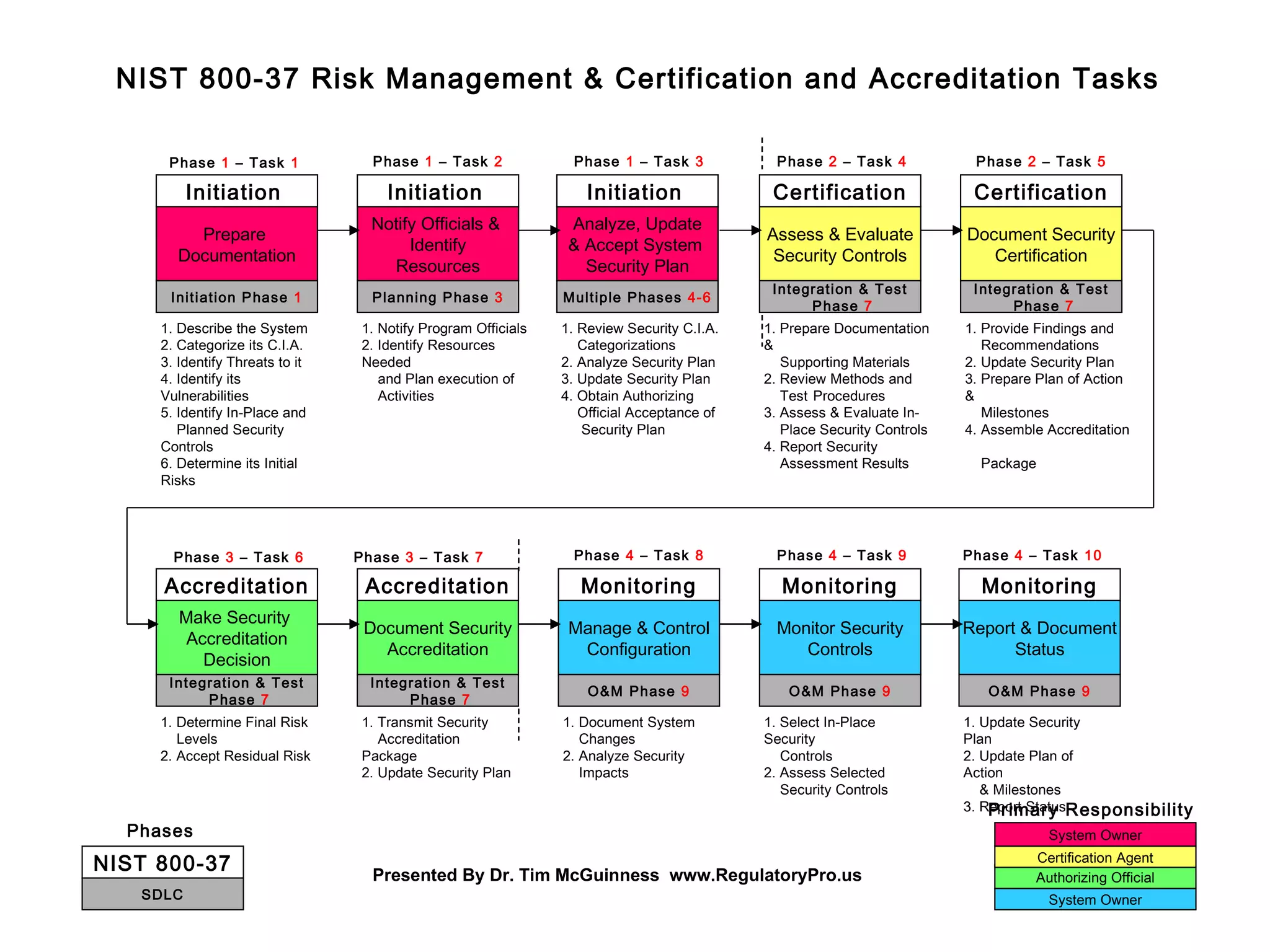
The document outlines the tasks and responsibilities involved in assessing and maintaining the security of a system over multiple phases, according to NIST 800-37. It describes 10 phases organized in 4 categories: initiation, planning, operations and maintenance, and integration and testing. The phases involve initial risk assessment, planning resource needs, ongoing monitoring and management of security controls, assessing controls, and authorizing use of the system. Responsibilities are assigned to different roles at each phase.