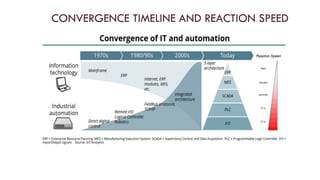
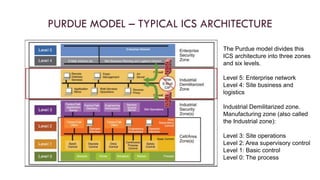
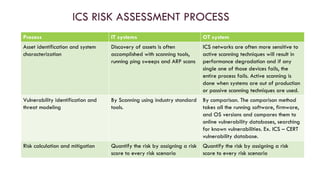
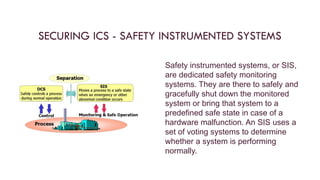
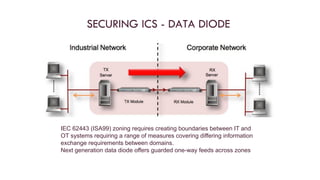
The document discusses the unique security challenges associated with industrial control systems (ICS) and SCADA systems, highlighting their critical role in infrastructure and vulnerability to cyber threats due to increased connectivity. It outlines the differences between IT and operational technology (OT) systems, emphasizing the need for convergence for efficiency while also exposing ICS to greater risk. The document also addresses risk assessment processes, defense strategies like defense-in-depth, and the importance of policies, procedures, and safety systems in securing ICS.