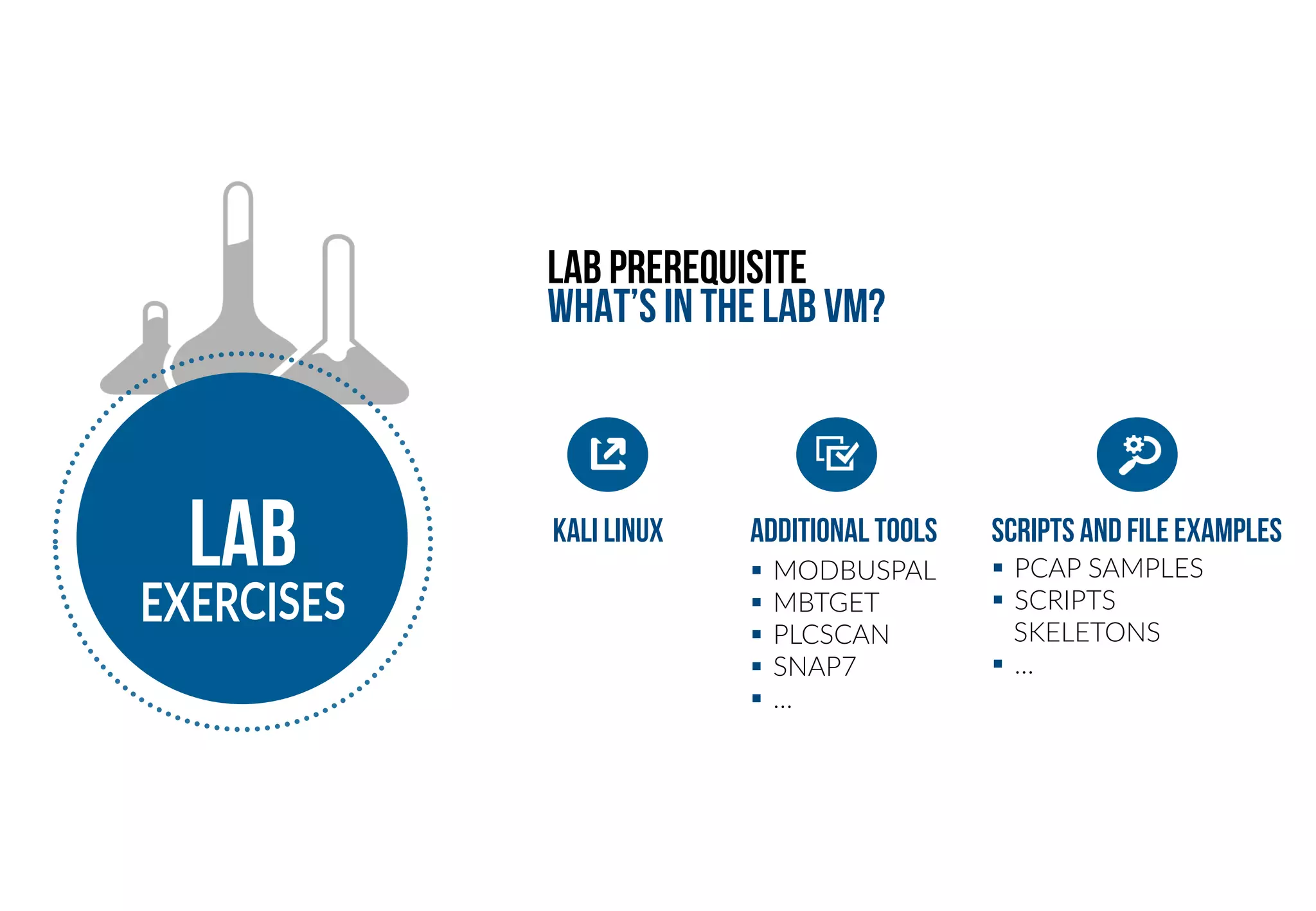
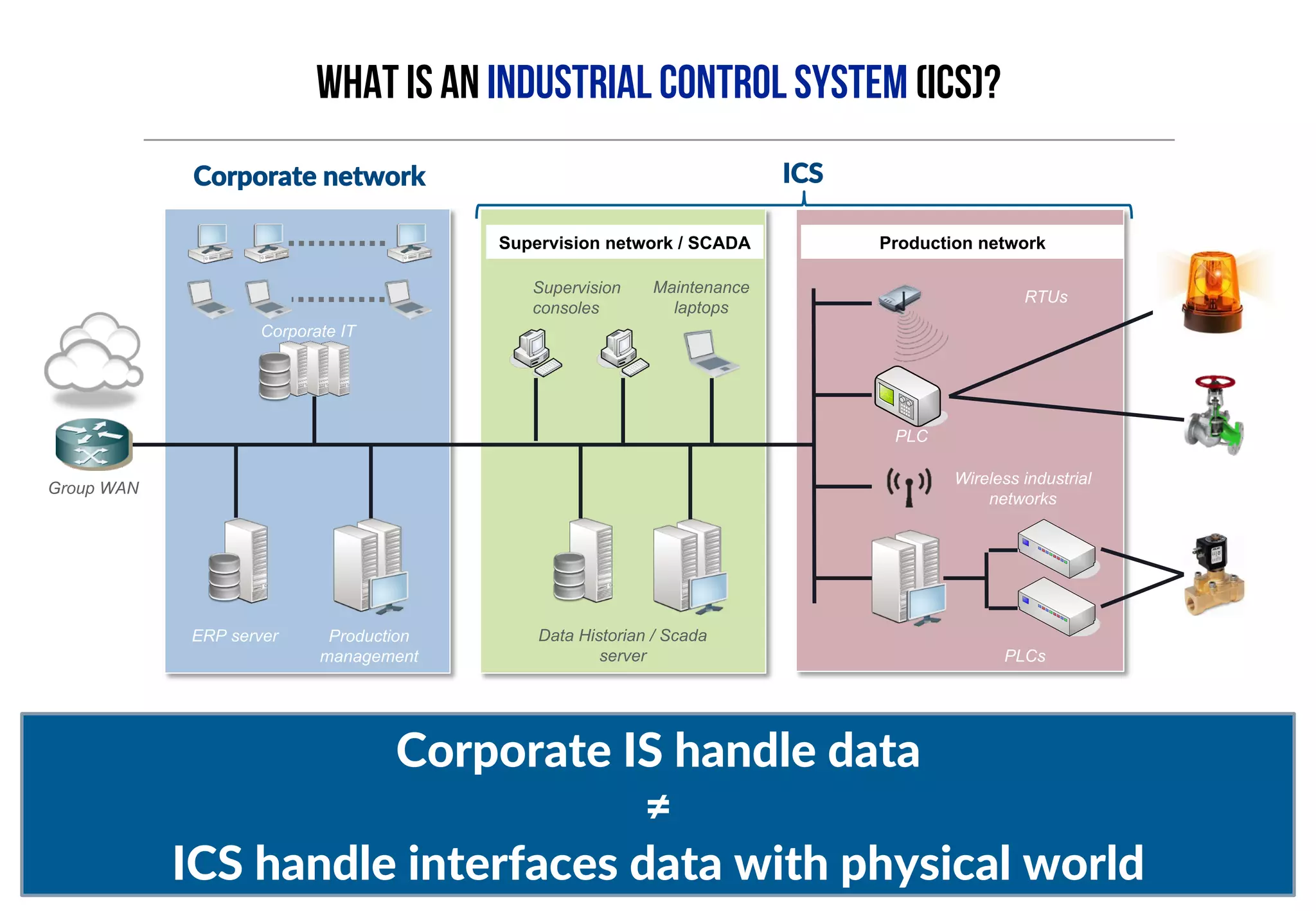
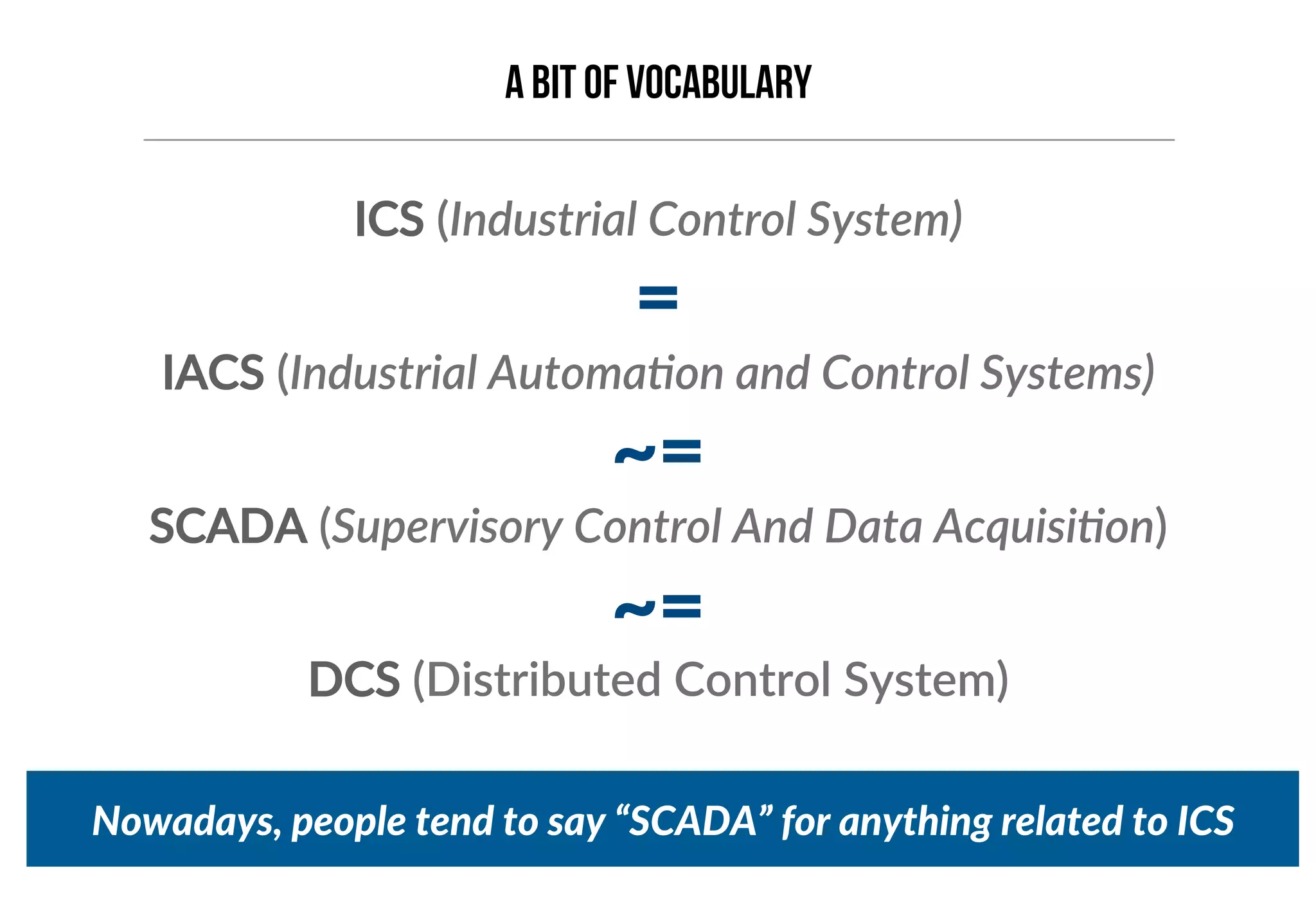
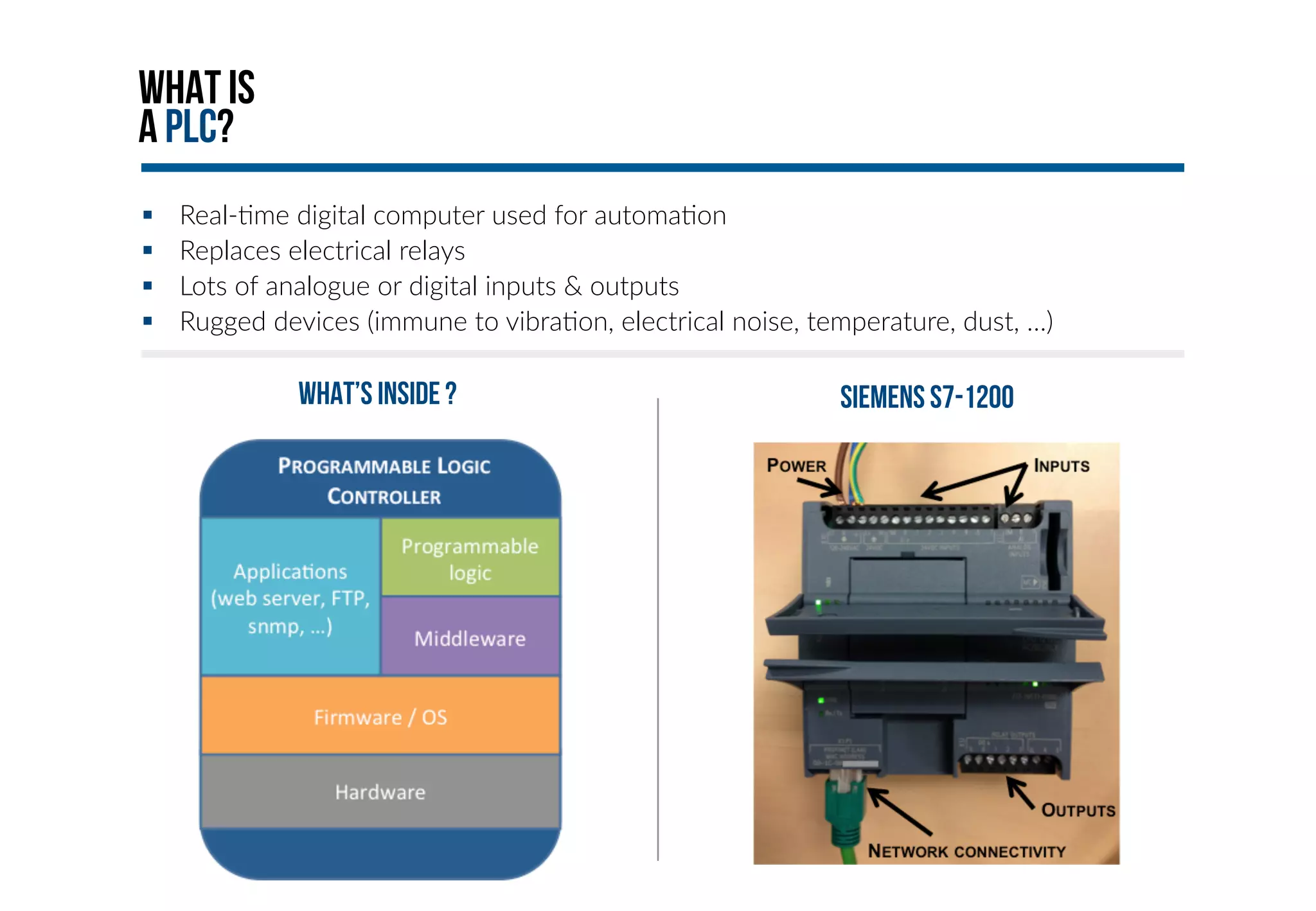
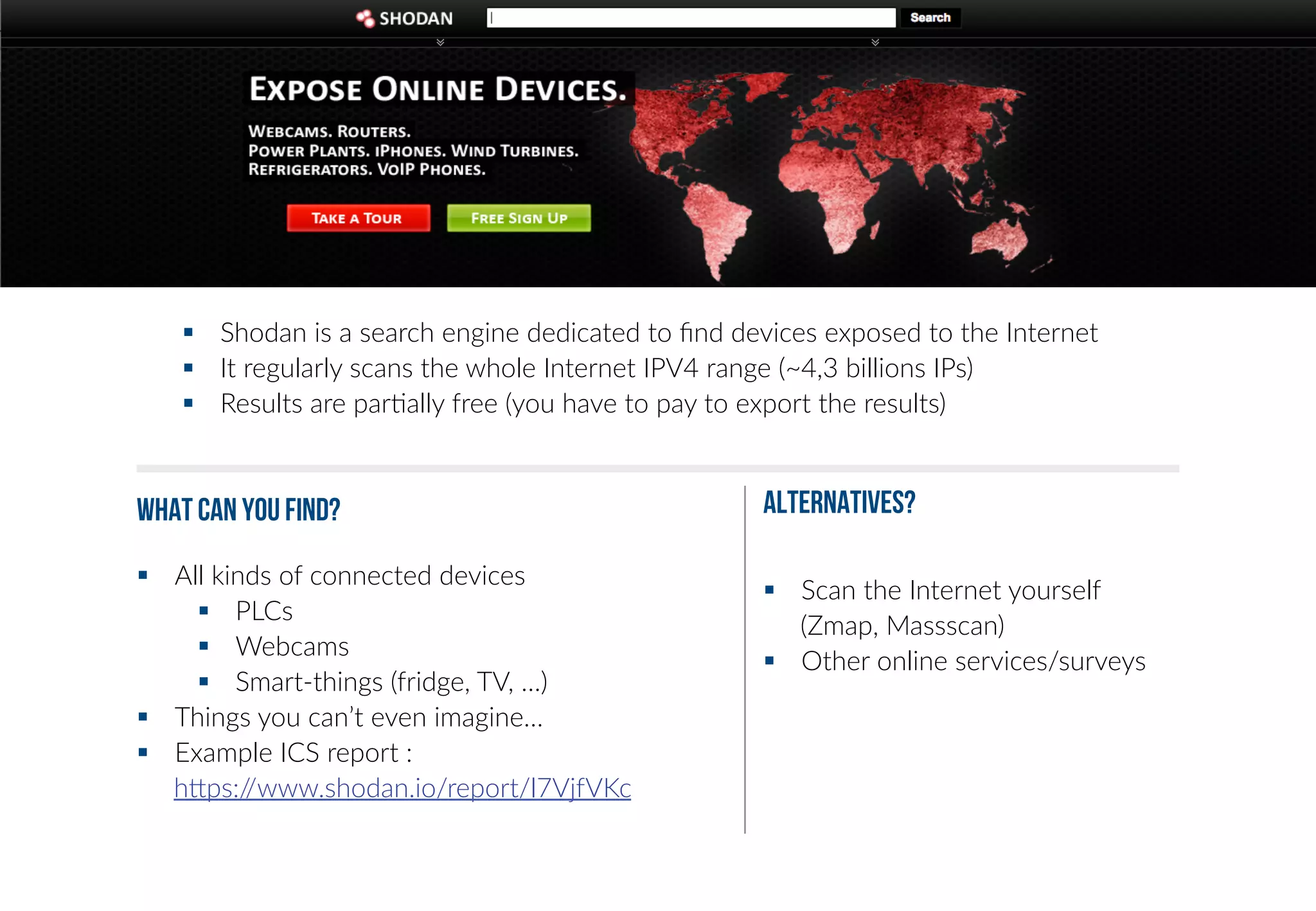
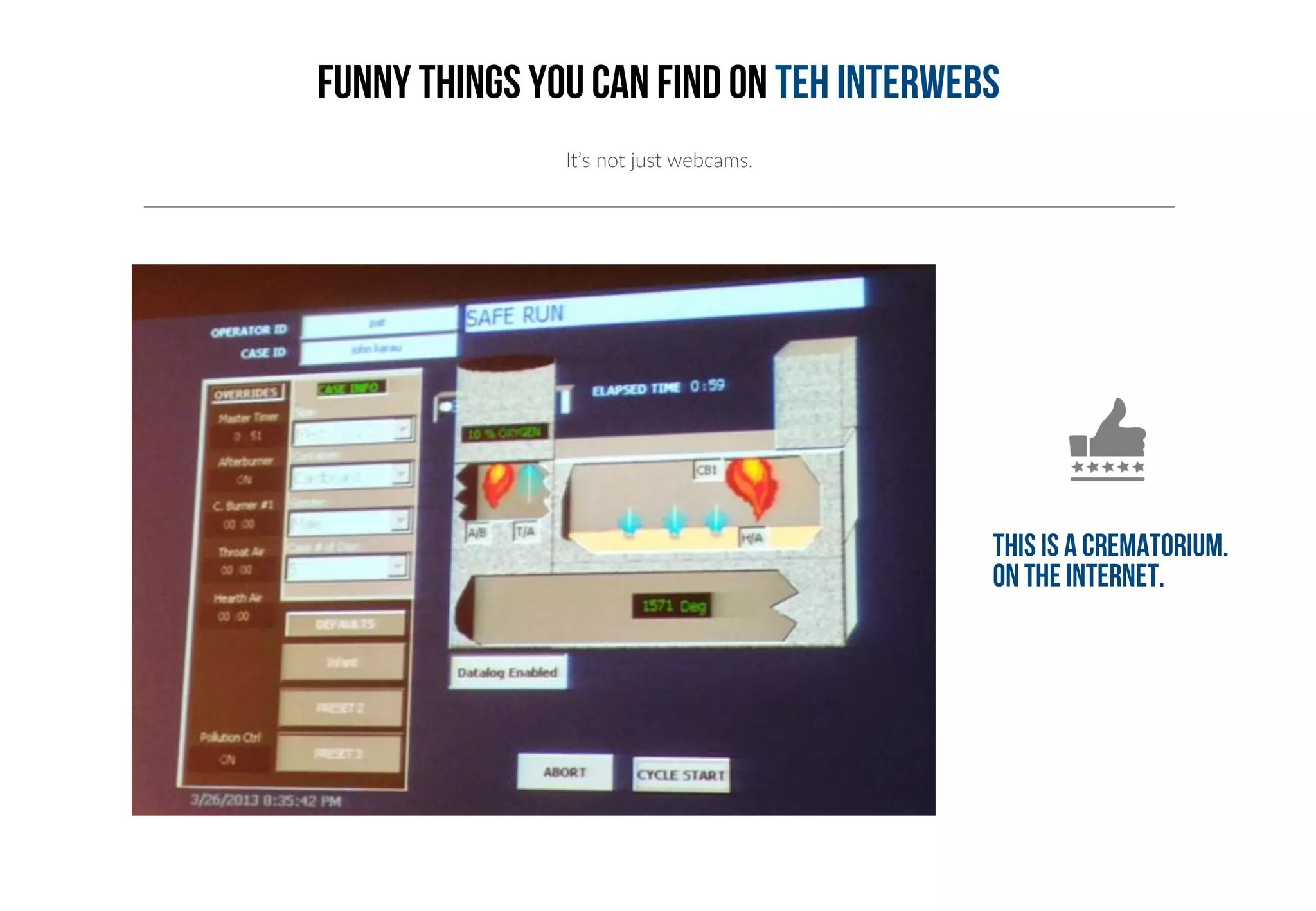
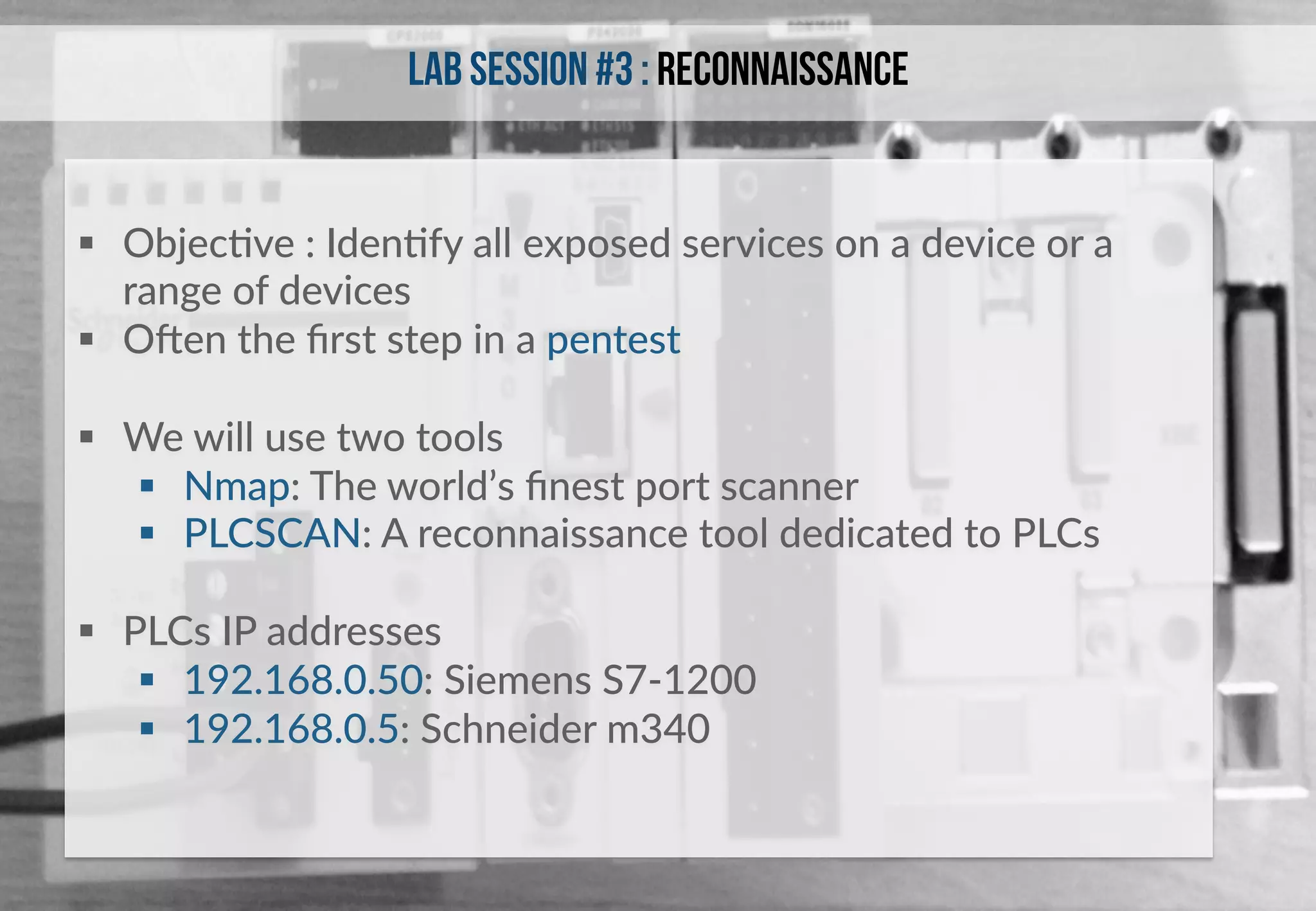
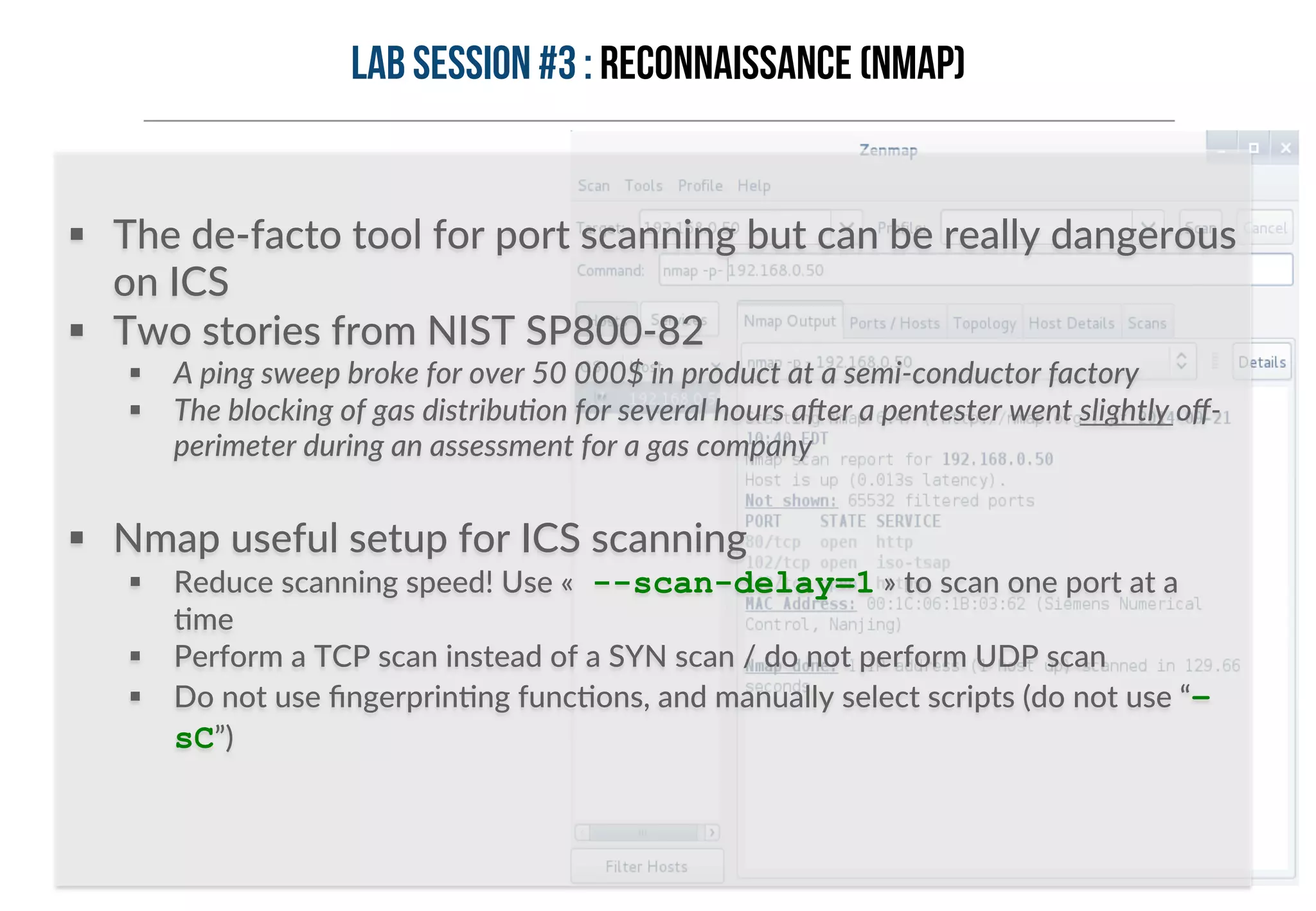
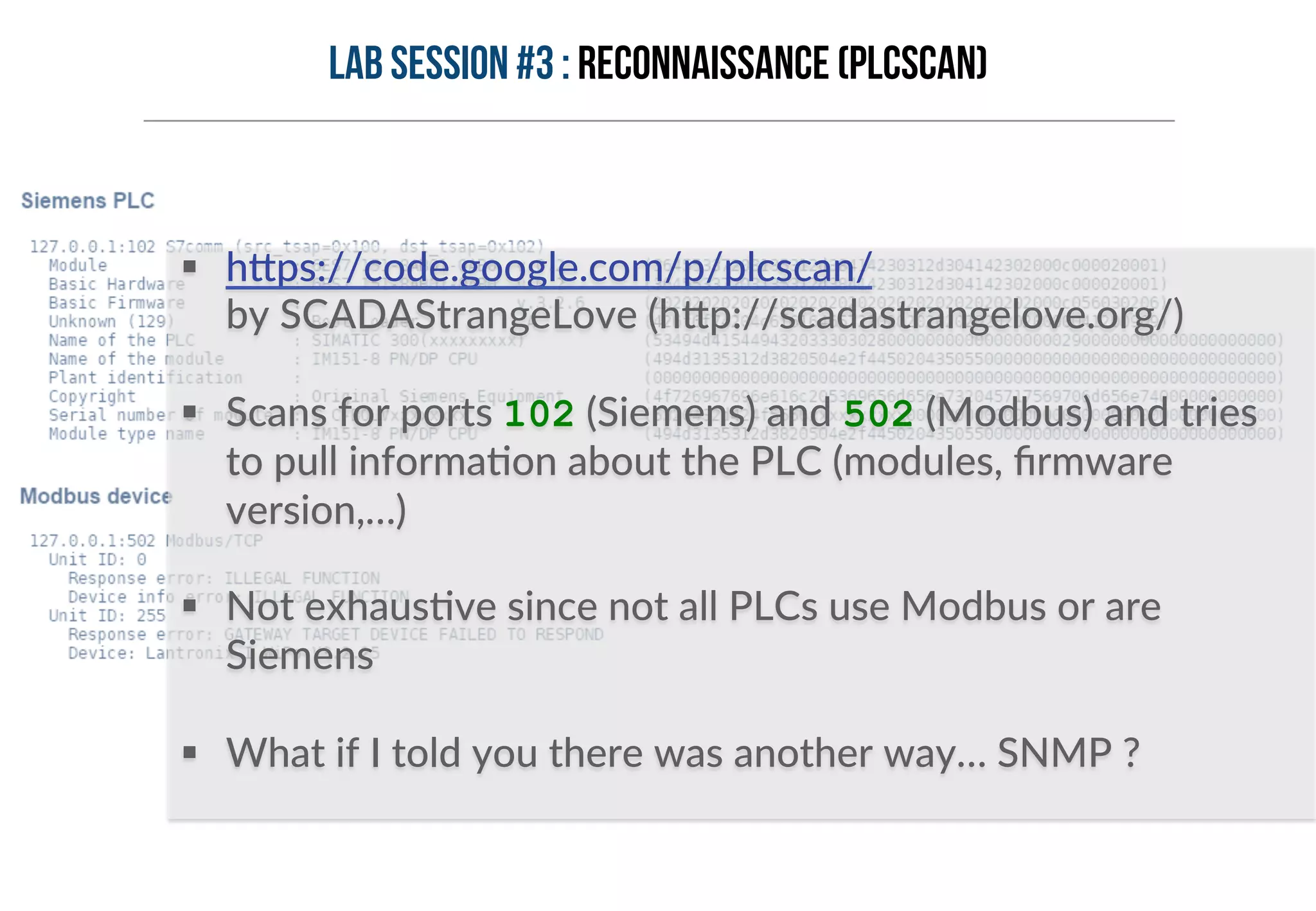
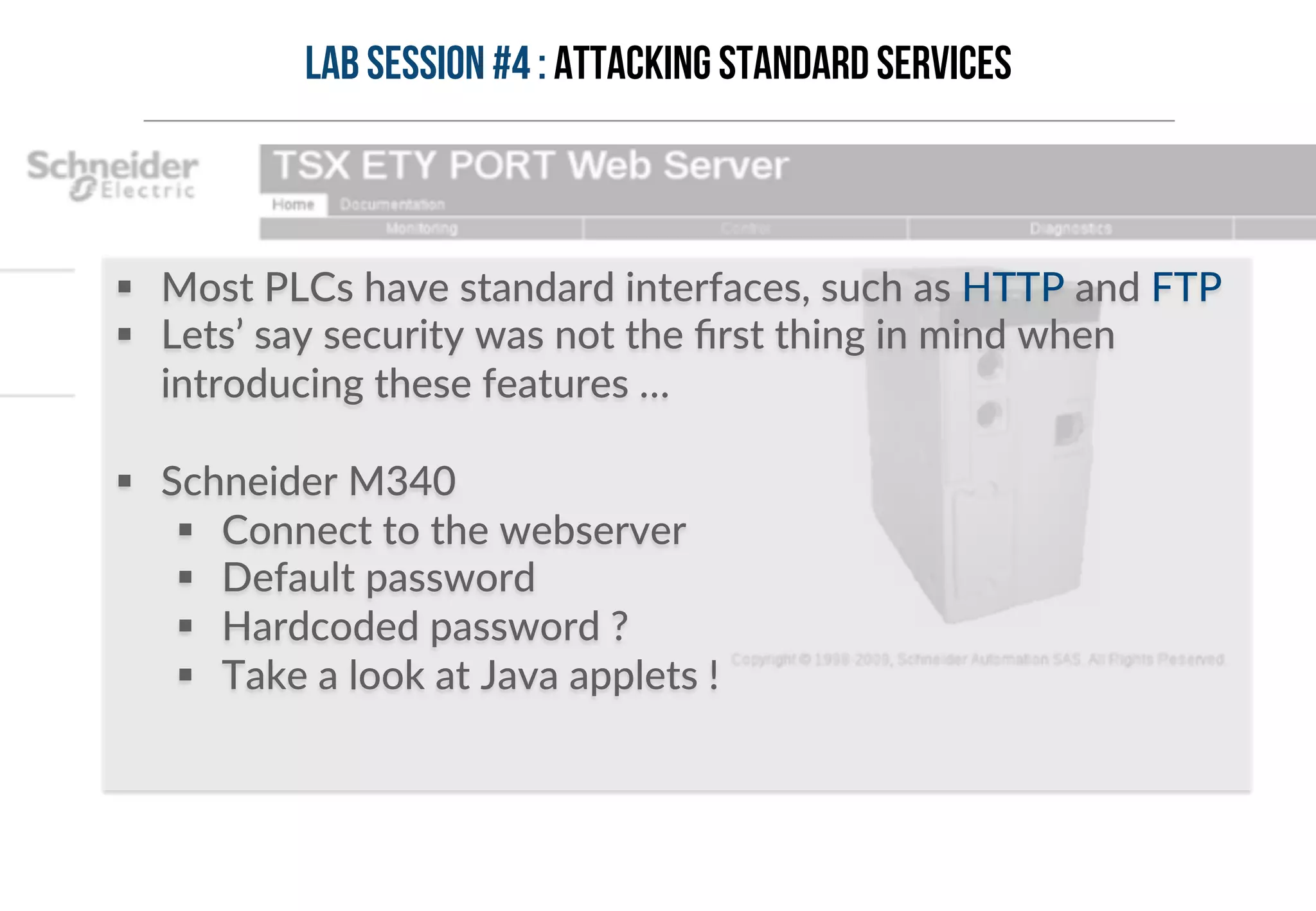
This document provides an overview of industrial control systems (ICS) and Programmable Logic Controllers (PLCs). It discusses the components of ICS, including sensors, actuators, HMIs, PLCs, and more. It also covers the MODBUS protocol commonly used in ICS, providing details on its master/slave architecture and function codes. The document concludes by discussing tools used in the workshop, such as Kali Linux, MBTGET, PLCSCAN, and Metasploit modules, to analyze MODBUS communications, perform reconnaissance on PLCs, and attack standard services and protocols.





![PLC
programming
§ “Ladder Logic” was the first programming language for PLC, as it mimics the real-‐life
circuits
§ IEC 61131-‐3 defines 5 programming languages for PLCs
§ LD: Ladder Diagram
§ FBD: Func+on Block Diagram
§ ST: Structured Text
§ IL: Instruc+on List
§ SFC: Sequen+al Func+on Chart
Ladder diagram example Structured text example
(* simple state machine *)
TxtState := STATES[StateMachine];
CASE StateMachine OF
1: ClosingValve();
ELSE
;; BadCase();
END_CASE;
Instruction list example
LD Speed
GT 1000
JMPCN VOLTS_OK
LD Volts
VOLTS_OK LD 1
ST %Q75](https://image.slidesharecdn.com/introductiontoindustrialcontrolsystemsicsv1-141019075916-conversion-gate01/75/Introduction-to-Industrial-Control-Systems-Pentesting-PLCs-101-BlackHat-Europe-2014-15-2048.jpg)


![www.solucom.fr
Contact
Arnaud SOULLIE
Senior consultant
arnaud.soullie[AT]solucom.fr](https://image.slidesharecdn.com/introductiontoindustrialcontrolsystemsicsv1-141019075916-conversion-gate01/75/Introduction-to-Industrial-Control-Systems-Pentesting-PLCs-101-BlackHat-Europe-2014-36-2048.jpg)