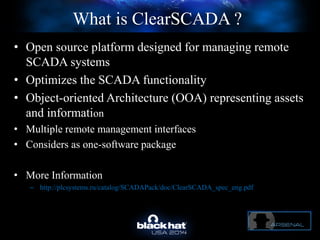
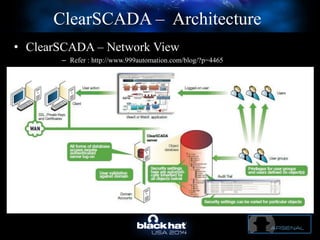
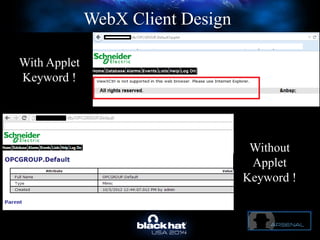
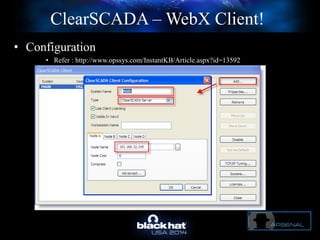
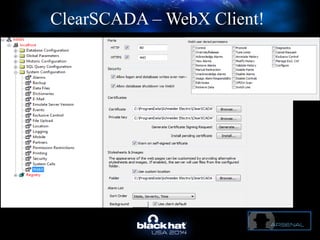
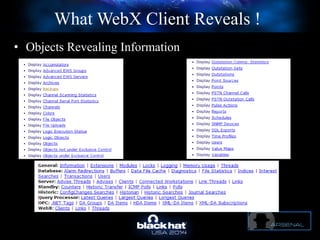
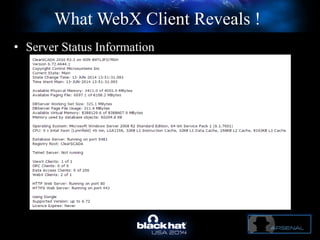
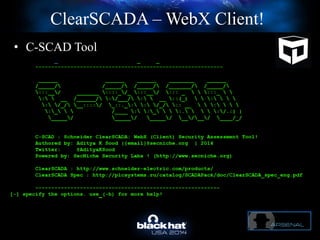
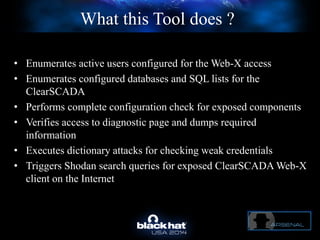
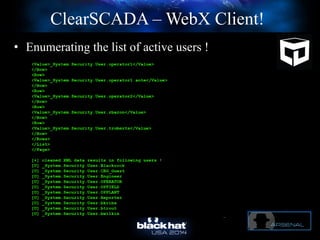
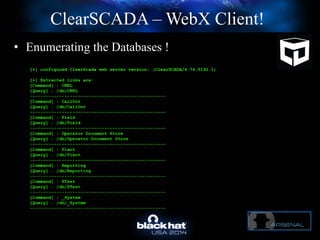
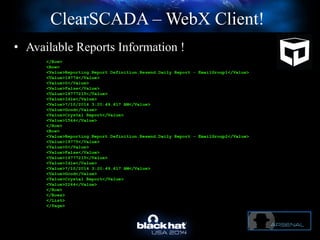
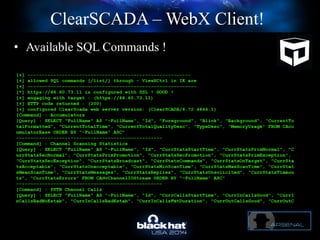
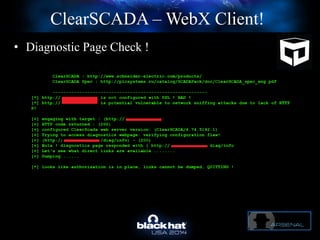
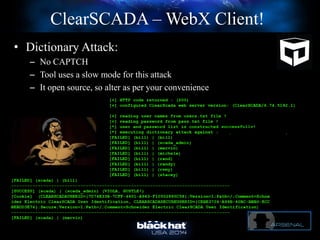
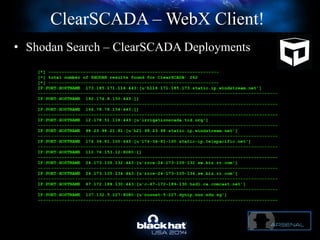
The document discusses C-Scad, a tool designed for assessing security vulnerabilities in the ClearSCADA WebX client. It details its capabilities, such as user enumeration, database checks, and vulnerability integration, emphasizing the need for dedicated SCADA penetration testing tools due to the security risks associated with the WebX client. The conclusion highlights the importance of tailored security assessments, as standard tools may not adequately evaluate the software's context.