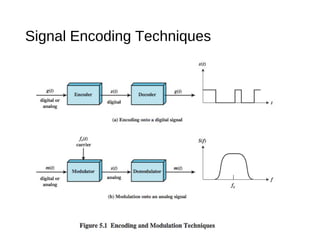
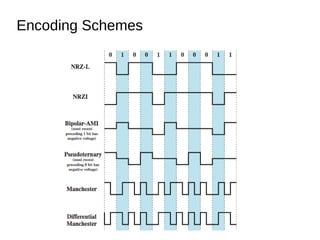
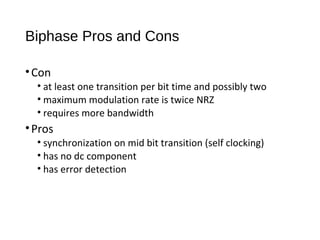
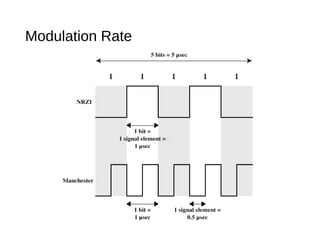
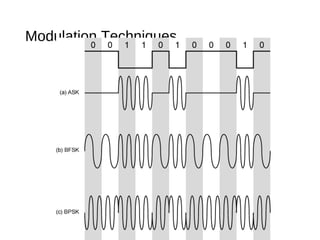
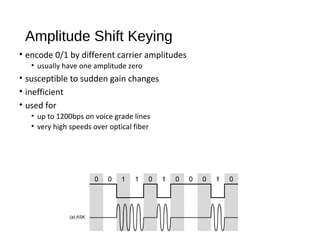
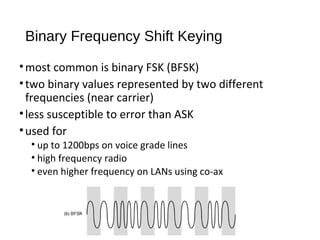
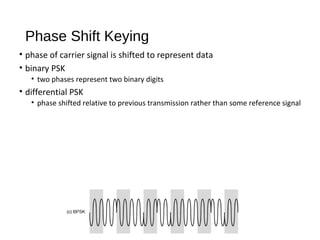
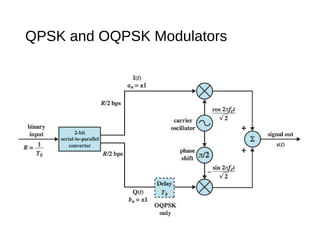
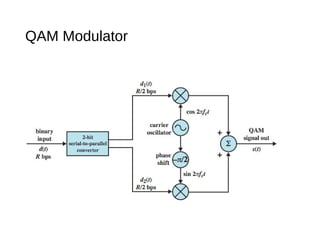
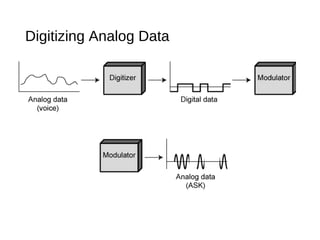
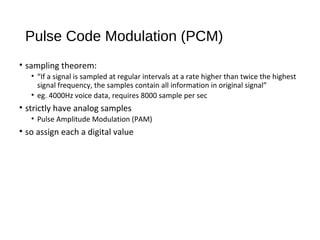
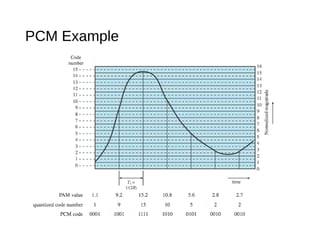
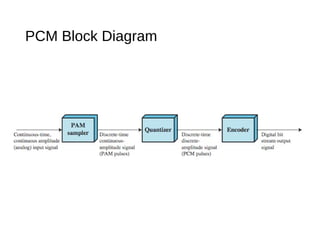
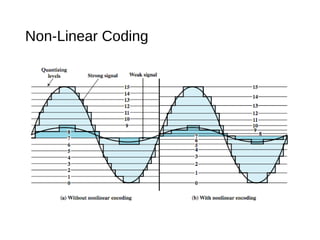
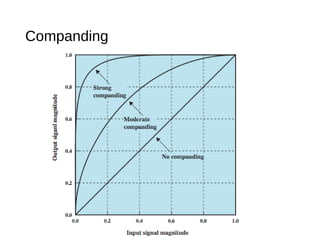
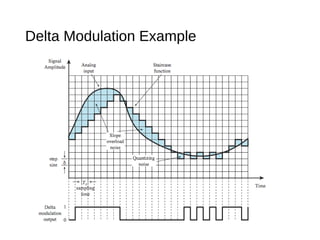
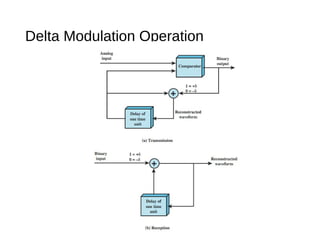
Digital signals can be encoded in various ways:
1) NRZ-L uses two voltage levels to represent 0s and 1s, maintaining a constant level during each bit.
2) NRZI represents 1s as transitions and 0s as no transitions at the start of each bit.
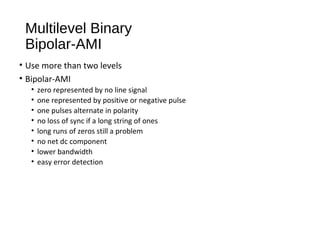
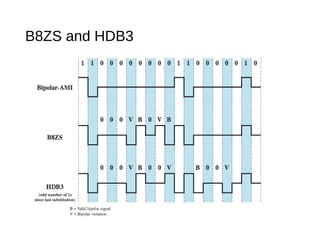
3) Bipolar-AMI represents 0s as no signal and alternating positive and negative pulses for 1s, eliminating long runs of the same signal.