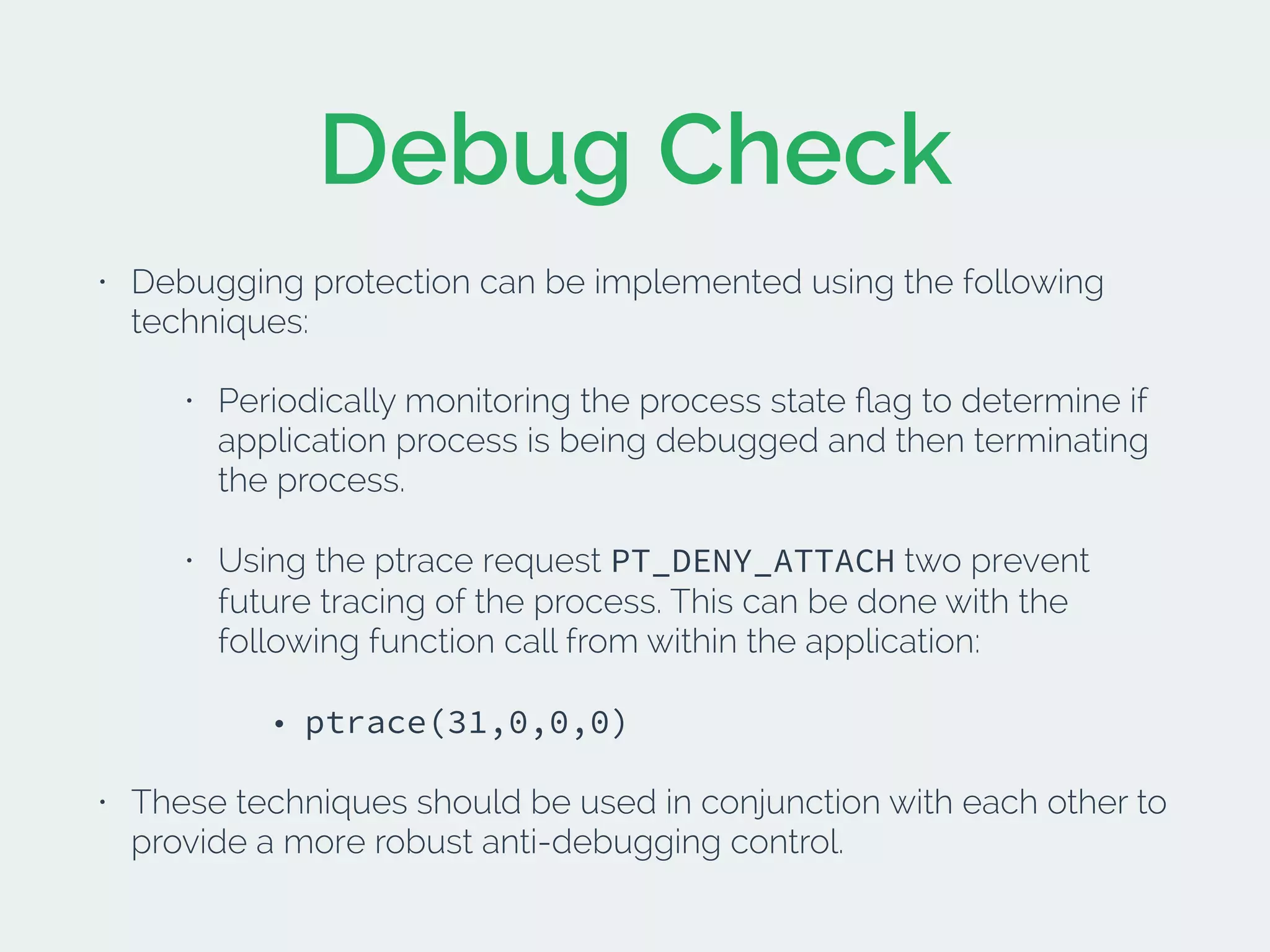
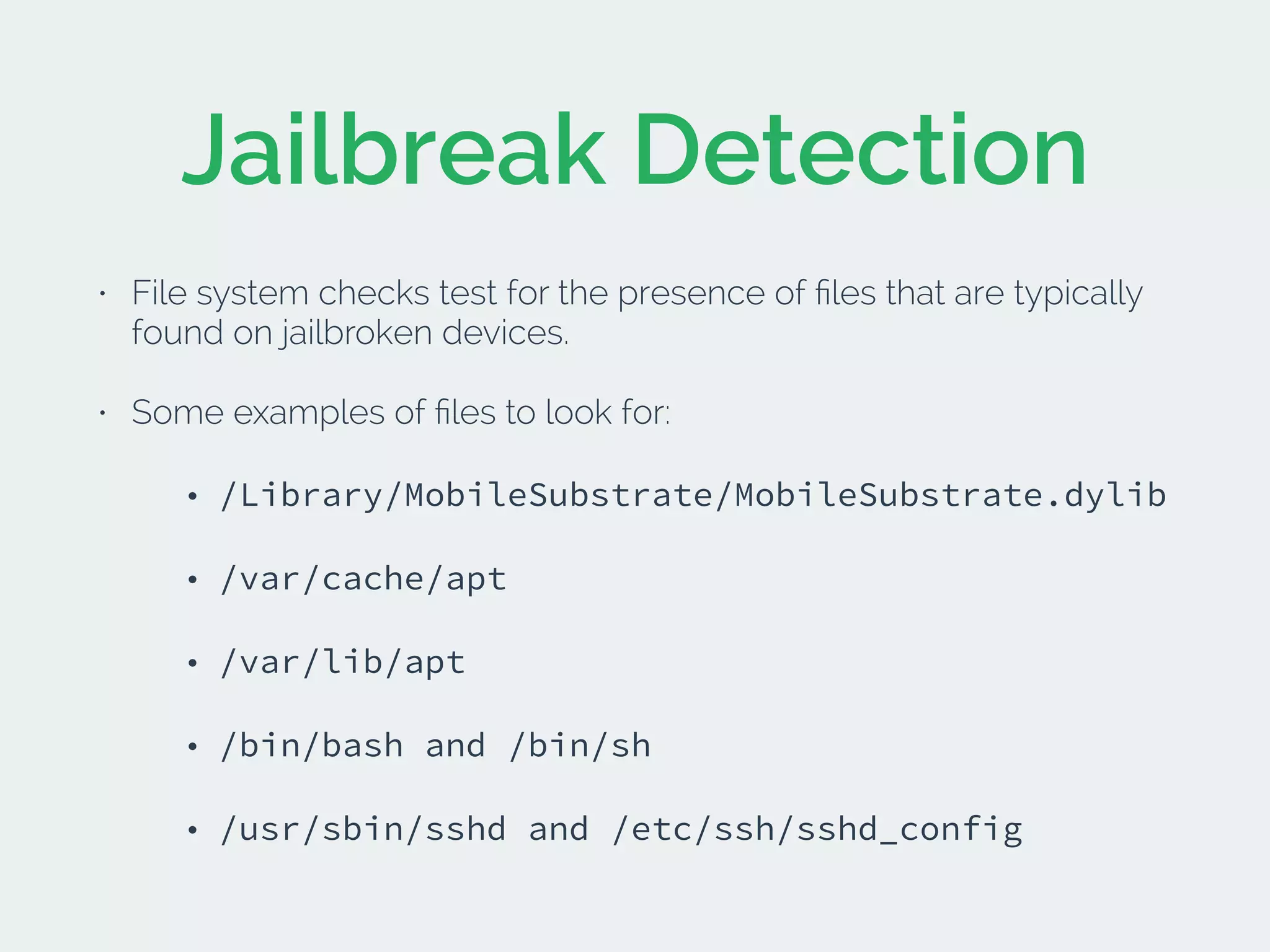
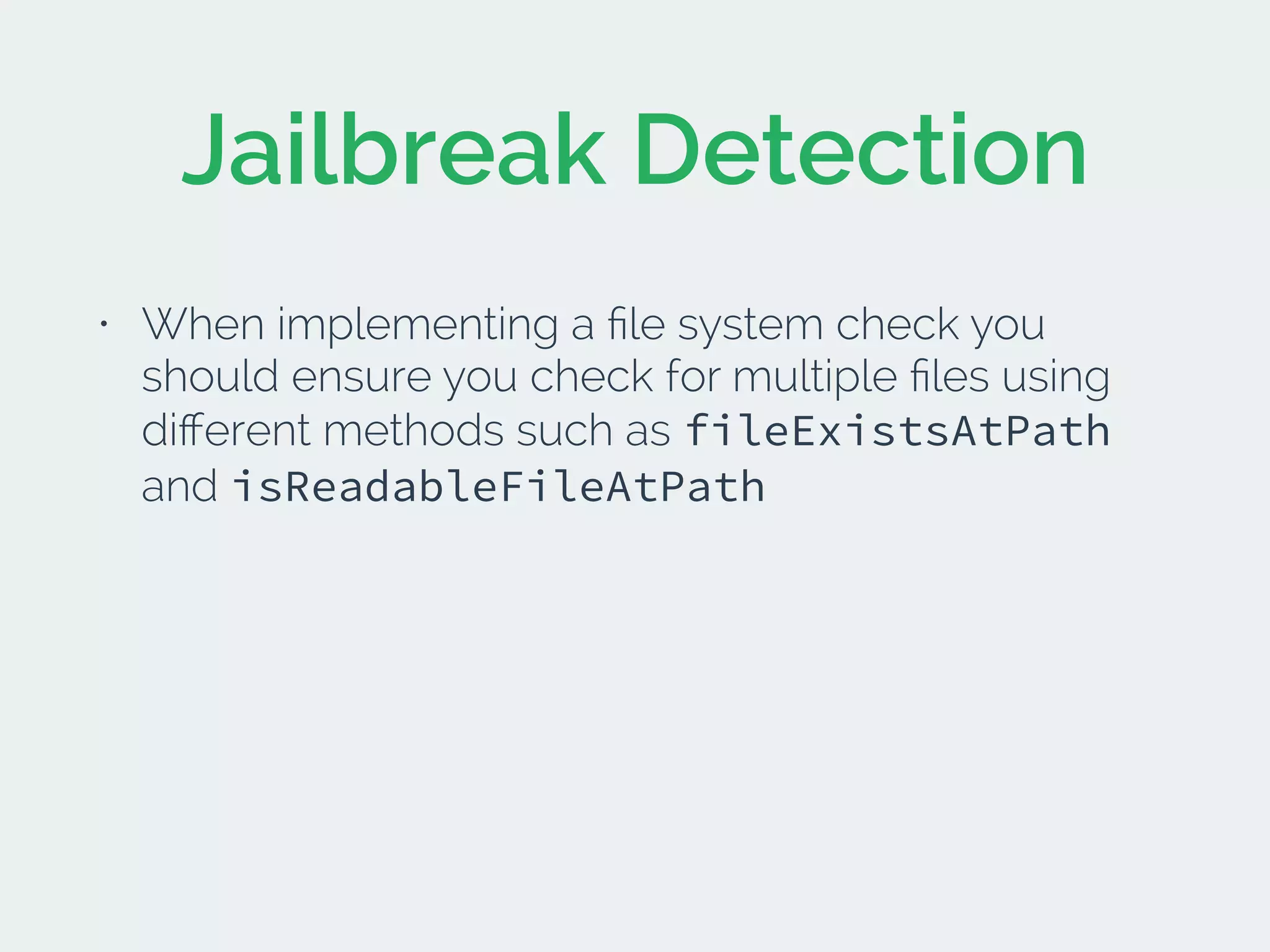
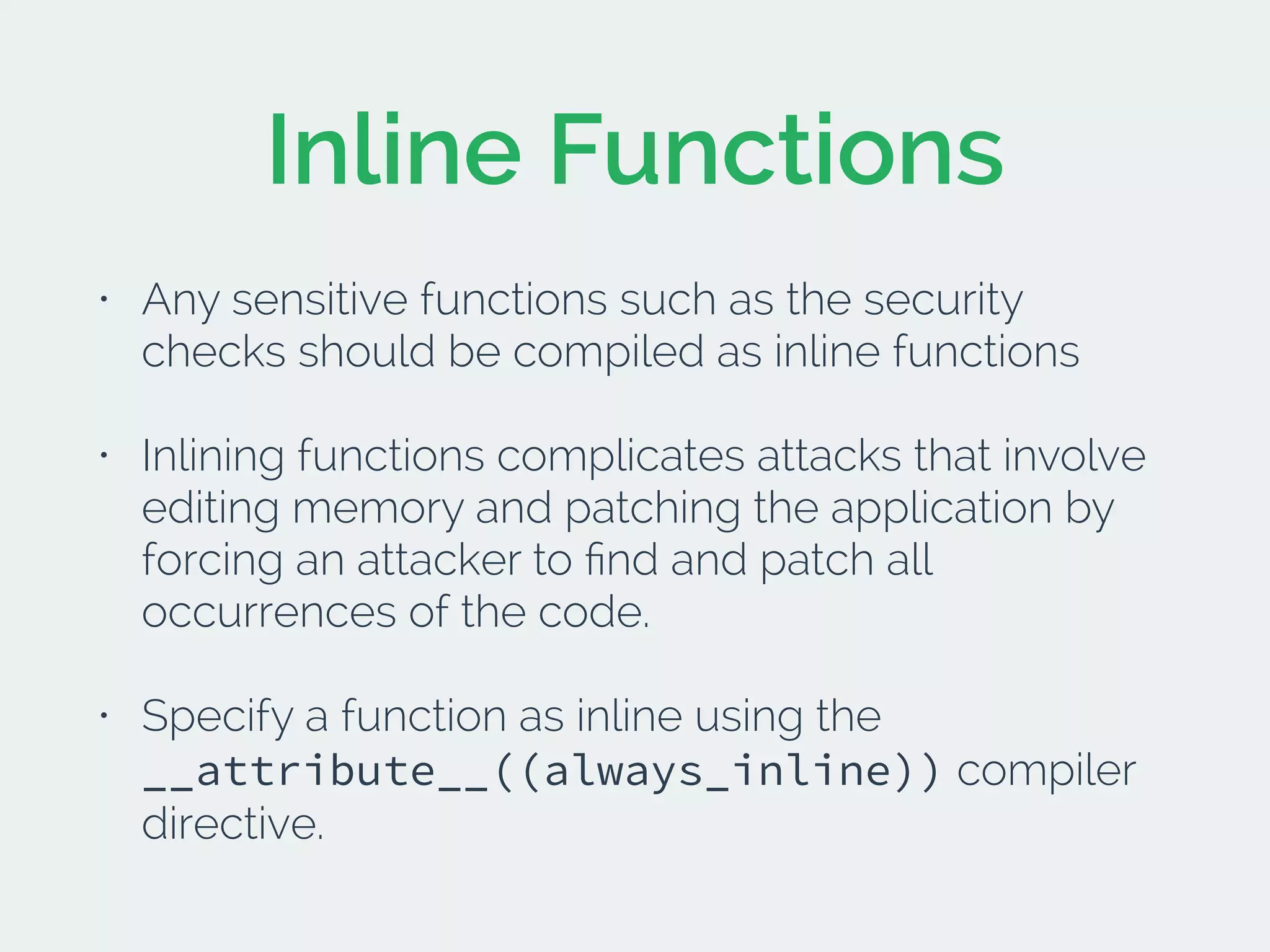
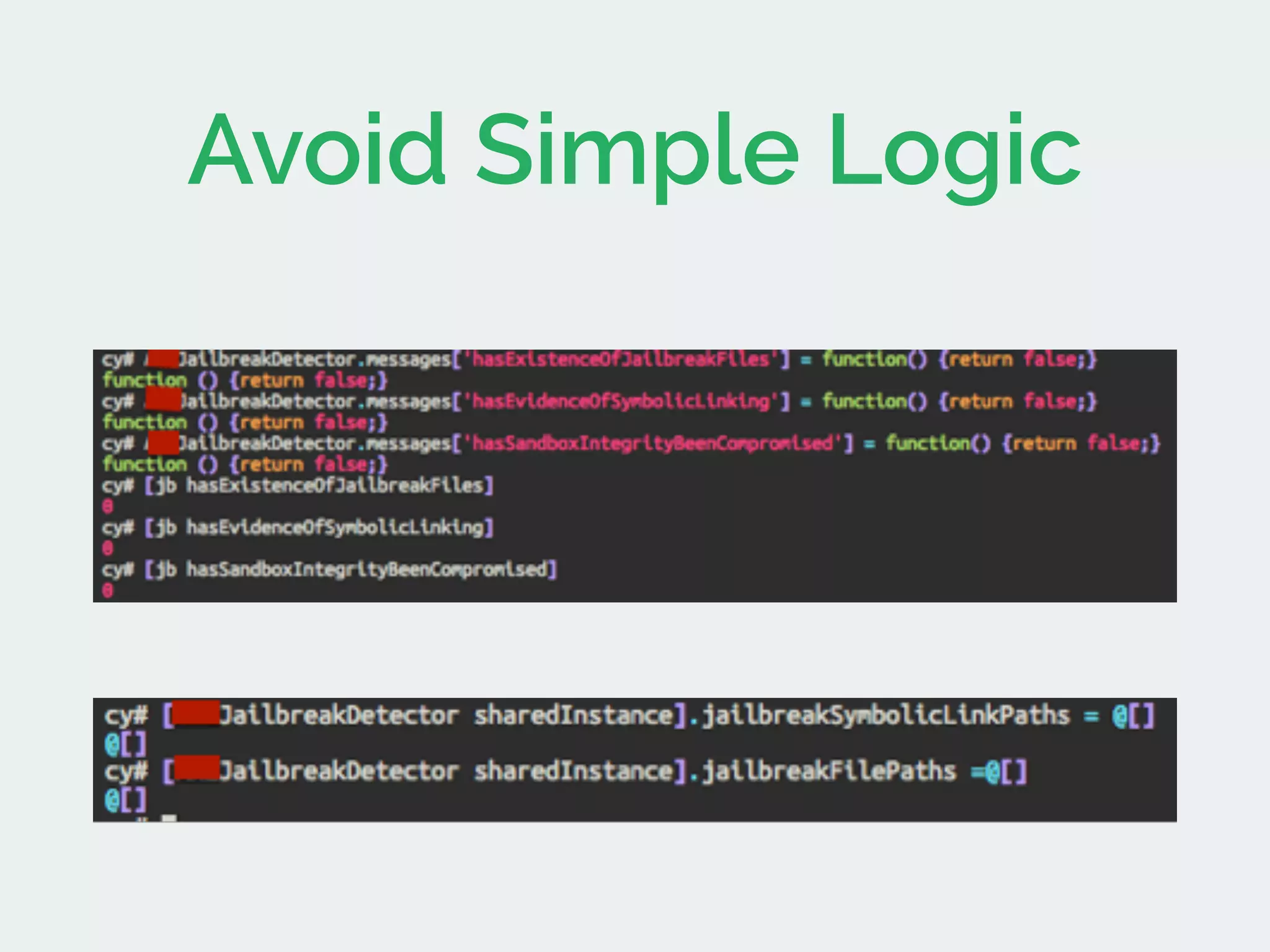
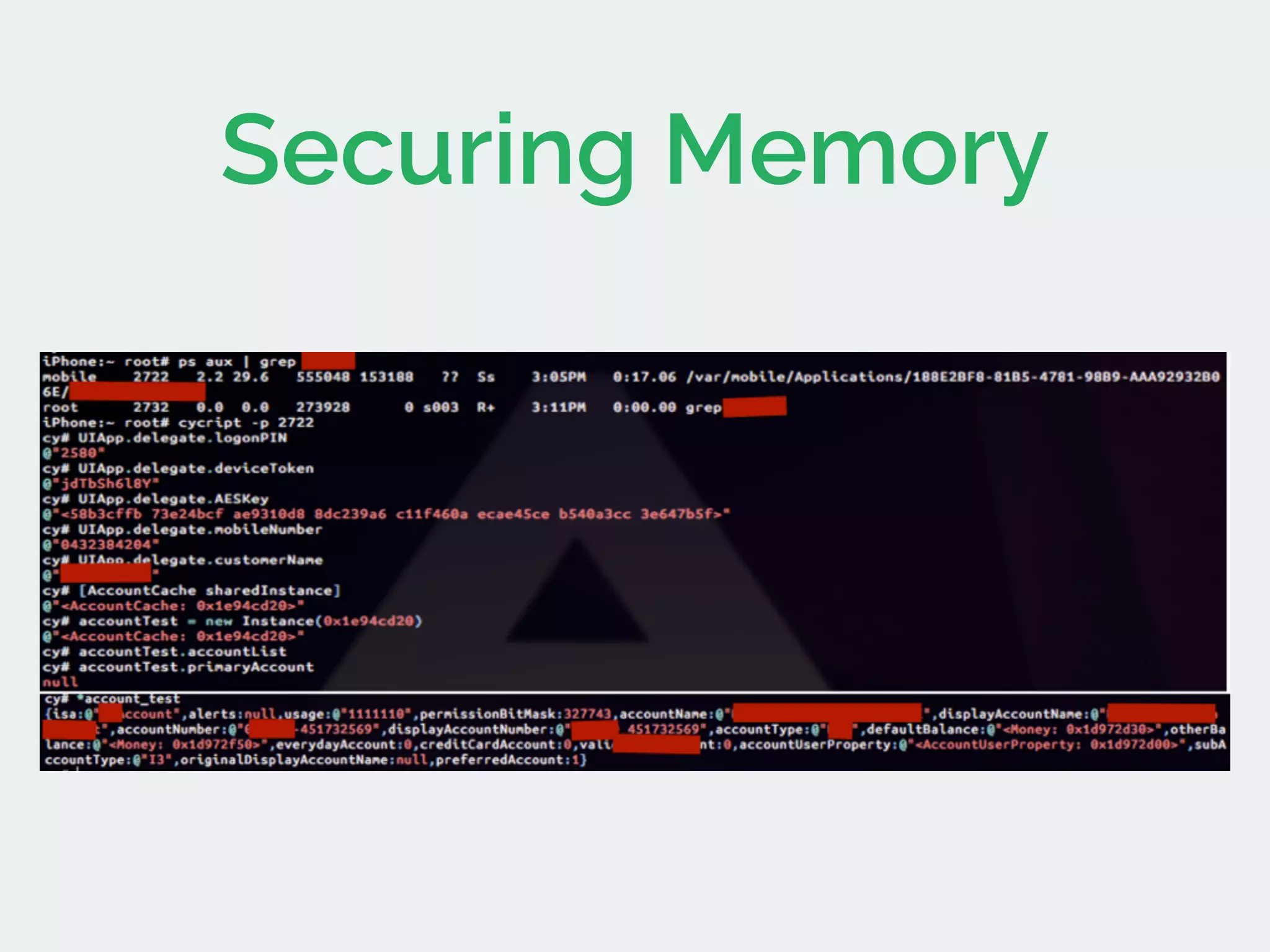
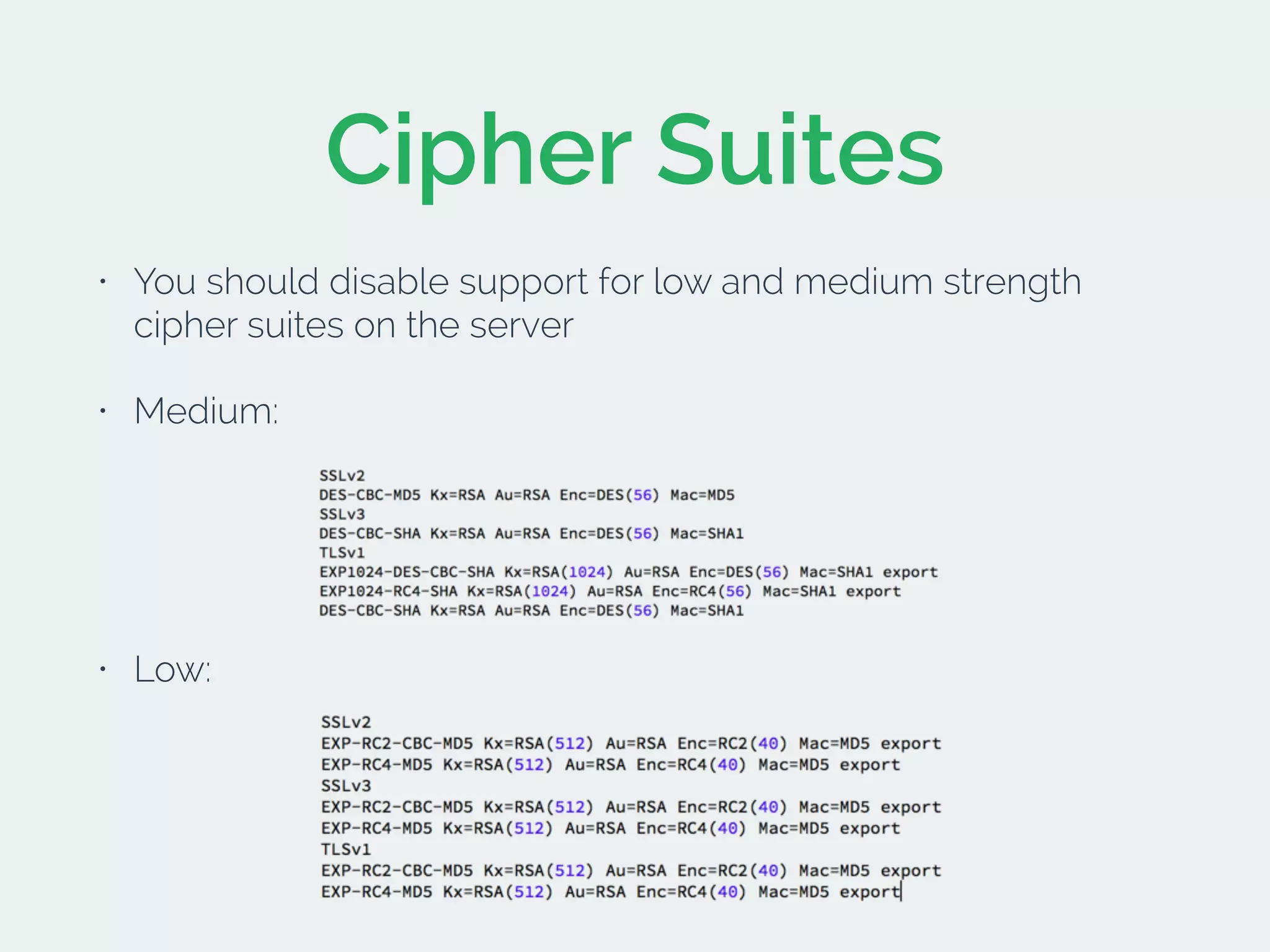
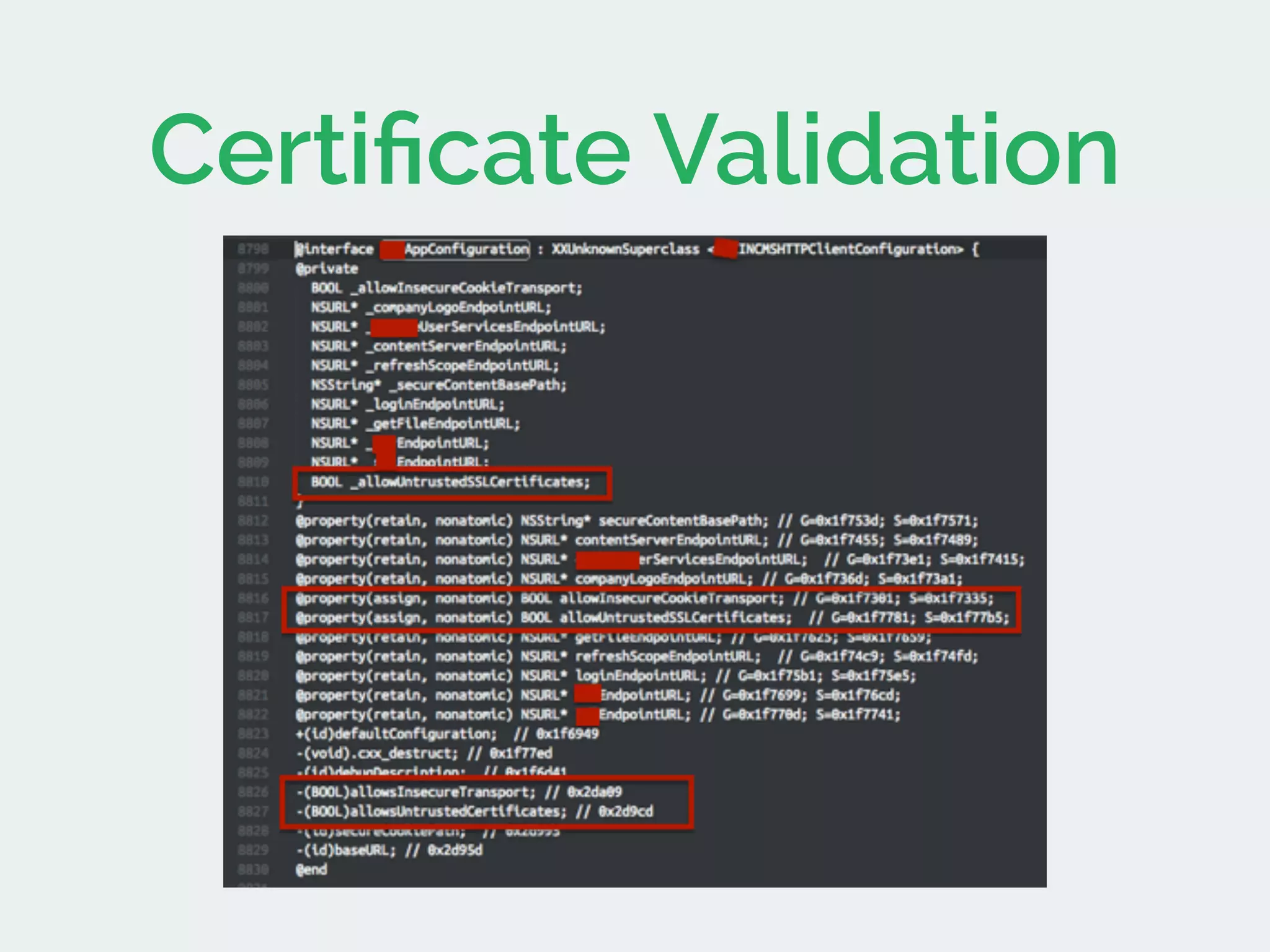
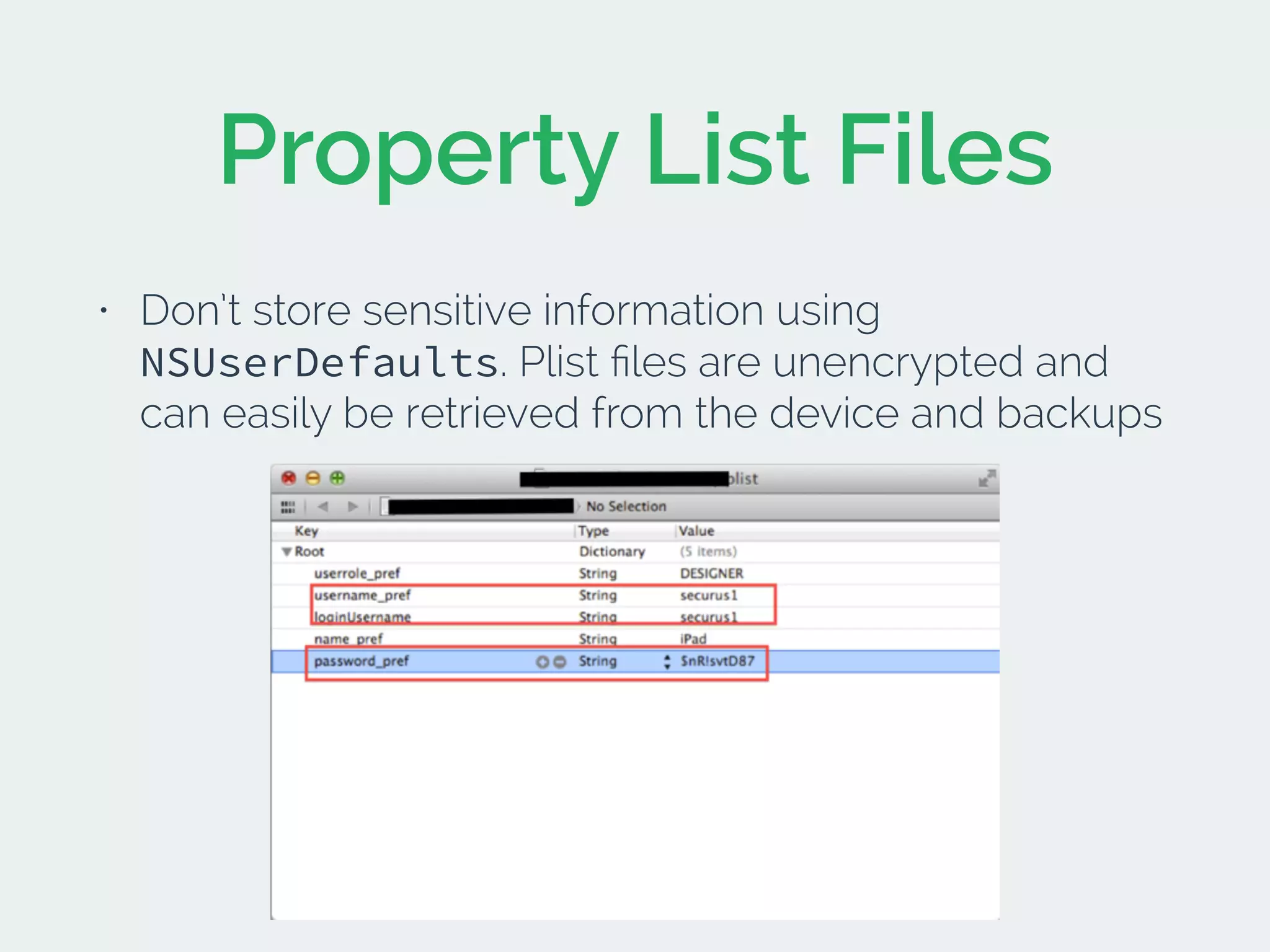
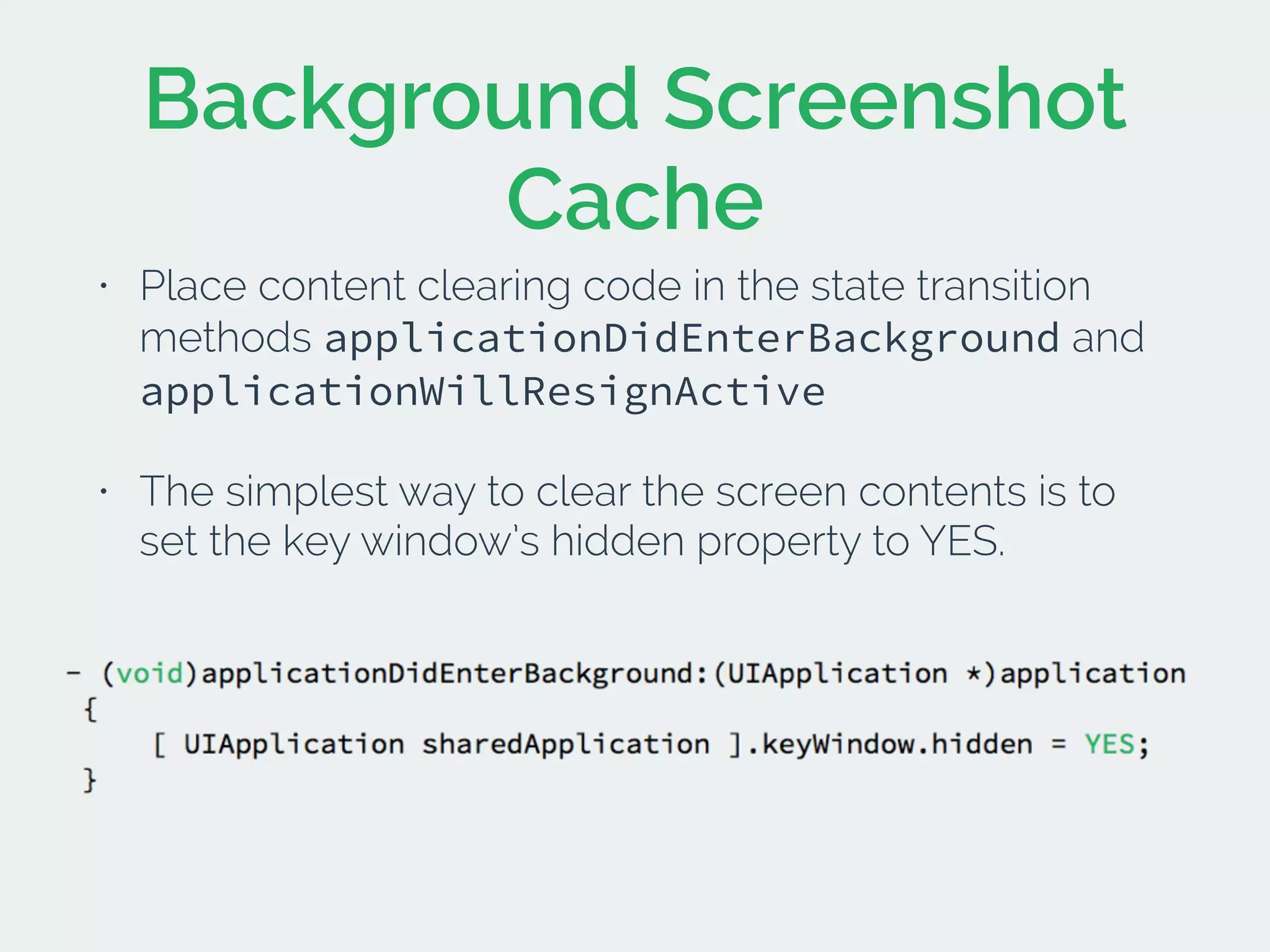
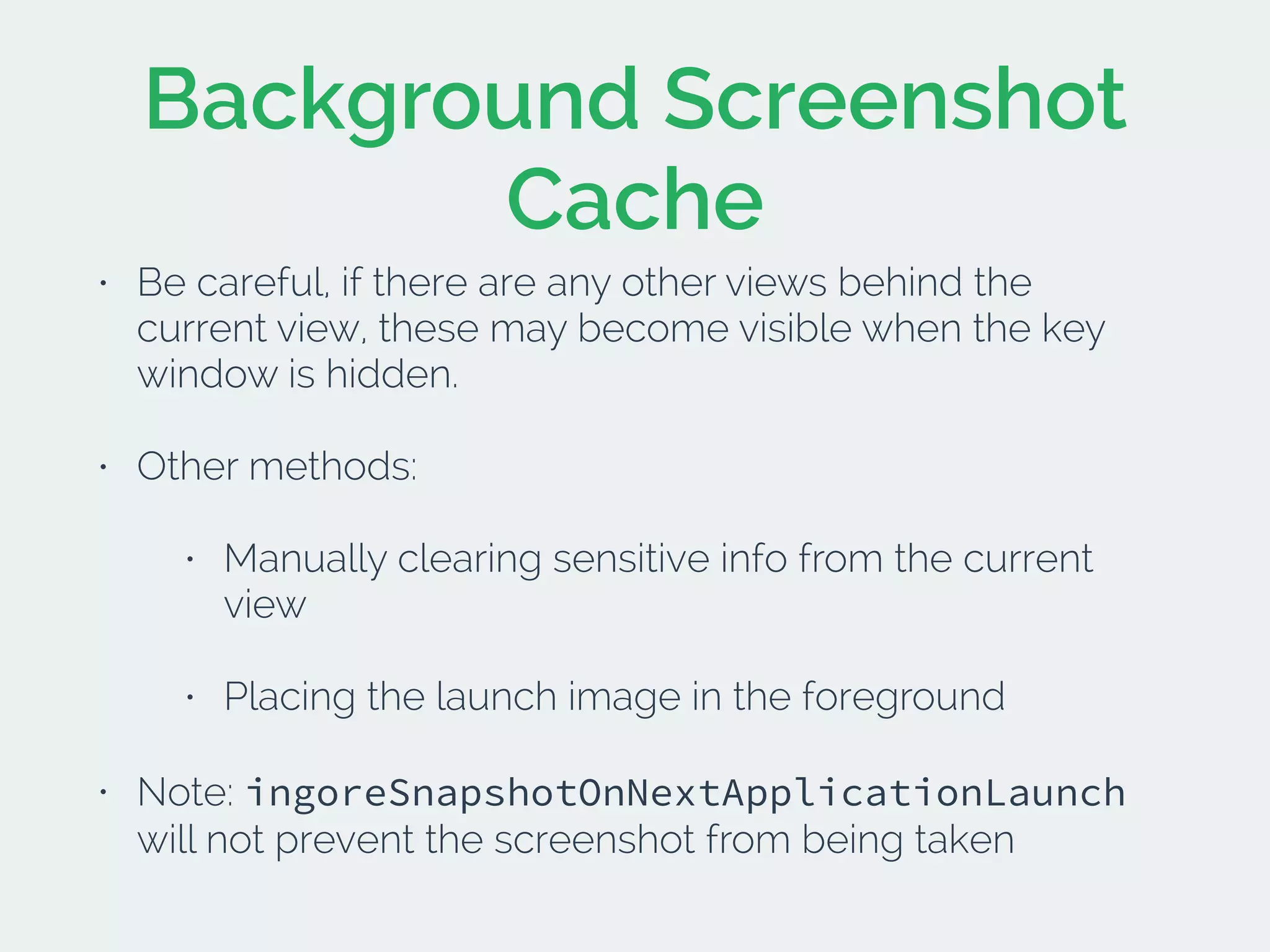
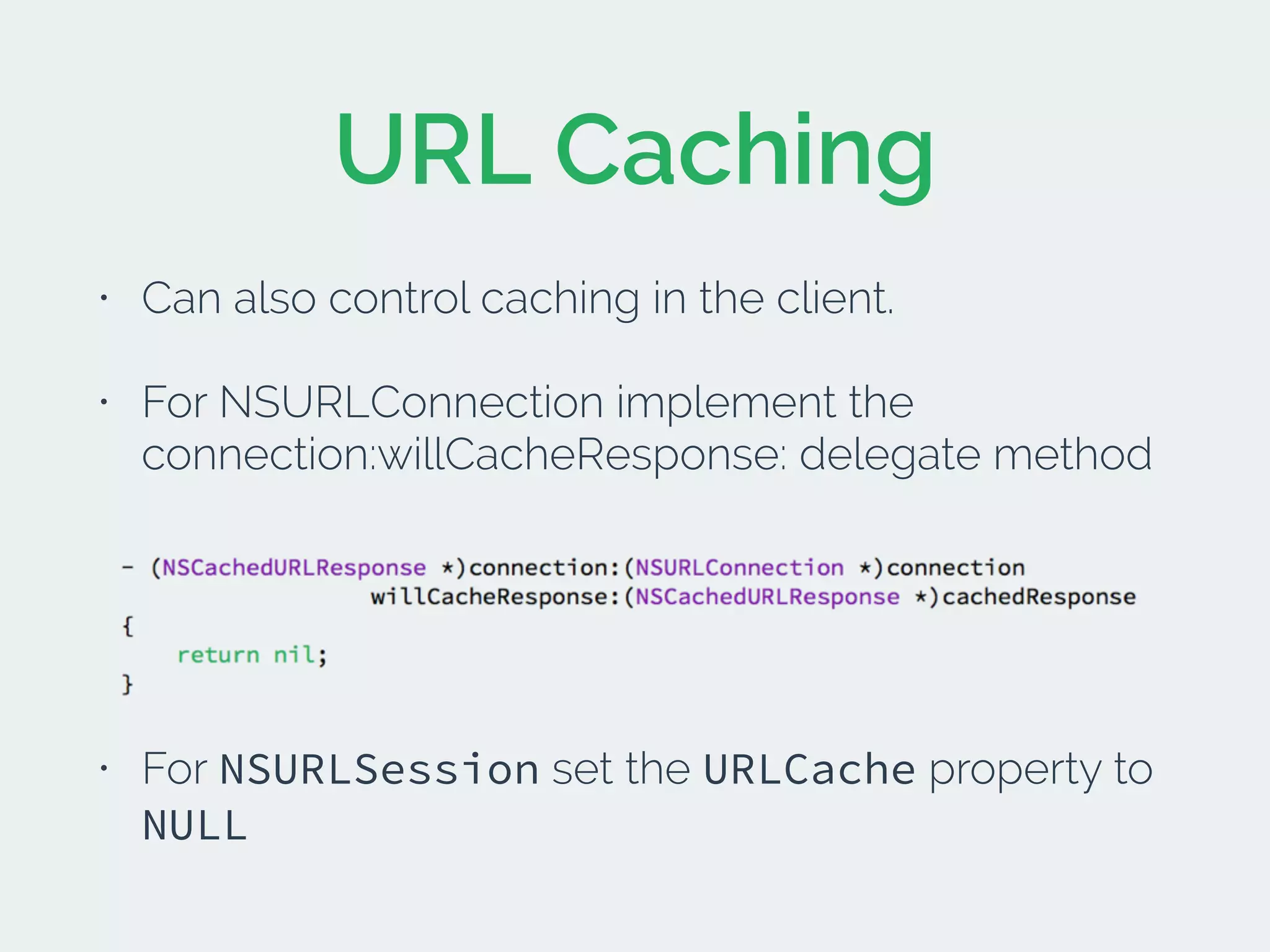
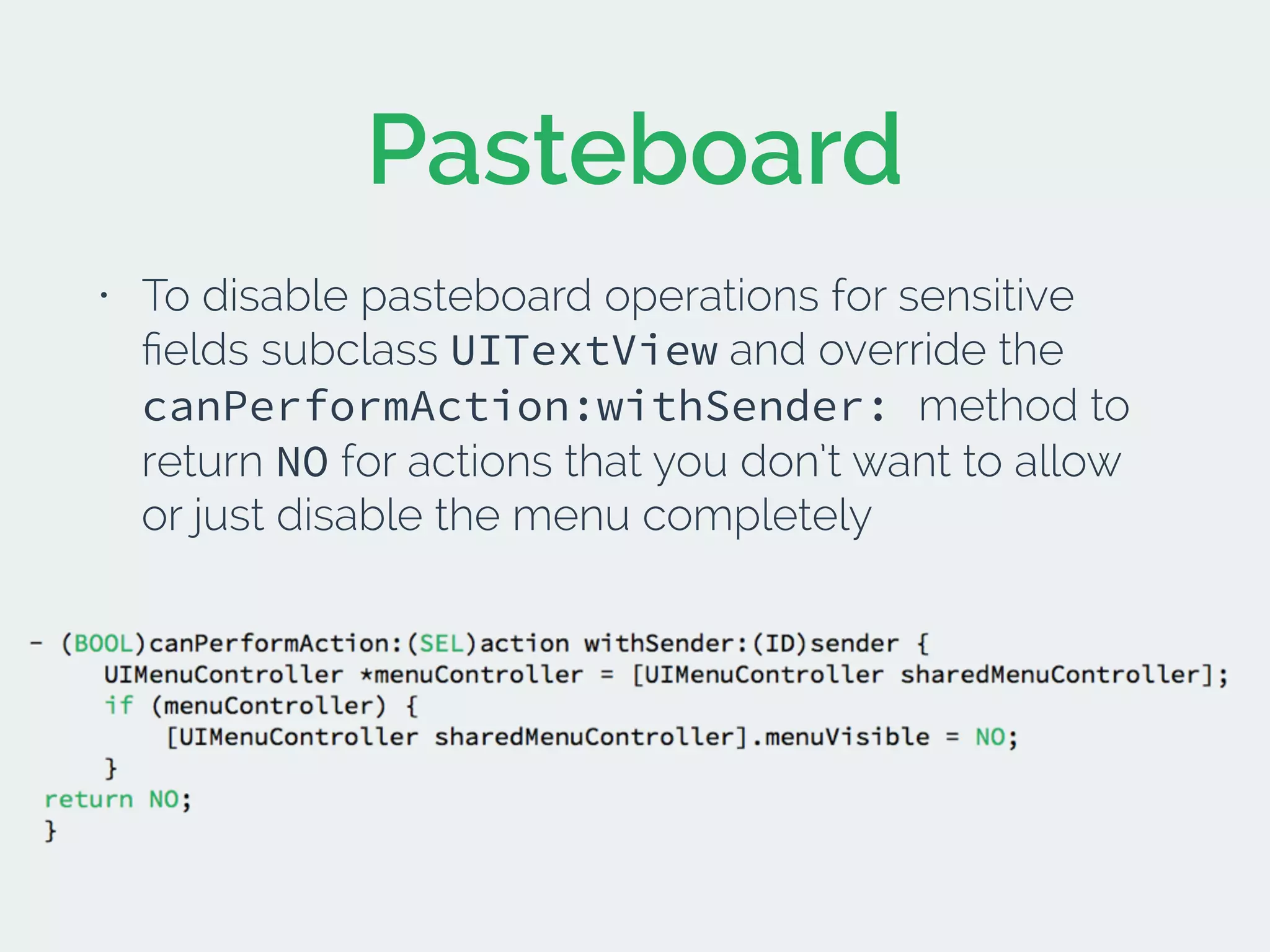
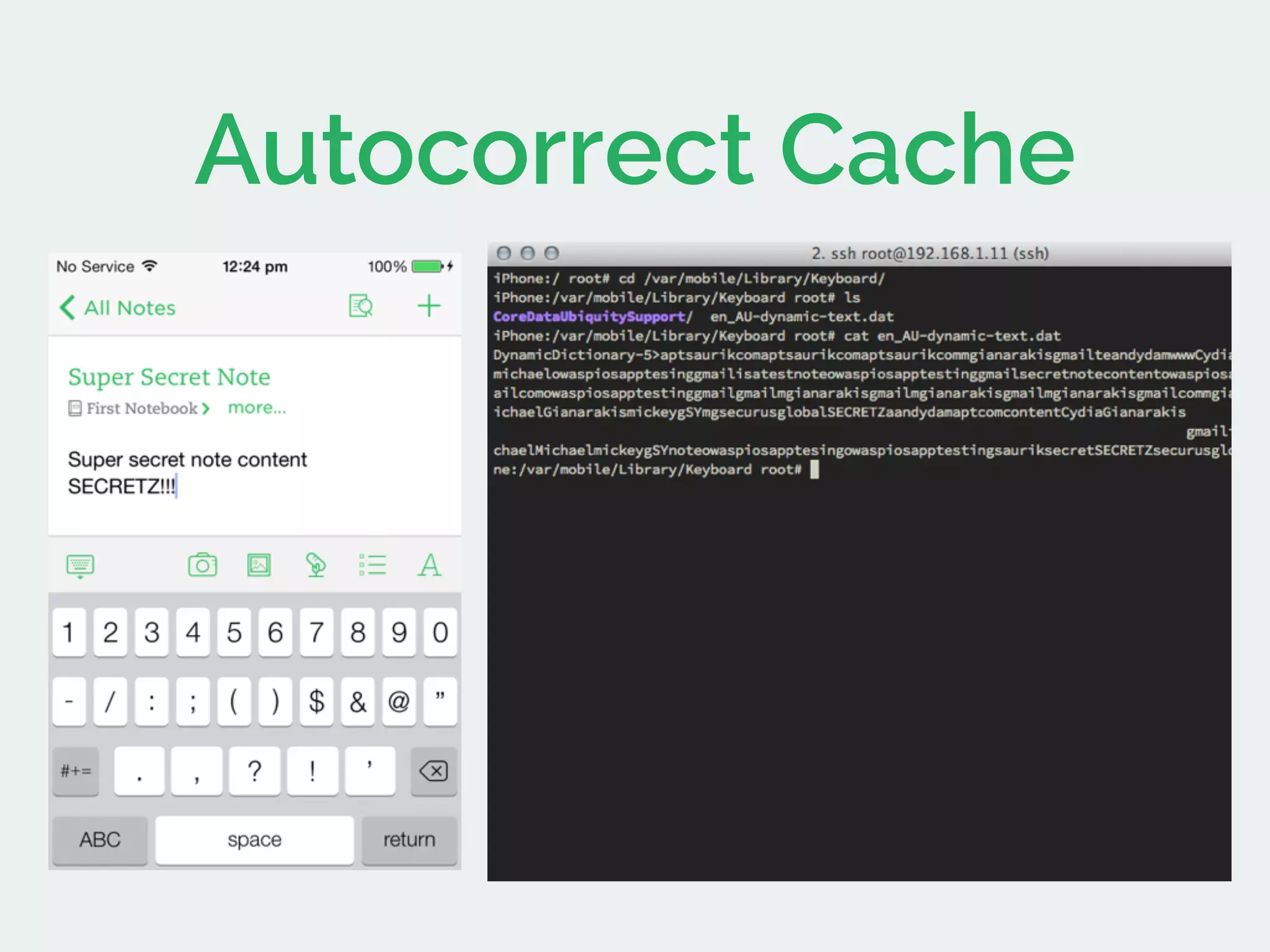
The document discusses developing secure iOS applications. It covers common security issues like binary and runtime security, transport layer security, and data security. It provides principles for secure design like not trusting the client/runtime and not storing sensitive data on devices. It also describes techniques to address specific issues like debug checks, jailbreak detection, and preventing unintended data leakage.