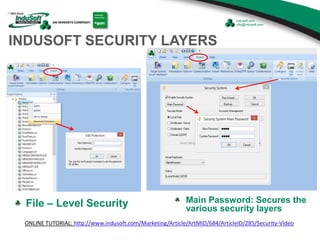
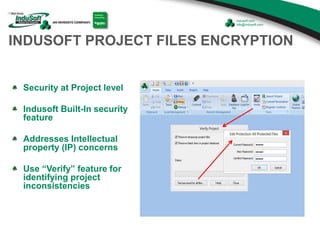
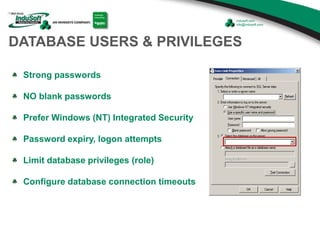
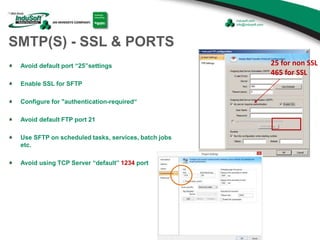
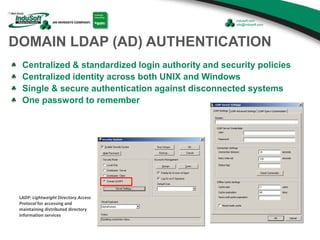
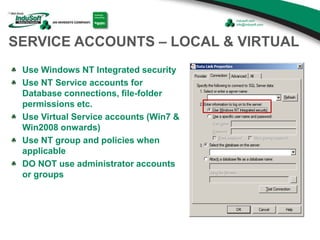
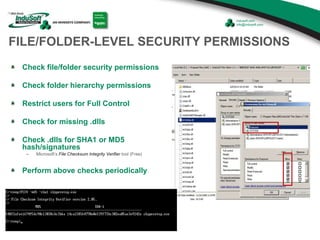
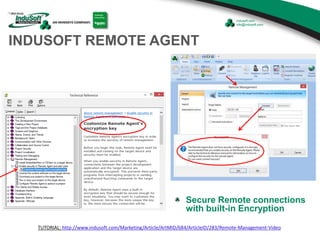
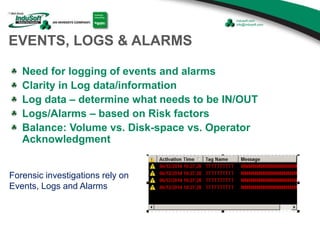
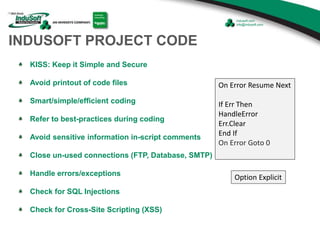
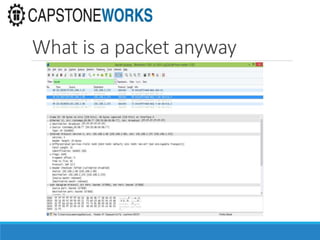
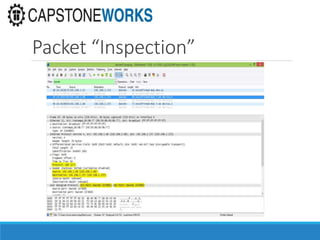
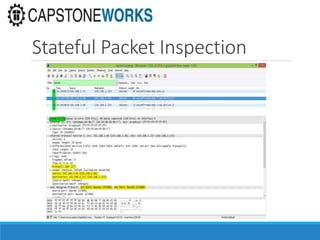
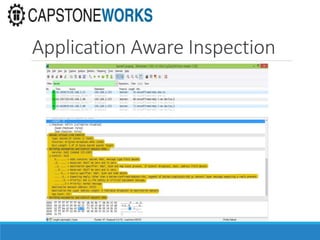
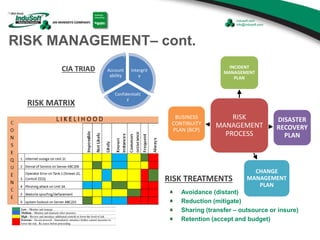
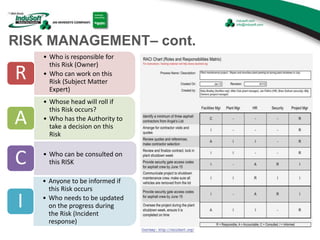
The document discusses cybersecurity considerations for SCADA and HMI systems using InduSoft Web Studio. It begins with an agenda that includes enhancing cybersecurity on InduSoft projects and firewalls and other SCADA security considerations. The document then discusses guidelines for improving security on InduSoft projects such as implementing risk management processes, using strong passwords, encrypting sensitive data, and configuring appropriate network, database, file, and project security. It emphasizes the importance of cybersecurity awareness, training and certifications to enhance security.







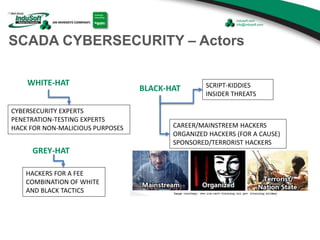







![SECURITY BEYOND PASSWORDS - contd
Project Security design
should address:
– Runtime Security
– Engineering Access
– Auto Log-Off options
– Account Lockup (after 3 tries)
[to be strictly enforced]
– Password options enforcement](https://image.slidesharecdn.com/20140716scadaandhmisecurityinindusoftwebstudio-140717135230-phpapp02/85/SCADA-and-HMI-Security-in-InduSoft-Web-Studio-18-320.jpg)