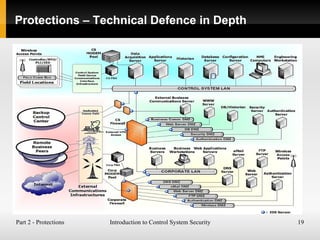
The document introduces control system security, detailing what control systems are and their unique risks, strengths, and weaknesses. It covers protections through people, processes, and technology, emphasizing the importance of network separation and regular security assessments. Additionally, it outlines governance policies, compliance audits, and resources for further learning about industrial control system security.

![Introduction Crispin Harris Security Specialist [email_address] 10 th May, 2010](https://image.slidesharecdn.com/securingcontrolsystemsv0-4-110510065612-phpapp02/85/Securing-control-systems-v0-4-2-320.jpg)