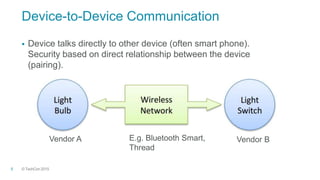
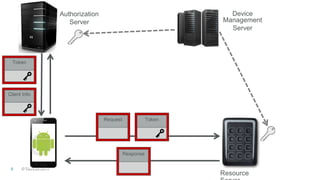
The document discusses authorization for internet of things devices using OAuth 2.0. It outlines design patterns like backend data portability and device-to-device communication. It then describes the architecture involving clients, authorization servers, resource servers, and devices. Finally, it provides an overview of relevant standards organizations and technologies like OAuth, COSE, OpenID Connect, and FIDO that can help address IoT security challenges.