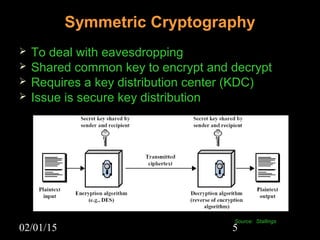
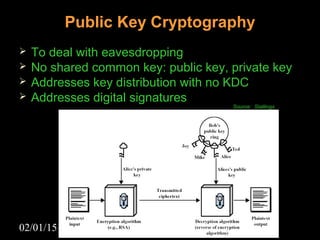
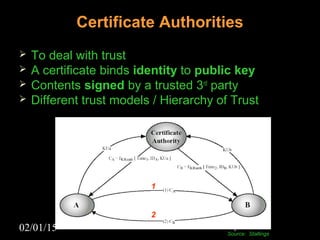
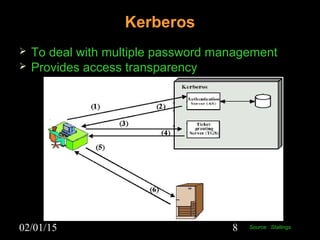
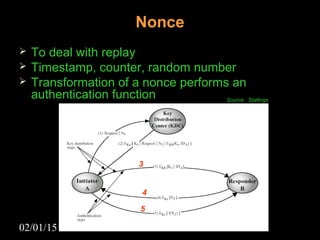
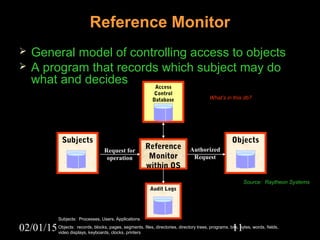
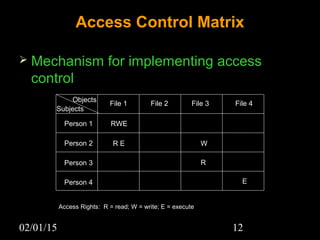
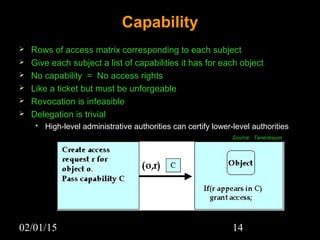
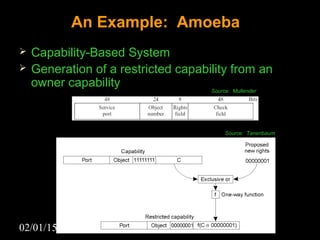
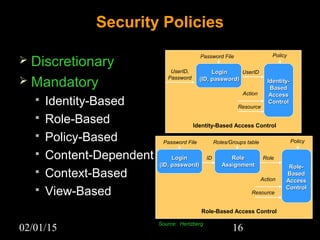
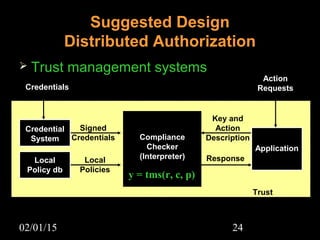
This document discusses security aspects in distributed operating systems. It covers authentication methods like symmetric cryptography and public key cryptography. It also discusses authorization mechanisms like access control matrices, lists and capabilities. The document proposes a design for distributed authentication using public key Kerberos and distributed authorization using trust management systems. It concludes that current security in distributed OS still relies on traditional centralized mechanisms and that alternatives like trust management systems are still immature.