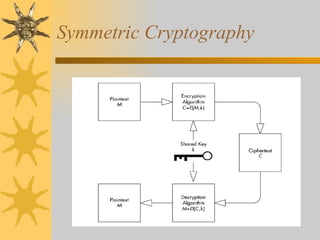
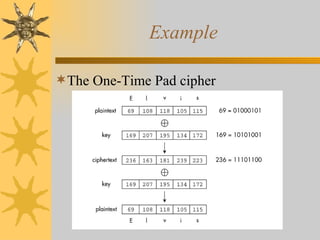
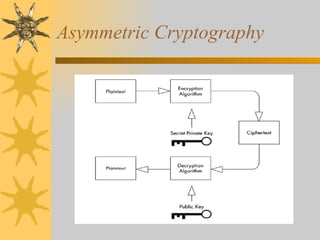
This document discusses .NET security concepts such as cryptography, code access security, role-based security, and strong naming of assemblies. It provides examples of symmetric and asymmetric cryptography. It also explains how .NET enforces security through evidence and policy-based permissions as well as role-based access control. Finally, it discusses how to sign assemblies with strong names for verification and tamper-proofing.














![.NET Security Programming Demanding Permissions FileIOPermission fileioperm = new FileIOPermission(FileIOPermissionAccess.AllAccess,@"c:\" ); fileioperm.Demand(); Requesting Permissions. using System.Security.Permissions; [assembly:UIPermissionAttribute(SecurityAction.RequestMinimun, Unrestricted =true)] Denying Permissions. CodeAccessPermission permission = new FileIOPermission(FileIOPermissionAccess.AllAccess,@"c:\"); permission.deny(); Asserting Permissions.](https://image.slidesharecdn.com/security-in-net-framework-1229333888112073-1/85/Security-In-Net-Framework-21-320.jpg)
![Role-Based Security Perform the following tasks to create an instance of the GenericPrincipal class . 1 . Create a new instance of the identity class and initialize it with the name you want it to hold. The following code creates a new GenericIdentity object and initializes it with the name MyUser. GenericIdentity MyIdentity = new GenericIdentity("MyUser"); 2. Next, create a new instance of the GenericPrincipal class and initialize it with the previously created GenericIdentity object and an array of strings that represent the roles that you want associated with this principal. The following code example specifies an array of strings that represent an administrator role and a user role. The GenericPrincipal is then initialized with the previous GenericIdentity and the string array. String[] MyStringArray = {"Manager", "Teller"}; GenericPrincipal MyPrincipal = new GenericPrincipal(MyIdentity, MyStringArray); 3. Finally, use the following code to attach the principal to the current thread. This is valuable in situations where the principal must be validated several times, it must be validated by other code running in your application, or it must be validated by a PrincipalPermission object. You can still perform role-based validation on the principal object without attaching it to the thread. For more information, see Replacing a Principal Object. Thread.CurrentPrincipal = MyPrincipal;](https://image.slidesharecdn.com/security-in-net-framework-1229333888112073-1/85/Security-In-Net-Framework-23-320.jpg)

![Strong Naming Assemblies 1. First generate a public/private key pair sn -k MyKeyPair.snk 2. Extracts the public key from MyKeyPair.snk and places it into MyPublicKey.snk. sn -p MyKeyPair.snk MyPublicKey.snk 3. Now sign a DLL or an EXE assembly with MyPublicKey.snk using Assembly Linker utility Al.exe. al /out:WalkingThruEvidence.exe /keyfile:MyKeyPair.snk 4. Finally the following code to the source file named AssemblyInfo.cs , [assembly:AssemblyKeyFileAttribute(@"...\MyKeyPair.snk ")]](https://image.slidesharecdn.com/security-in-net-framework-1229333888112073-1/85/Security-In-Net-Framework-25-320.jpg)

