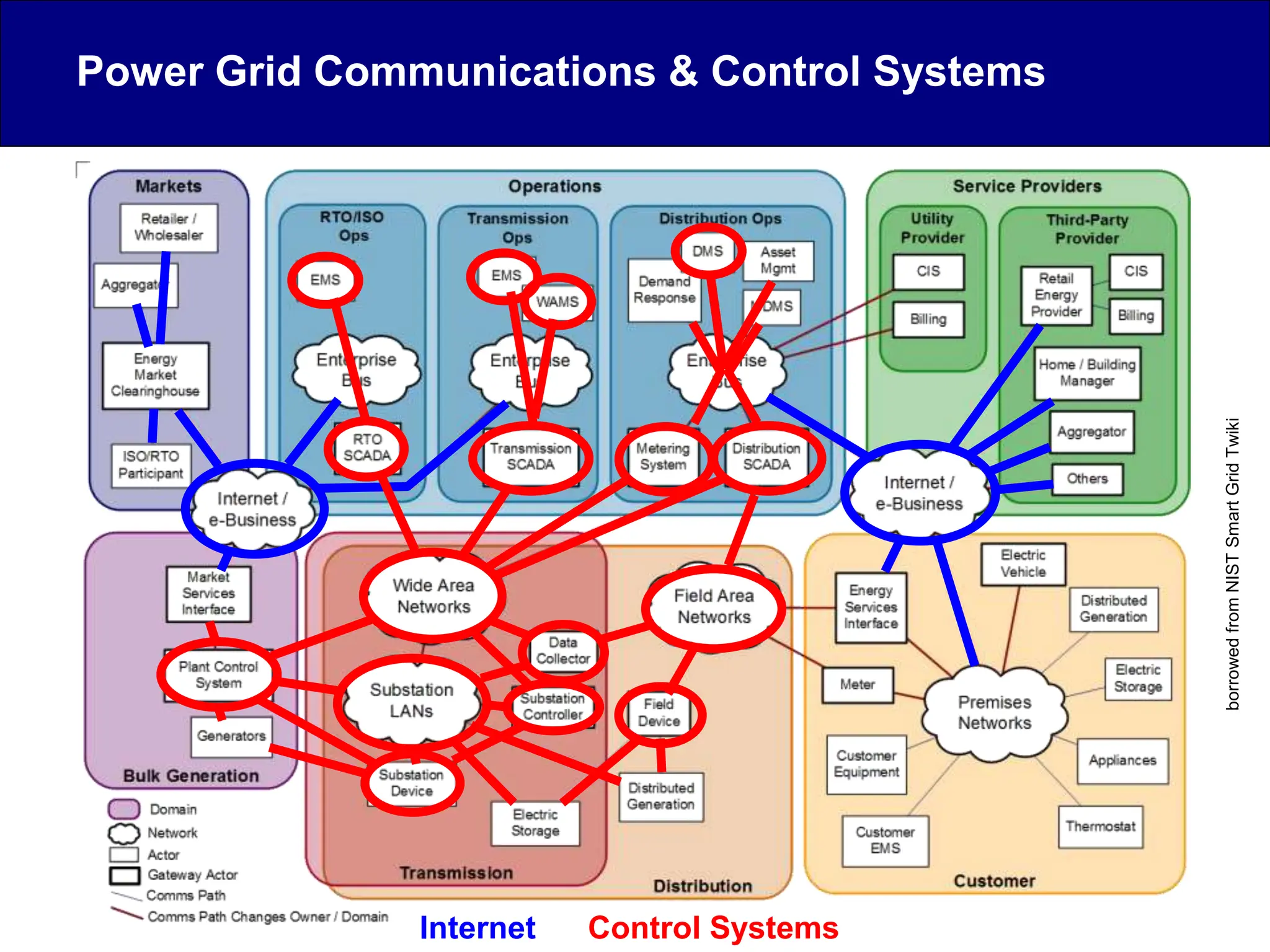
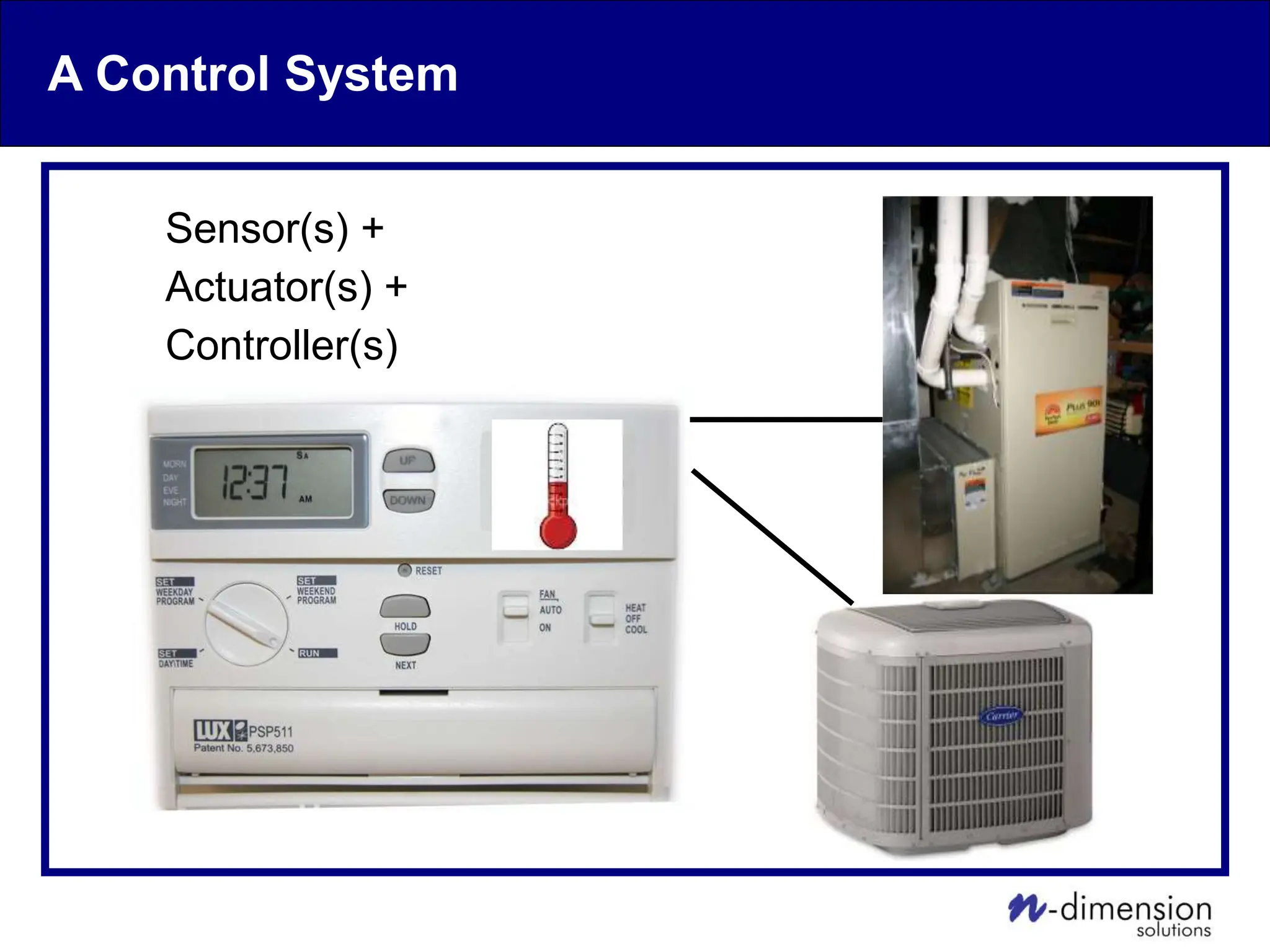
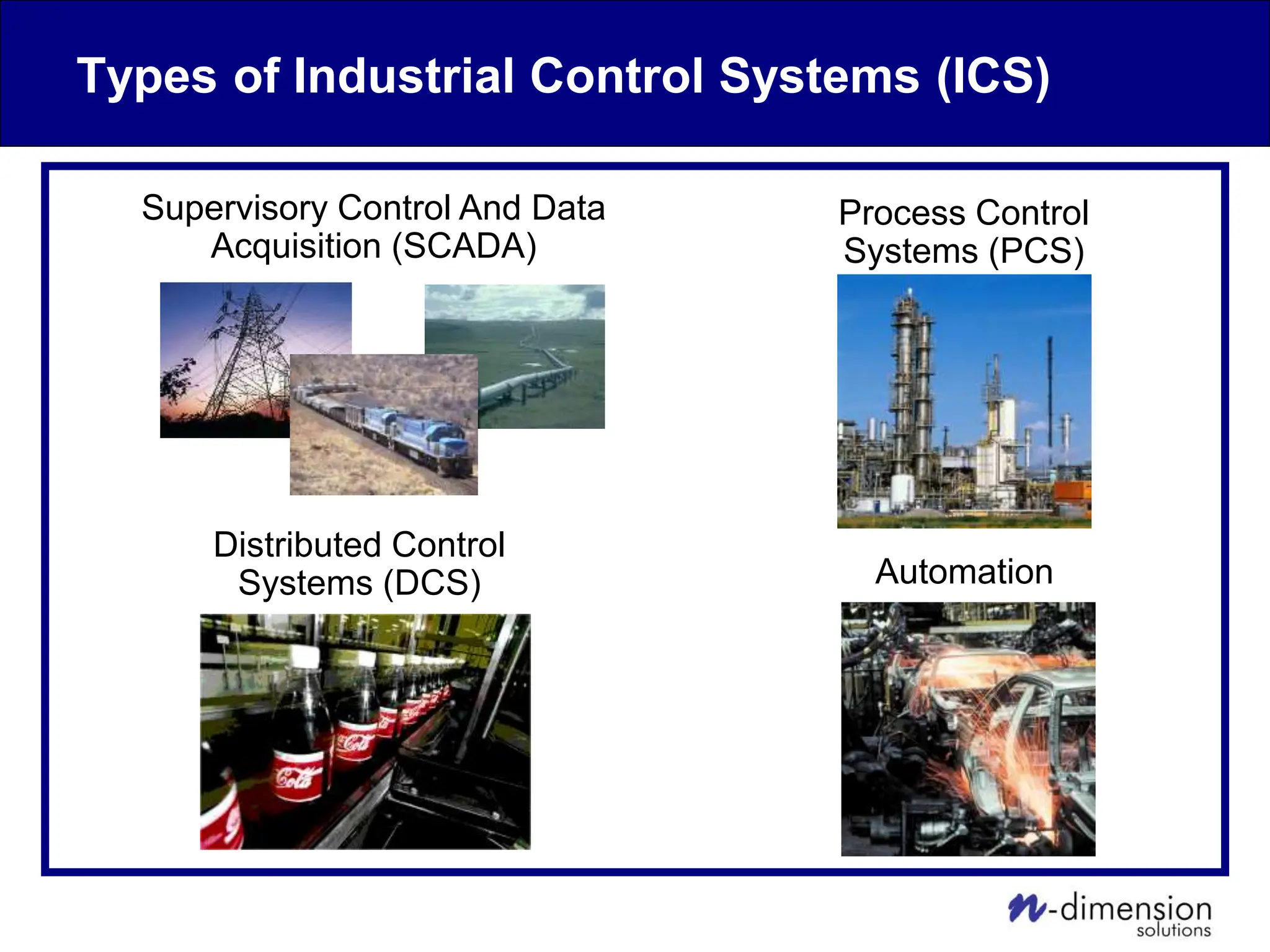
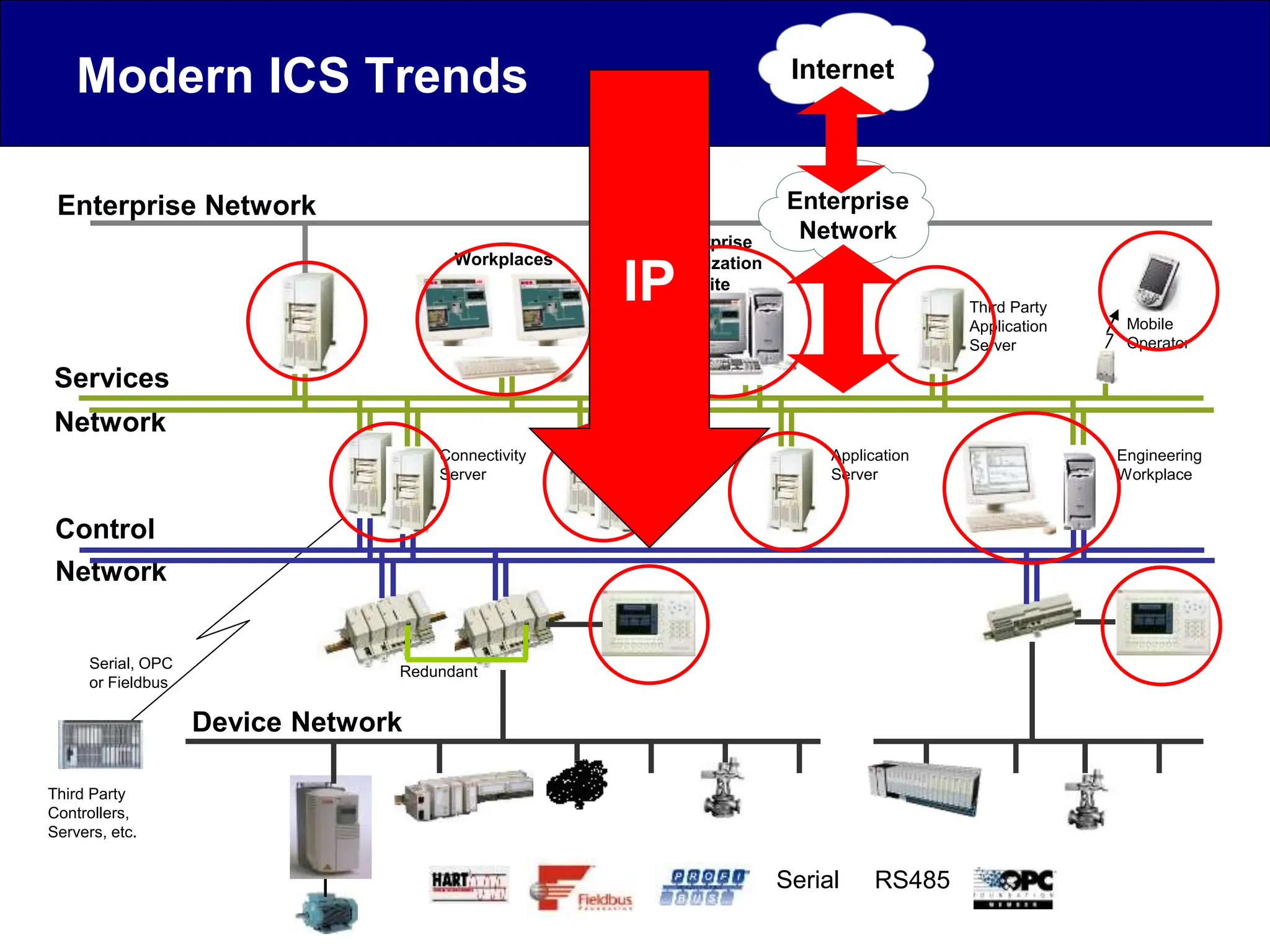
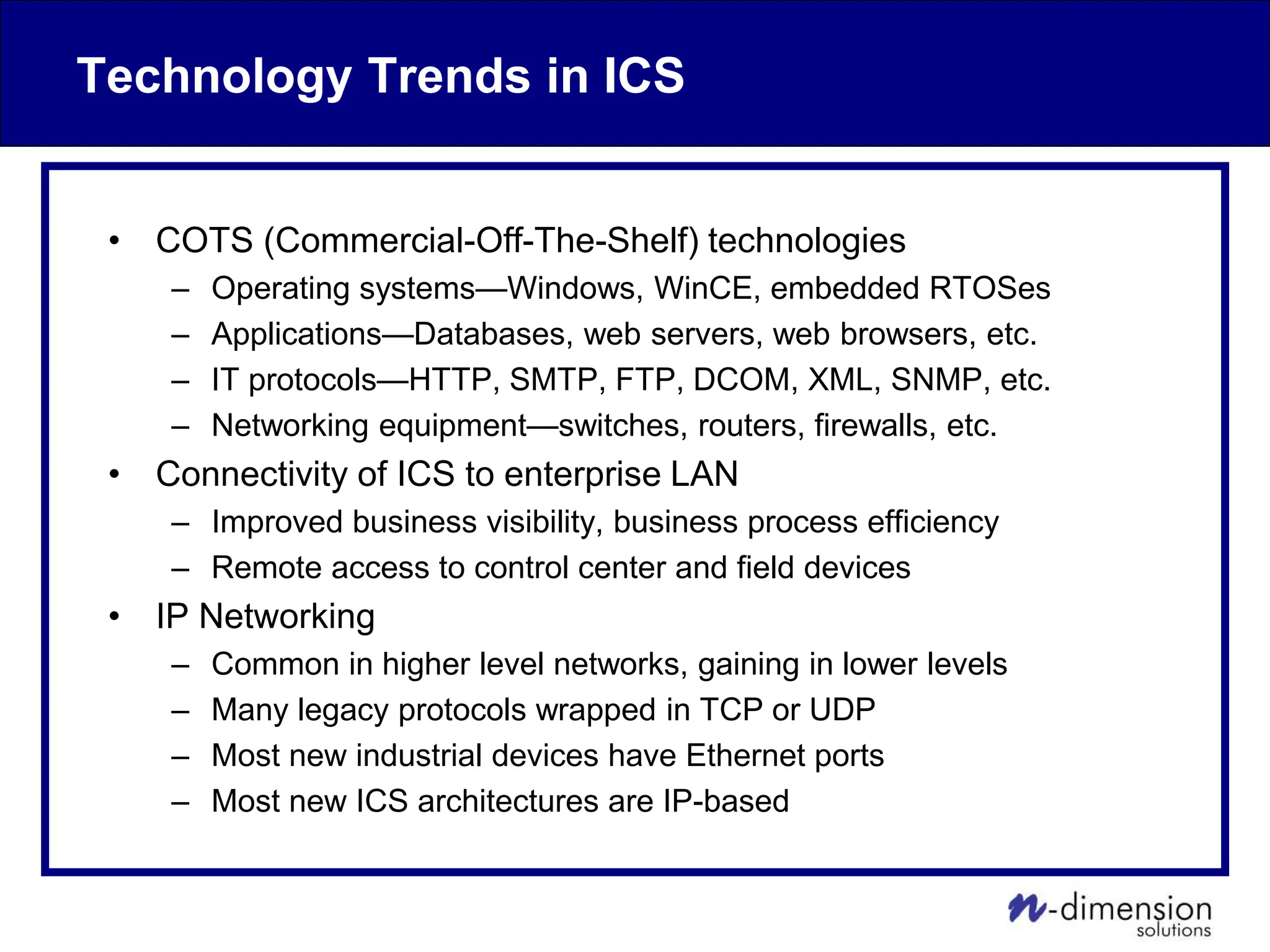
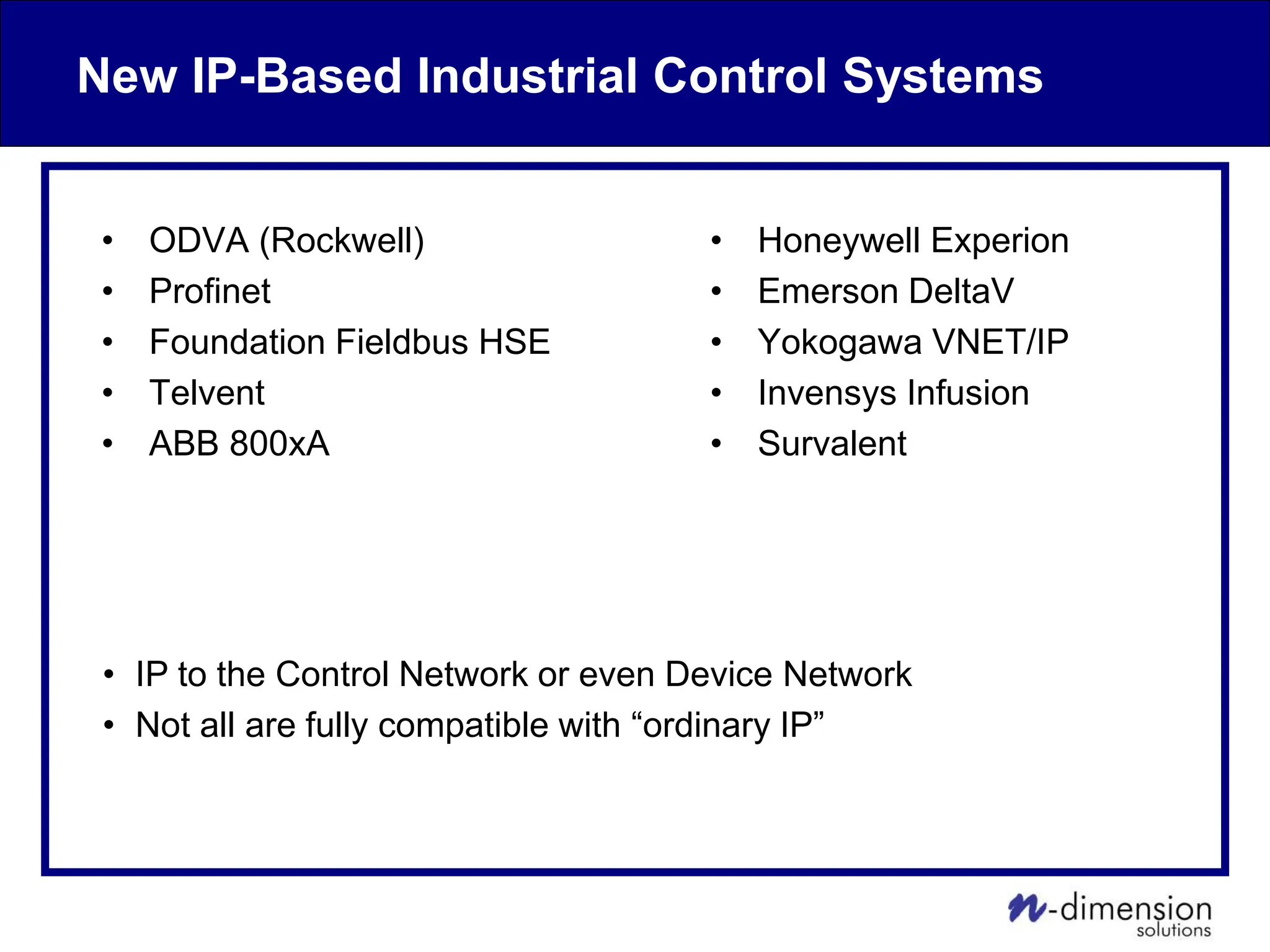
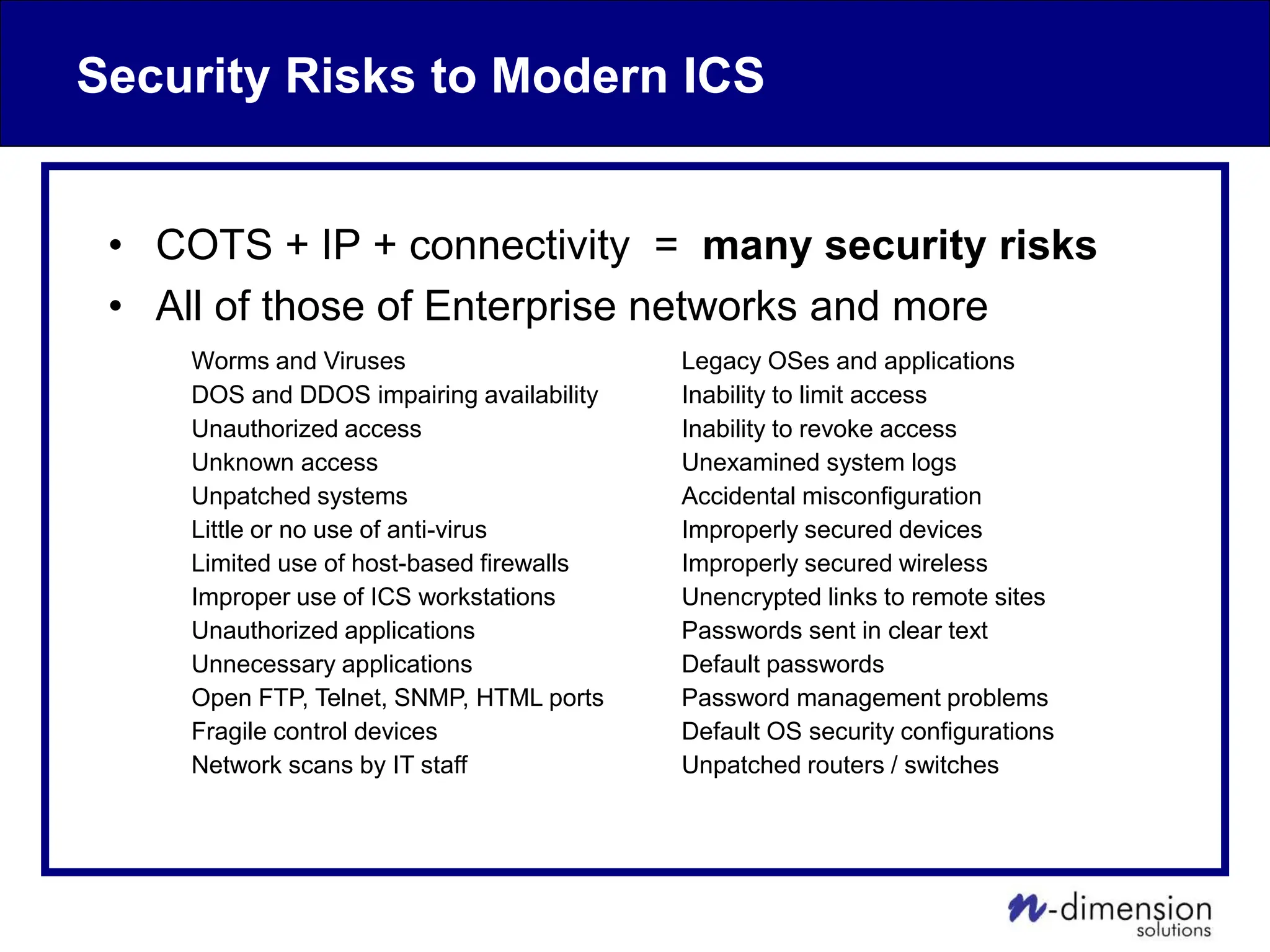
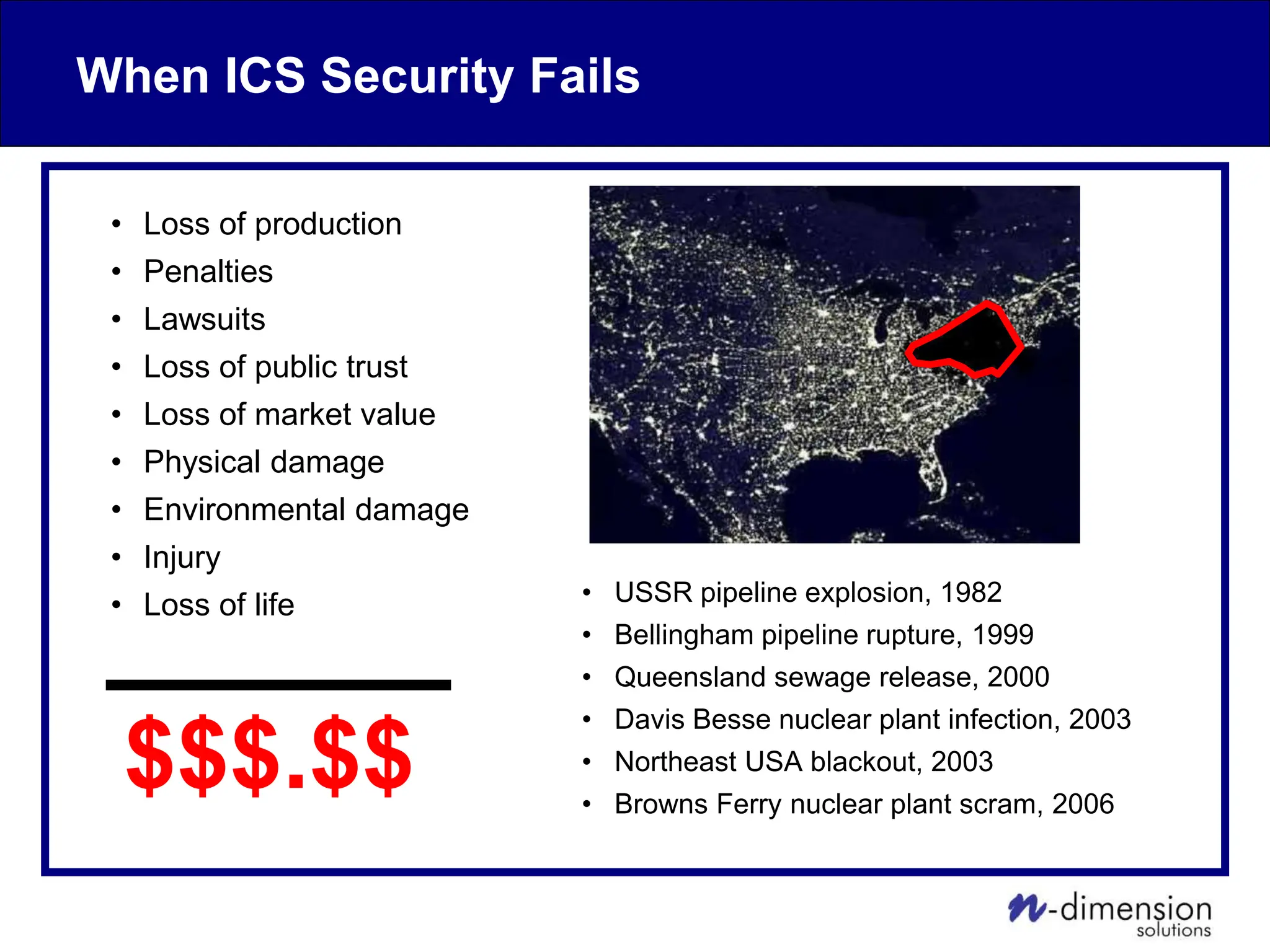
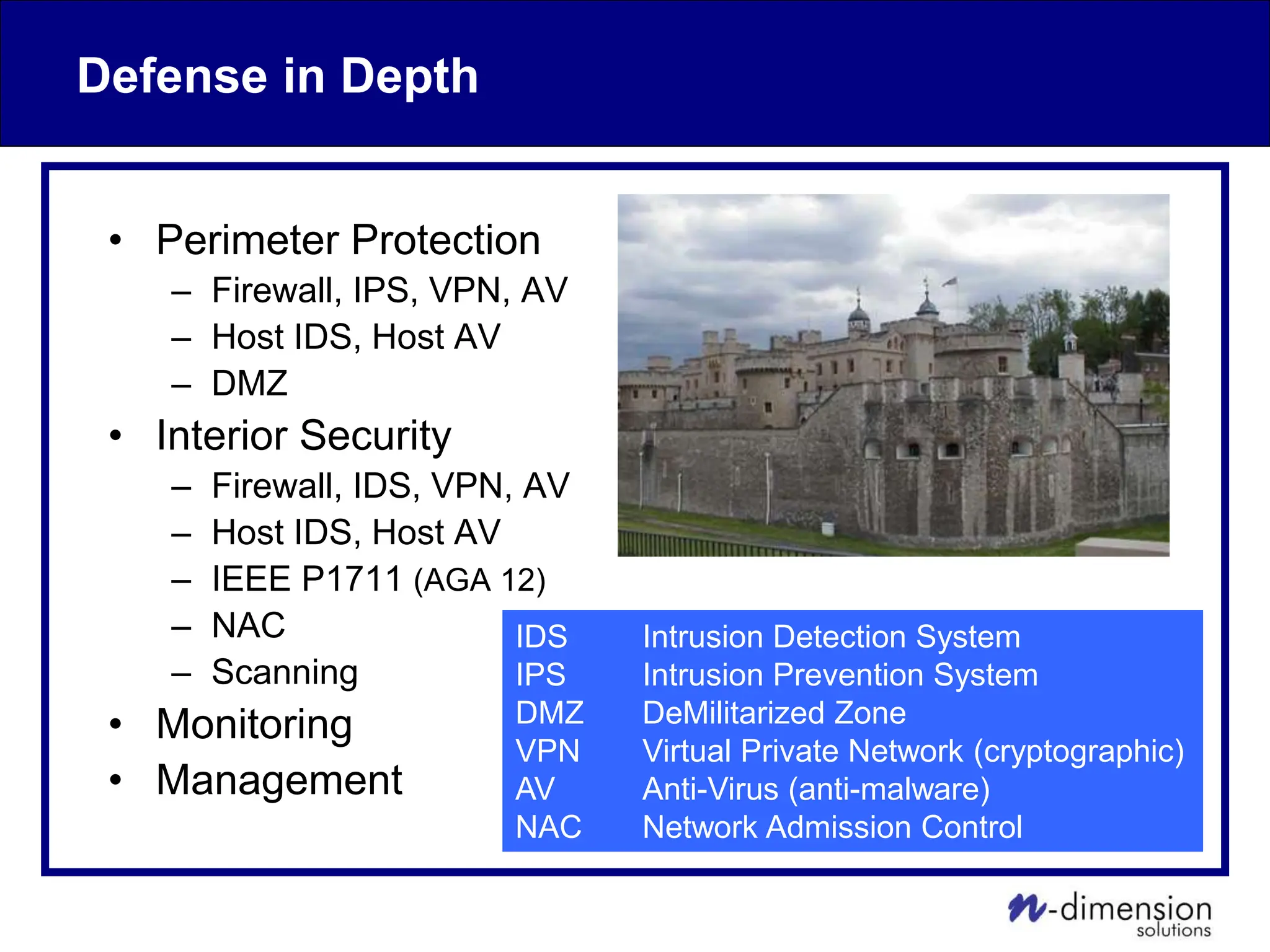
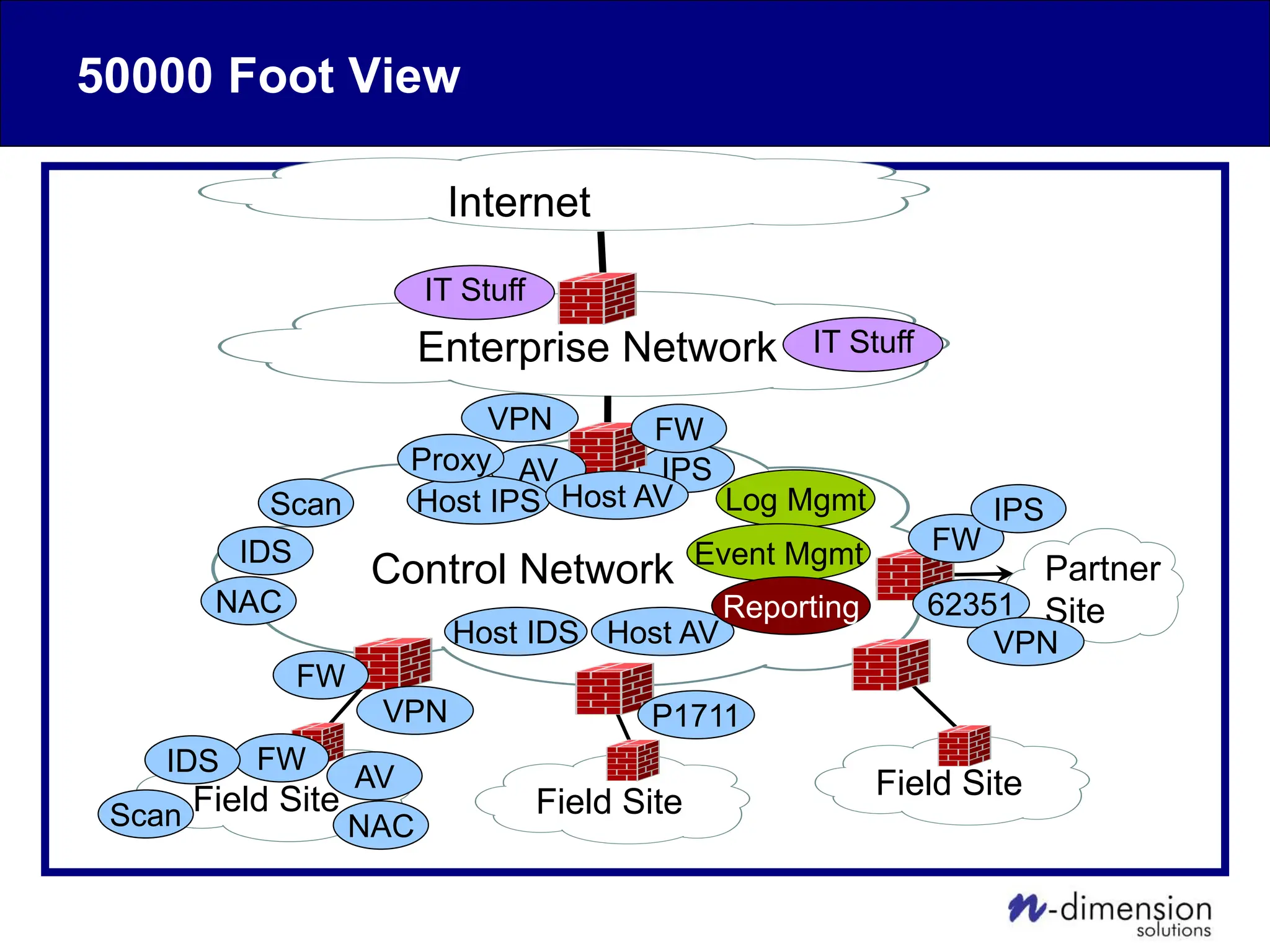
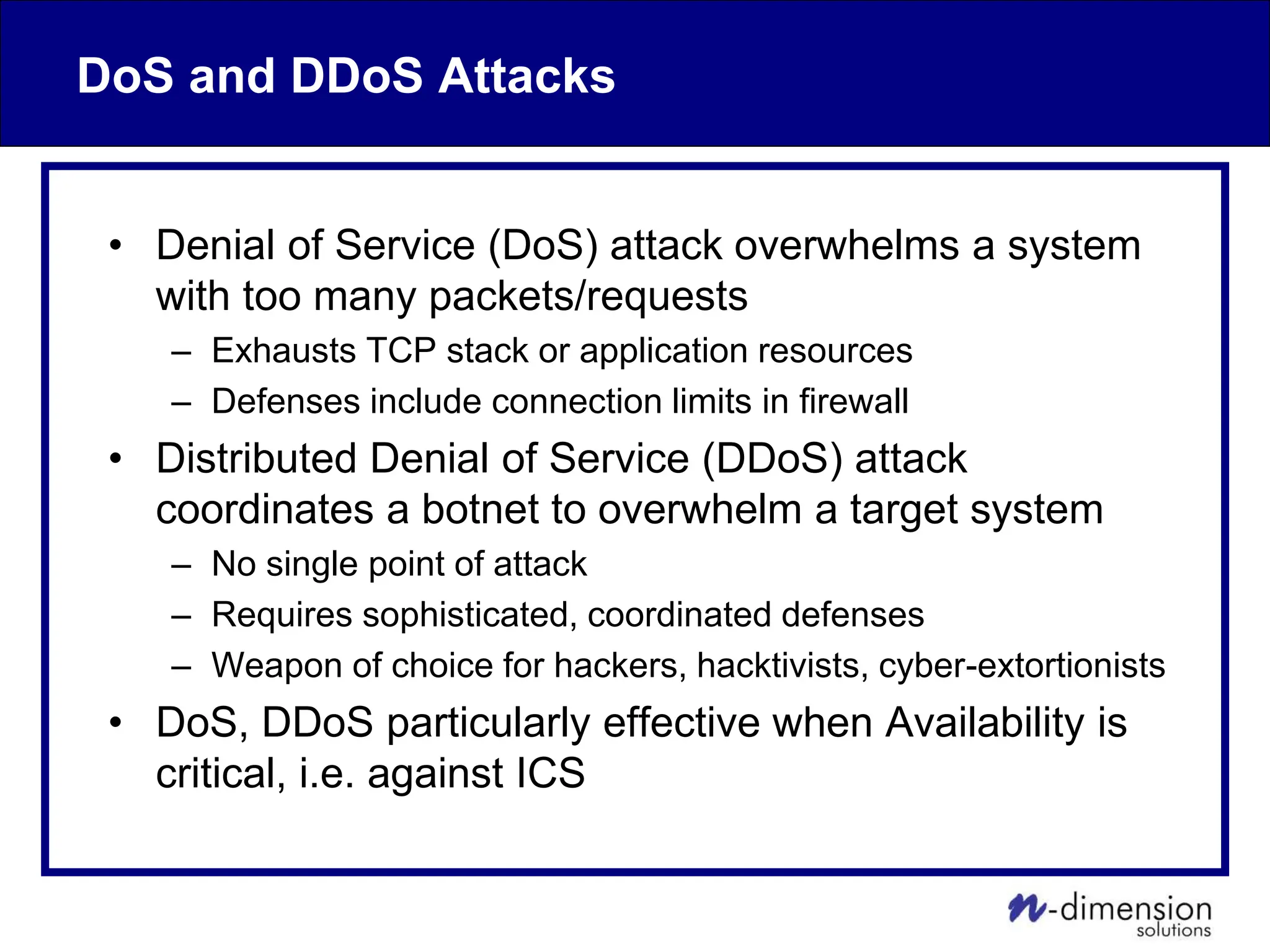
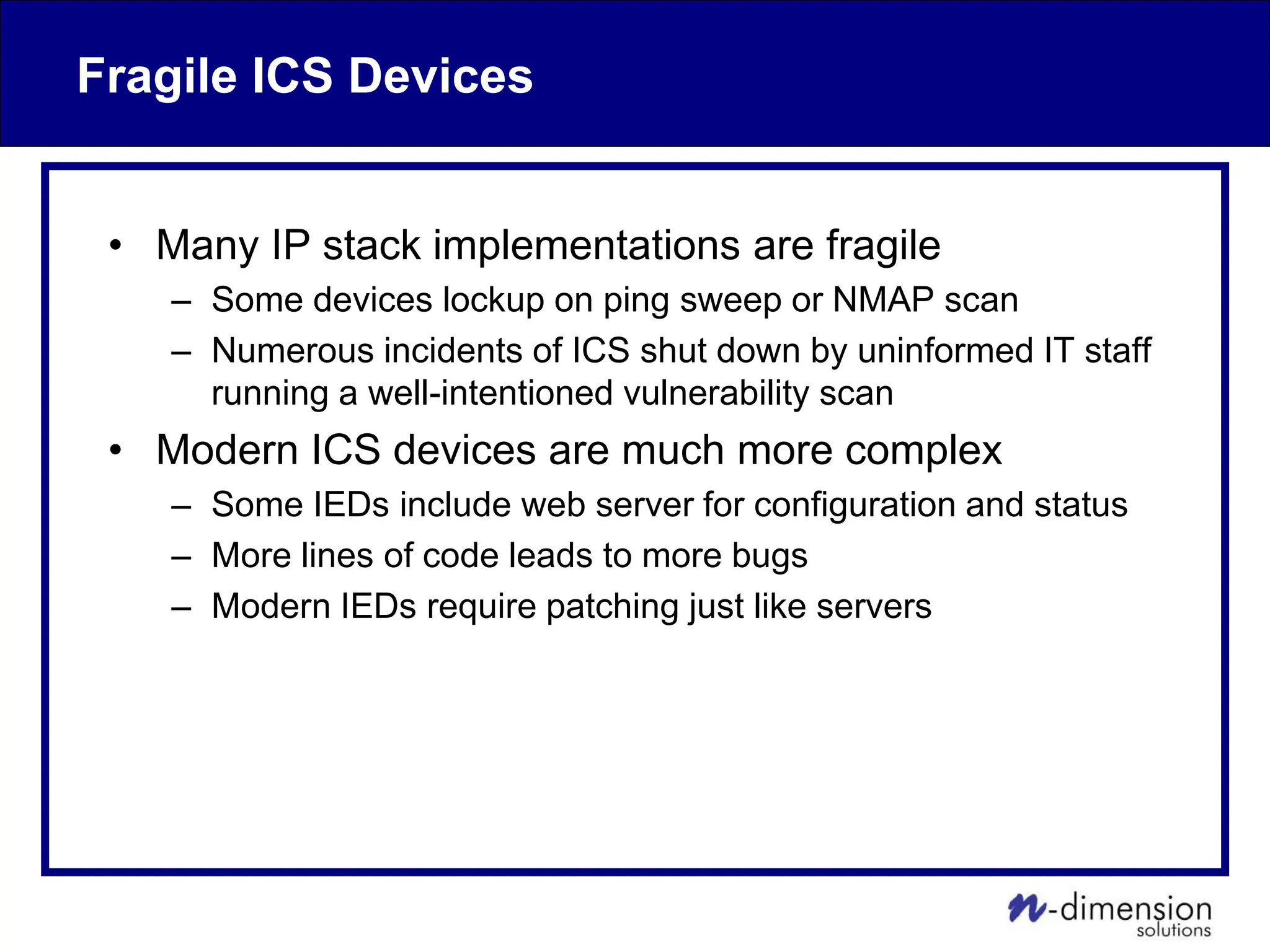
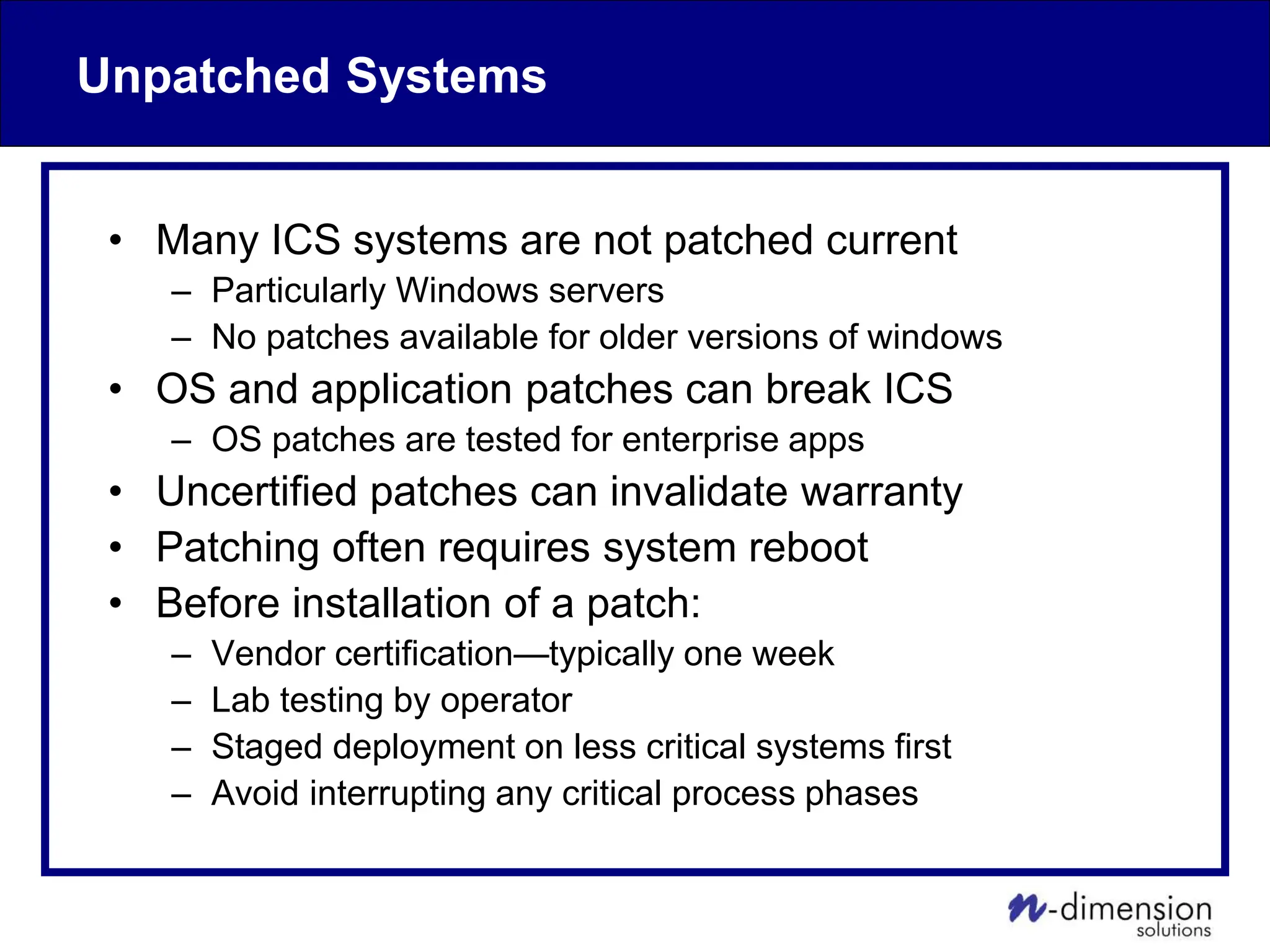
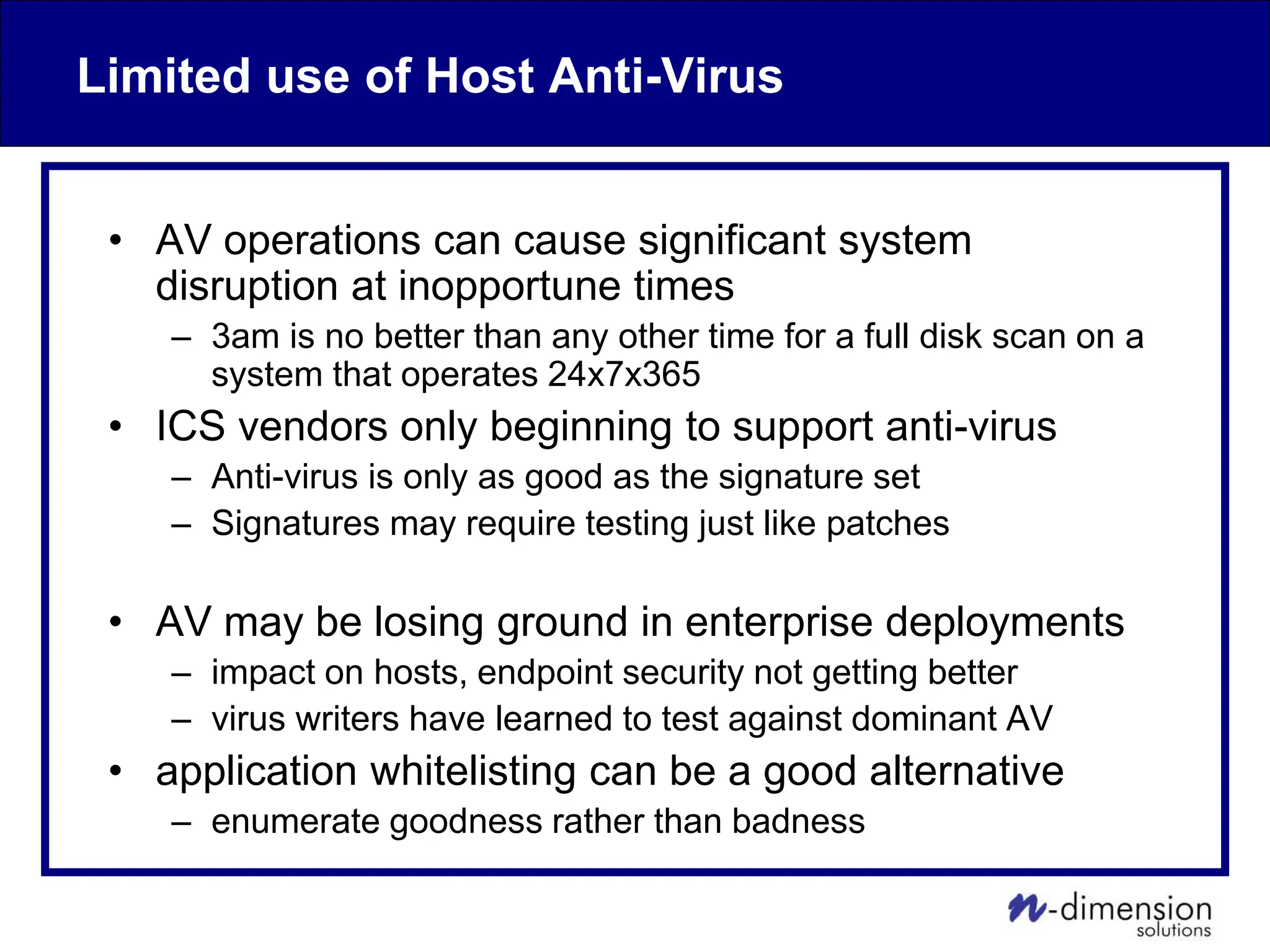
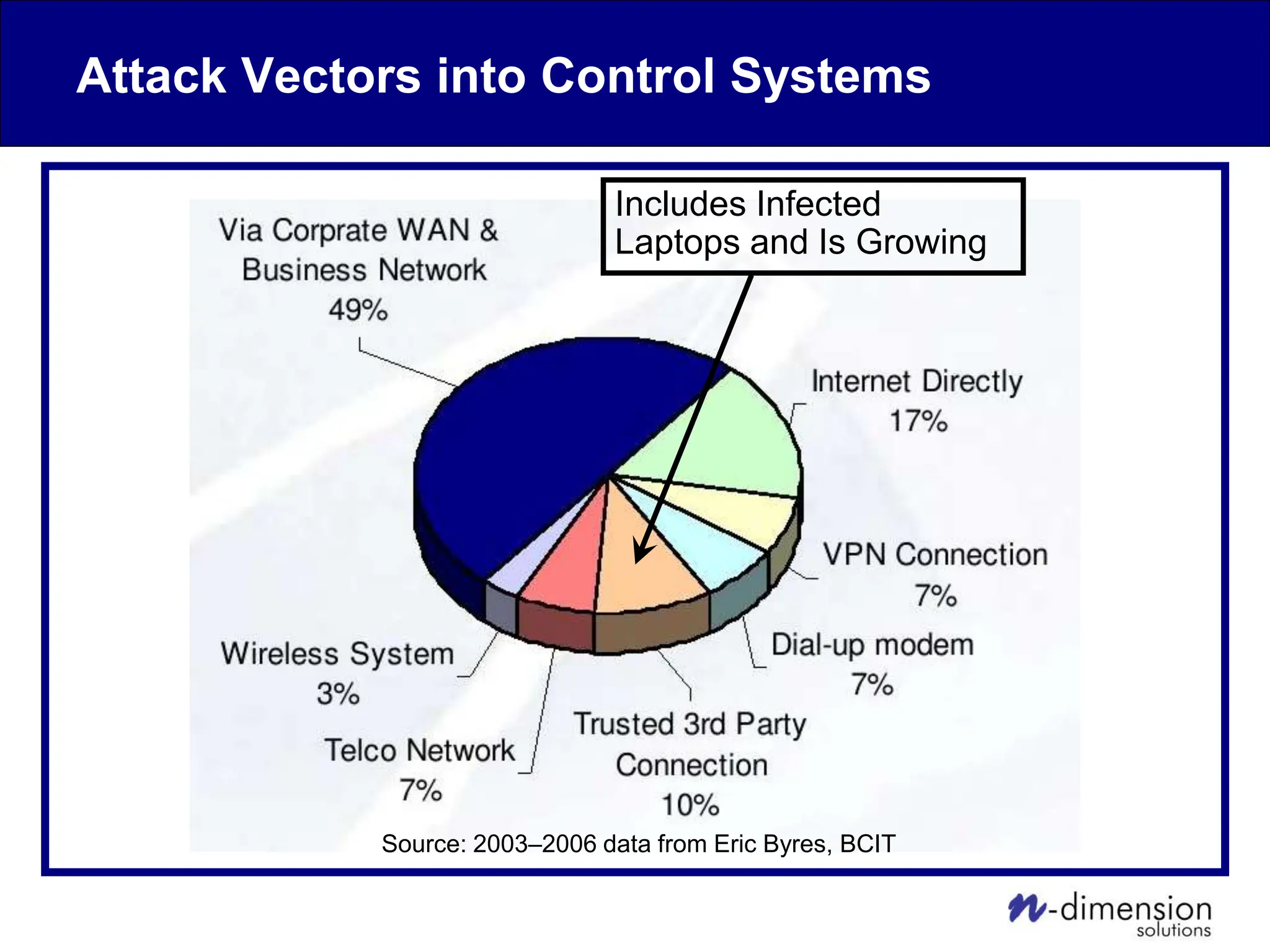
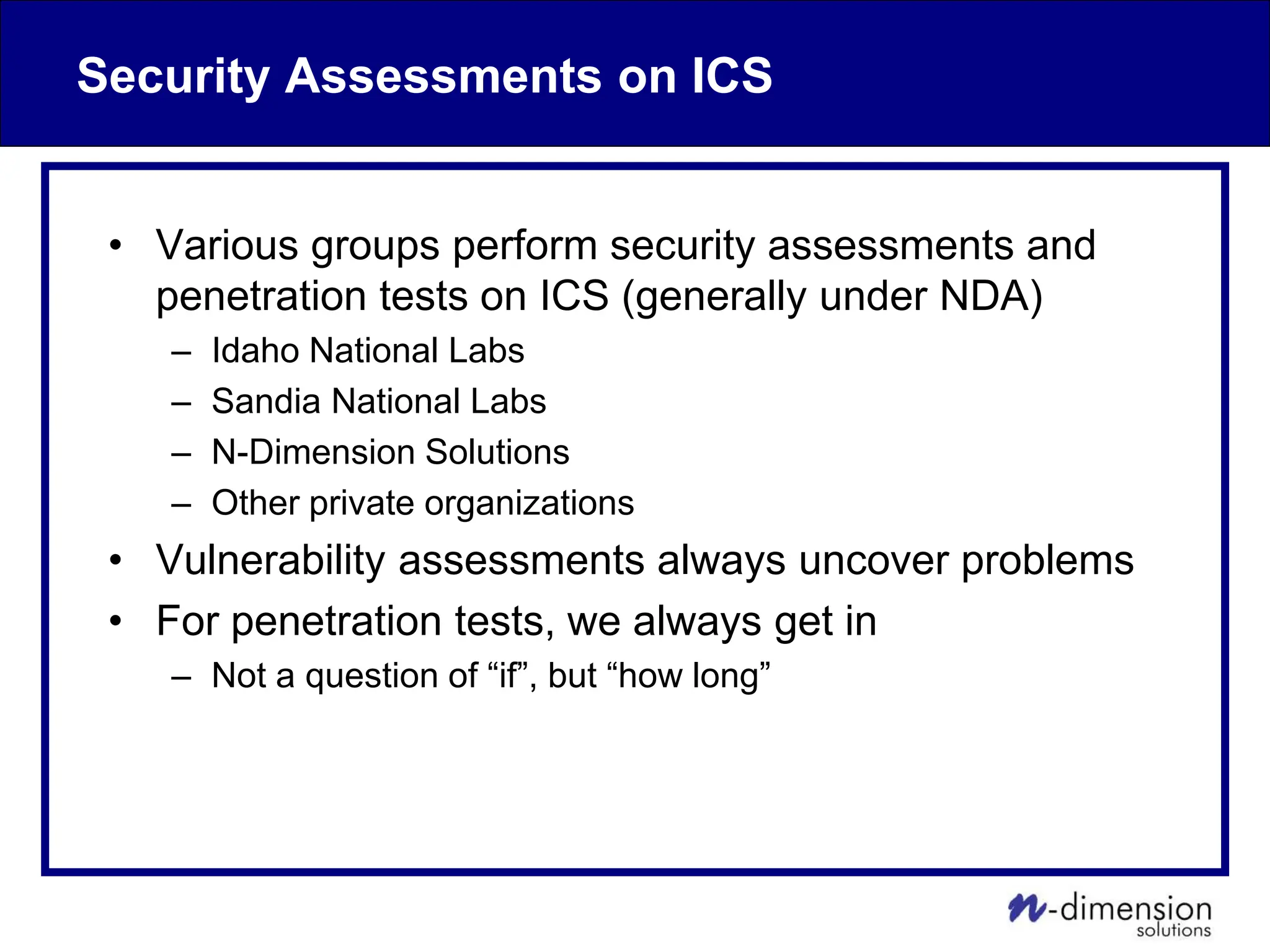
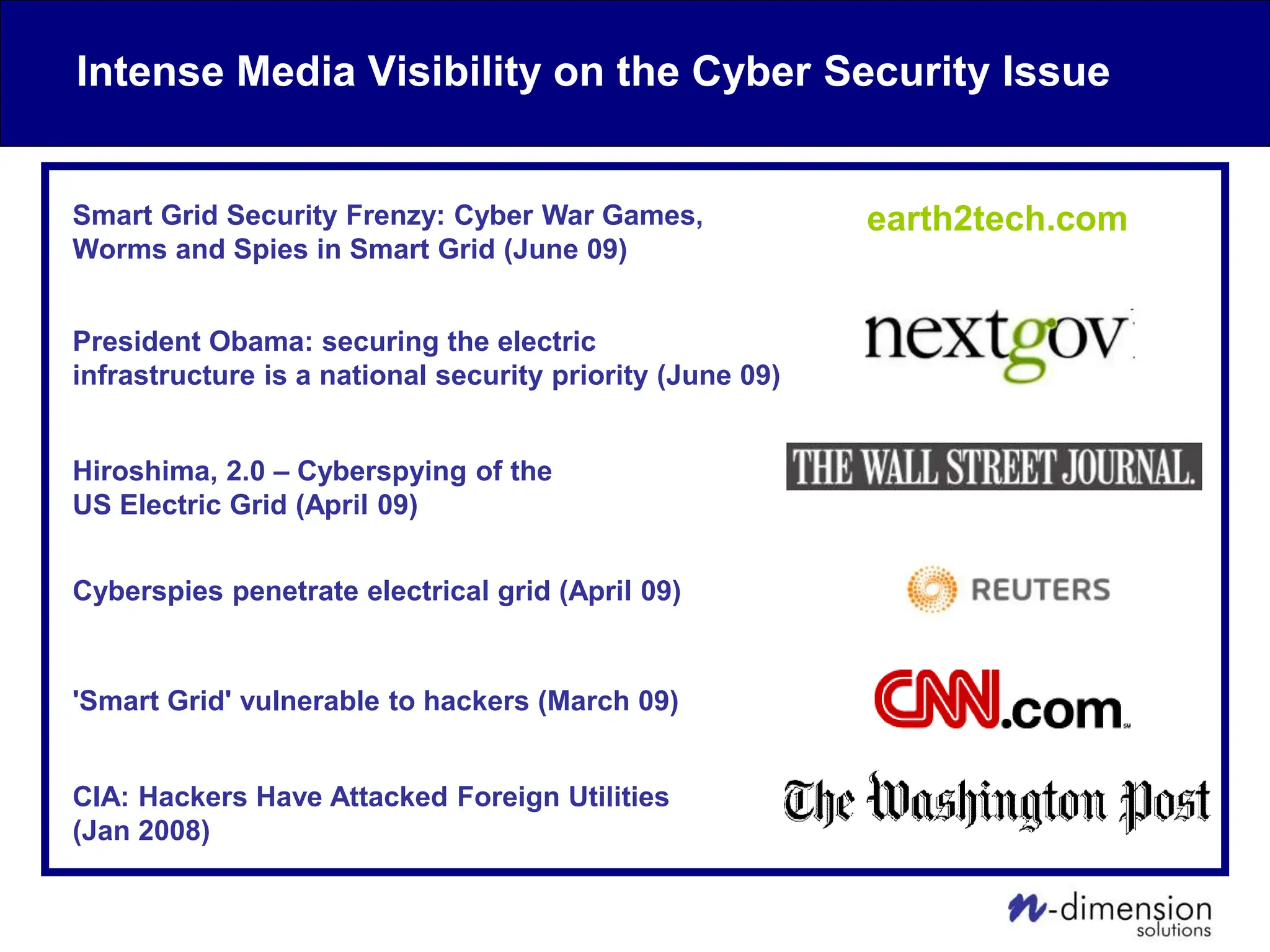
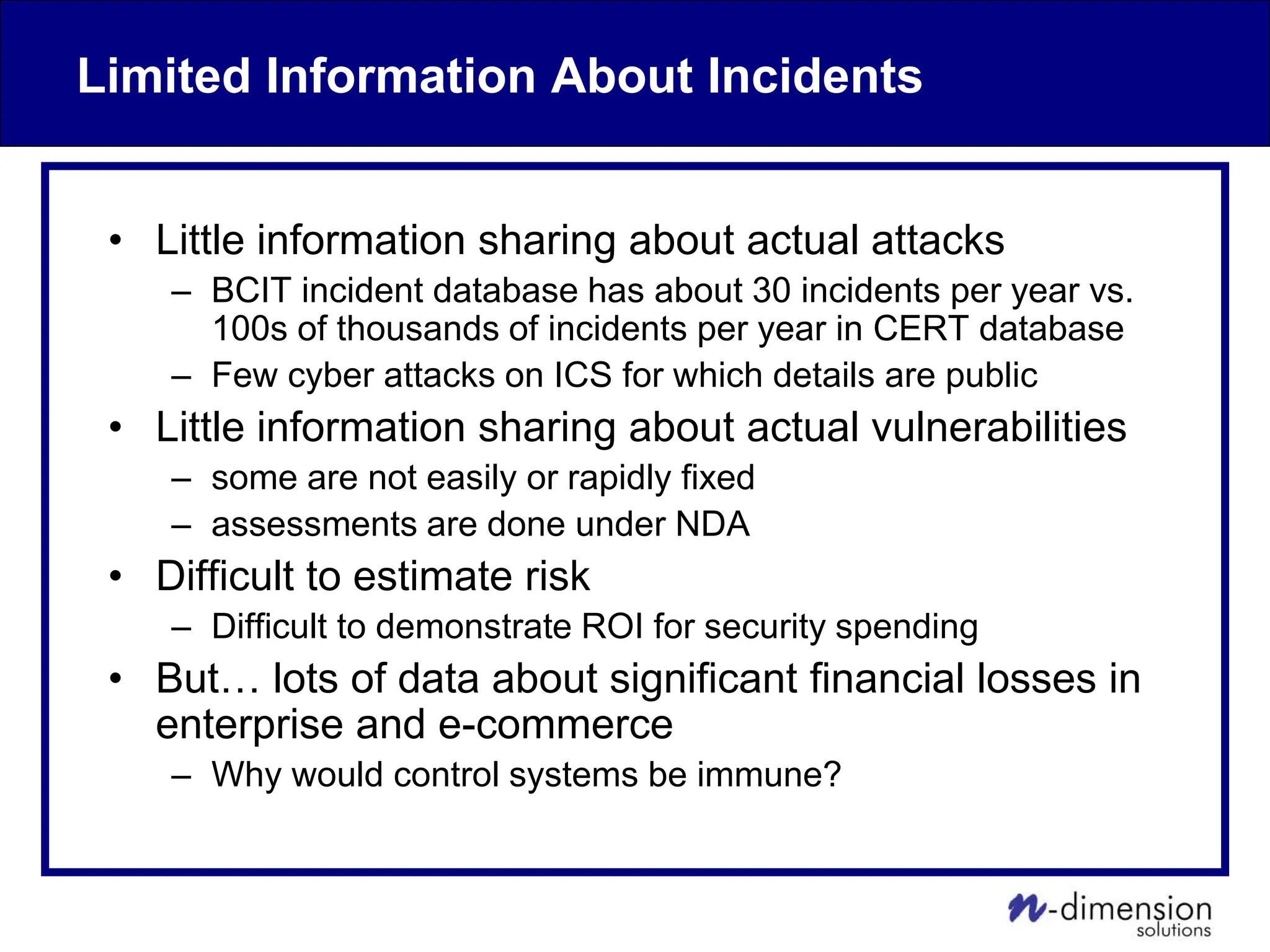
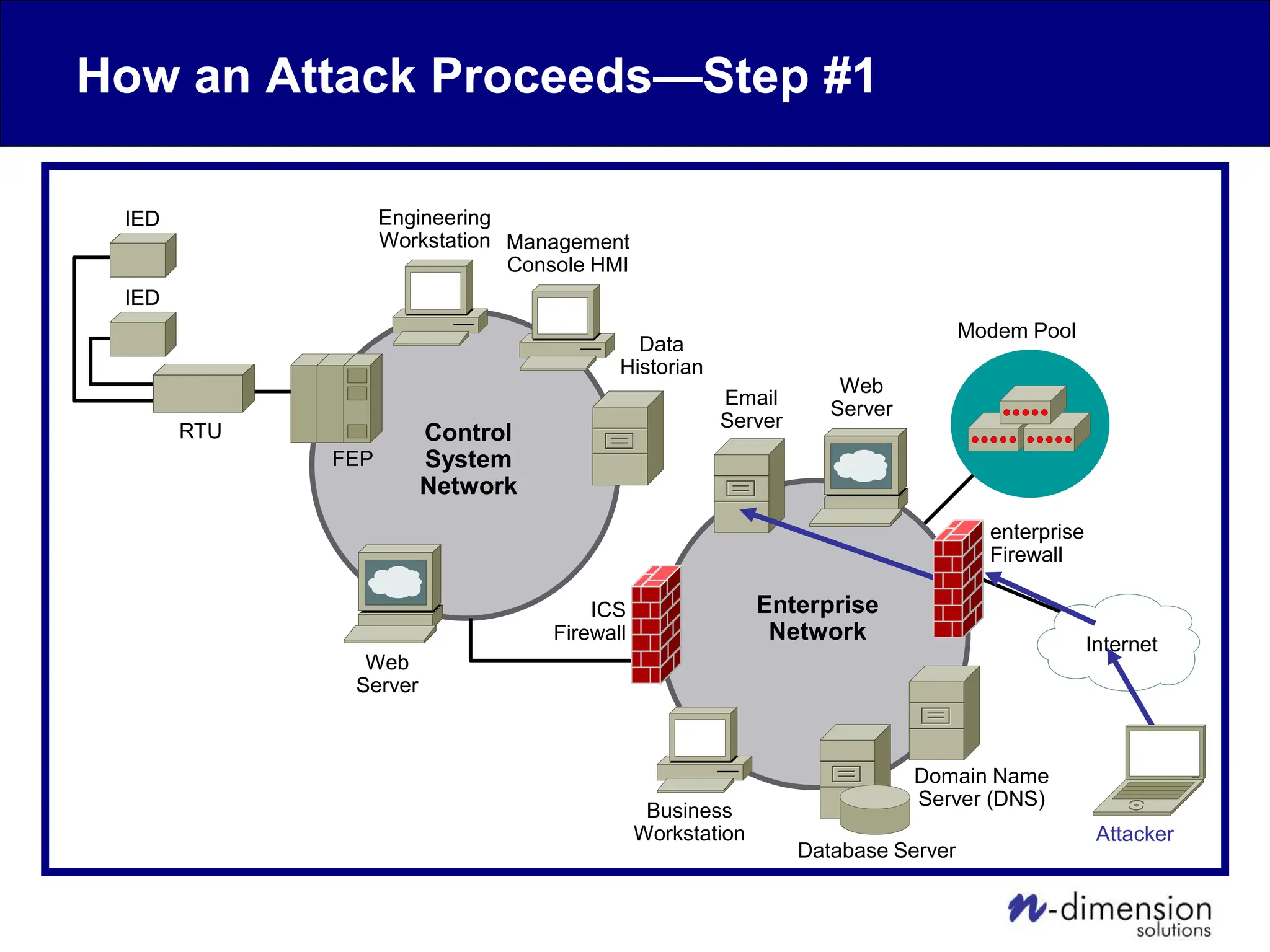
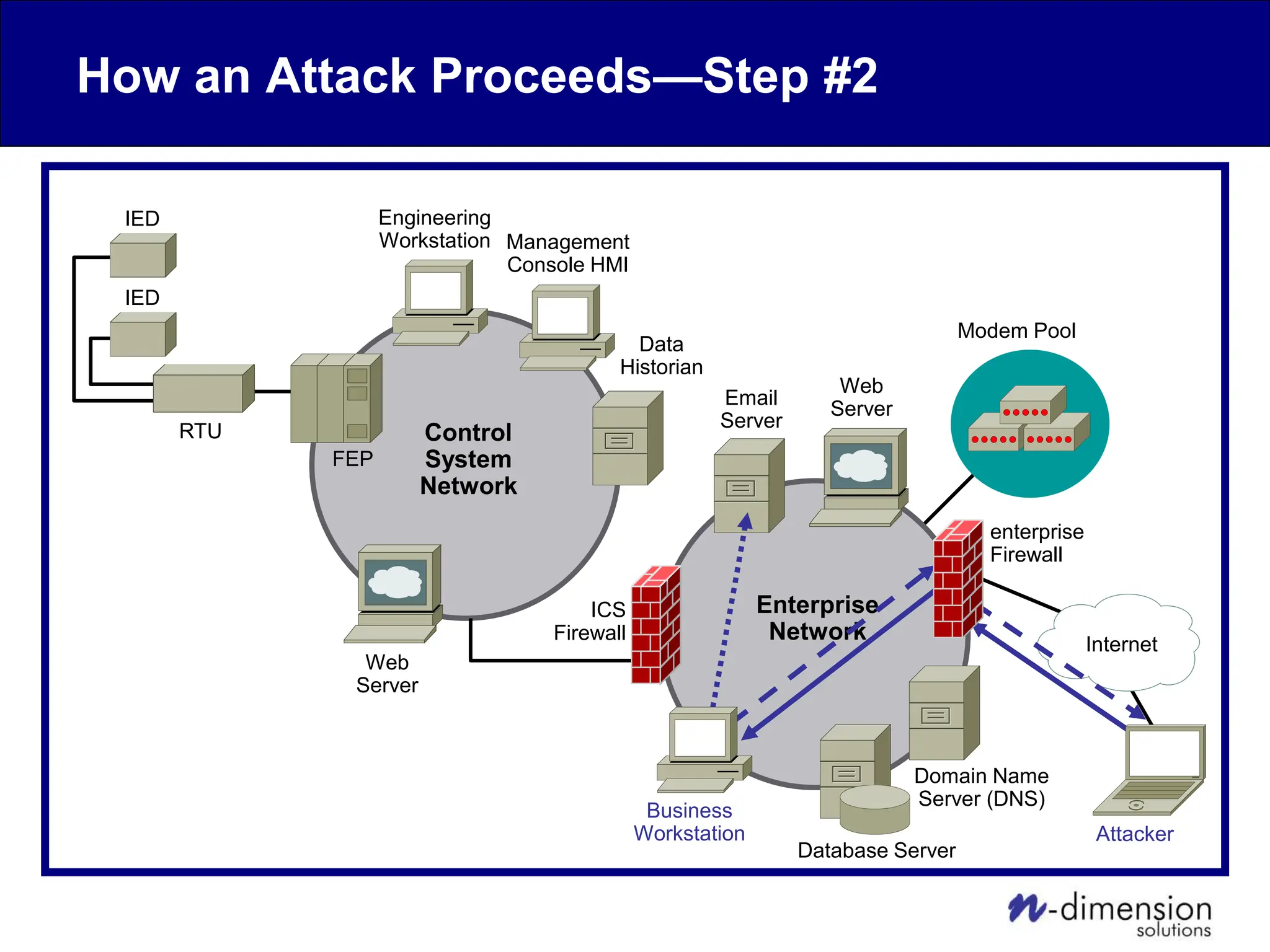
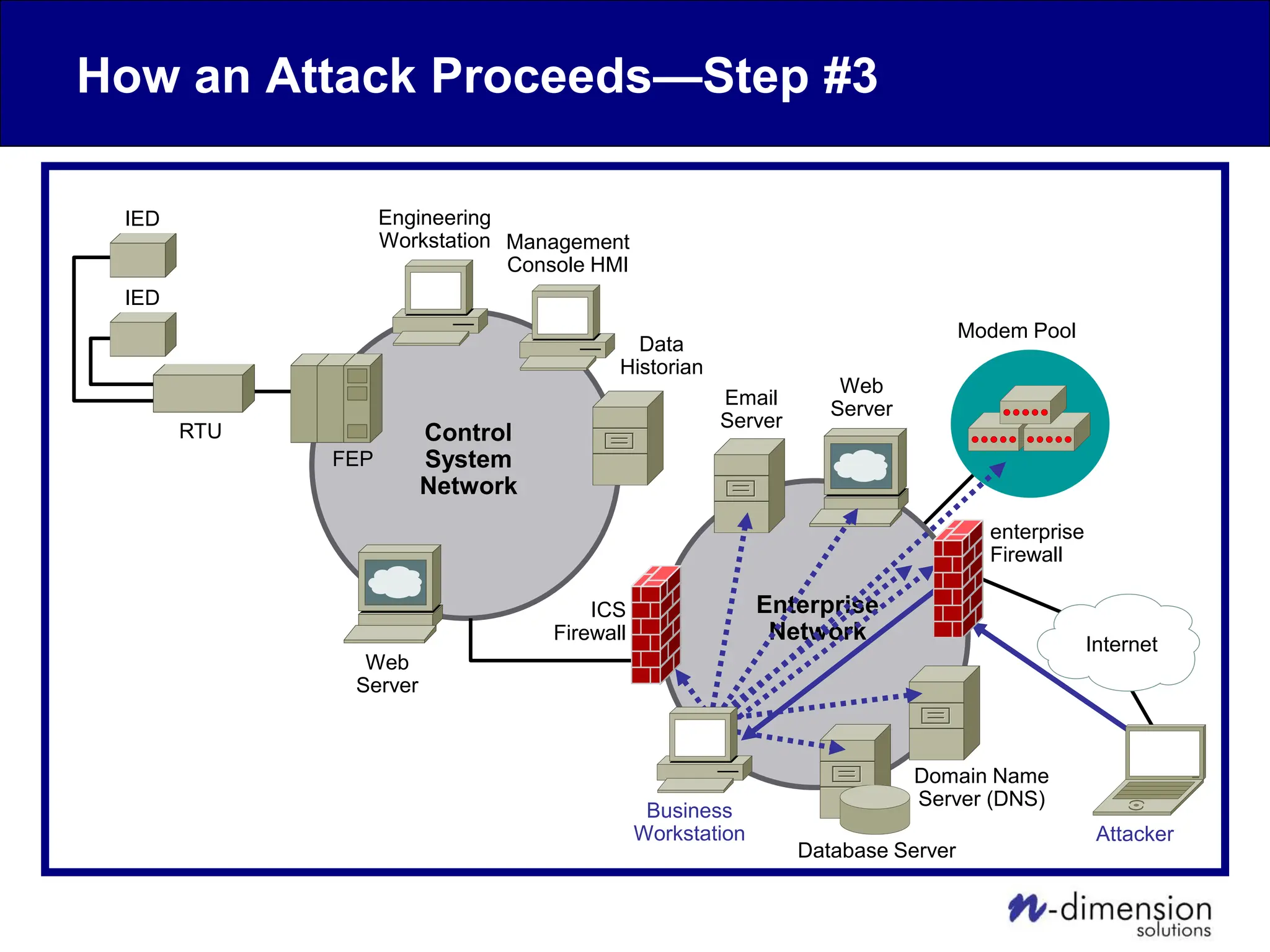
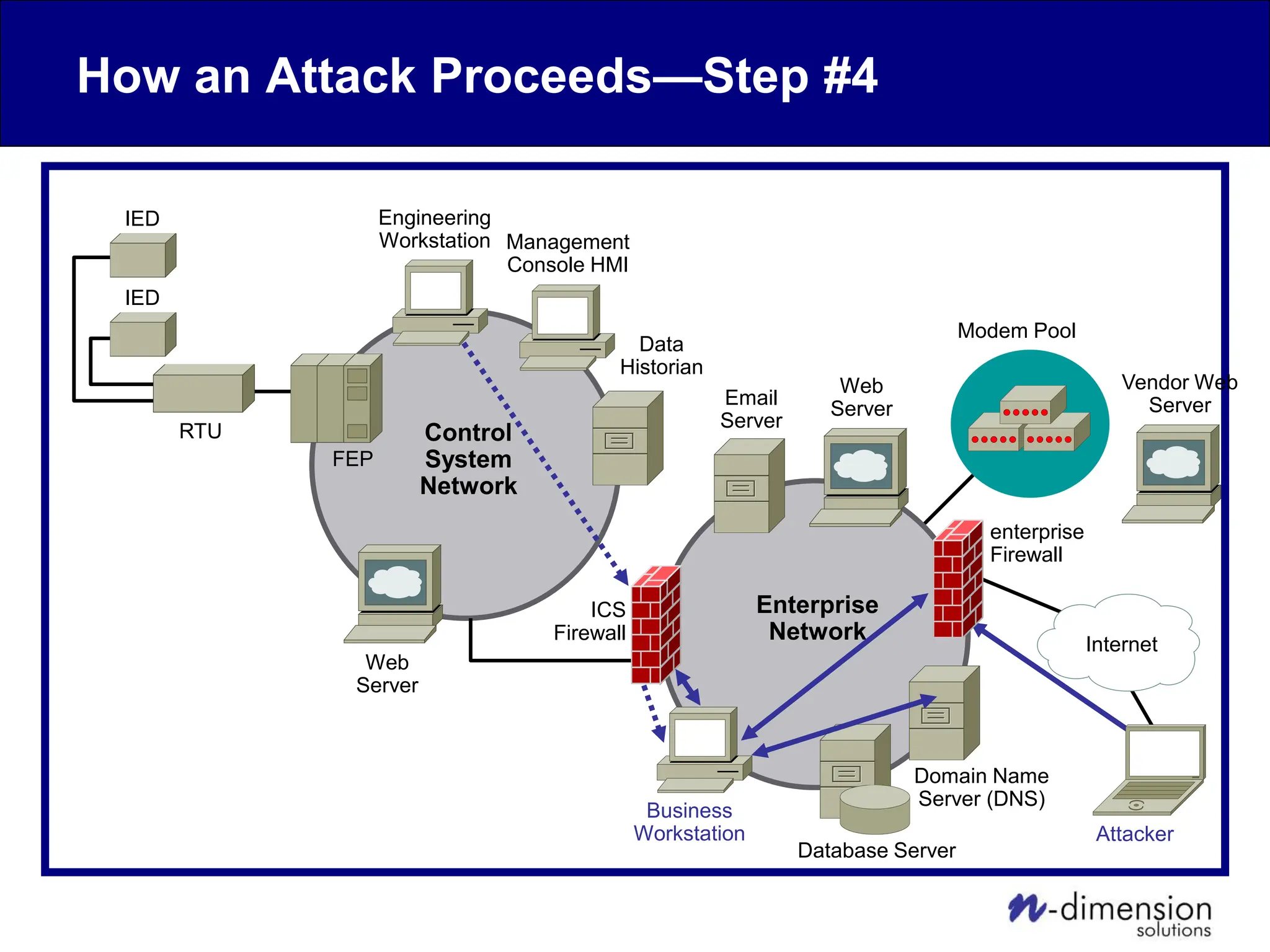
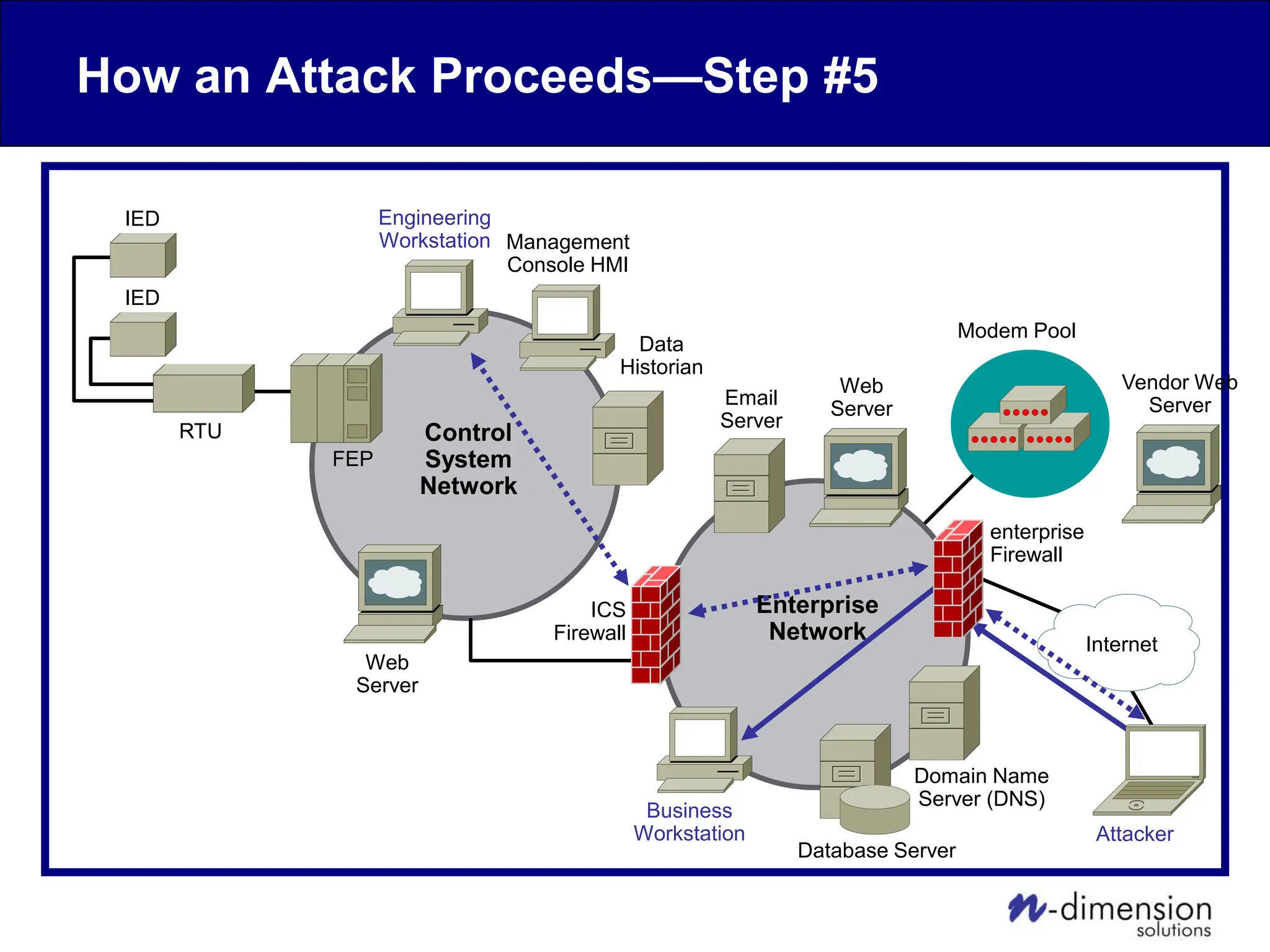
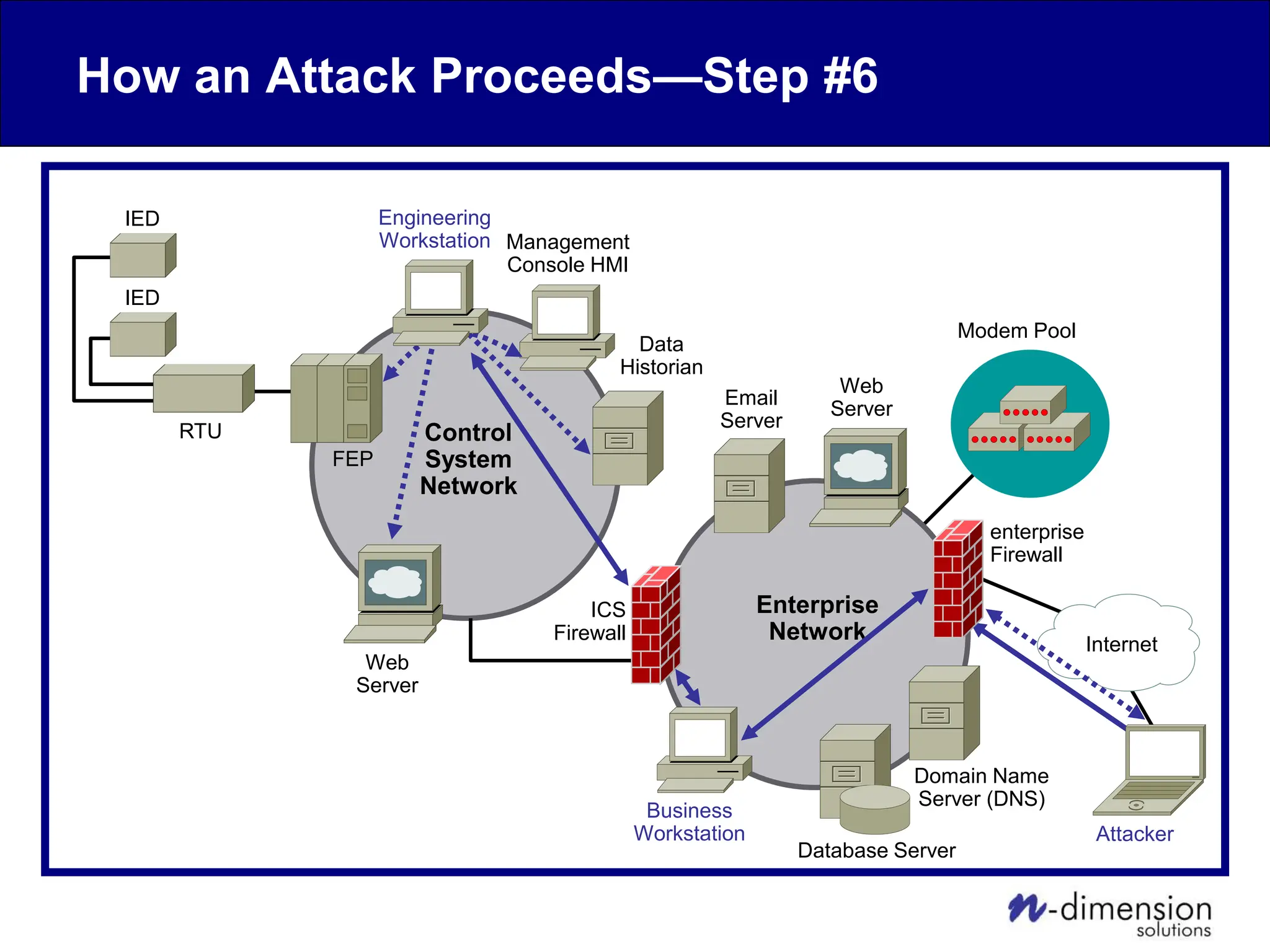
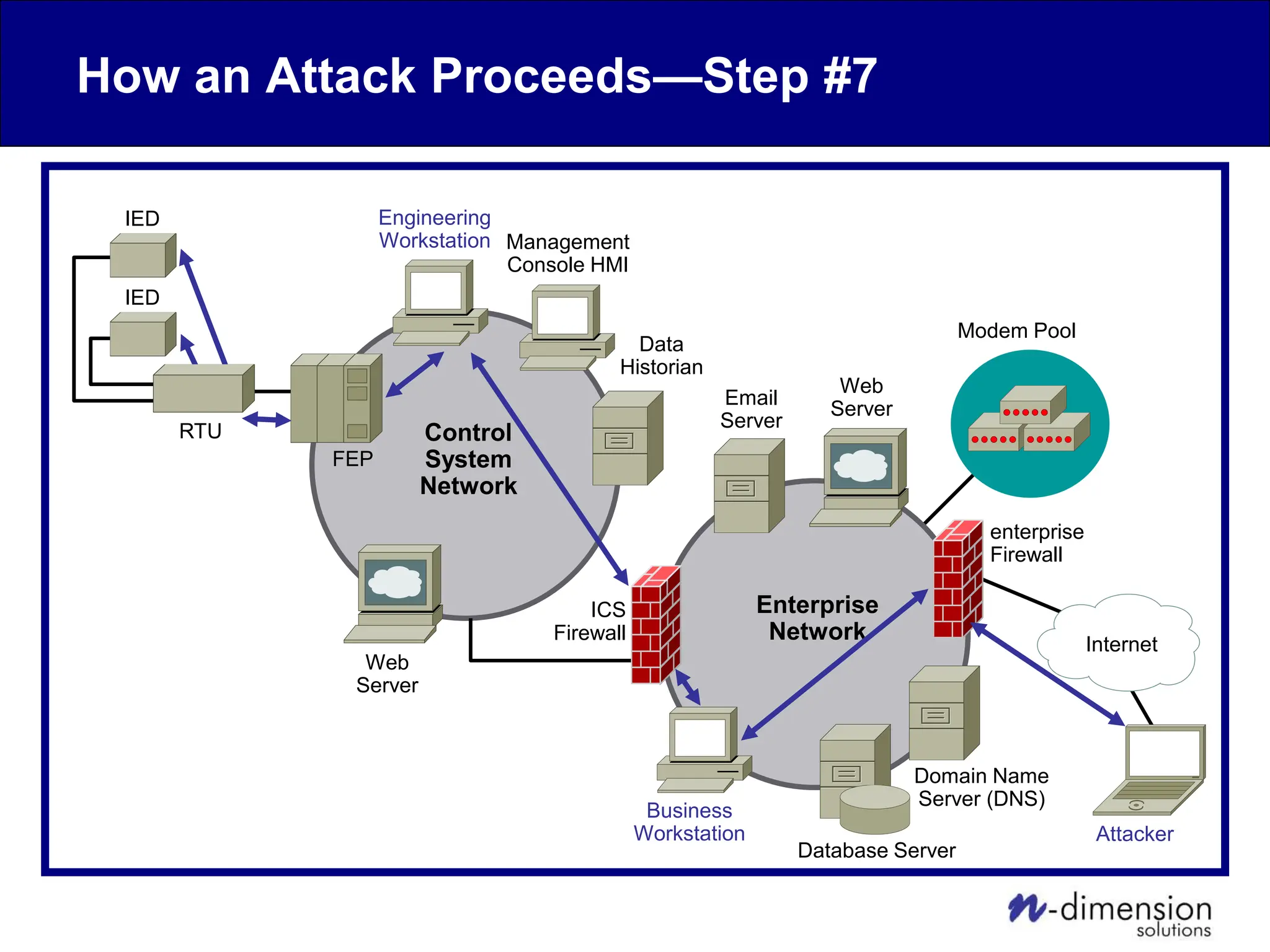
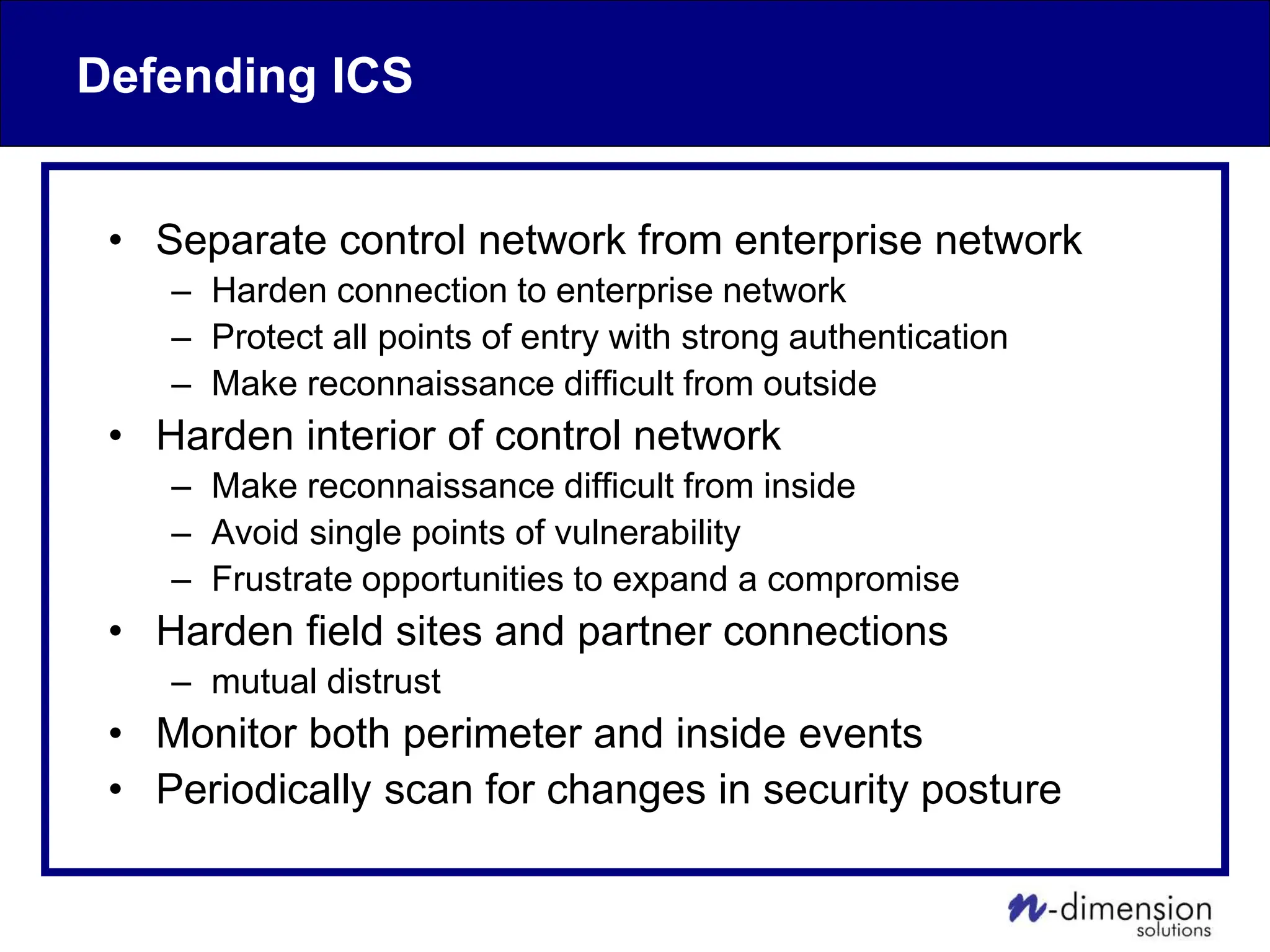
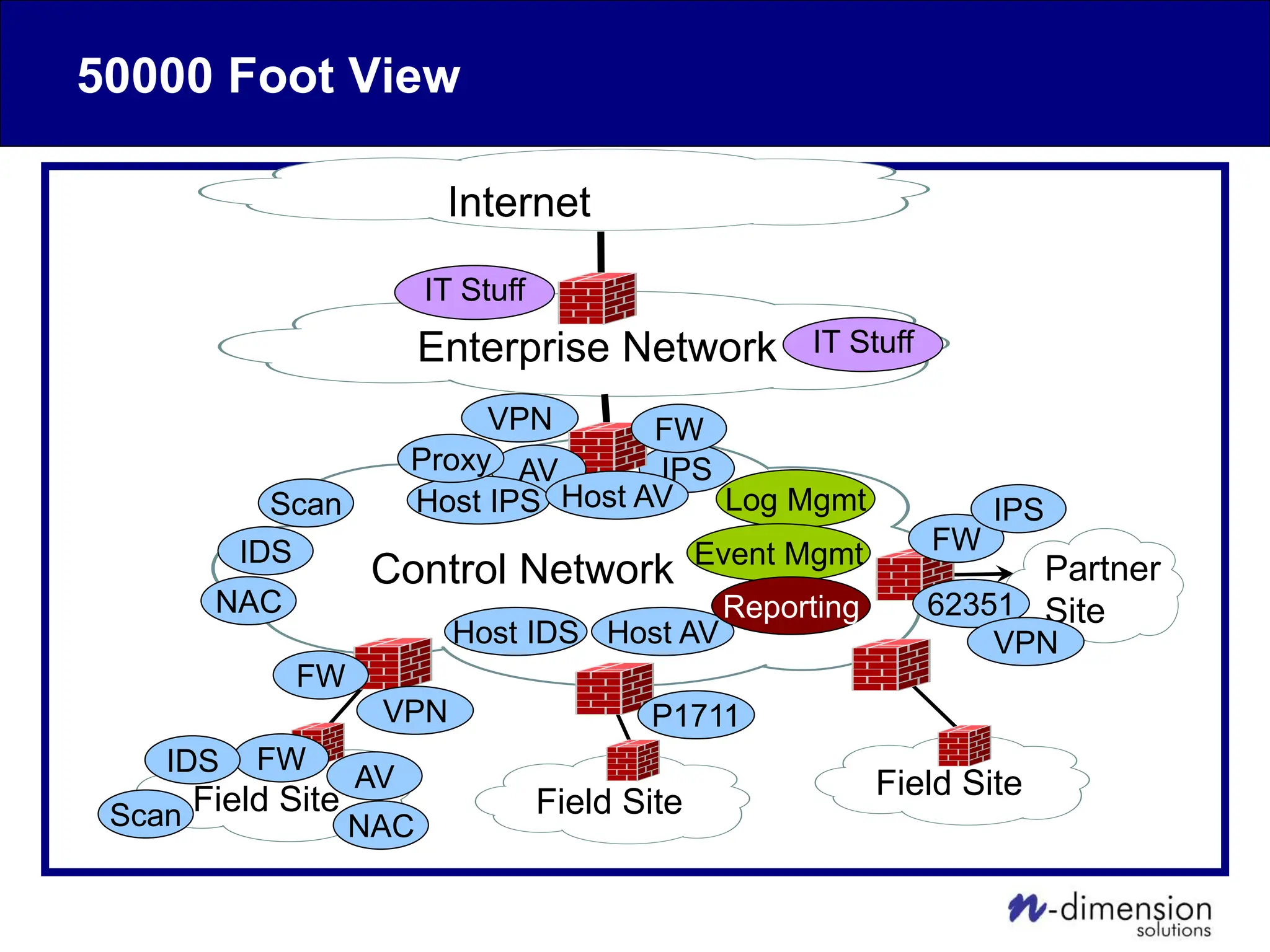
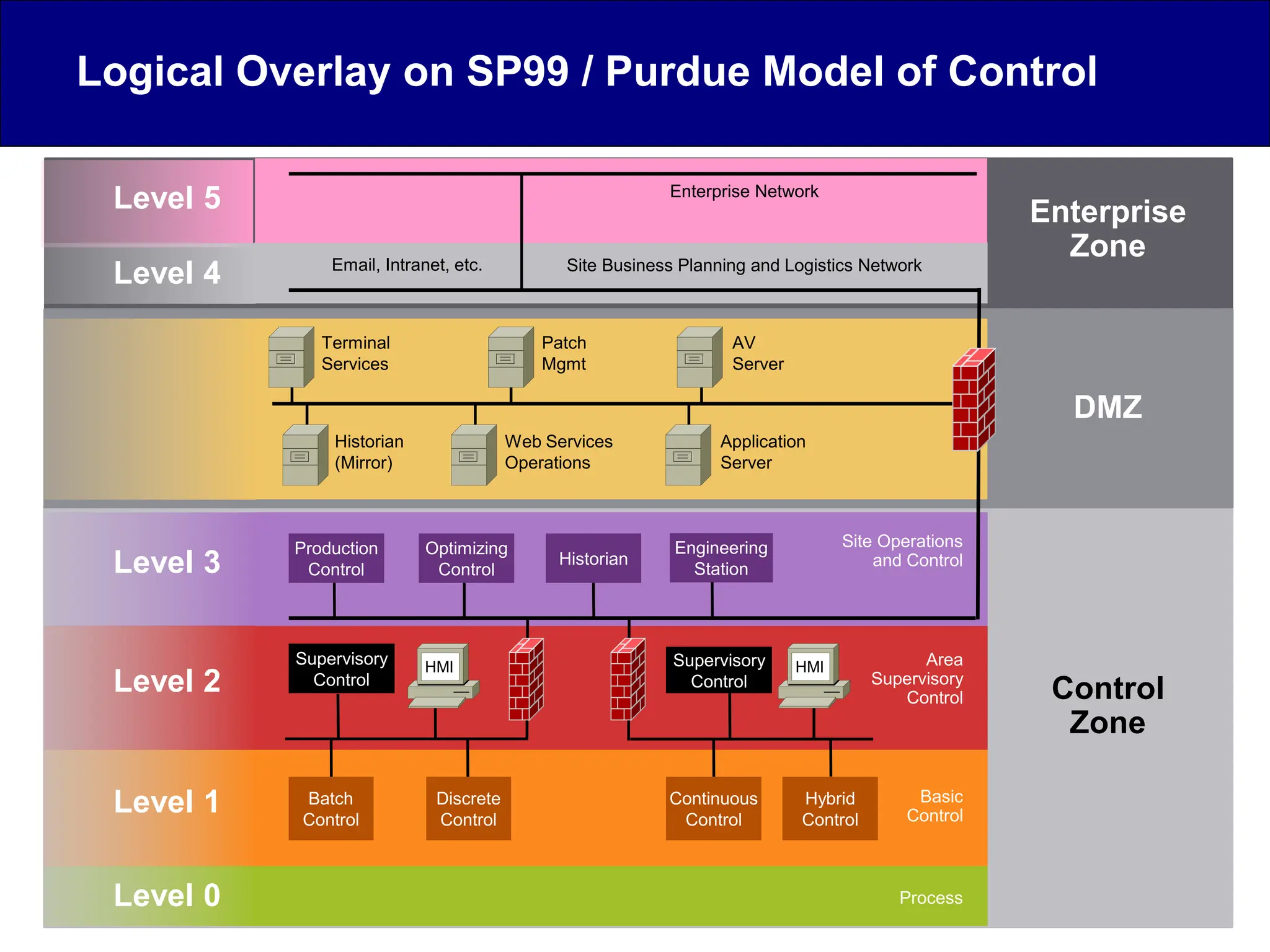
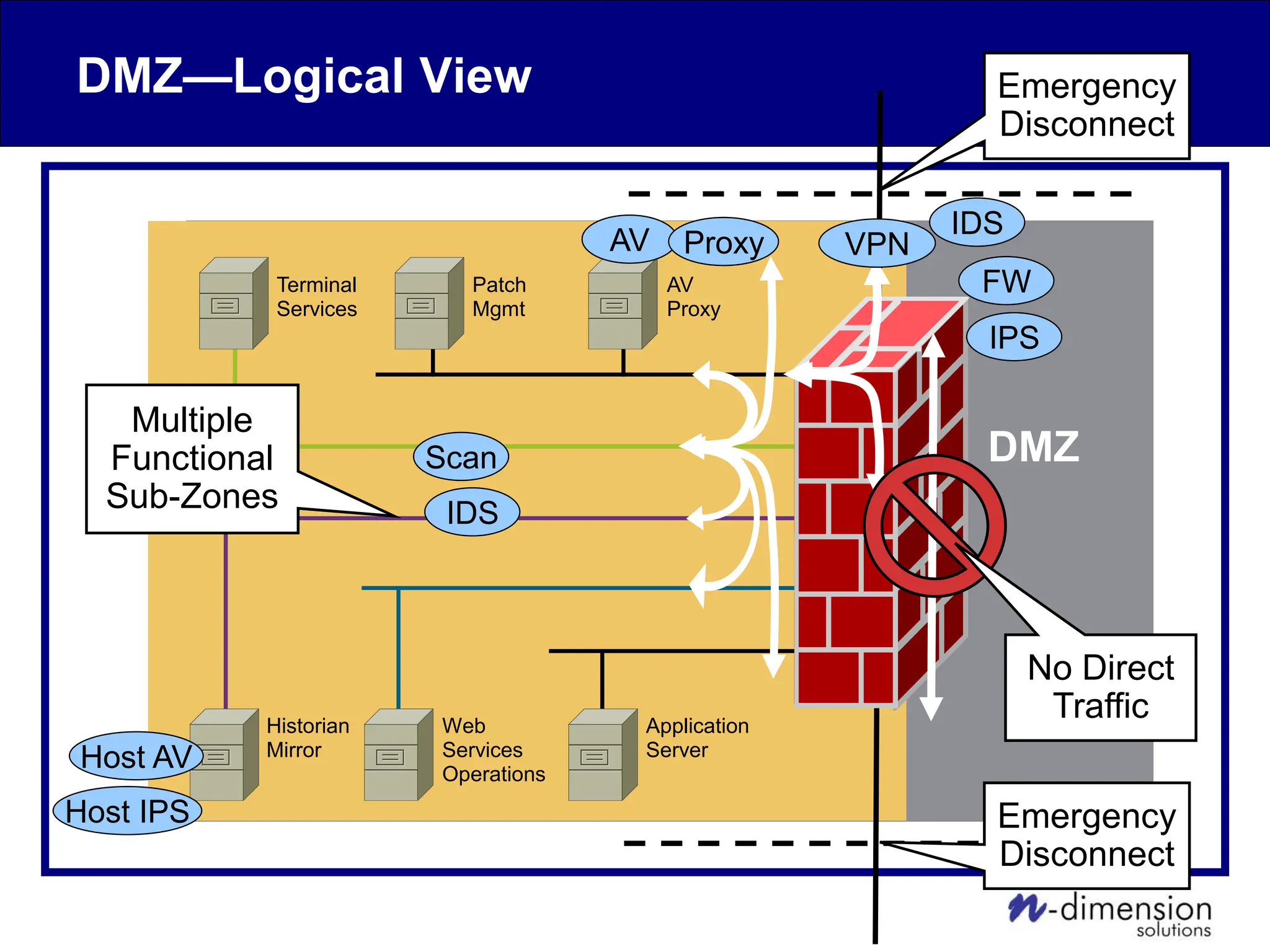
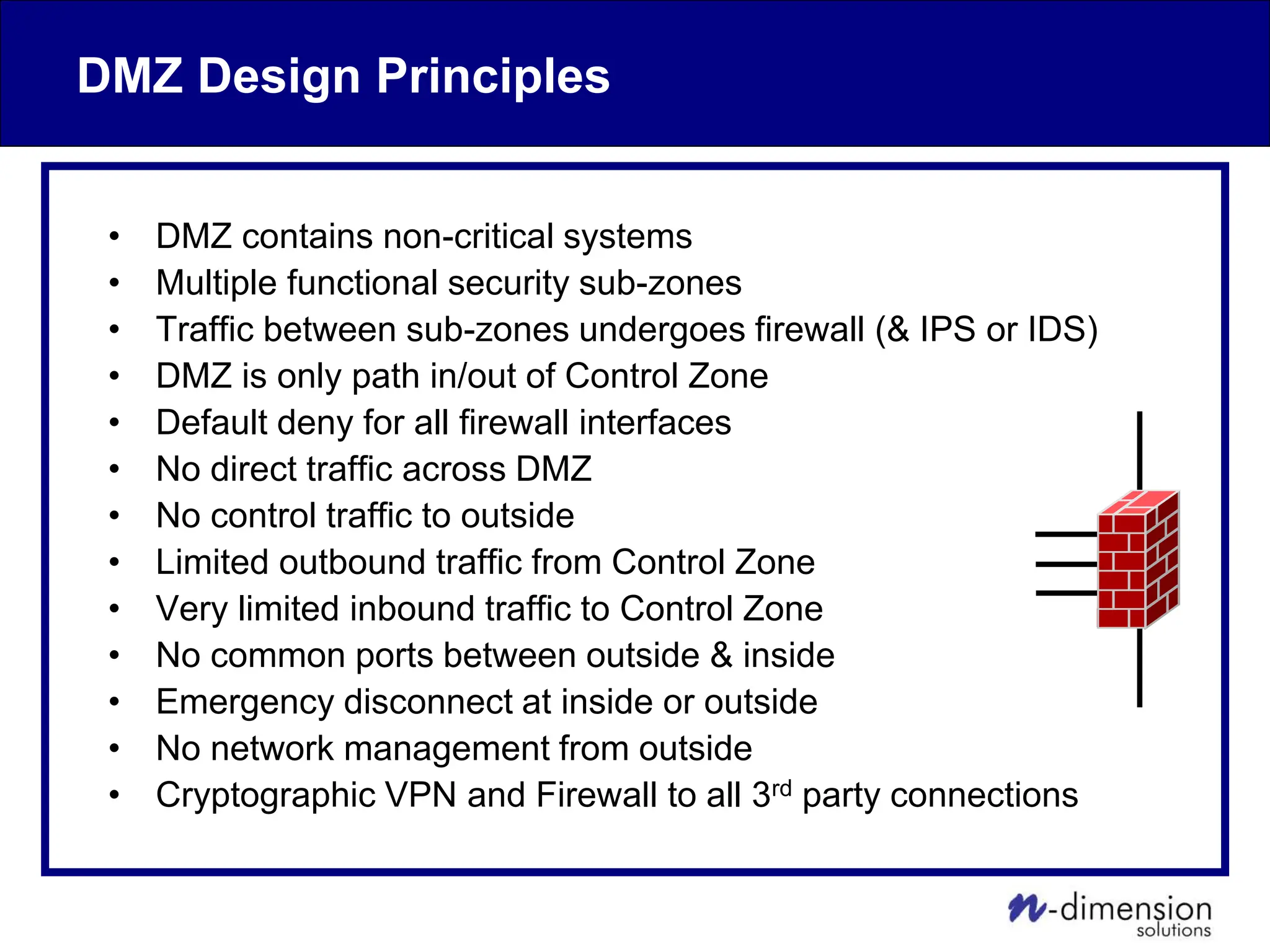
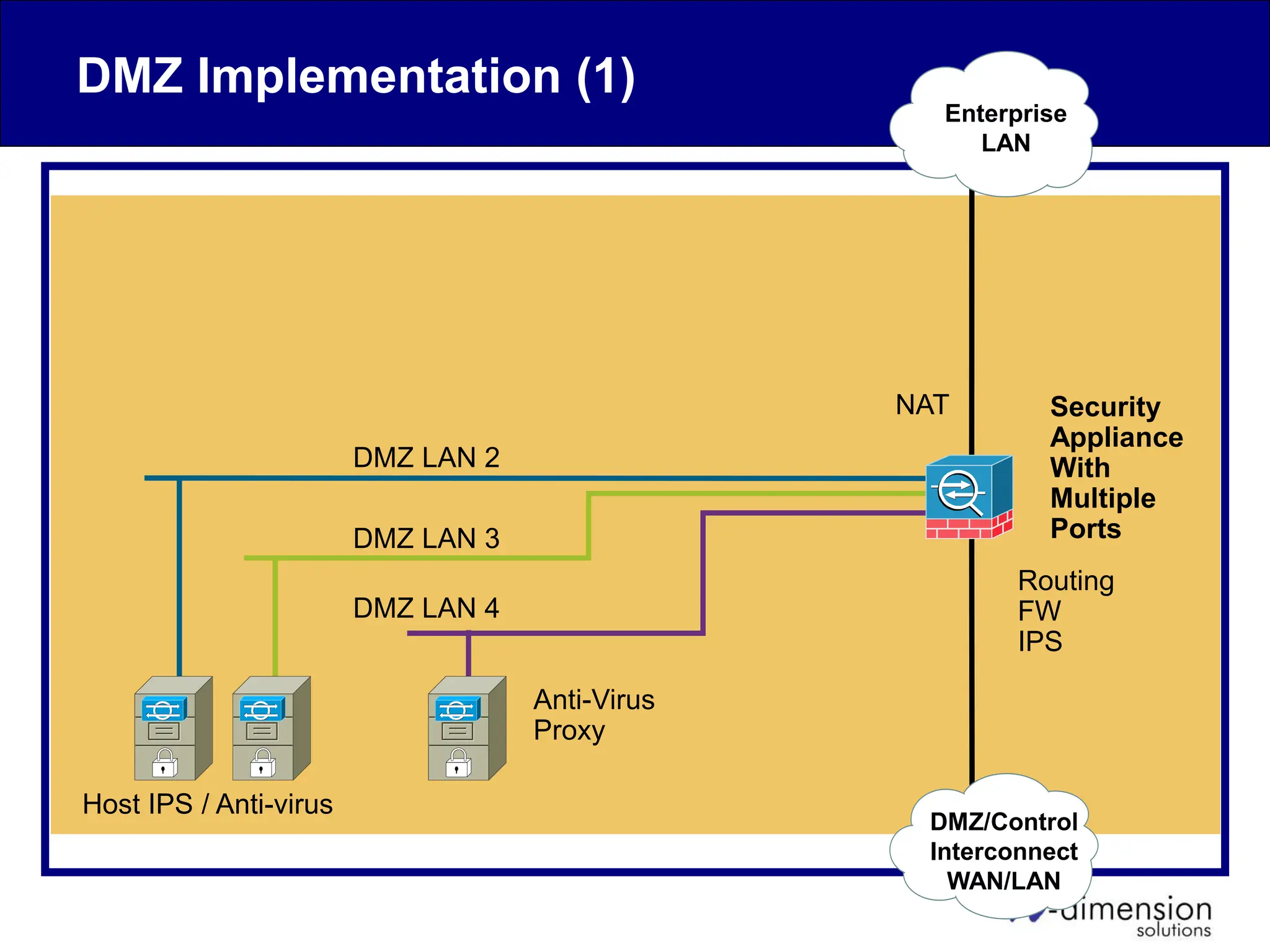
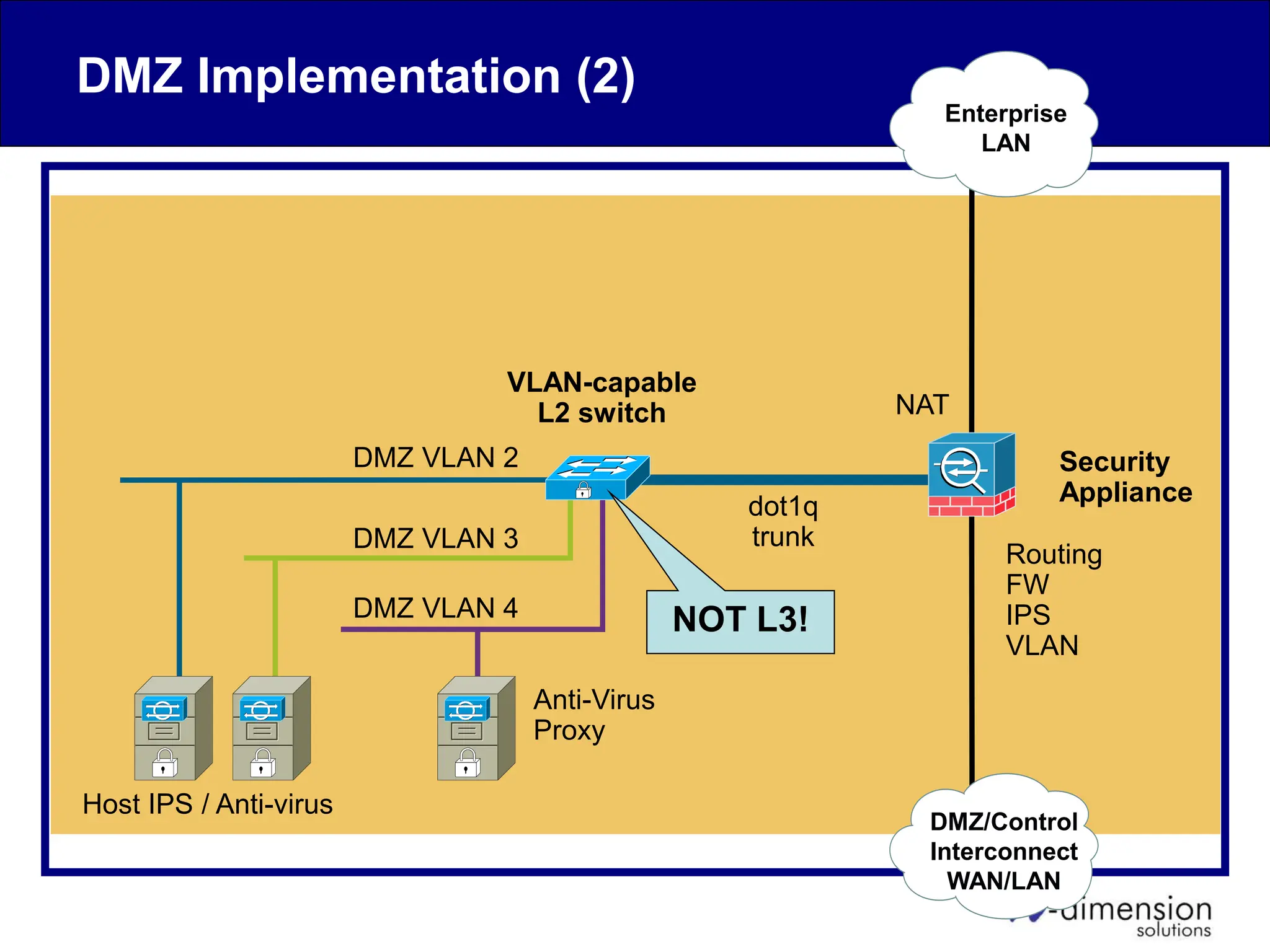
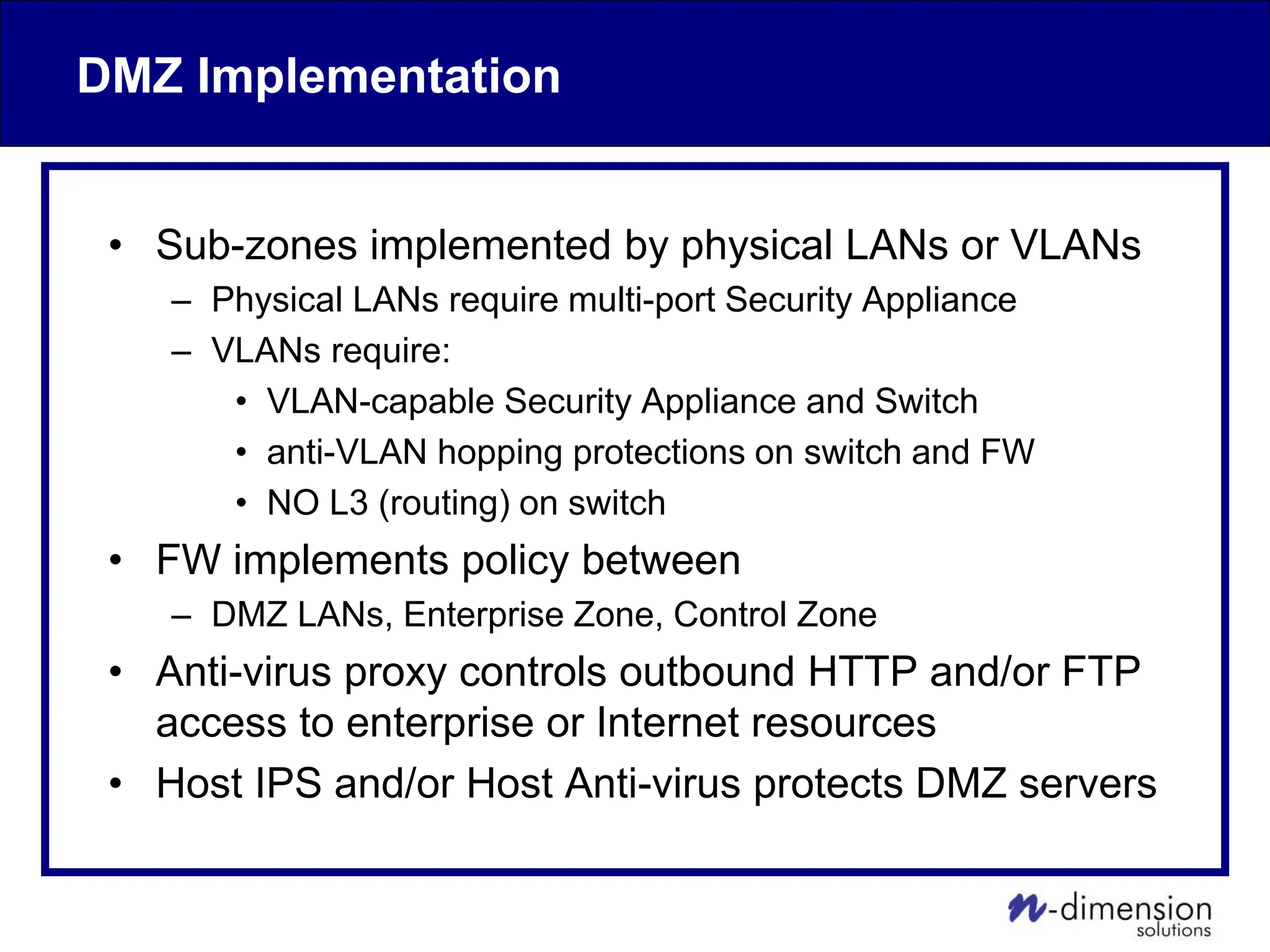
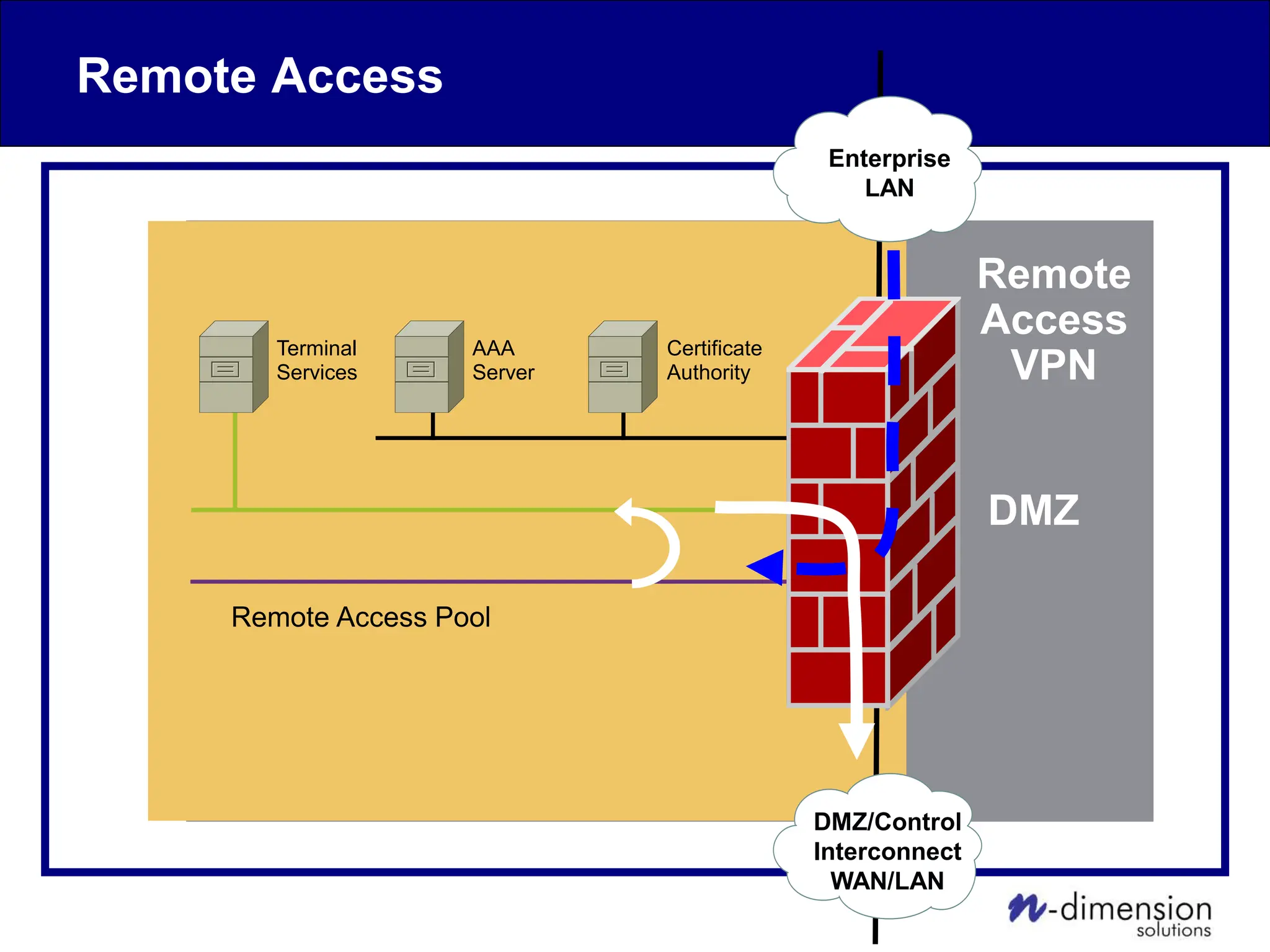
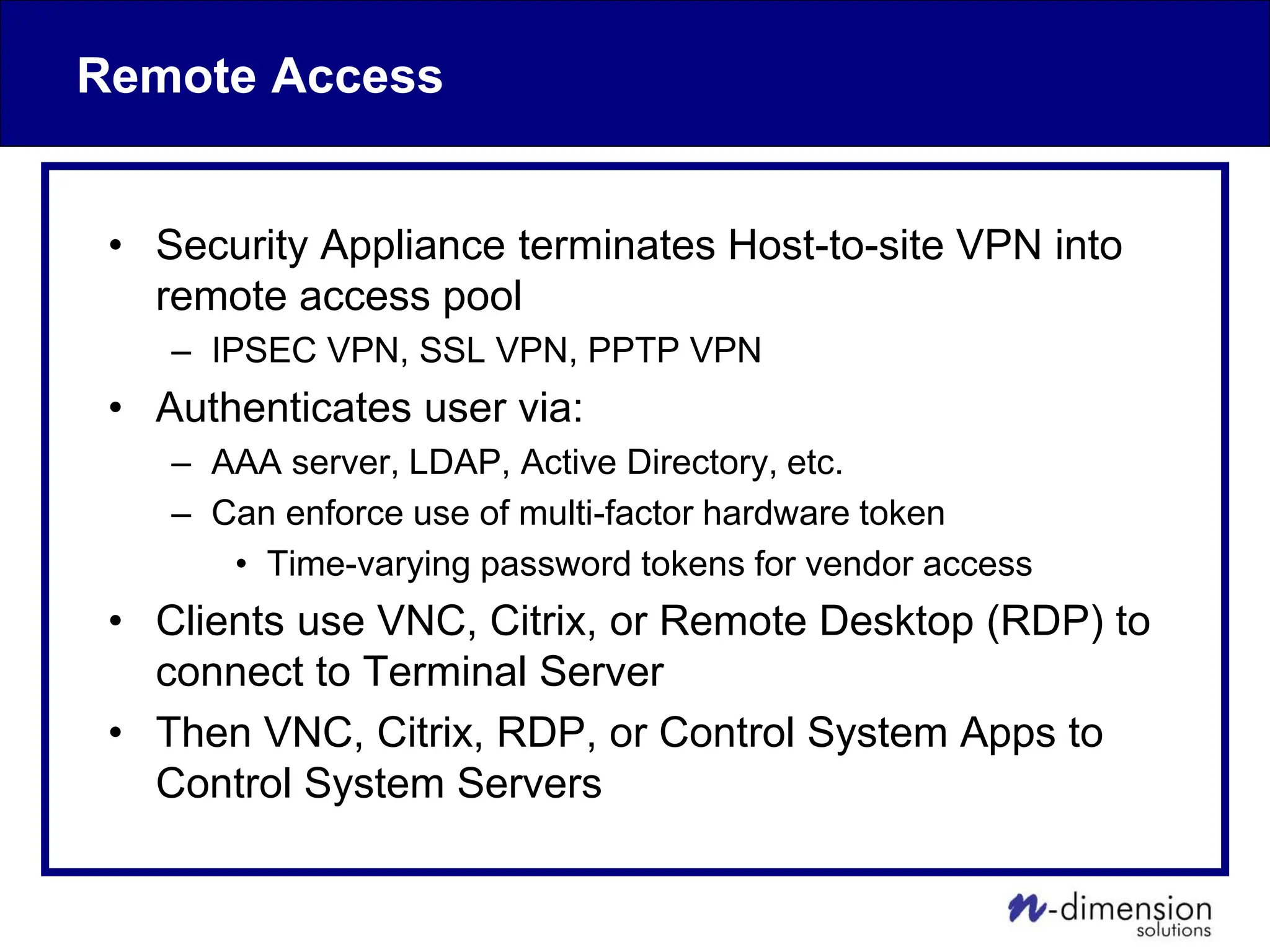
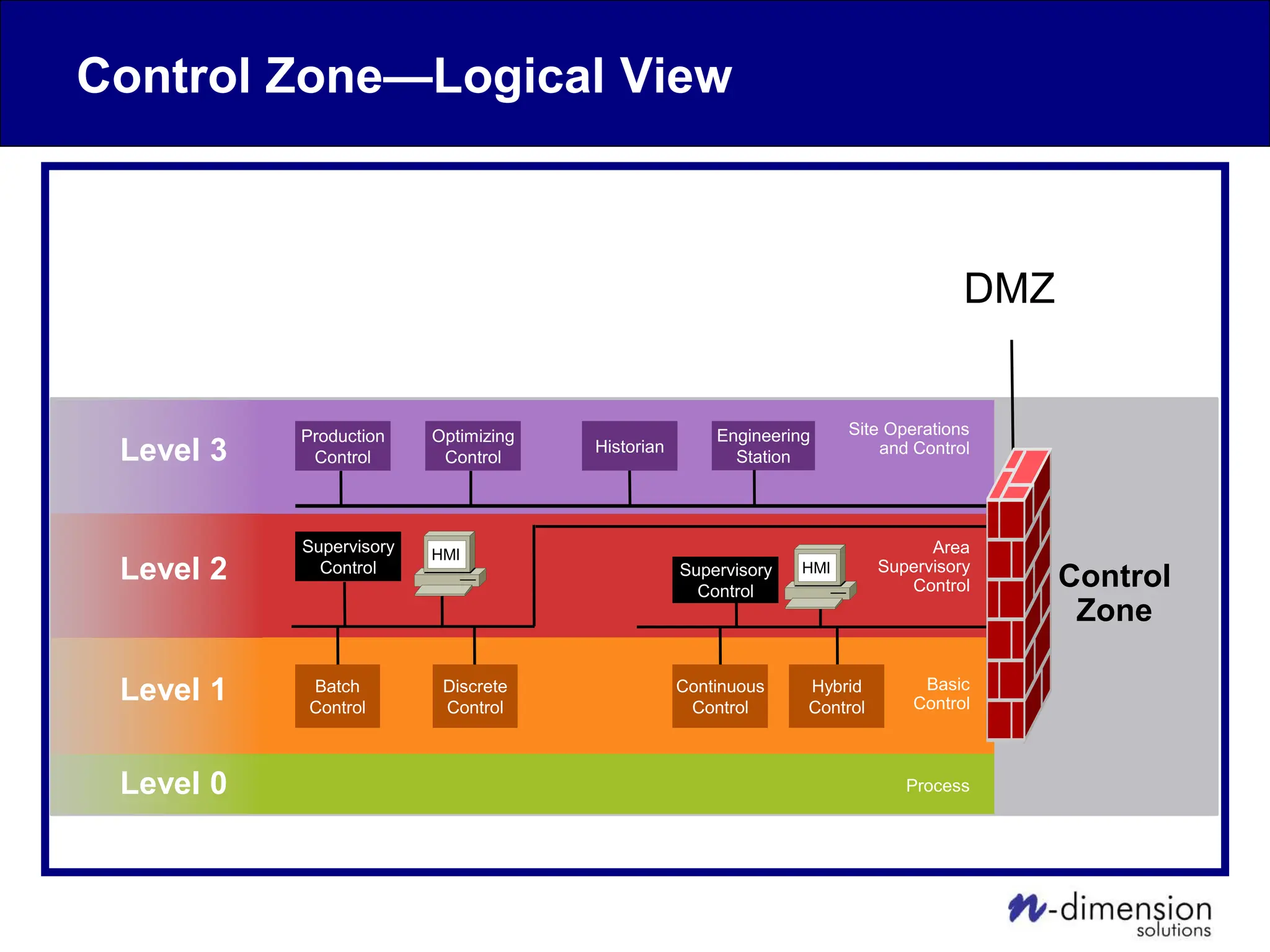
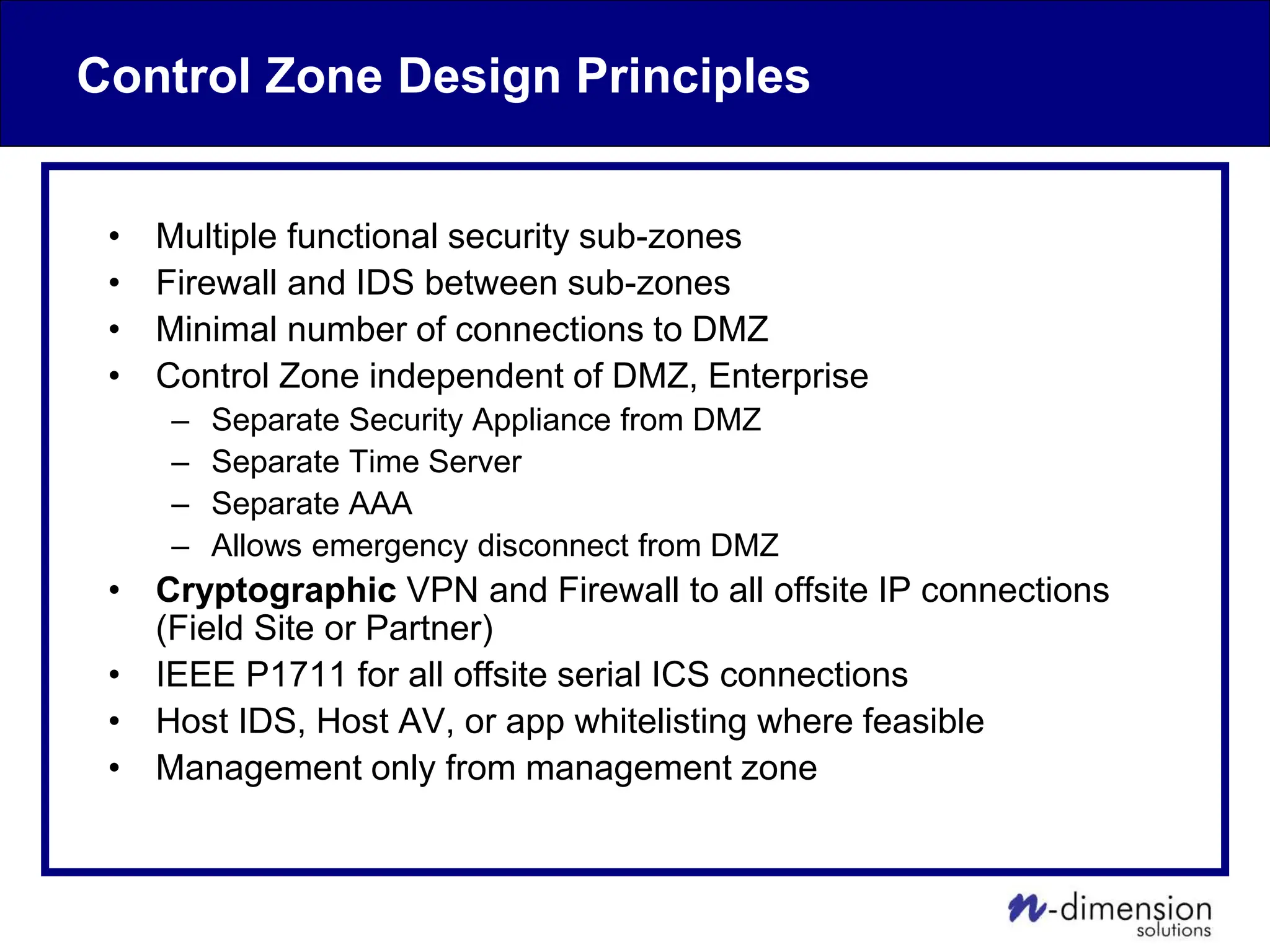
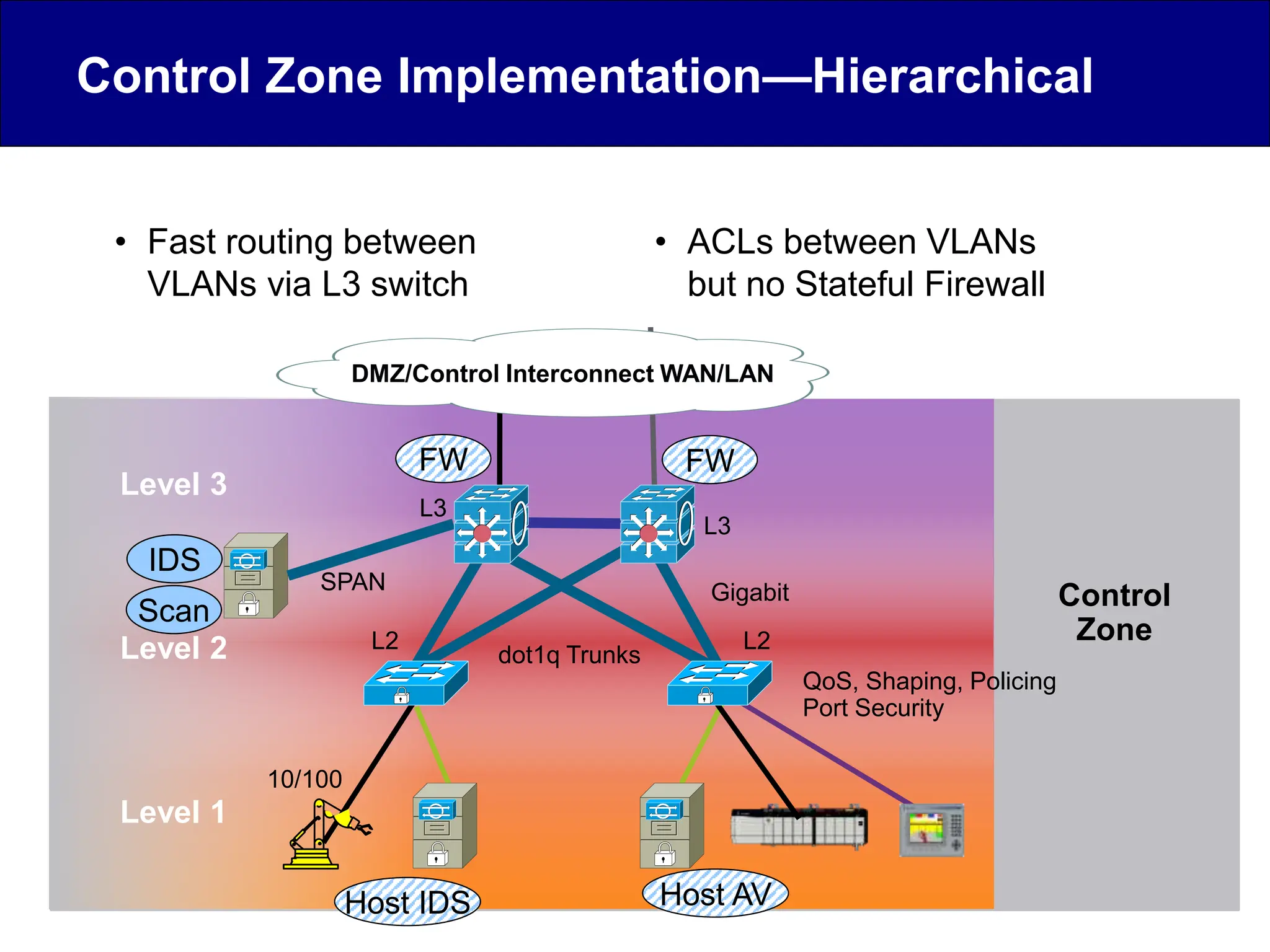
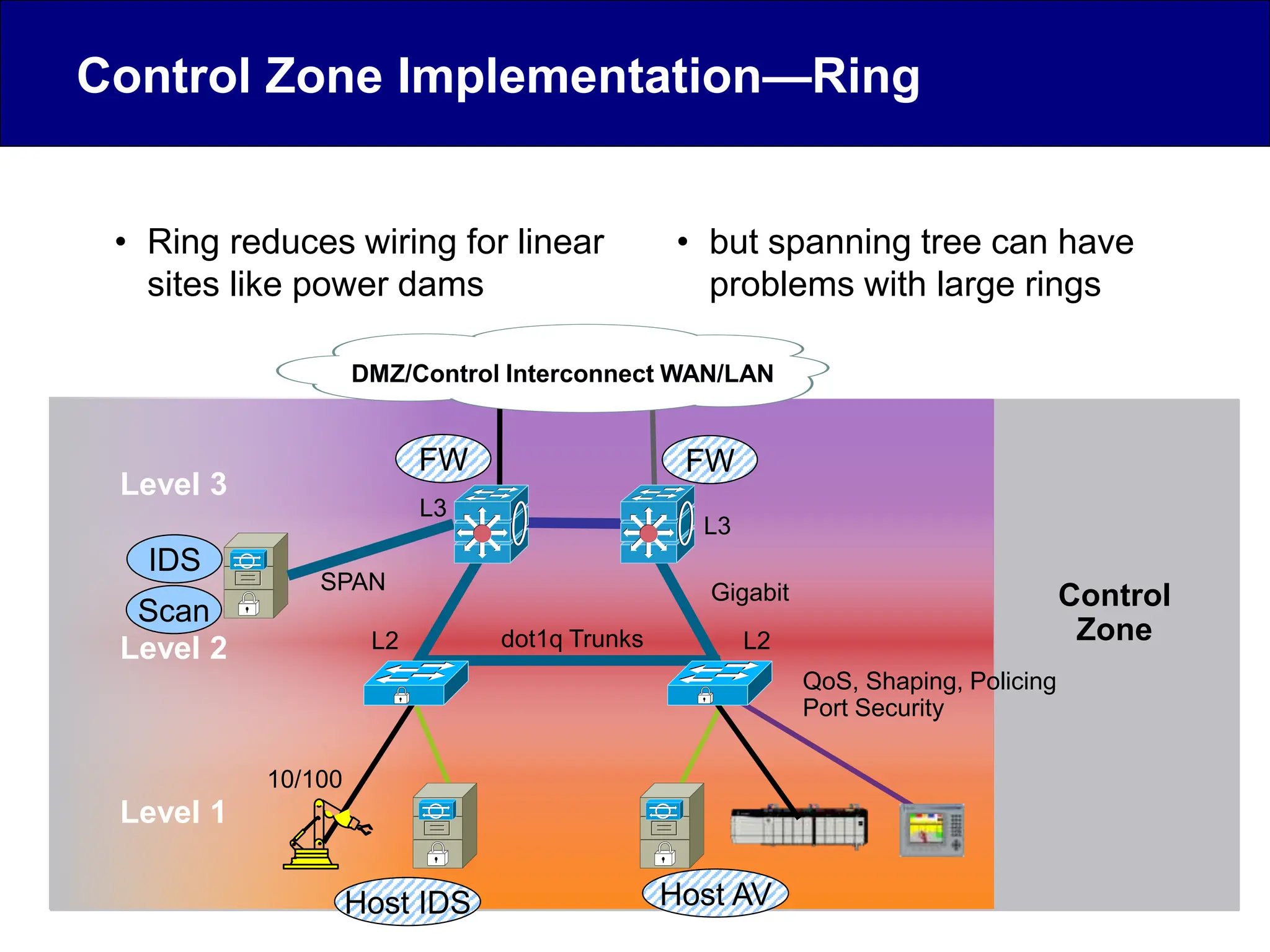
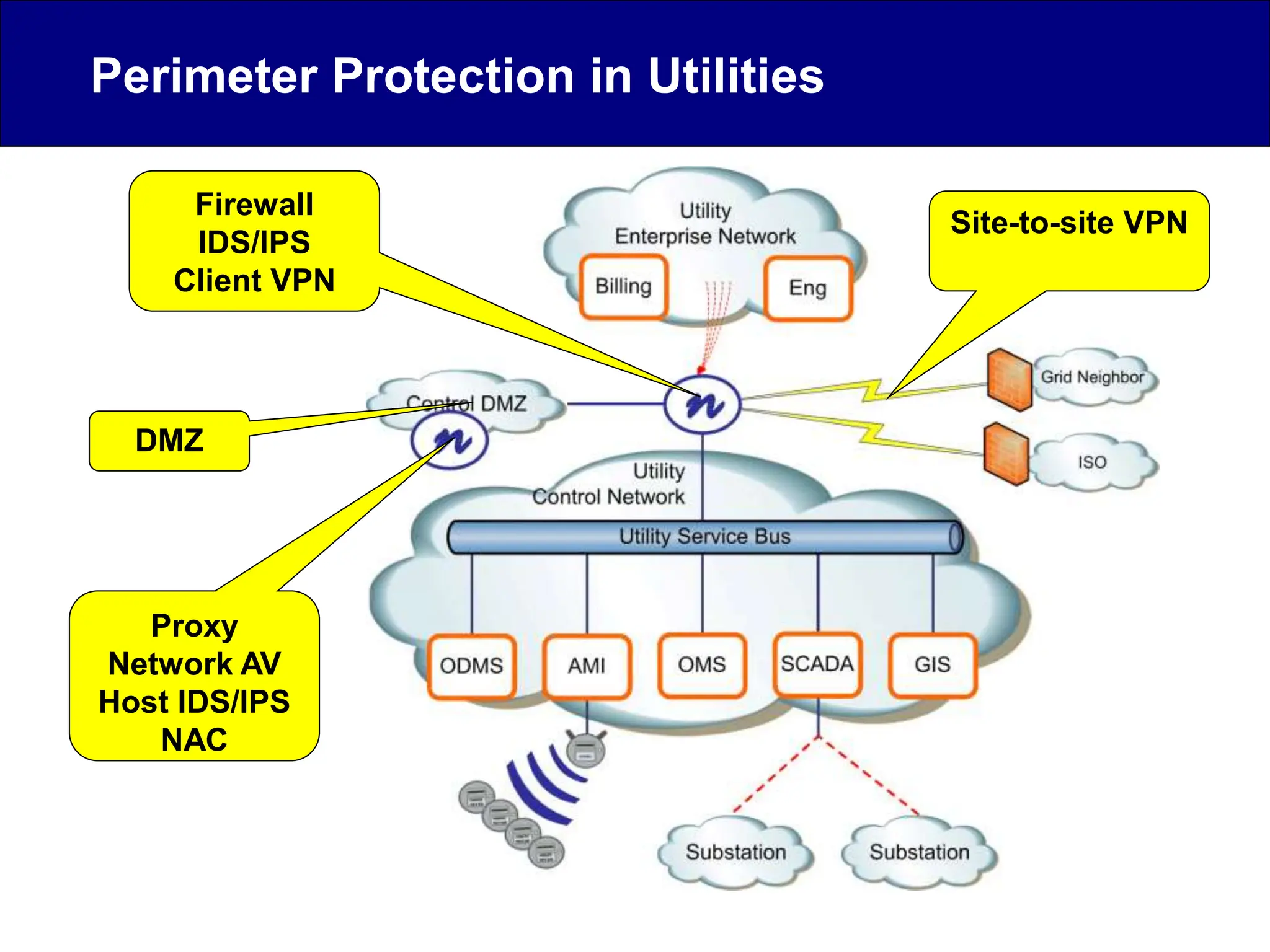
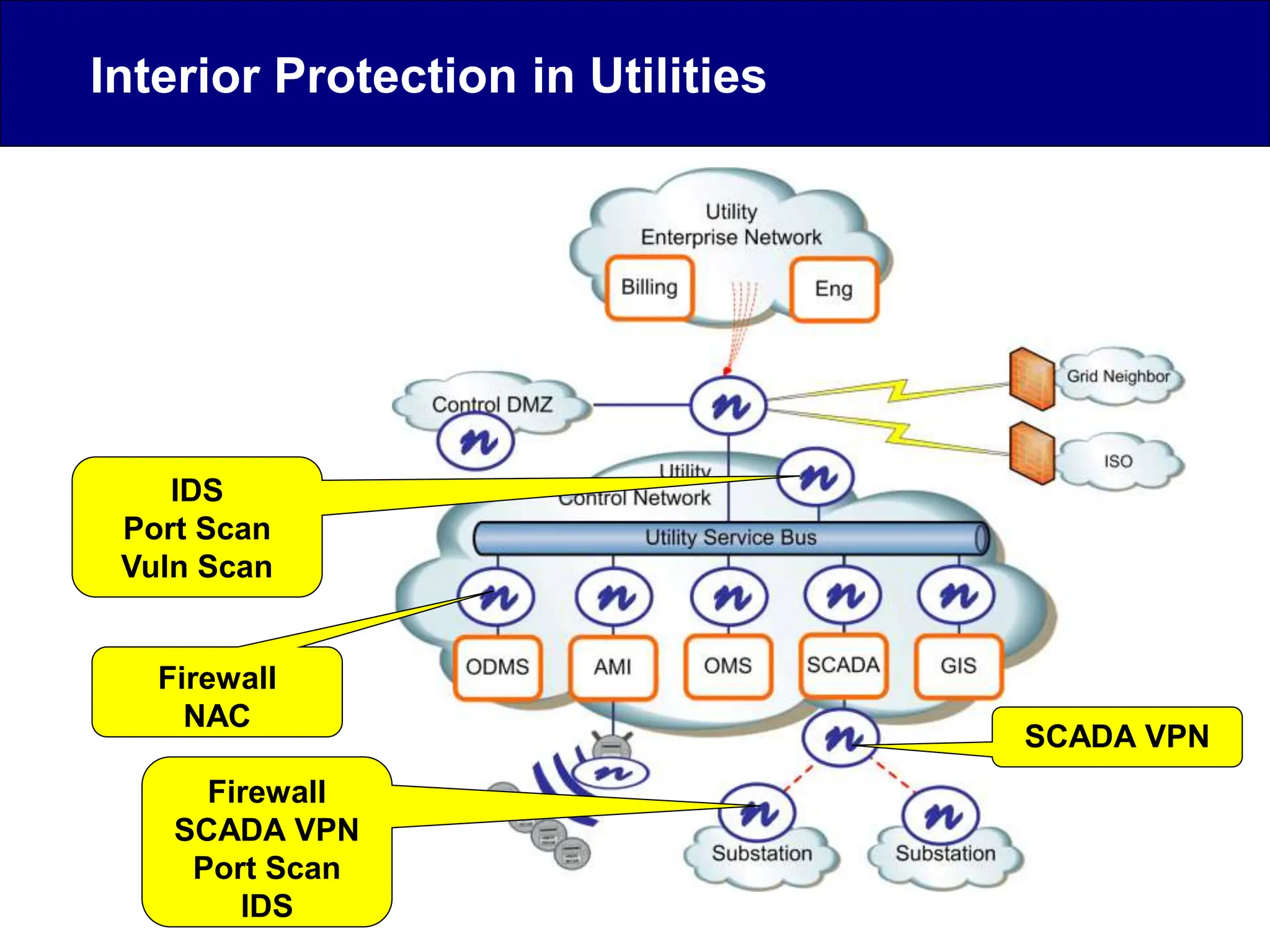
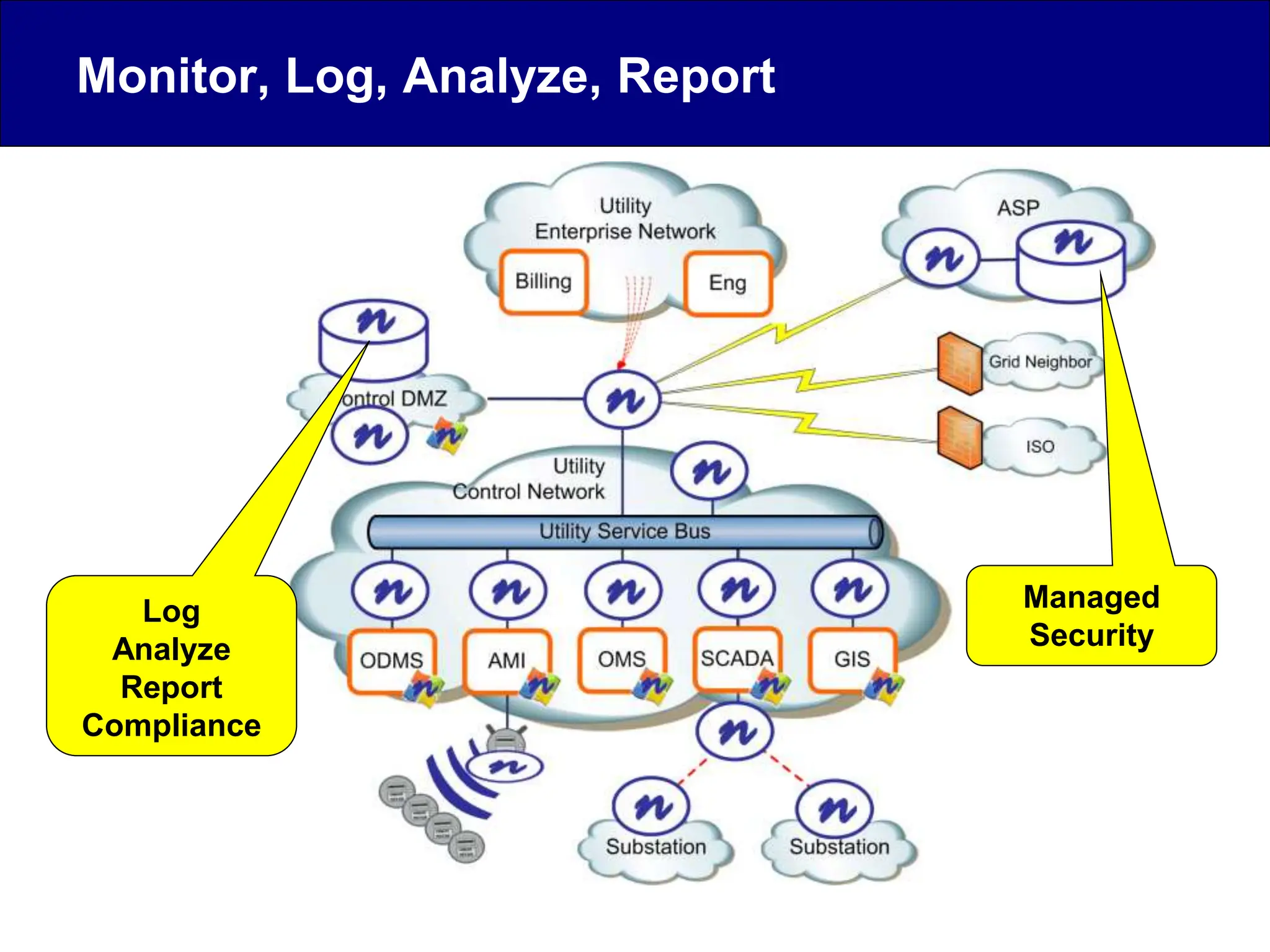
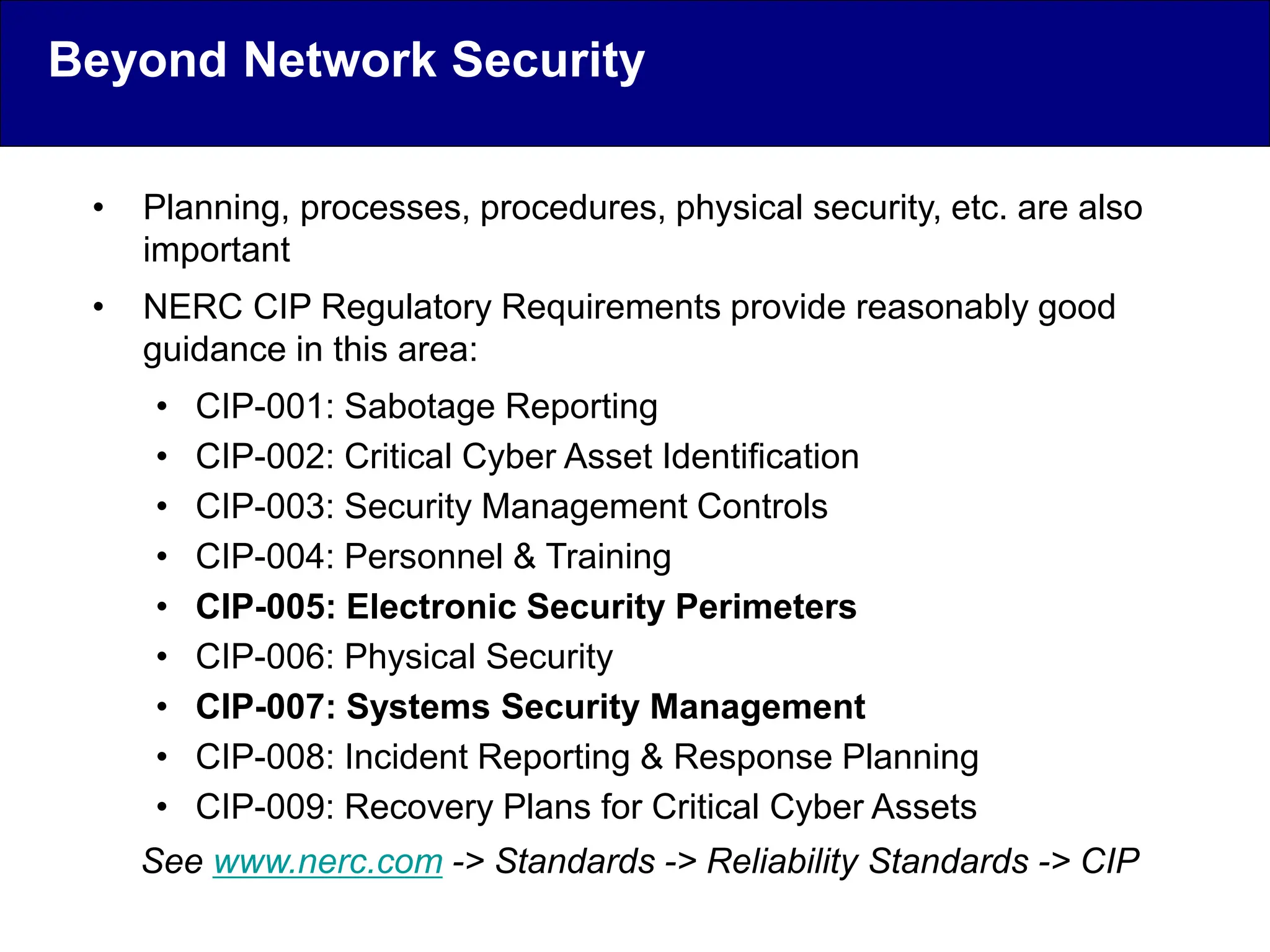
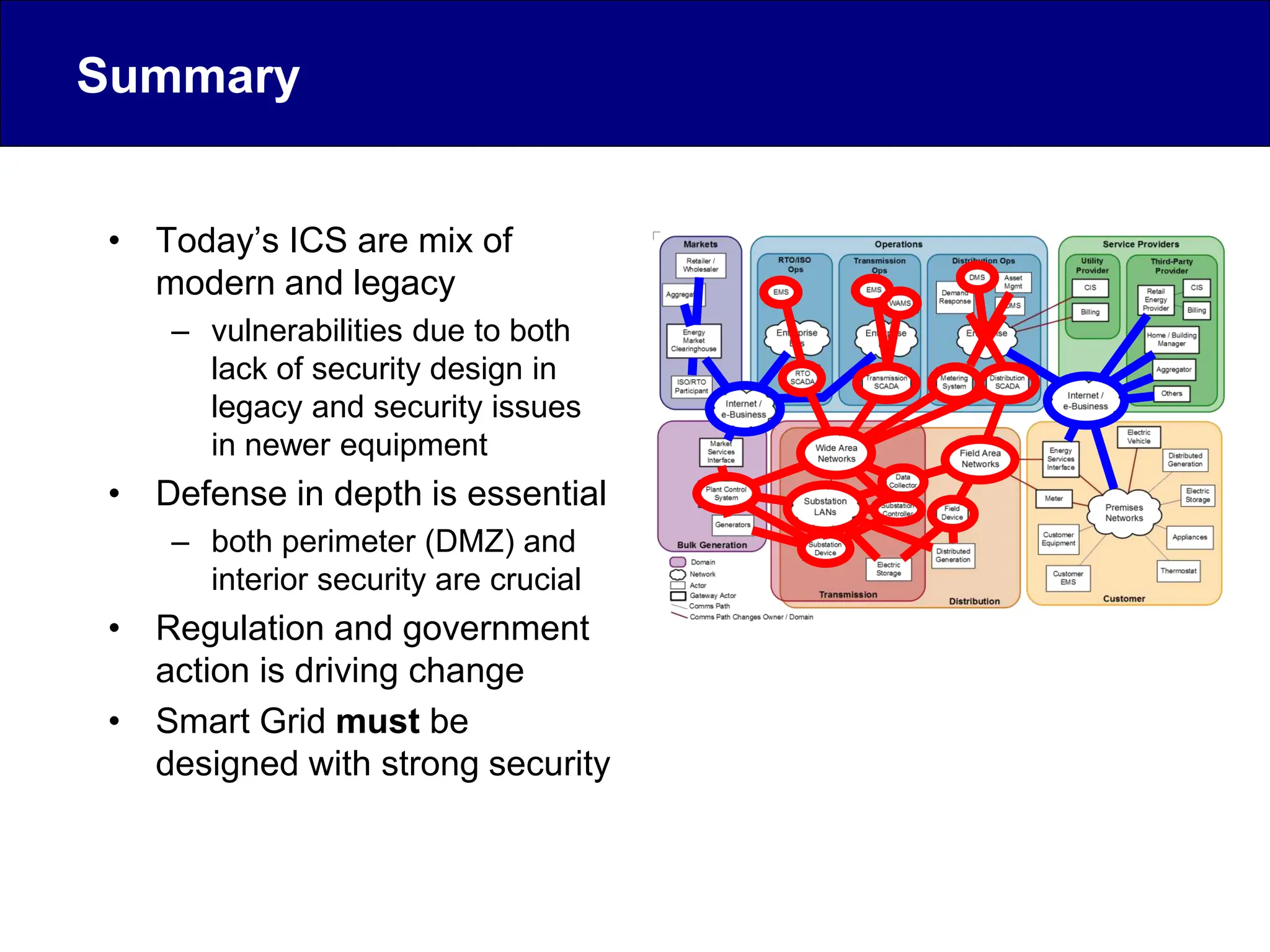
This document discusses cyber security issues related to industrial control systems (ICS) and securing control systems. It provides an overview of ICS types, historical context, technology trends incorporating more commercial off-the-shelf components and connectivity. This introduces security risks like worms, viruses, unauthorized access. Specific risks are examined like denial of service attacks, fragile devices, unpatched systems, poor authentication. The document outlines defense strategies like perimeter protection, interior security, monitoring and outlines how an attack could progress if not properly defended. It emphasizes separating control networks and hardening connections to frustrate opportunities for attackers.