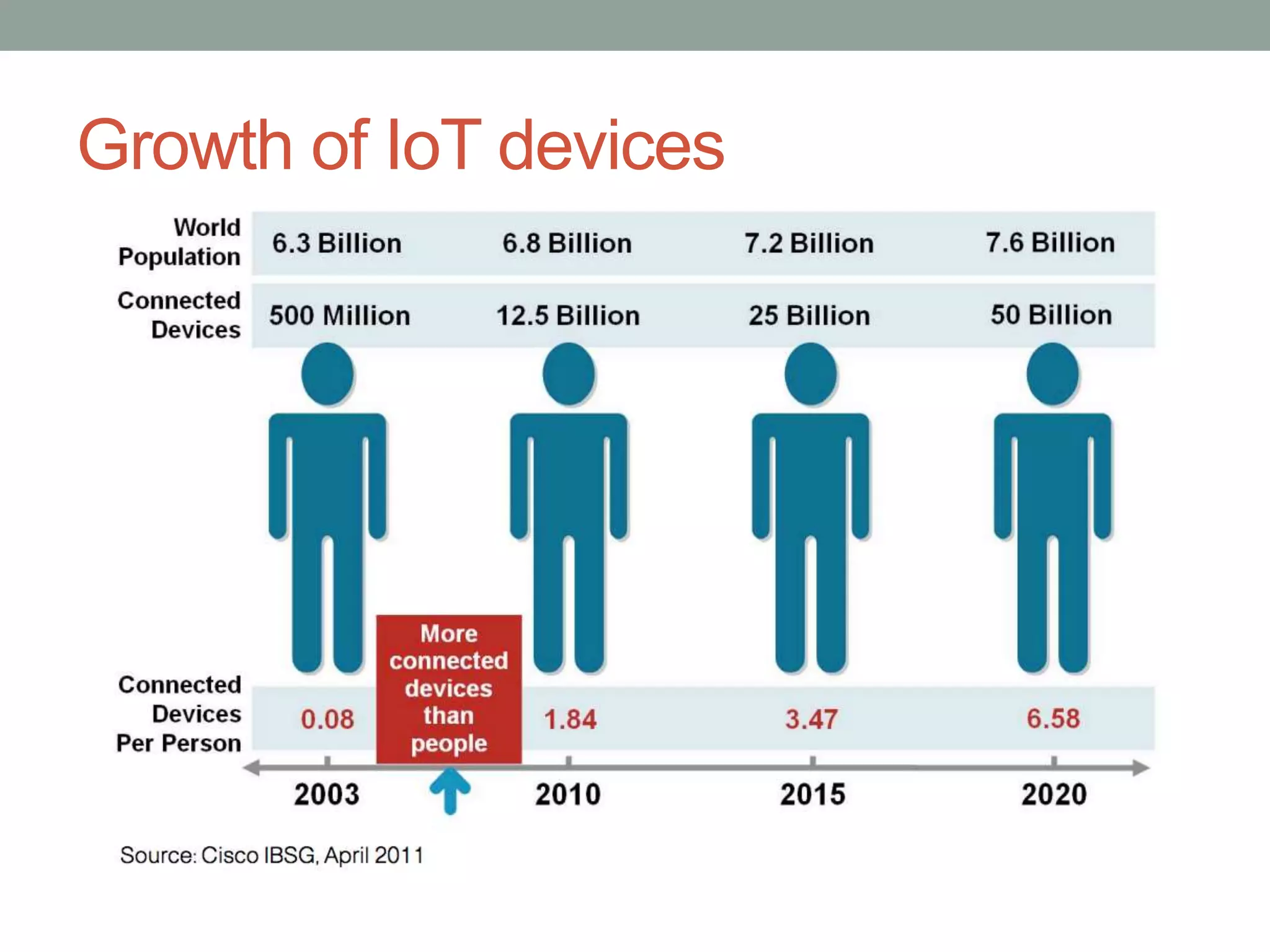
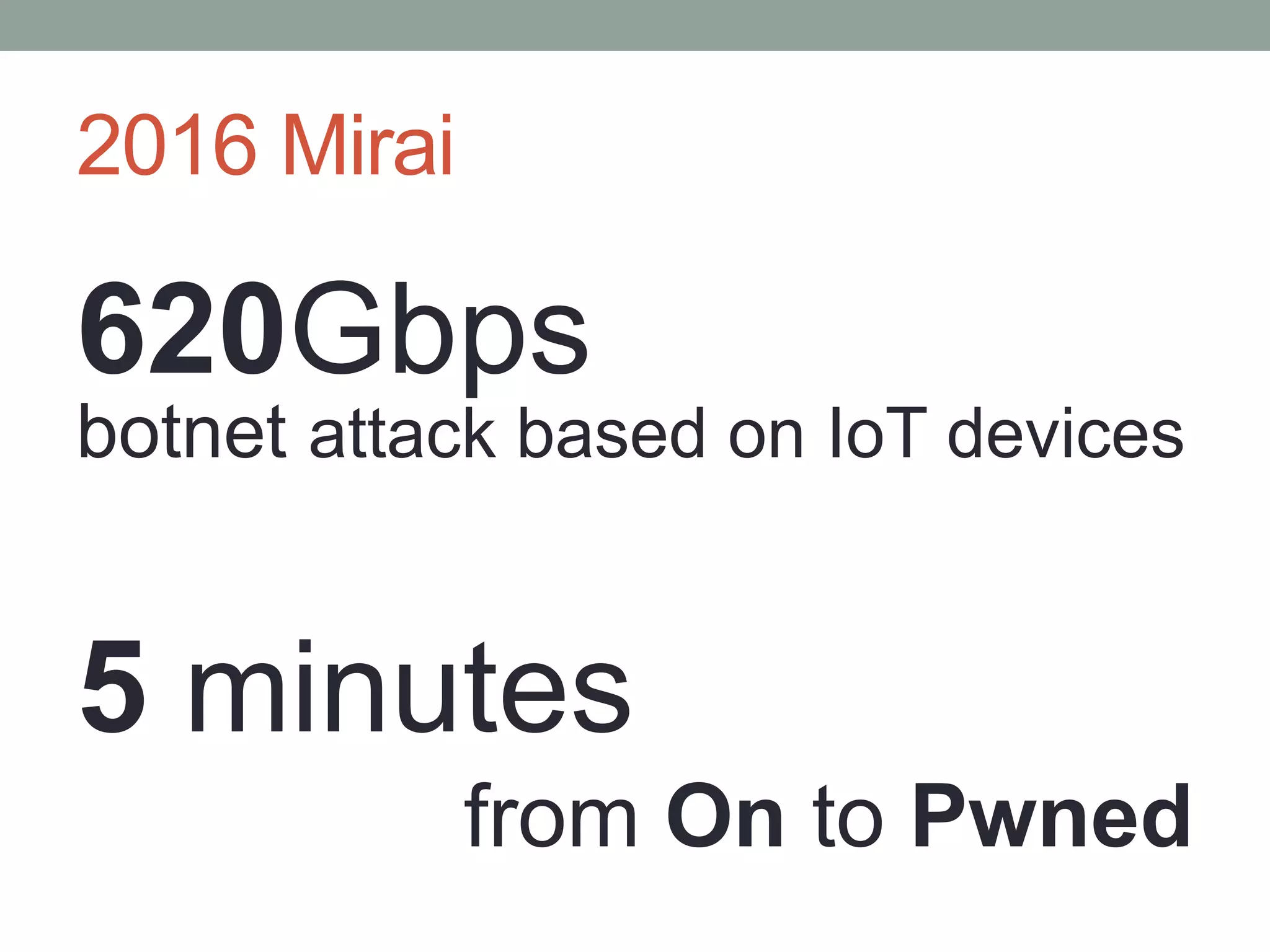
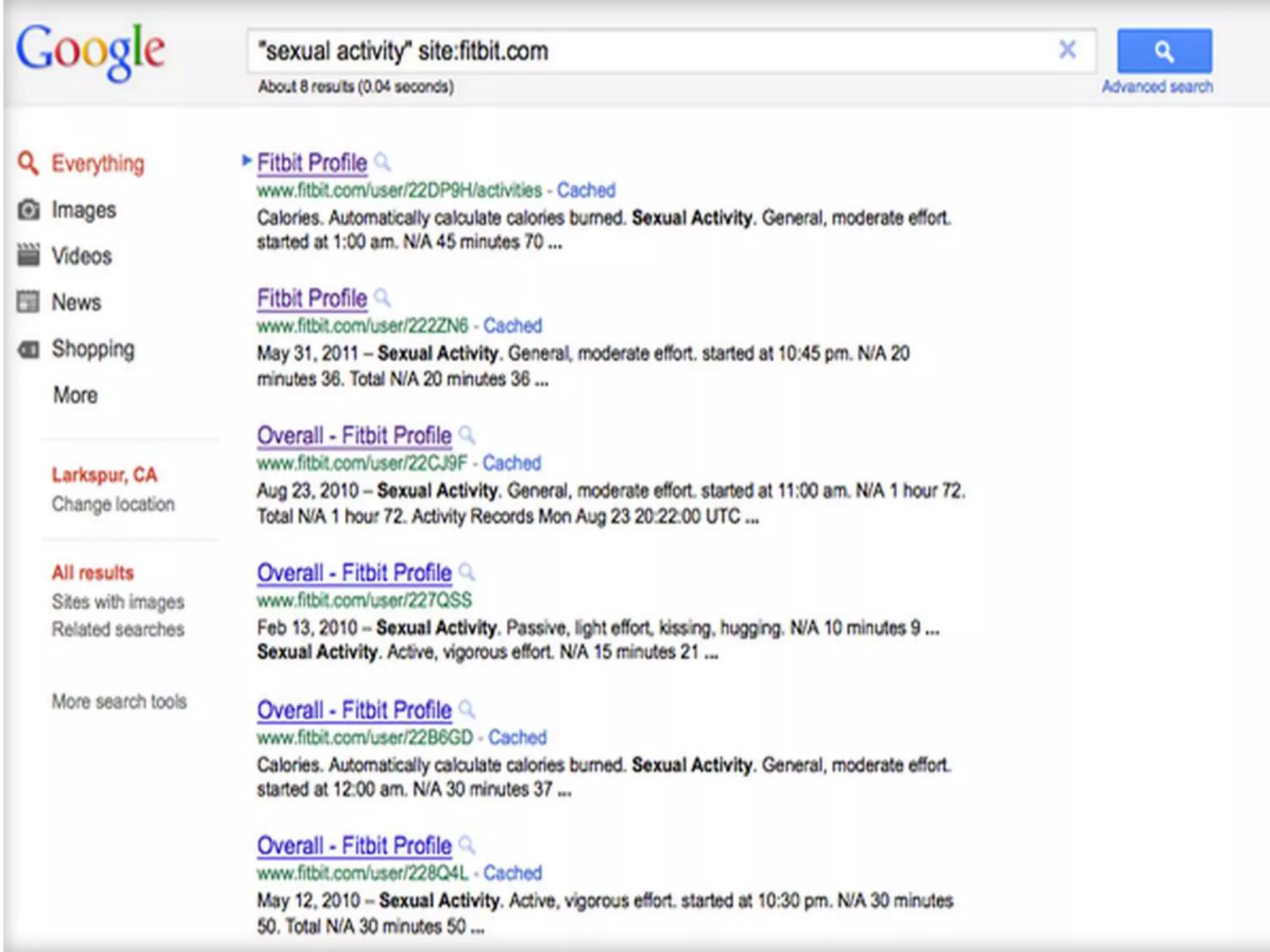
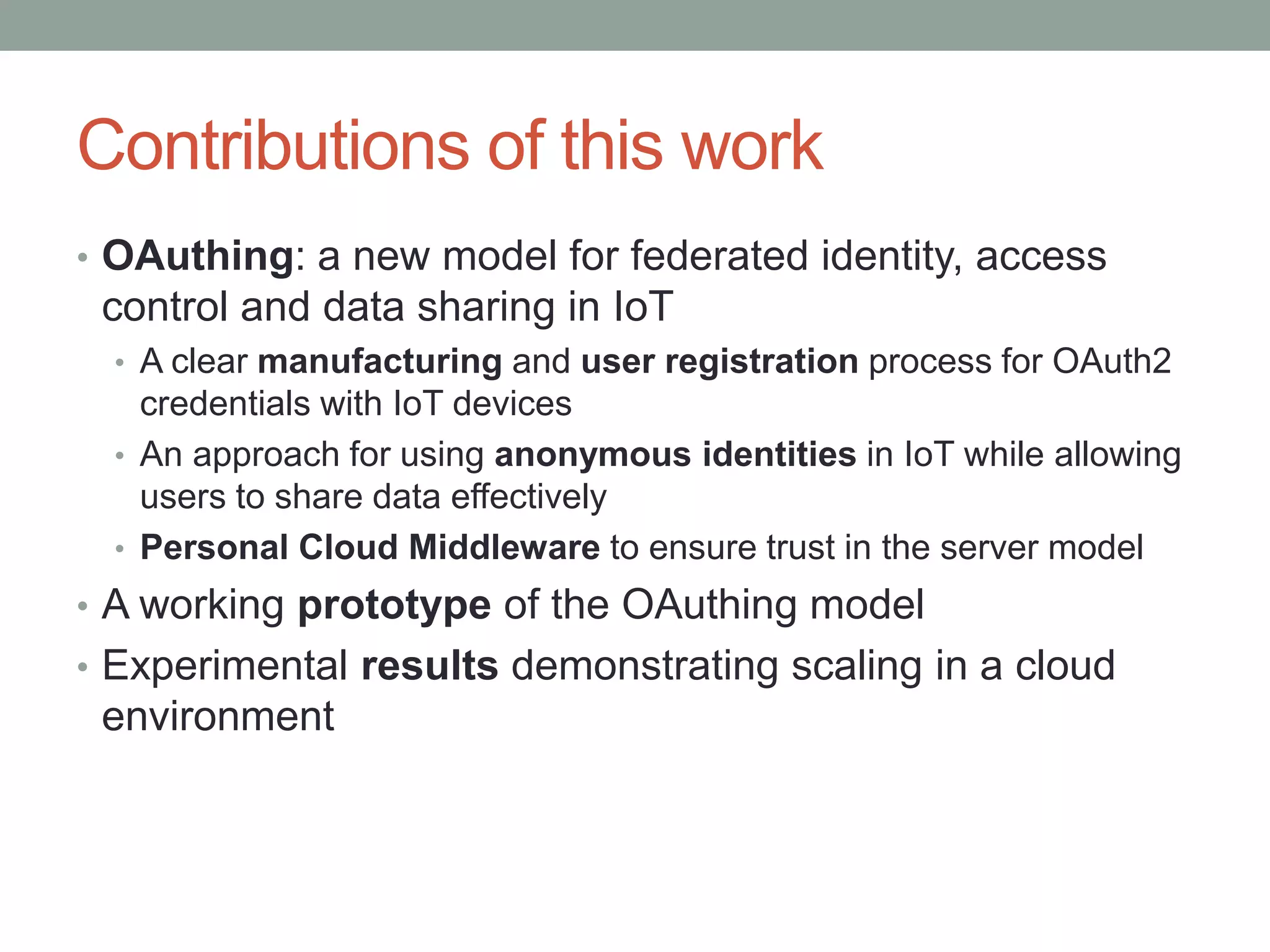
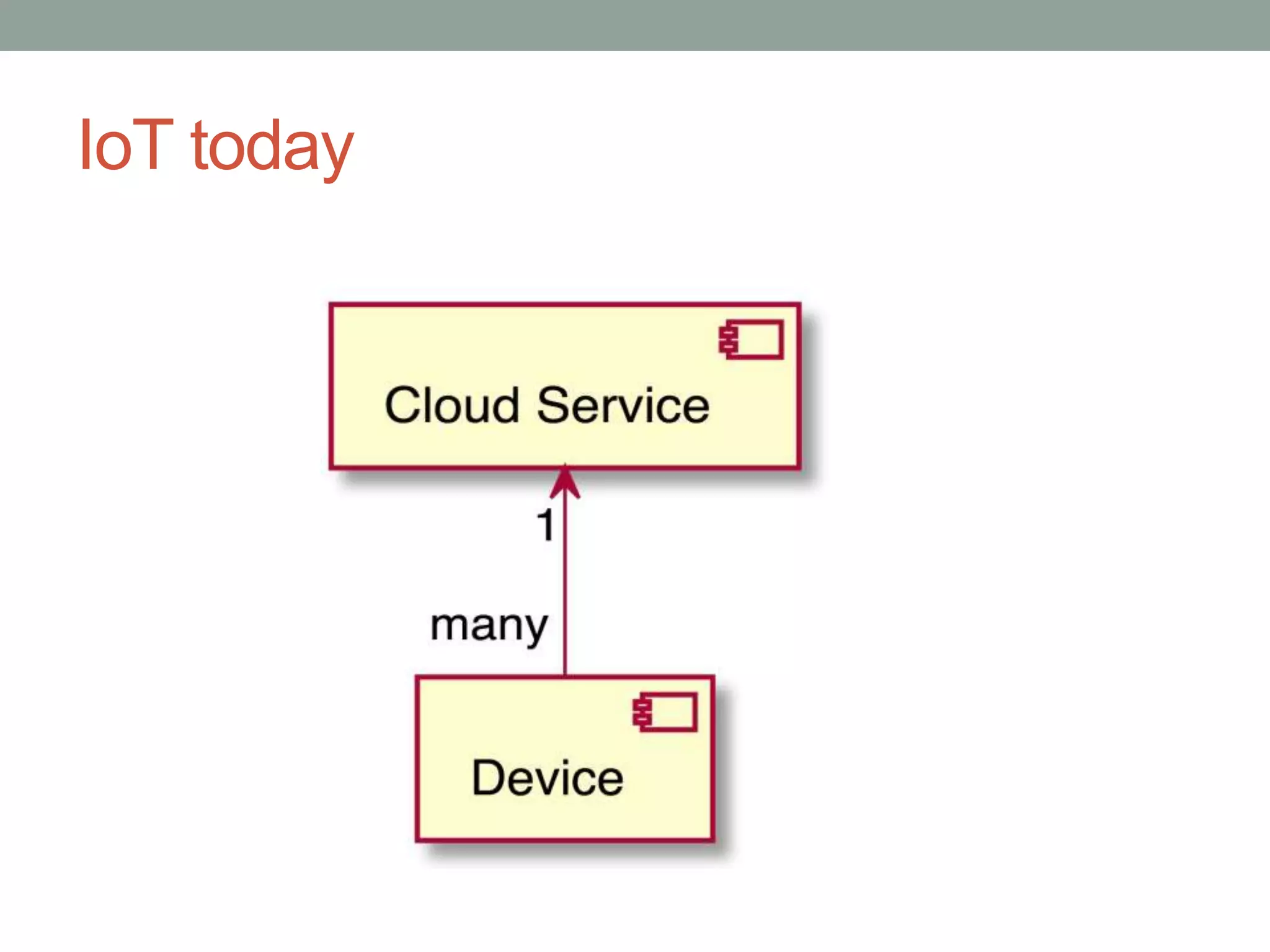
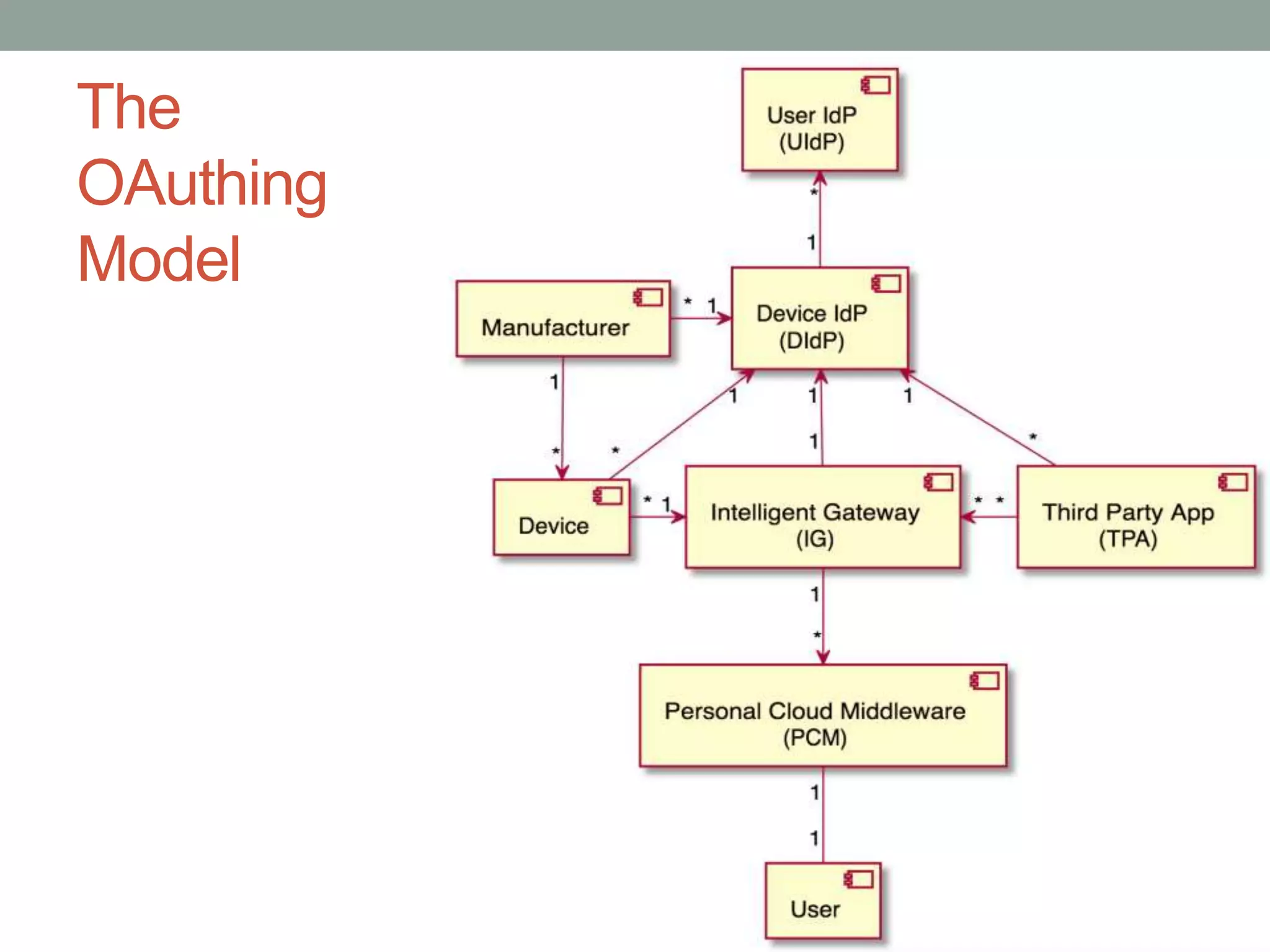
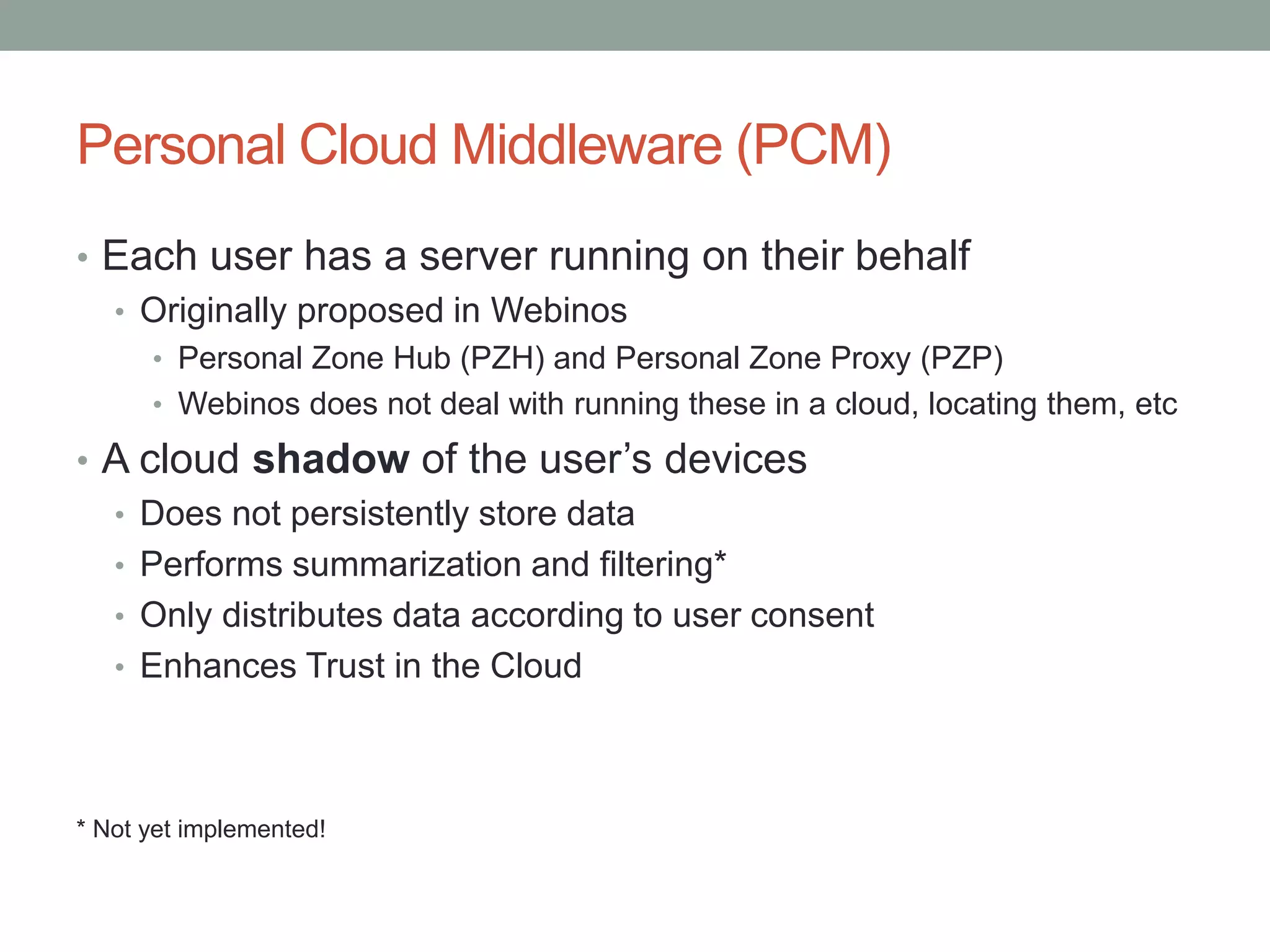
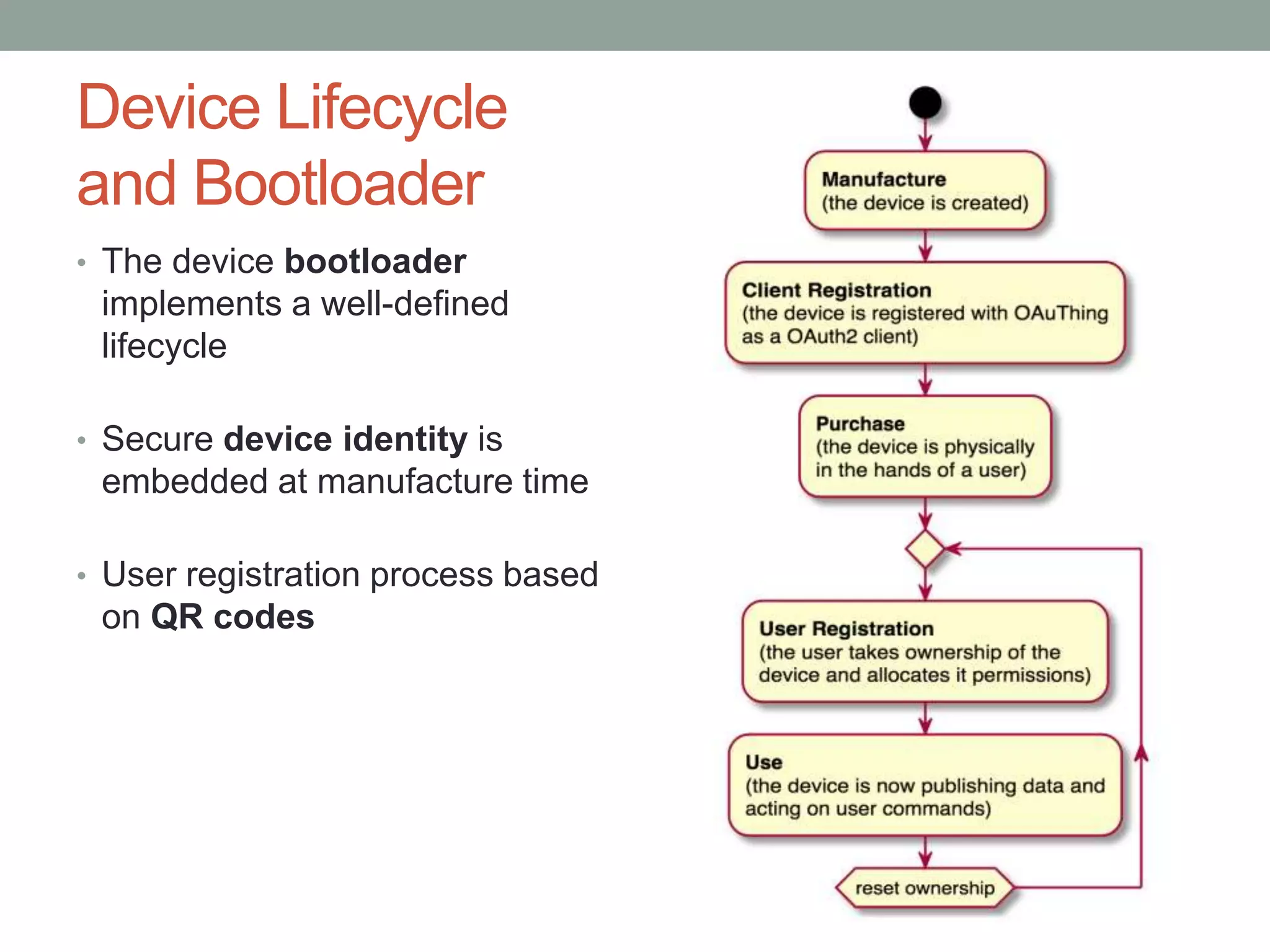
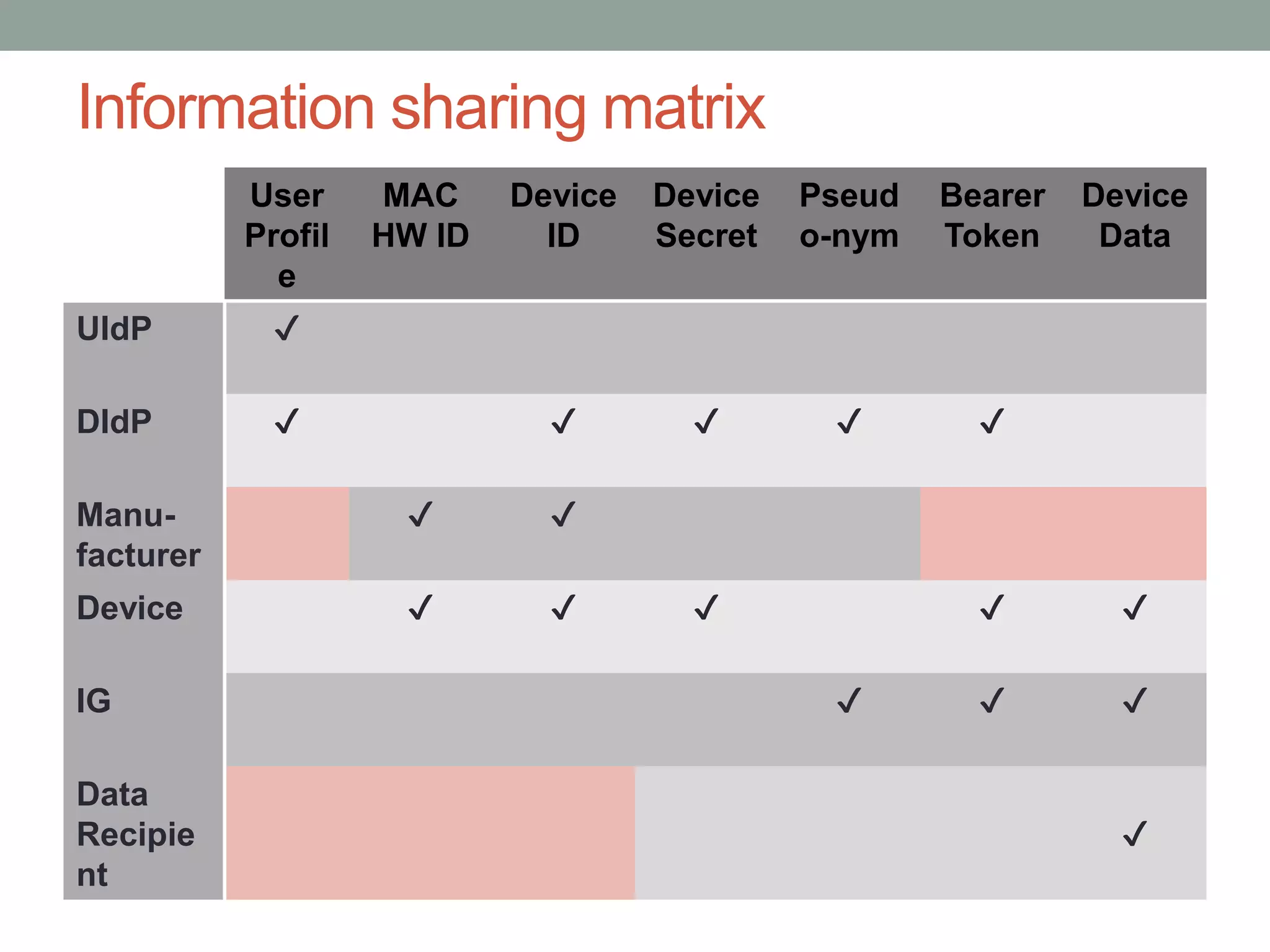
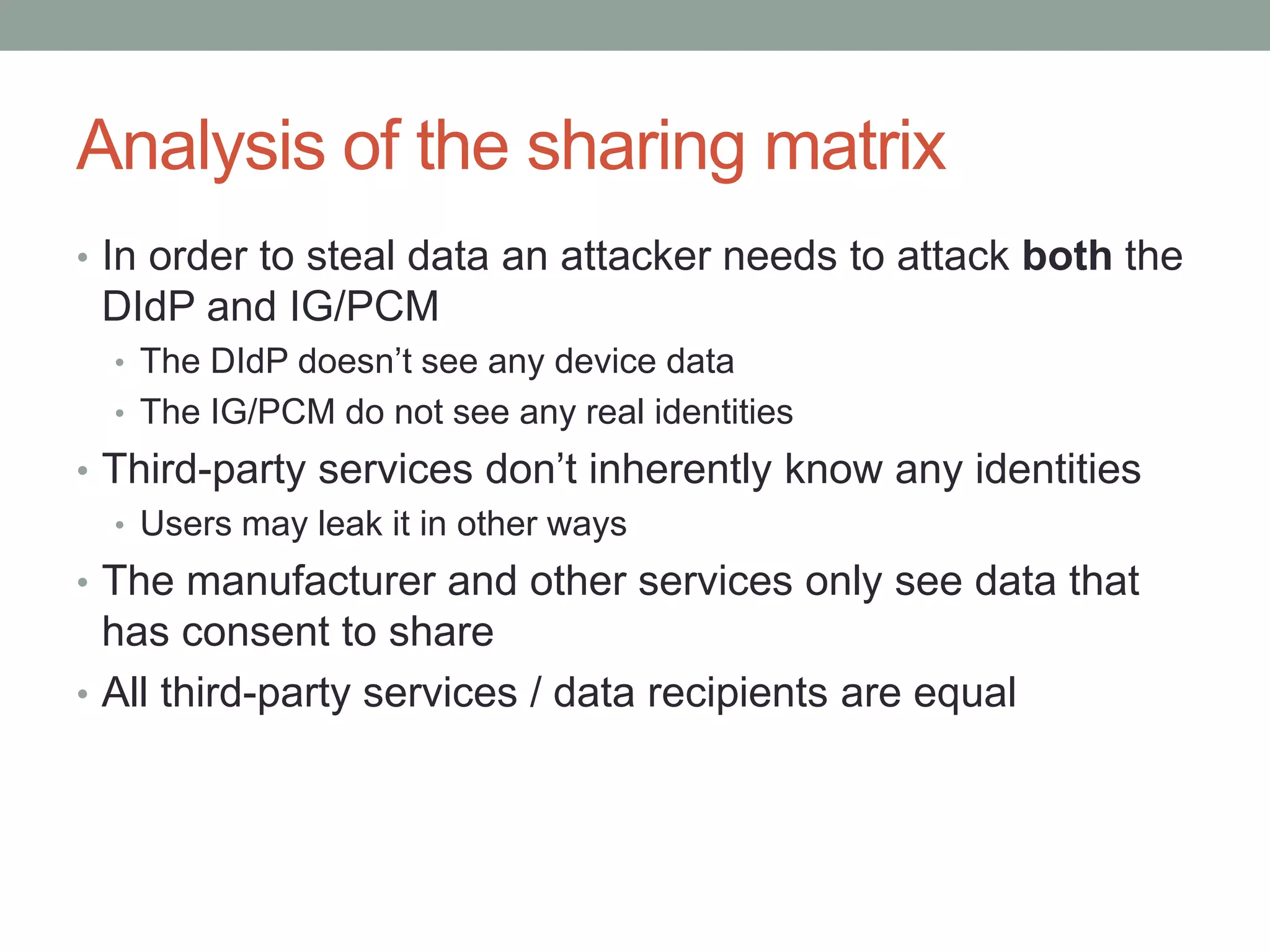
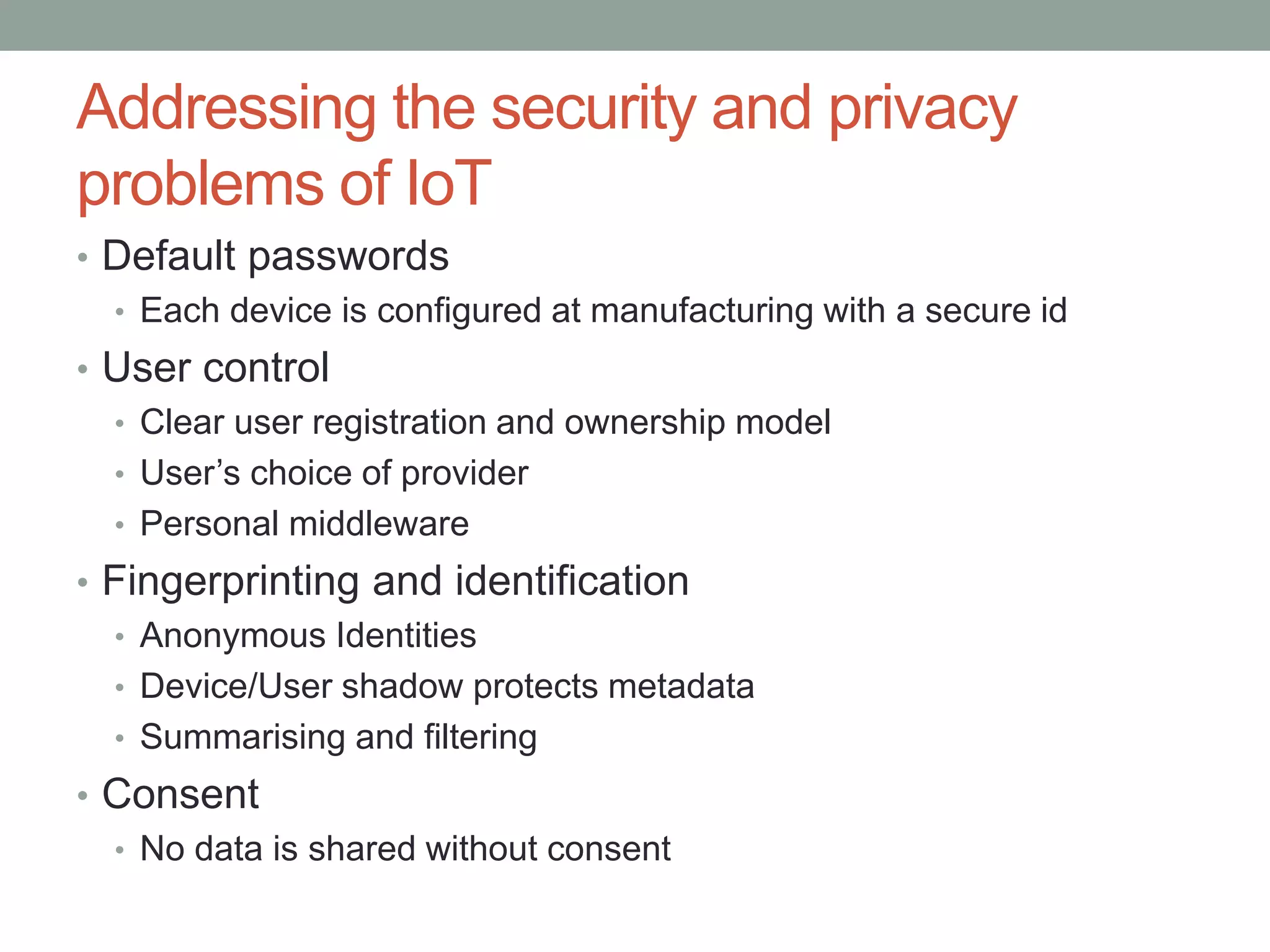
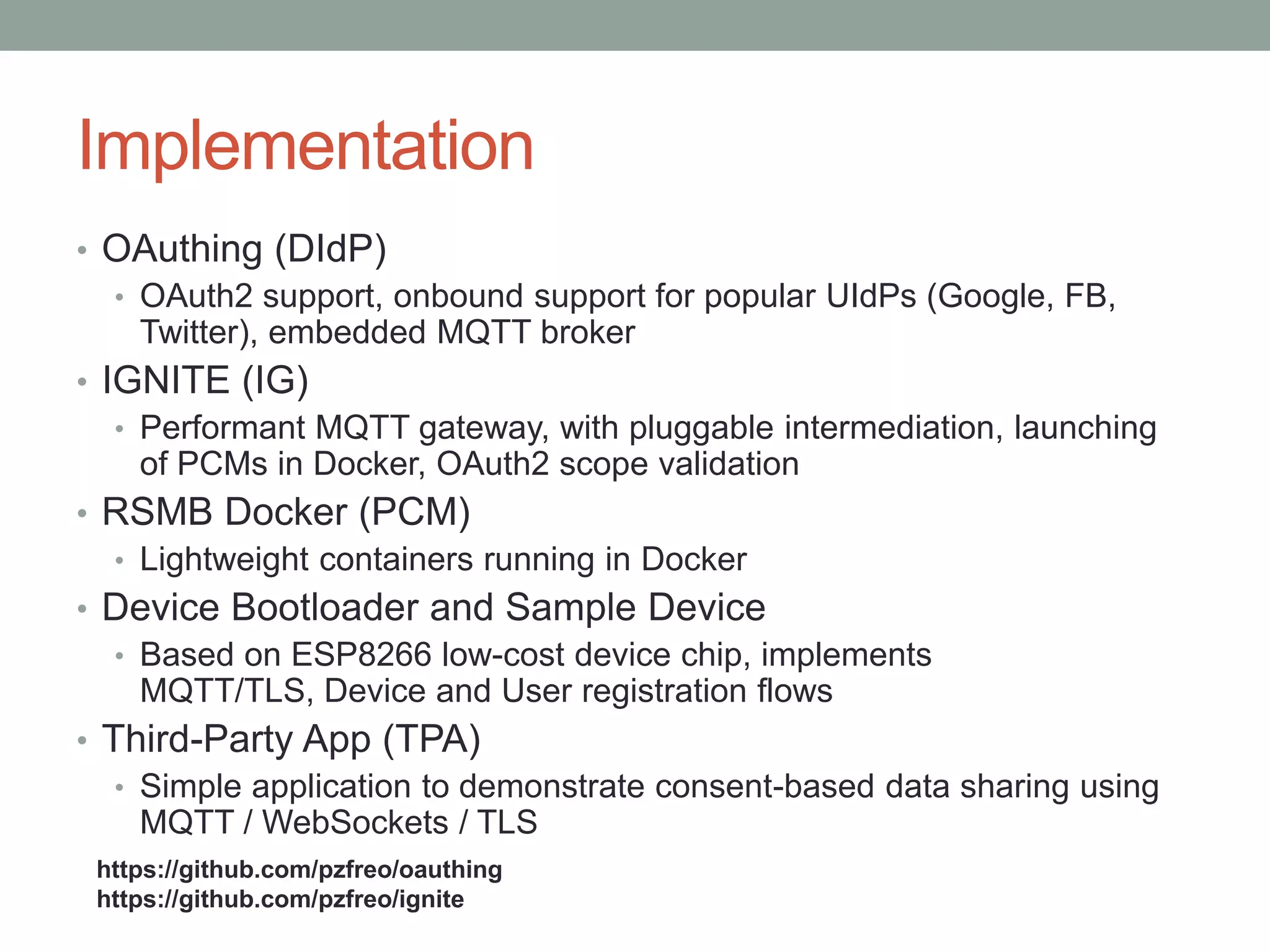
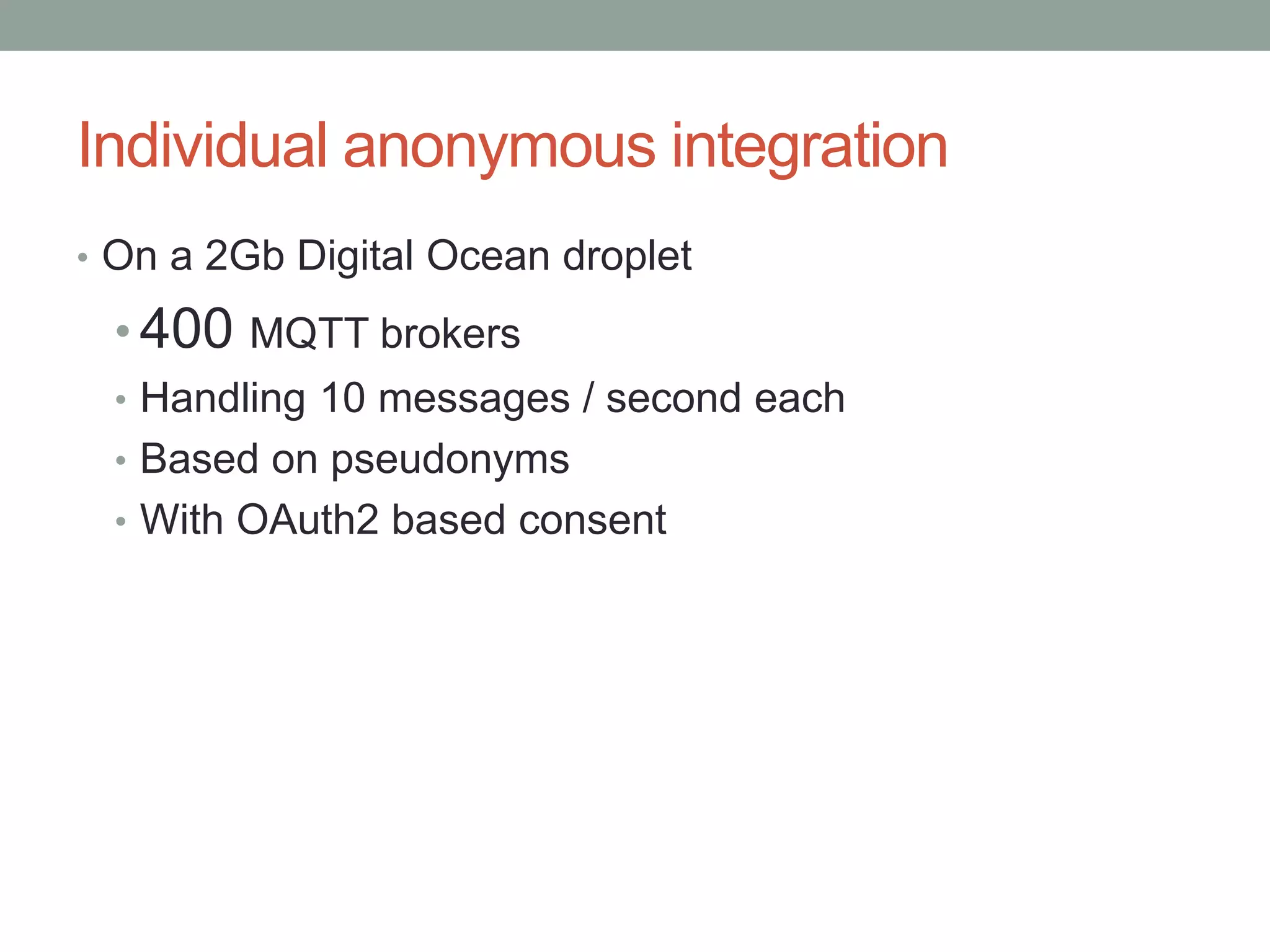
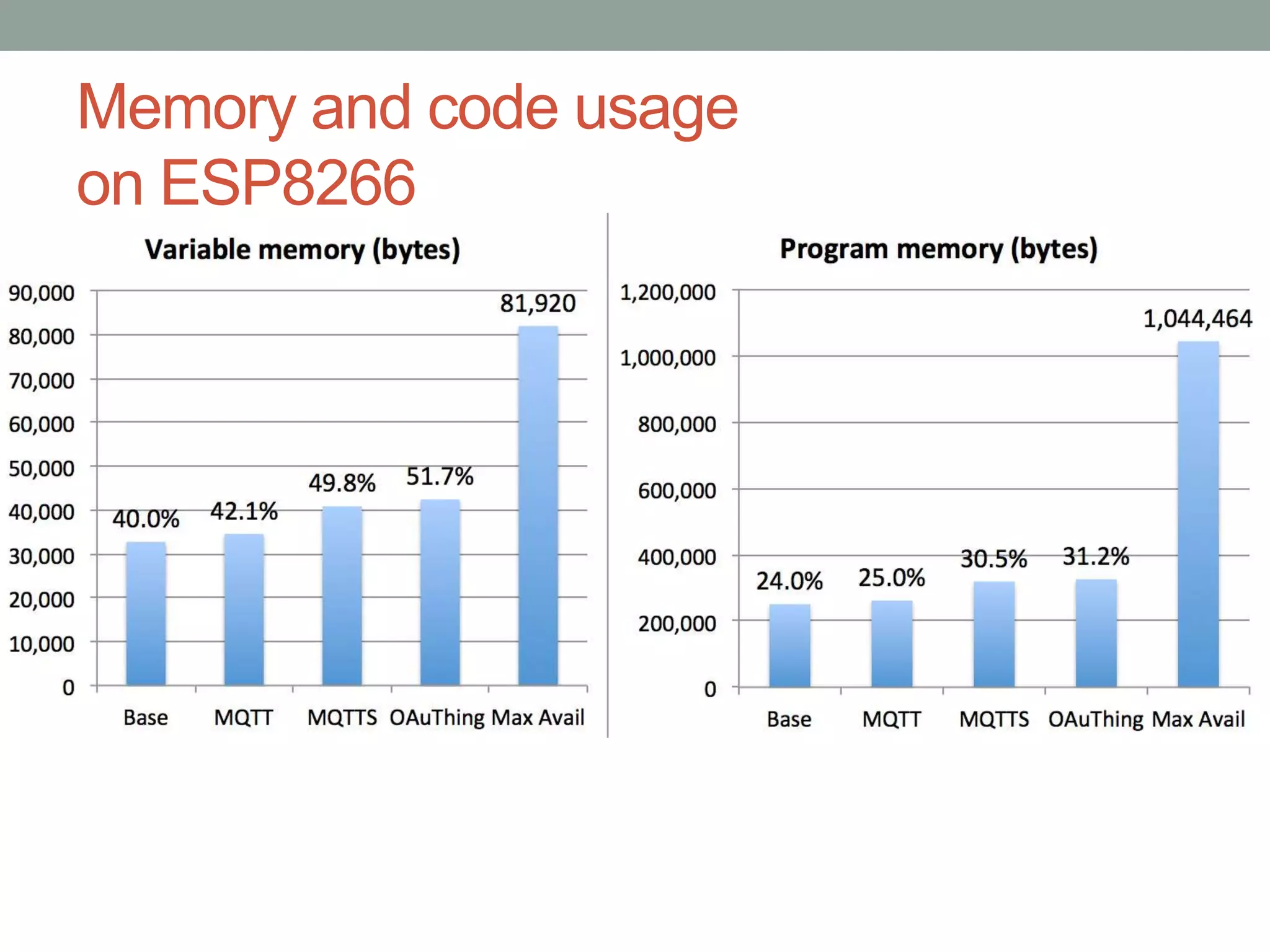
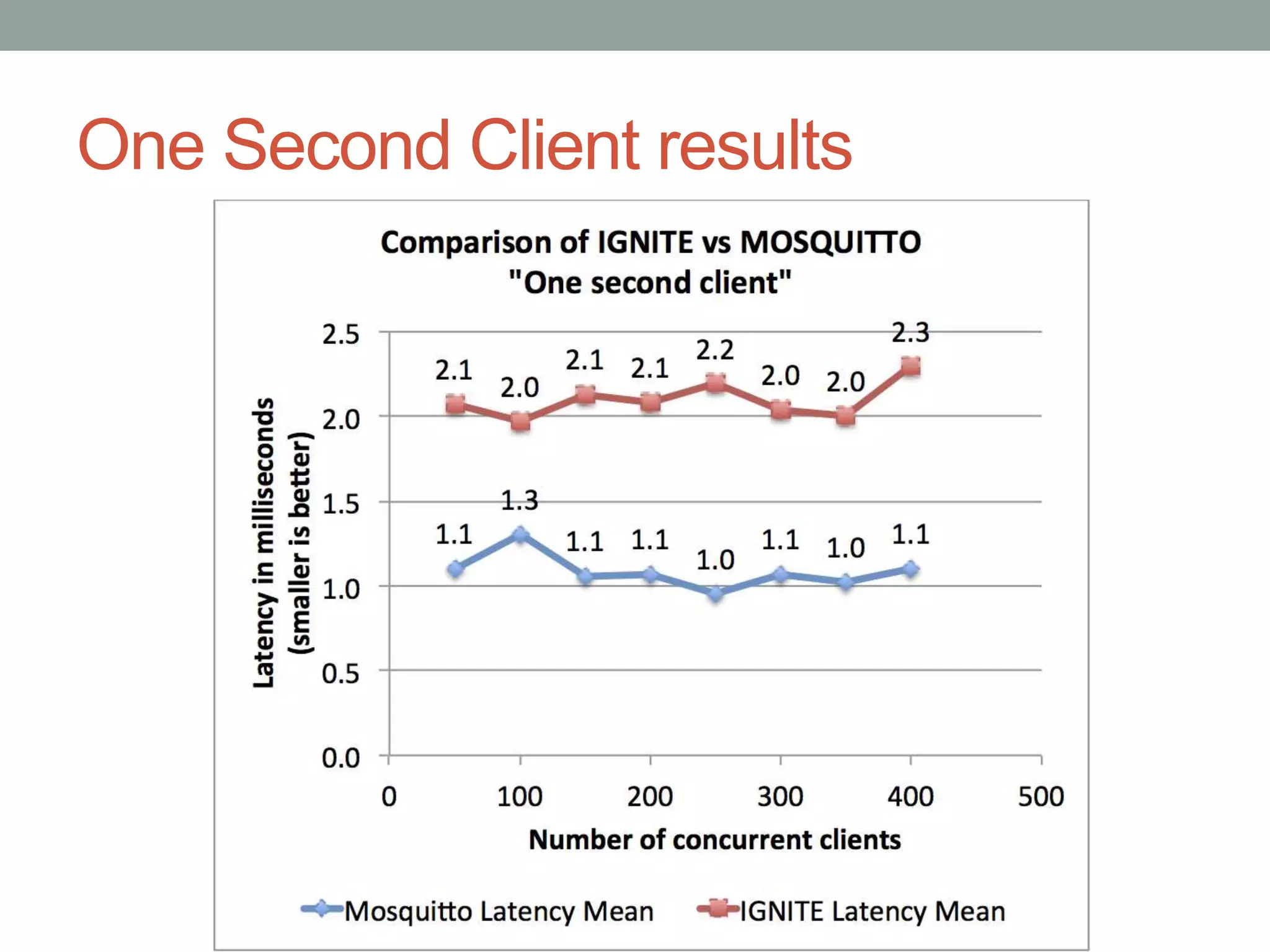
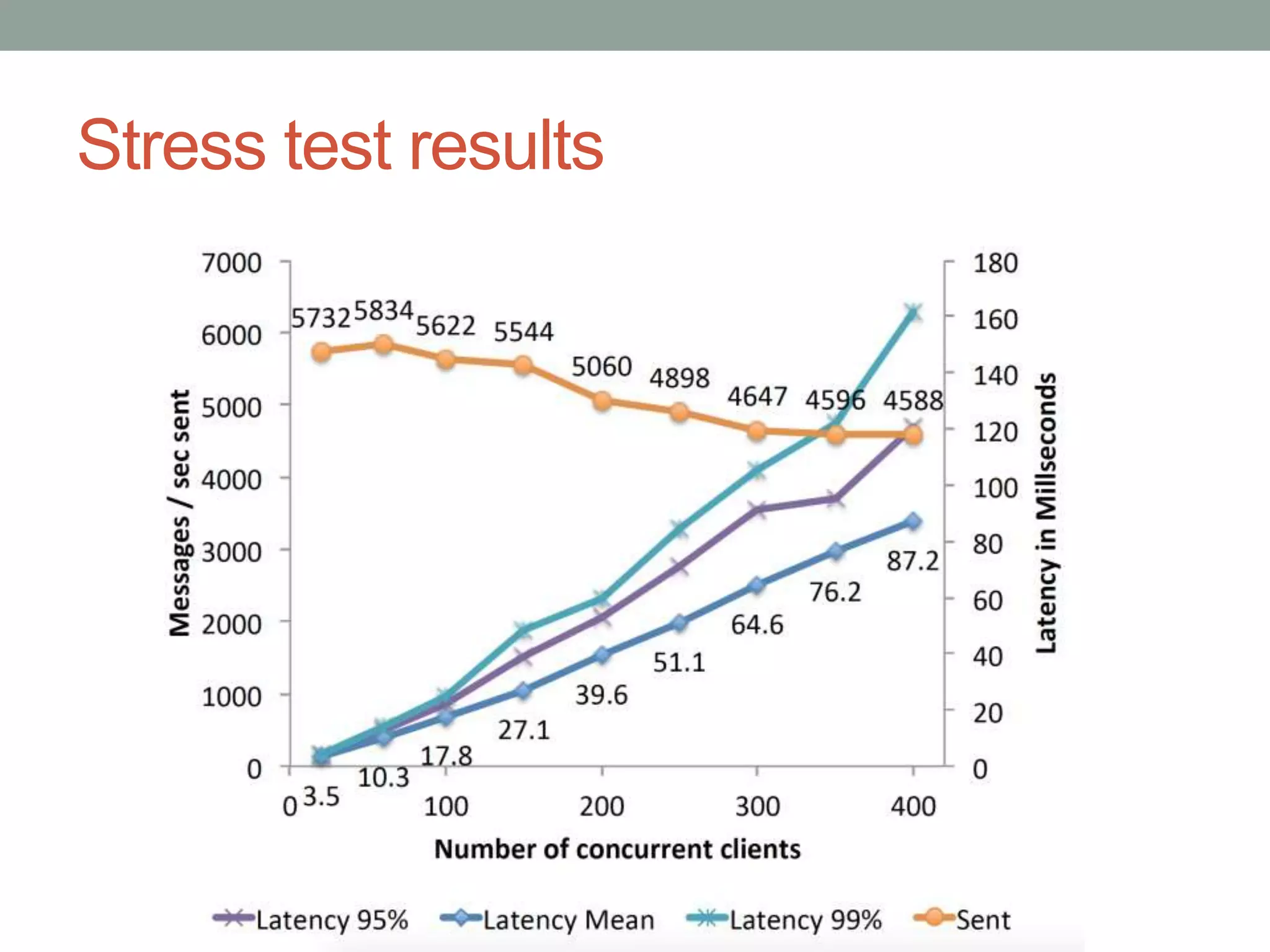
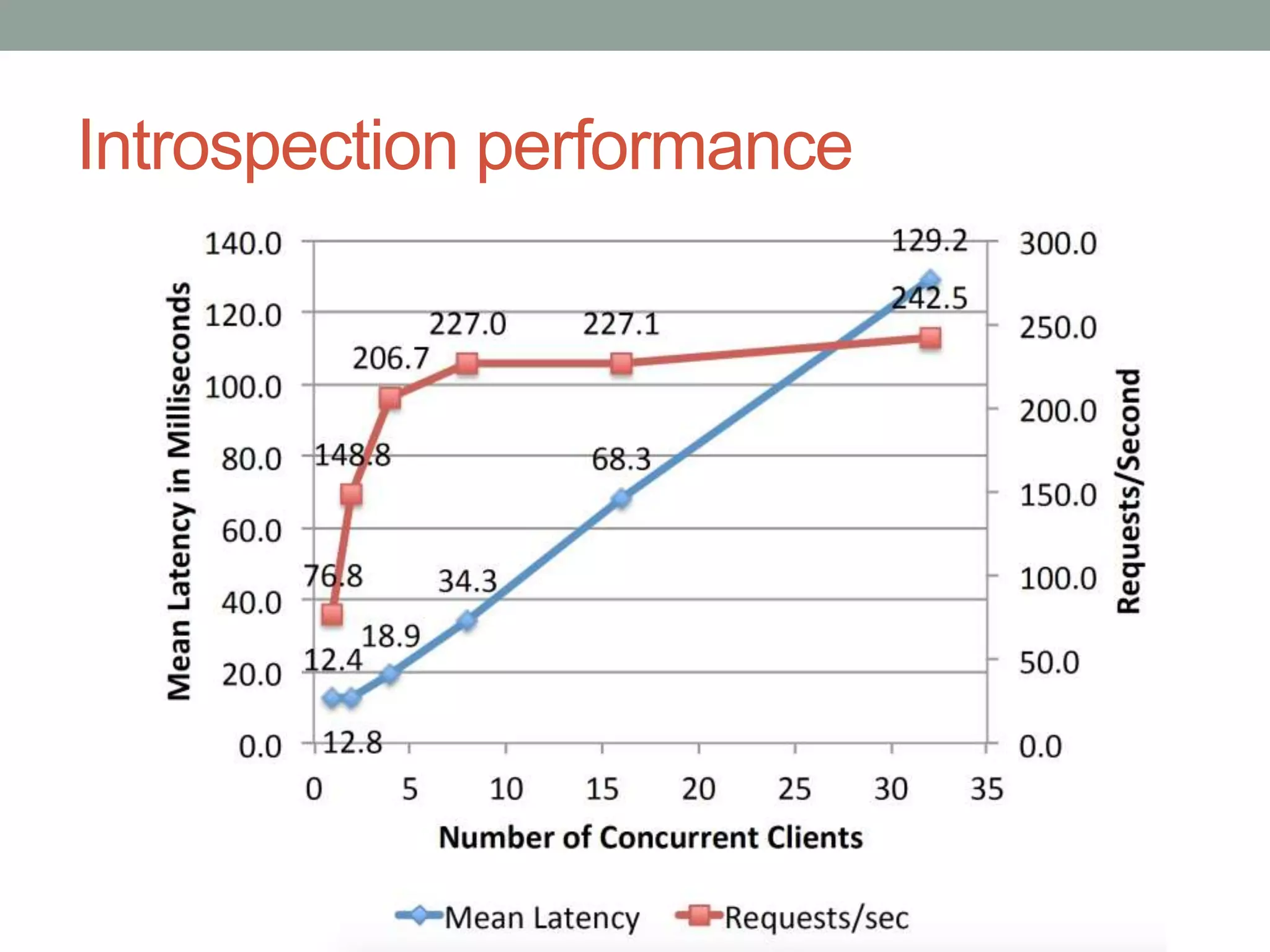
This document proposes a new model called OAuthing for federated identity, access control, and data sharing in IoT. It describes the growth of IoT devices and privacy/security issues. The model includes a Device Identity Provider (DIdP) that provides anonymous identities and tokens, a Personal Cloud Middleware (PCM) that runs on behalf of each user to filter data, and an Intelligent Gateway (IG) that routes requests based on identities. It presents the implementation including a device bootloader, and prototype results showing it can support 400 brokers handling 10 messages/second each with low latency. Comparisons are made to related work which don't provide the same anonymous identities, registration processes, or personal middleware capabilities.










![Comparison with related work
• OAuth for Devices
• Previous work offers OAuth2 models for devices:
• FIOT [8], IGNITE [9], IOT-OAS [1], COMPOSE[14], OAuth1 for MQTT[13], IBM
Watson, AWS IoT
• None of these provide:
• Anonymous Identities
• Clear automated registration processes or
• Personal Cloud Middleware
• Webinos
• Concept of Personal Zone Hub – personal middleware
• Does not address usability of PZH, how to configure and run in a cloud
• Does not support federated identity to the device
• IoT@Work [16]
• A model for anonymous identities for IoT
• No separation of identity management and data sharing systems
• No federated identity models
[n] References refer to the bibliography in the paper](https://image.slidesharecdn.com/oauthingmeetuppresentation-161130183500/75/Anonymous-Individual-Integration-for-IoT-37-2048.jpg)