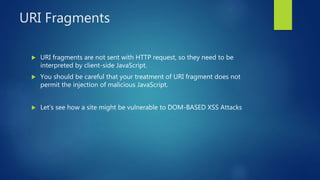
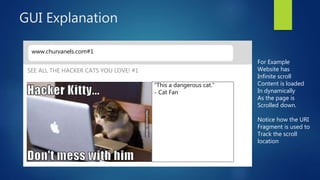
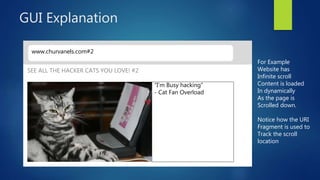
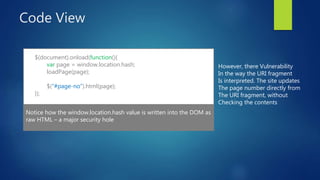
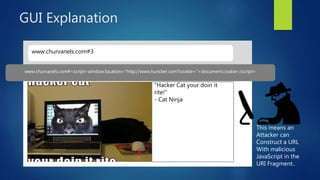
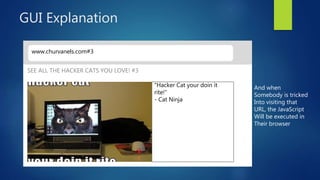
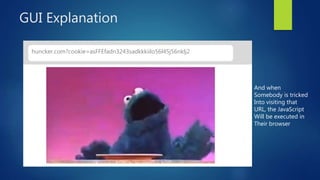
This document discusses DOM-based cross-site scripting (XSS) vulnerabilities that can occur when user-controllable data from the URI fragment is dynamically added to the DOM without validation. It provides examples of how malicious JavaScript could be injected via a crafted URL and executed in a victim's browser. The document recommends carefully auditing all JavaScript to identify vulnerabilities, parsing JSON input securely, and using frameworks that prevent unsafe DOM operations to protect against DOM-based XSS attacks.