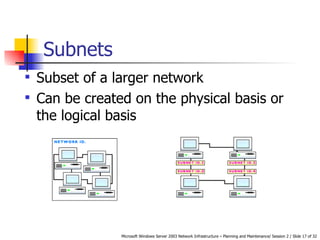
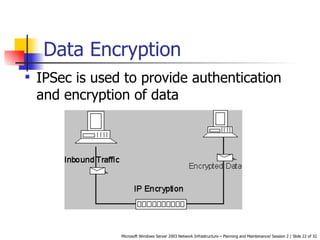
The document discusses network design using TCP/IP. It covers IP addressing, subnet masks, default gateways, and subnetting. It also discusses network security methods like IP packet filtering, encryption, authentication, and IPSec. Optimizing the subnet design, IP performance, remote subnets, and quality of service can create an effective network infrastructure.