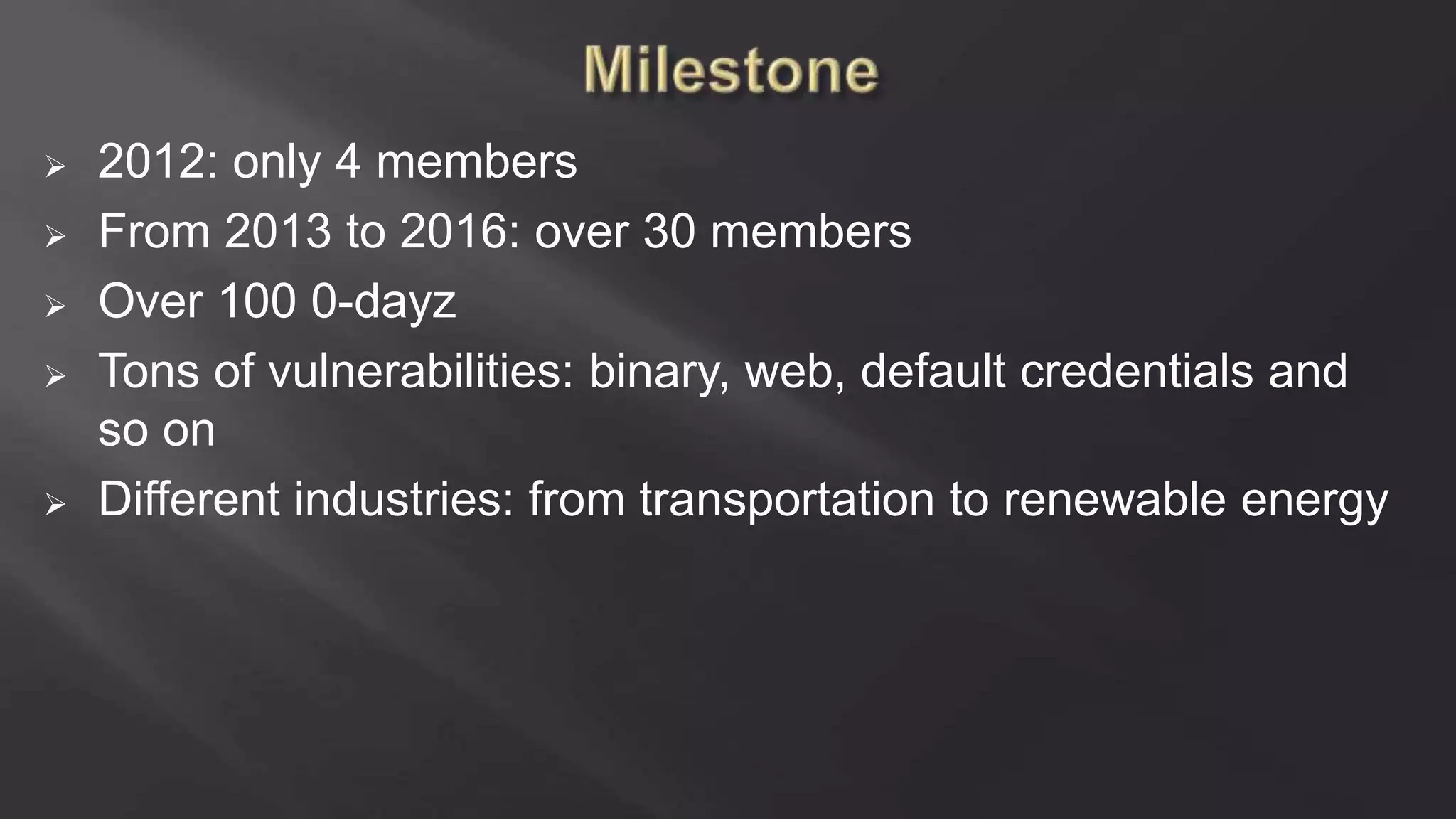
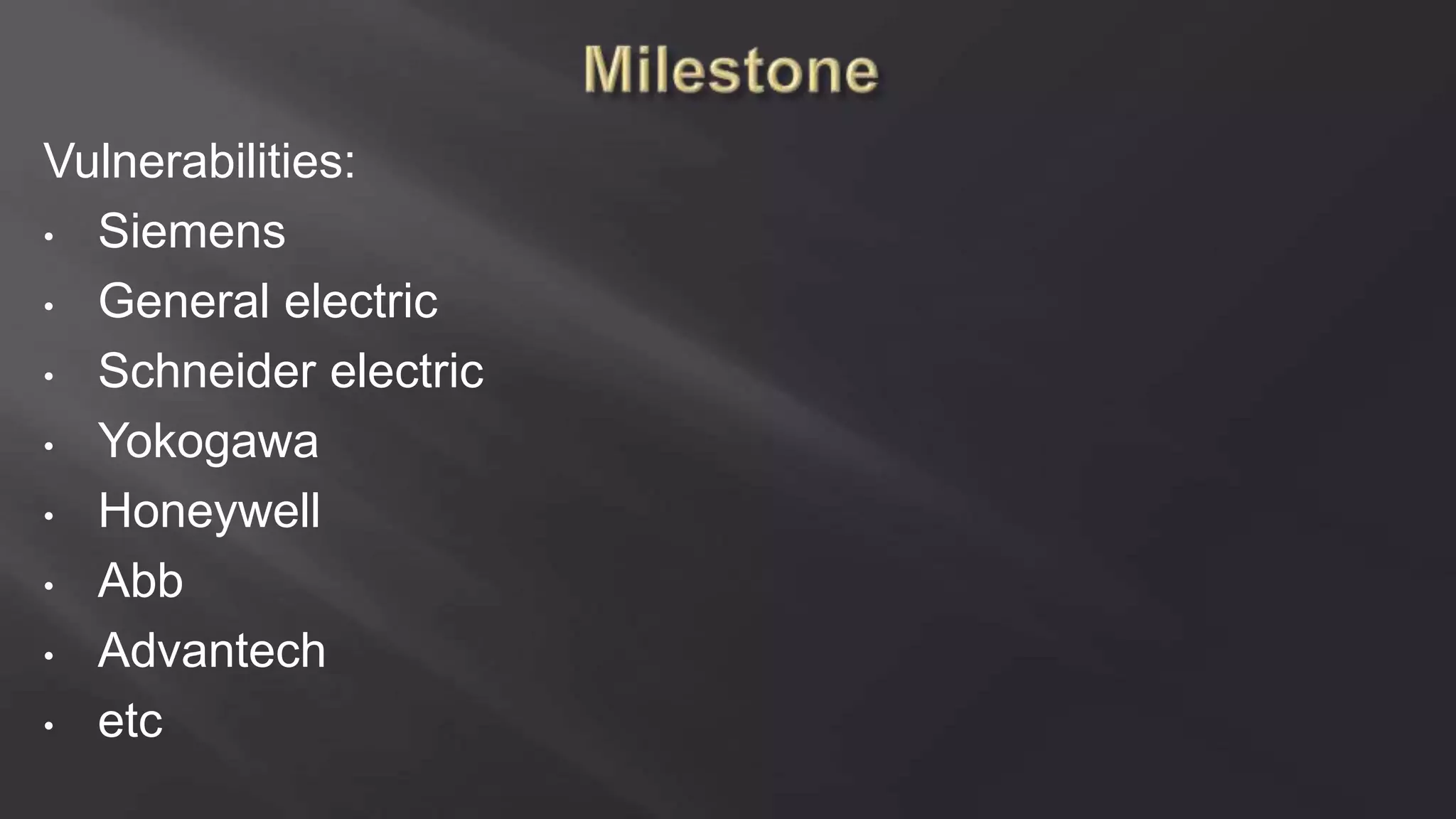
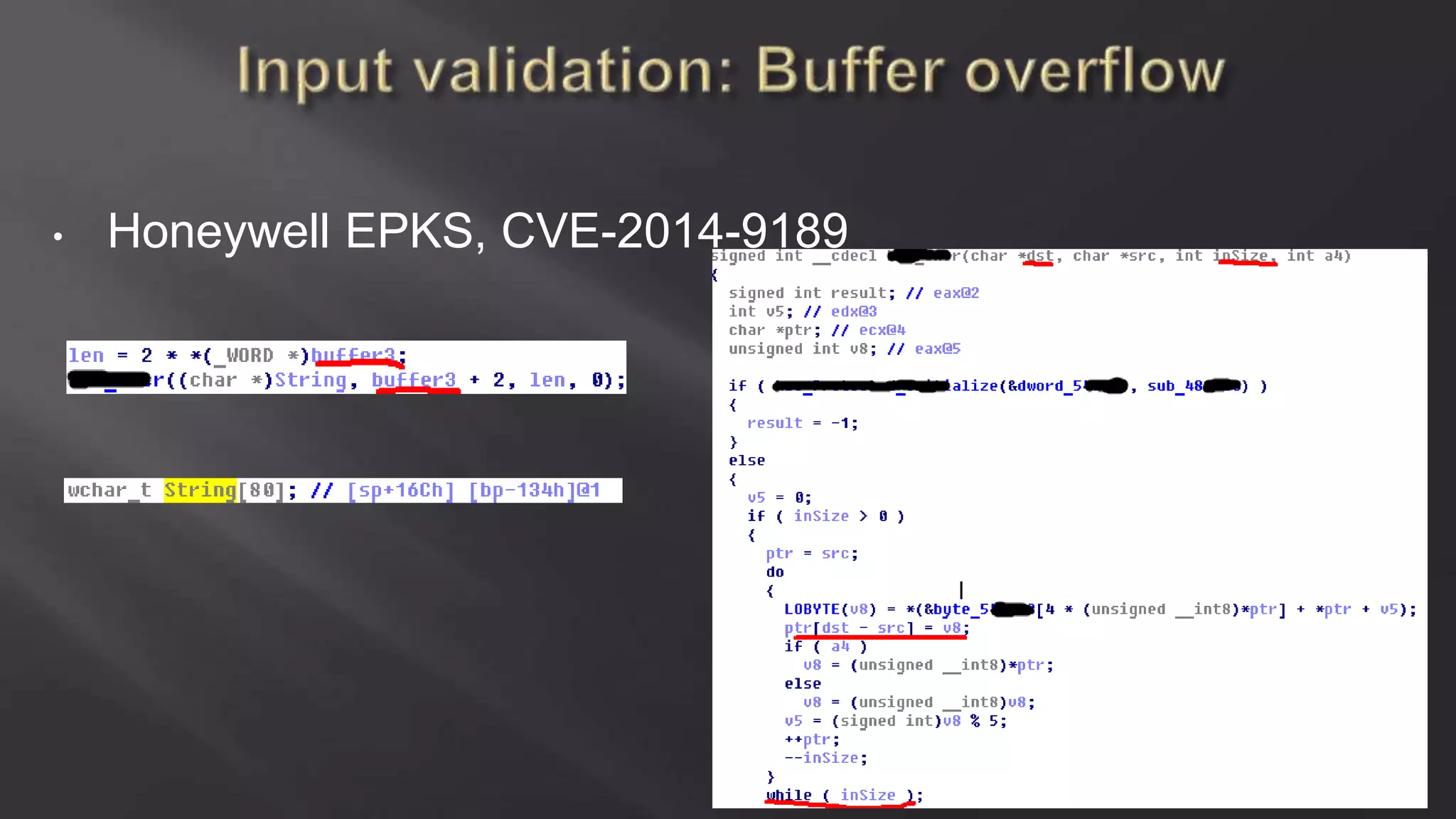
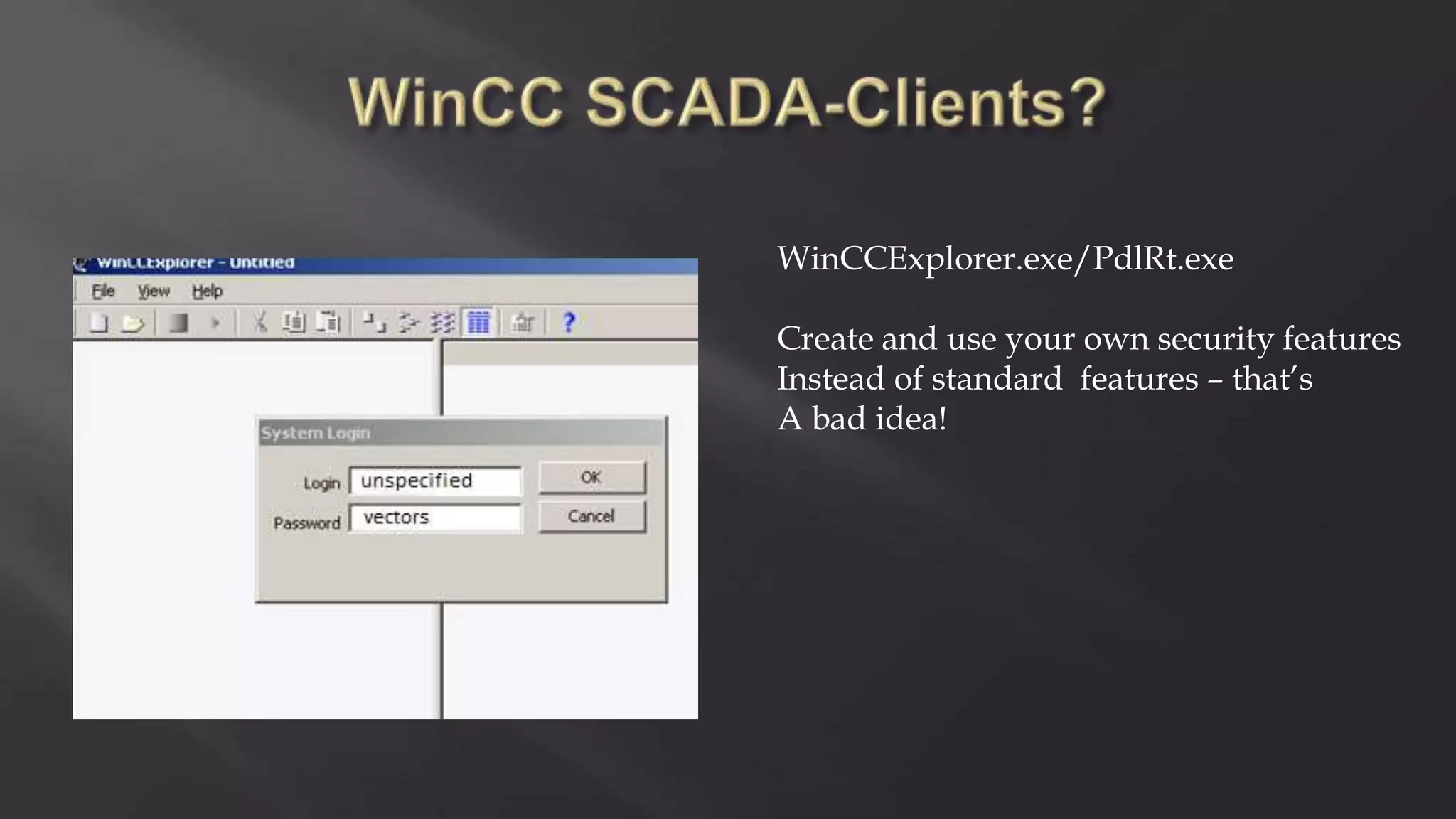
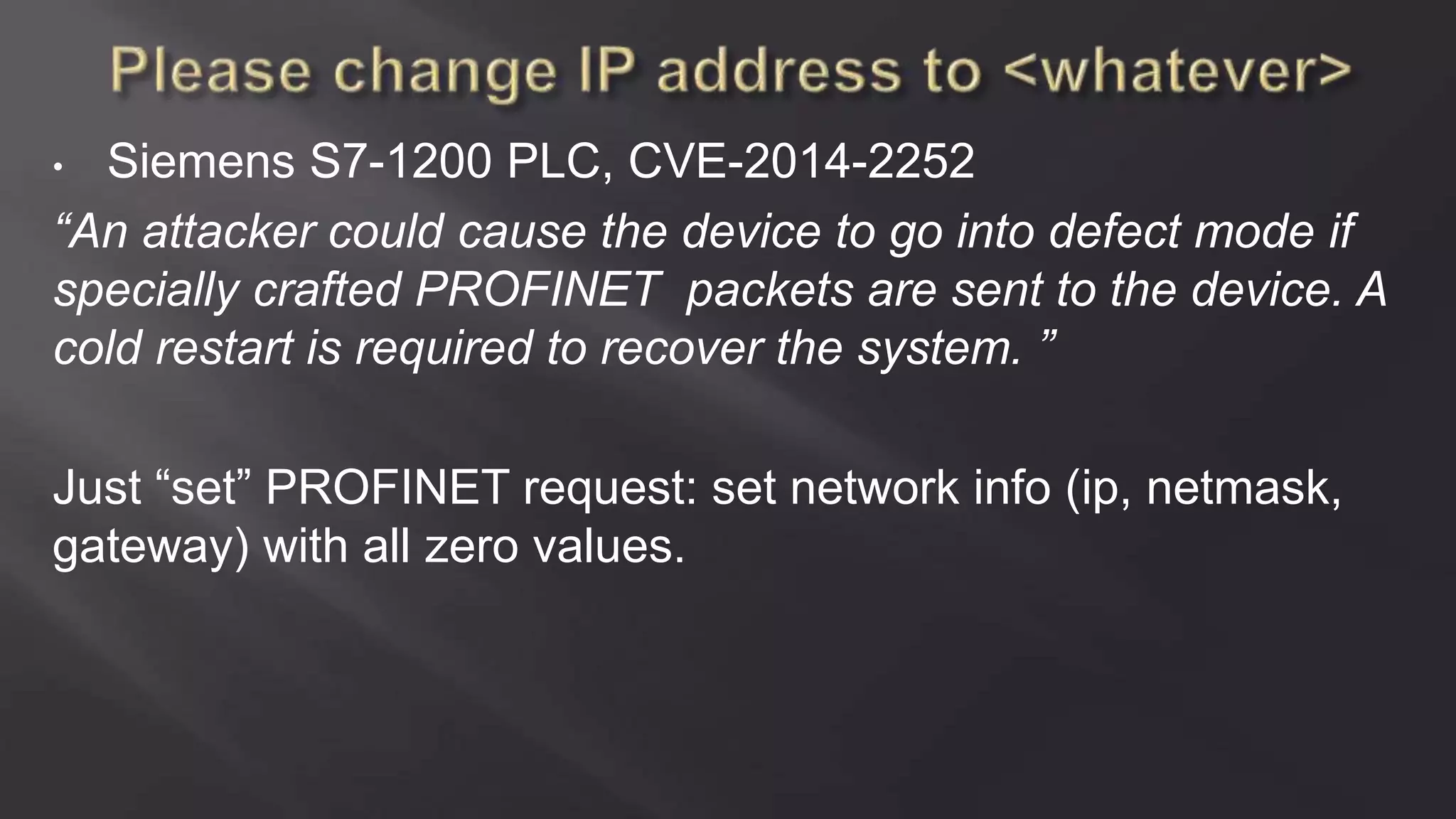
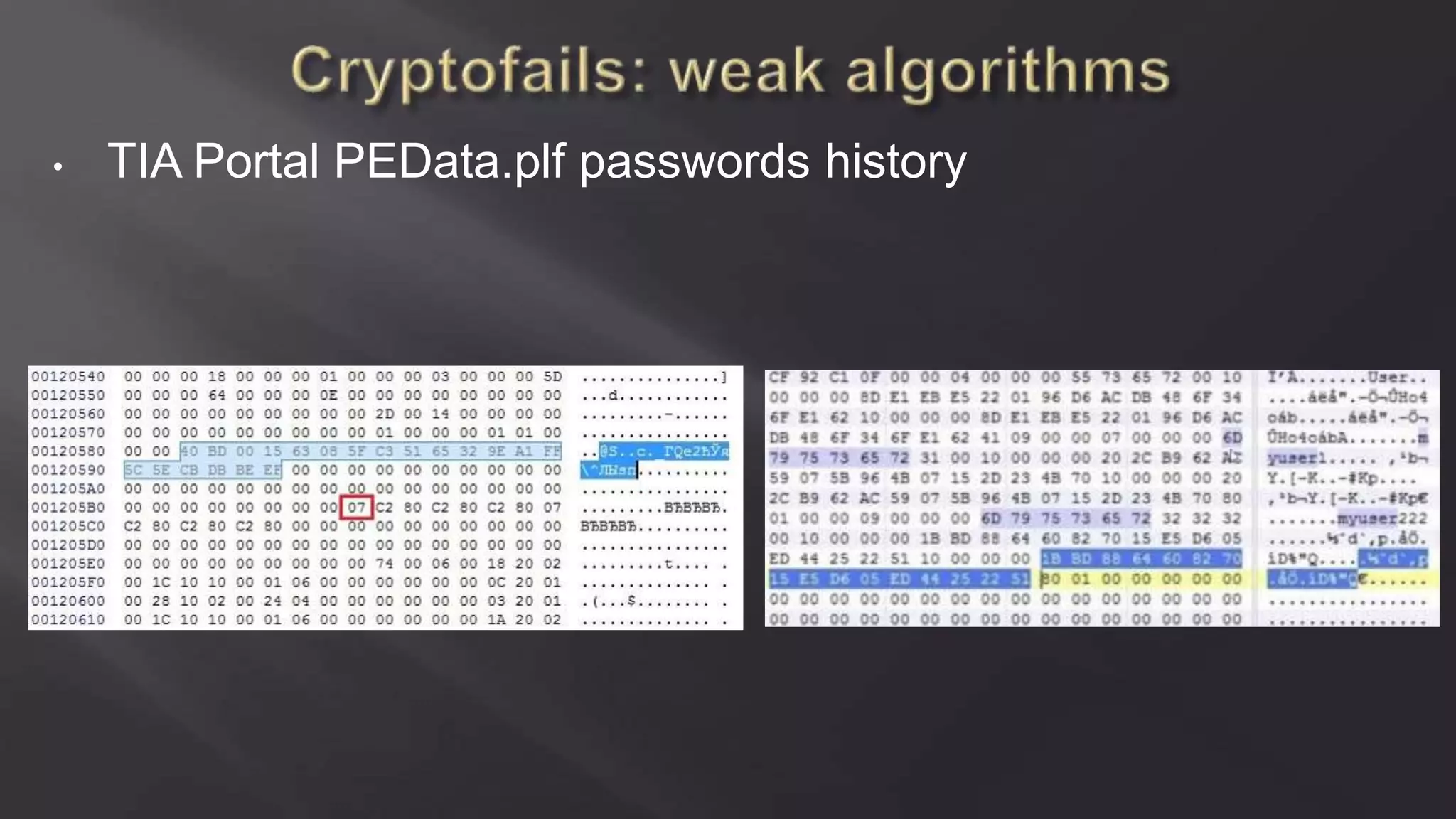
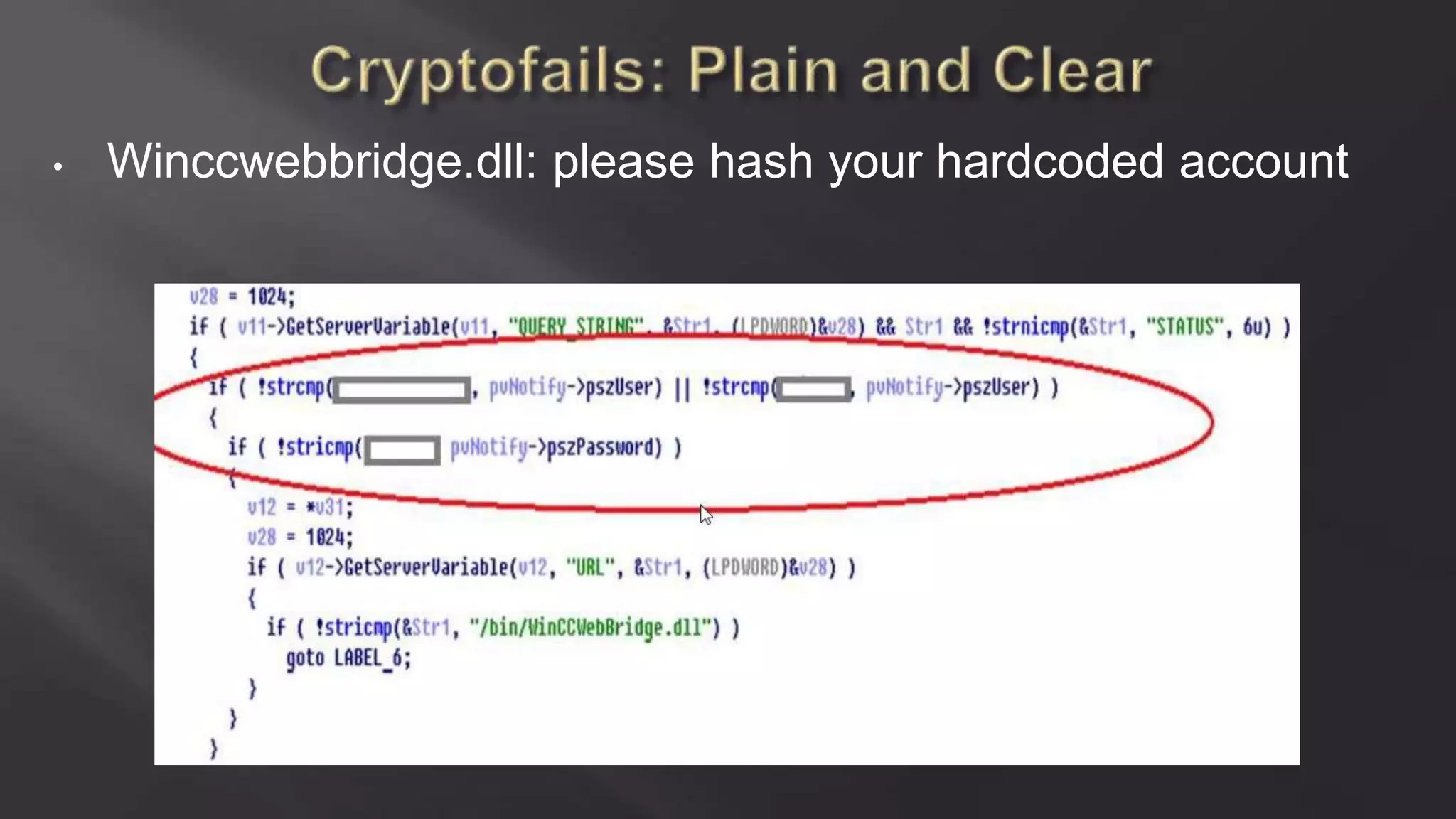
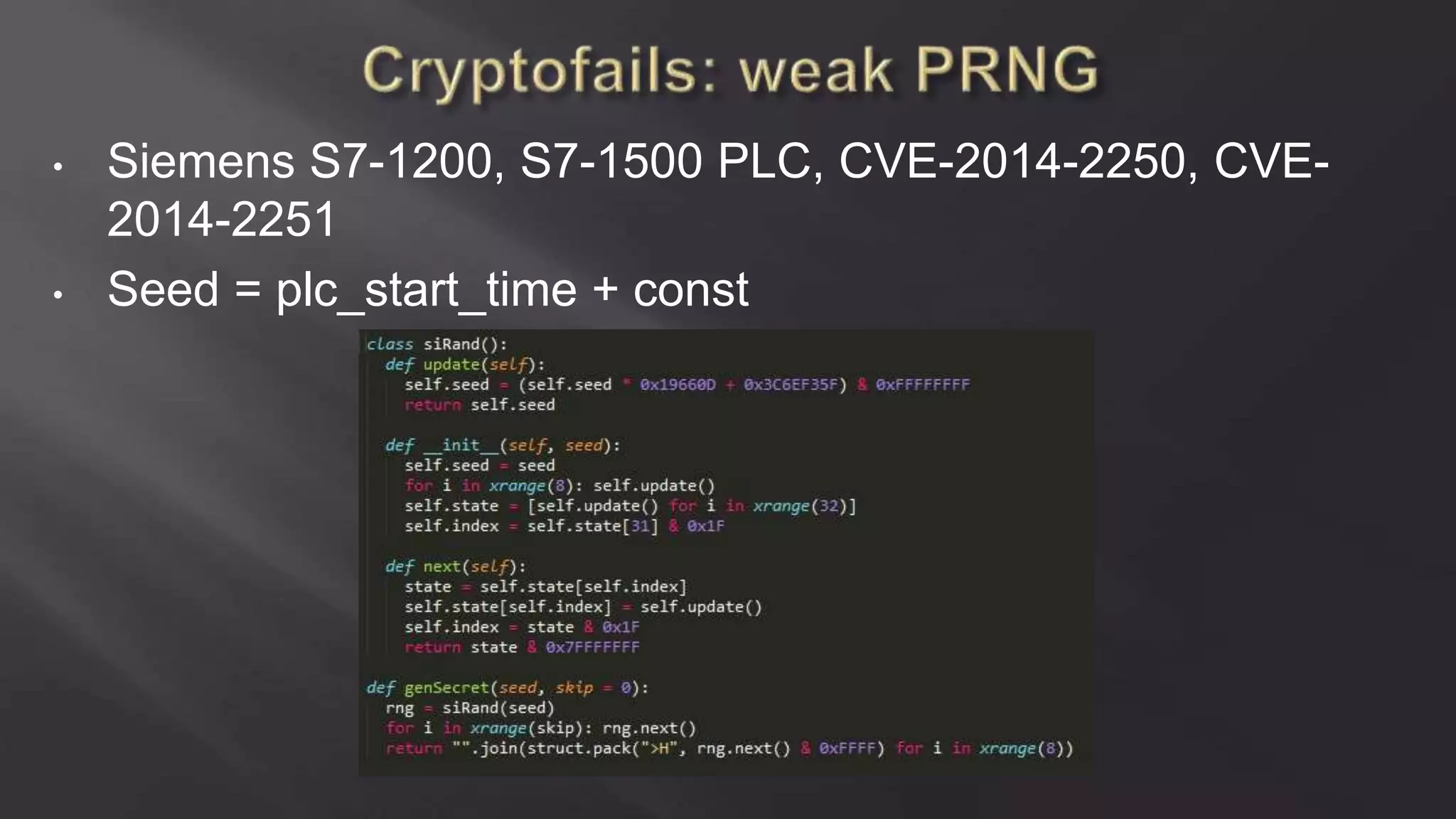
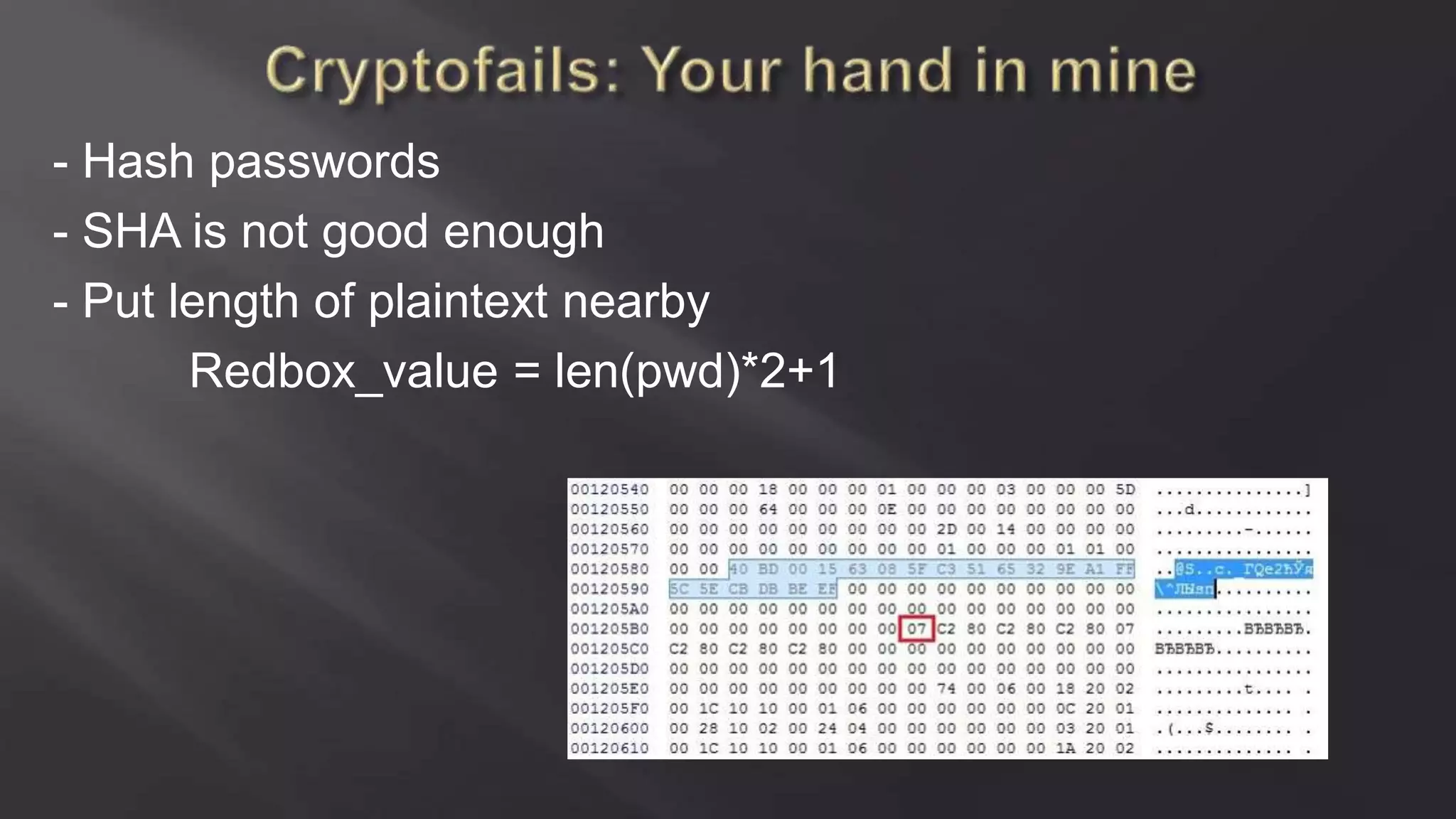
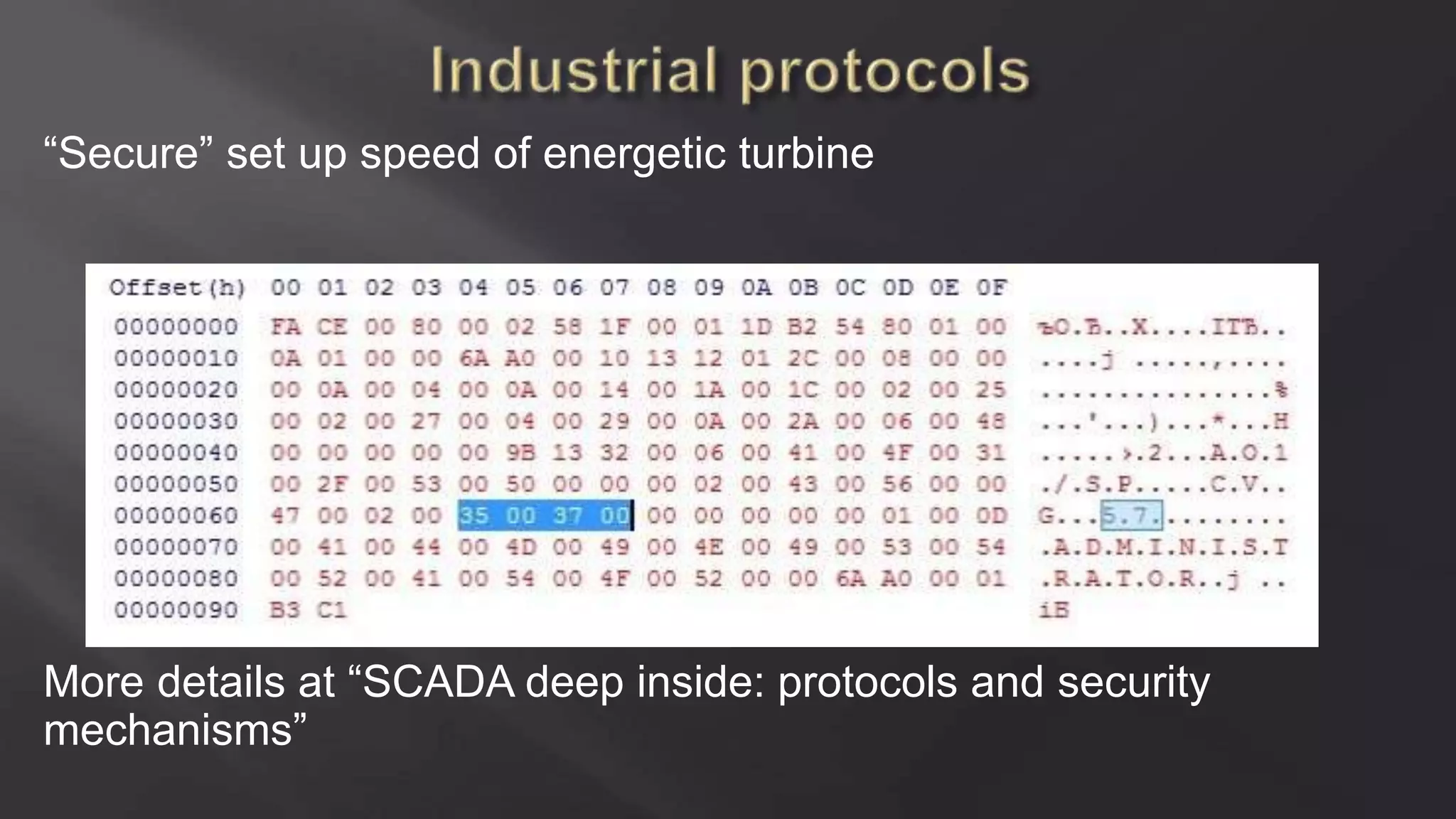
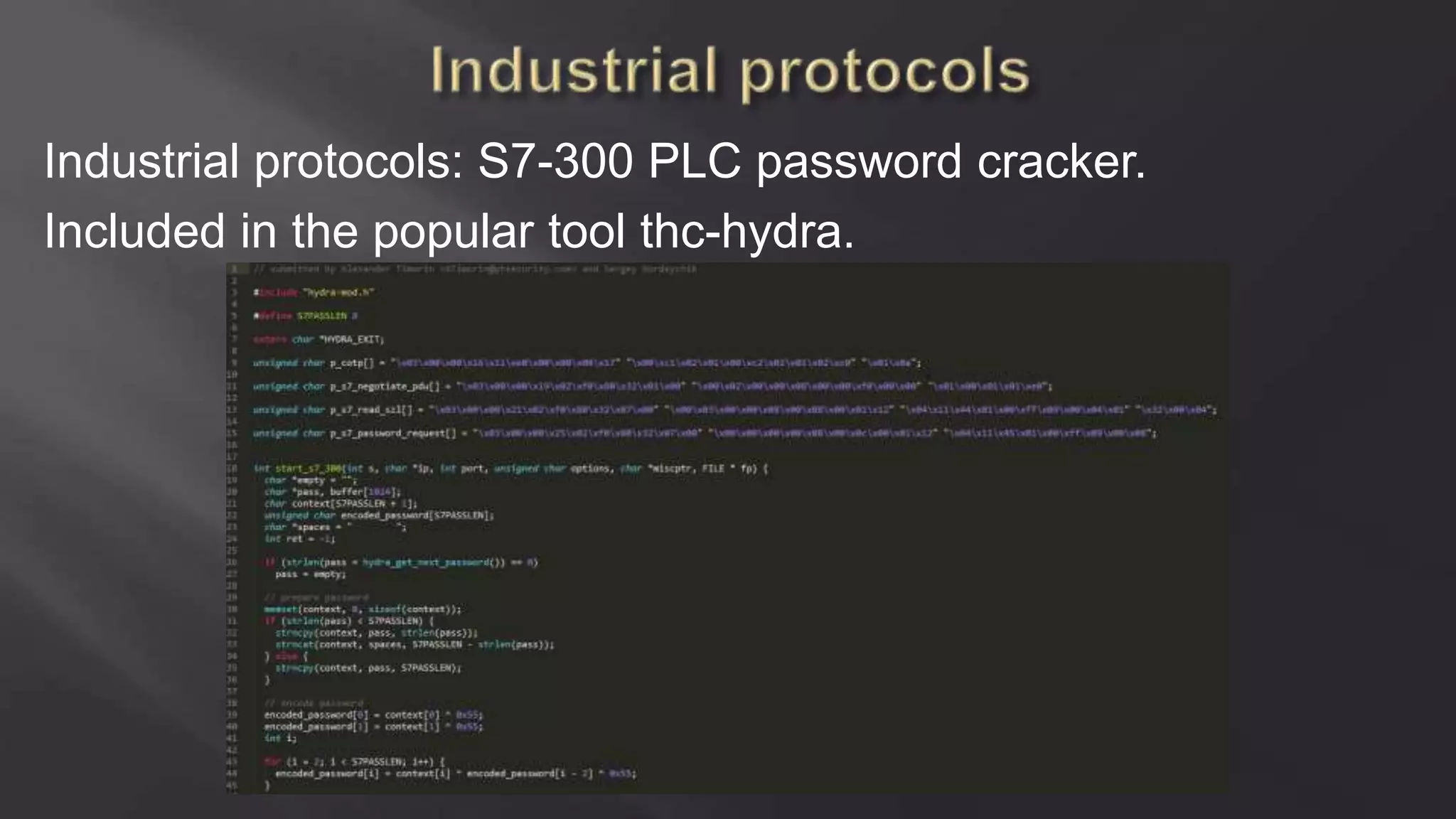
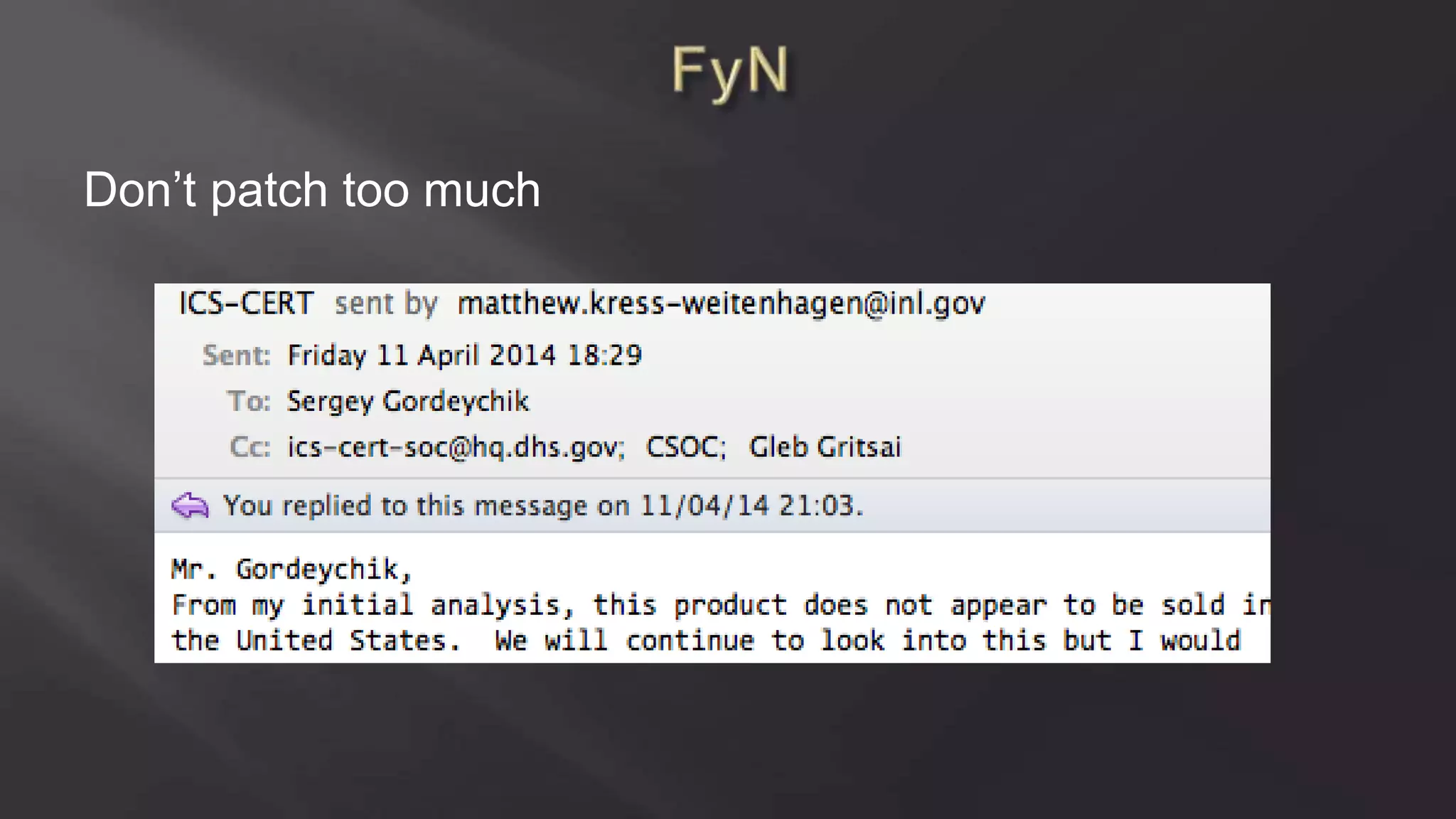
SCADASTRANGELOVE is a group of security researchers focused on ICS/SCADA security. They have discovered over 100 vulnerabilities in industrial control systems and devices since 2012. Their goal is to raise awareness of security issues in critical infrastructure systems and work with a responsible disclosure process to help vendors patch vulnerabilities.