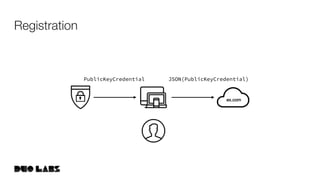
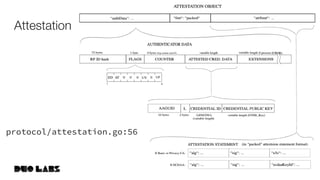
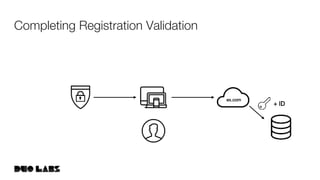
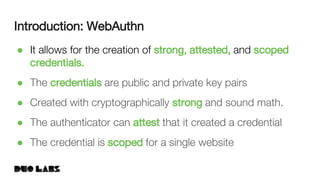
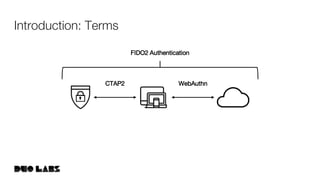
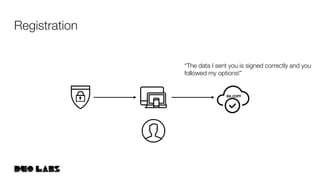
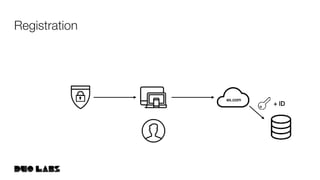
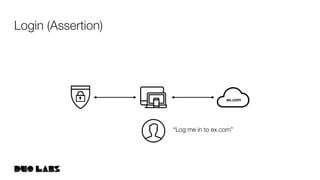
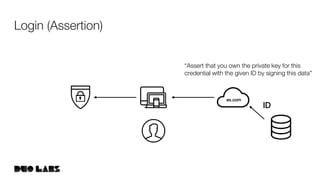
This document provides an overview and example of getting started with WebAuthn. It discusses the WebAuthn specification and terminology. It then demonstrates how to set up sample code to handle WebAuthn registration and login requests and responses. Specifically, it shows the structure of registration and login options that are sent to clients, and the credential responses that are returned, including parsing the response details. Key areas like challenges, credentials, attestation, and extensions are described. The document aims to help attendees understand how WebAuthn works at a high level and see an example implementation.













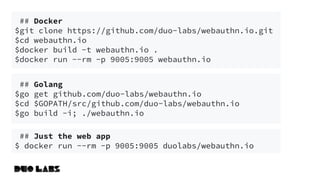











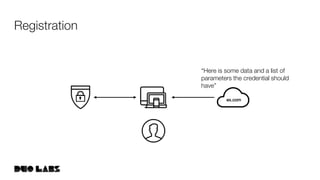
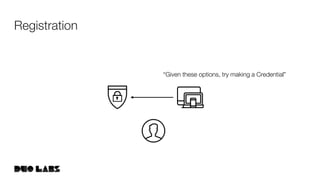
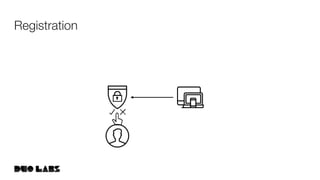
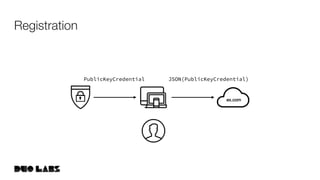

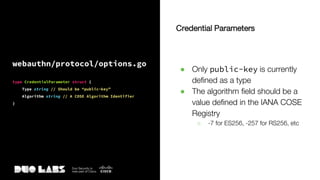
![webauthn/protocol/options.go
type PublicKeyCredentialCreationOptions struct {
Challenge Challenge
RelyingParty RelyingPartyEntity
User UserEntity
Parameters []CredentialParameter
AuthenticatorSelection AuthenticatorSelection
Timeout int
CredentialExcludeList []CredentialDescriptor
Attestation string
}
The Relying Party should
hand back a response that
looks like this
Credential Creation Options](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-52-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialCreationOptions struct {
Challenge Challenge
RelyingParty RelyingPartyEntity
User UserEntity
Parameters []CredentialParameter
AuthenticatorSelection AuthenticatorSelection
Timeout int
CredentialExcludeList []CredentialDescriptor
Attestation string
}
These 3 are required, the
rest are optional but
recommended.
Credential Creation Options](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-53-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialCreationOptions struct {
Challenge Challenge
RelyingParty RelyingPartyEntity
User UserEntity
Parameters []CredentialParameter
AuthenticatorSelection AuthenticatorSelection
Timeout int
CredentialExcludeList []CredentialDescriptor
Attestation string
}
● Generated by RP server-side.
● Helps prevent replay attacks
● Stored until the registration is
complete
○ As session data, in a DB, etc...
Challenge Parameter](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-54-320.jpg)

![webauthn/protocol/entities.go
type UserEntity struct {
Name string // Readable name used by the RP
Icon string
DisplayName string // Readable name chosen by the user
ID []byte // The RP’s ID for the user.
}
● Name and ID are required
● Display Name is used for the
user’s notification
User Information](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-56-320.jpg)

![webauthn/protocol/options.go
type PublicKeyCredentialCreationOptions struct {
Challenge Challenge
RelyingParty RelyingPartyEntity
User UserEntity
Parameters []CredentialParameter
AuthenticatorSelection AuthenticatorSelection
Timeout int
CredentialExcludeList []CredentialDescriptor
Attestation string
}
● The amount of time to allow the
authenticator/user to respond
● Not required by the client
○ May actually be overridden
● Uses milliseconds
● Recommend 60 seconds
○ That’s 60000 milliseconds!
Timeout Parameter](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-59-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialCreationOptions struct {
Challenge Challenge
RelyingParty RelyingPartyEntity
User UserEntity
Parameters []CredentialParameter
AuthenticatorSelection AuthenticatorSelection
Timeout int
CredentialExcludeList []CredentialDescriptor
Attestation string
}
● Allows us to exclude an
authenticator if it contains a
credential described in this list
● This is helpful for registering
multiple authenticators
● We’ll talk more about the
CredentialDescriptor
object later.
Credential Exclusion List](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-60-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialCreationOptions struct {
Challenge Challenge
RelyingParty RelyingPartyEntity
User UserEntity
Parameters []CredentialParameter
AuthenticatorSelection AuthenticatorSelection
Timeout int
CredentialExcludeList []CredentialDescriptor
Attestation string
}
● Tells us if we want the
authenticator to attest the
credential
● Three conveyance types
○ Direct
○ Indirect
○ None
Attestation Conveyence](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-61-320.jpg)
![In JSON
Provided to
navigator.credentials.create()
Requested at line 105 in
webauthn.io/static/dist/js/webauthn.js
{
"challenge":"InlQbas7et/4C0DVVW9/4qzoz2NuyM9c=",
"rp": {
"name": "webauthn.io",
"id": "webauthn.io"
},
"user": {
"name": "testuser",
"displayName": "testuser",
"id": "9AUAAAAAAAAAAA=="
},
"pubKeyCredParams": [
{
"type": "public-key",
"alg": -7
},
...
],
"authenticatorSelection": {
"authenticatorAttachment": "platform",
"requireResidentKey": false,
"userVerification": "preferred"
},
"timeout": 60000,
"attestation": "direct"
}
Registration Request](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-63-320.jpg)
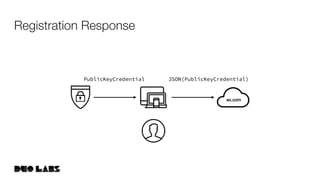

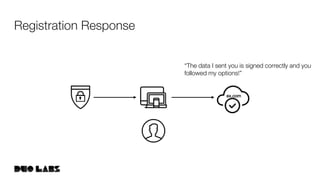
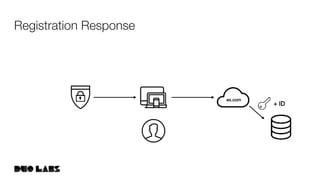





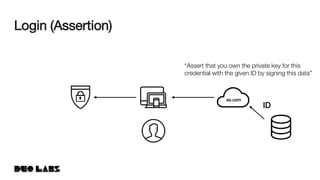
![webauthn/protocol/options.go
type PublicKeyCredentialRequestOptions struct {
Challenge Challenge
Timeout int
RelyingPartyId string
AllowedCredentials []CredentialDescriptor
UserVerification string
}
The Relying Party should
hand back a response that
looks like this
Credential Assertion Options](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-75-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialRequestOptions struct {
Challenge Challenge
Timeout int
RelyingPartyId string
AllowedCredentials []CredentialDescriptor
UserVerification string
}
● Challenge is the only
requirement!
○ Same structure as prior
Challenge Parameter](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-76-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialRequestOptions struct {
Challenge Challenge
Timeout int
RelyingPartyId string
AllowedCredentials []CredentialDescriptor
UserVerification string
}
● Same as in Creation
Request
Timeout Parameter](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-77-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialRequestOptions struct {
Challenge Challenge
Timeout int
RelyingPartyId string
AllowedCredentials []CredentialDescriptor
UserVerification string
}
● The URL of the RP
○ Can be inferred by client
Relying Party ID Attribute](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-78-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialRequestOptions struct {
Challenge Challenge
Timeout int
RelyingPartyId string
AllowedCredentials []CredentialDescriptor
UserVerification string
}
● List of Credential
Descriptions to allow for
● Should contain the
credentials registered to
the user for an RP
Allowed Credential List](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-79-320.jpg)
![webauthn/protocol/options.go
type CredentialDescriptor struct {
Type string // Should be “public-key”
CredentialID []byte // Stored Credential ID
Transport []string // “usb”,“nfc”,“ble”,”internal”
// “lightning” transport added recently!
}
● Type will be “public-key”
● Credential ID is the stored ID
● What transports the
authenticator should use assert
the credential.
○ Internal should be used if the
authenticator is built in to the
device.
Credential Descriptor](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-80-320.jpg)
![webauthn/protocol/options.go
type PublicKeyCredentialRequestOptions struct {
Challenge Challenge
Timeout int
RelyingPartyId string
AllowedCredentials []CredentialDescriptor
UserVerification string
}
● Should the user be verified by
the authenticator?
○ Required
○ Preferred
○ Discouraged
● User Verification == “Human”
Verification
● Defaults to preferred
● If set to required, client will
exclude ineligible authenticators
User Verification Requirements](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-81-320.jpg)
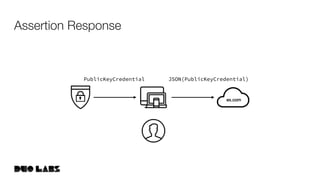
![In JSON
Provided to
navigator.credentials.get()
Requested at line 105 in
webauthn.io/static/dist/js/webauthn.js
{
"publicKey": {
"challenge": "DTea9k7tF9waXg0LTbOVOEvm0unHoo=",
"timeout": 60000,
"rpId": "webauthn.io",
"allowCredentials": [
{
"type": "public-key",
"id": "KWUeR0DoUAkpS5S3nHydoK..."
},
-- More Allowed Credentials -
-
{
"type": "public-key",
"id": "i7yvlHv0YMF3BK81VeqIdW..."
}
]
}
Assertion Request](https://image.slidesharecdn.com/developertrack02webauthntutorial-190925155456/85/Getting-Started-With-WebAuthn-83-320.jpg)