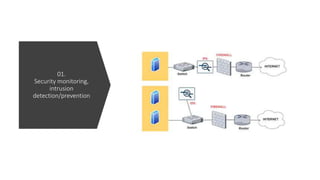
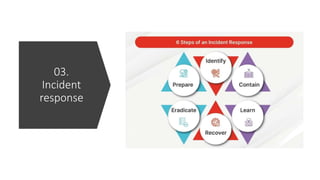
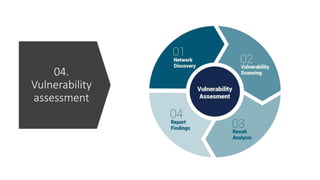
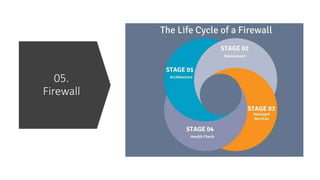
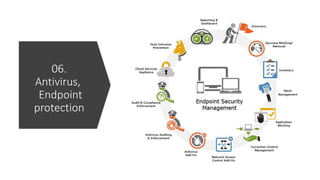
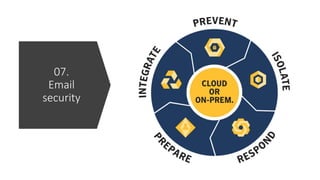
The document provides a comprehensive list of open-source security tools categorized into various domains such as security monitoring, threat intelligence, incident response, vulnerability assessment, firewall, antivirus/endpoint protection, and email security. Each category includes specific tools like Suricata for intrusion detection, MISP for threat intelligence, and OpenVAS for vulnerability assessment. The author, Boni Yeamin, is an IT officer specializing in defensive security at Akij Group in Dhaka, Bangladesh.