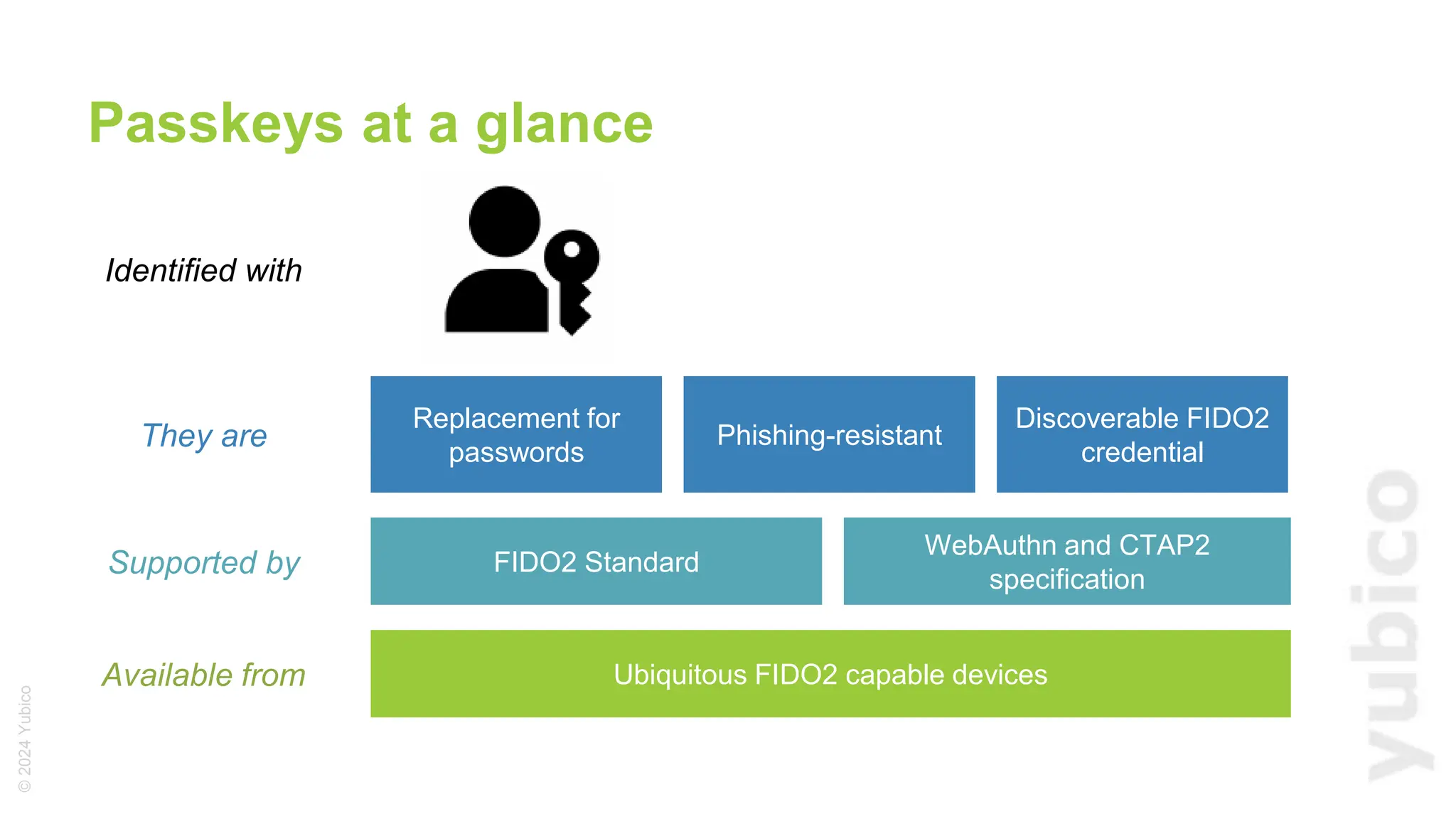
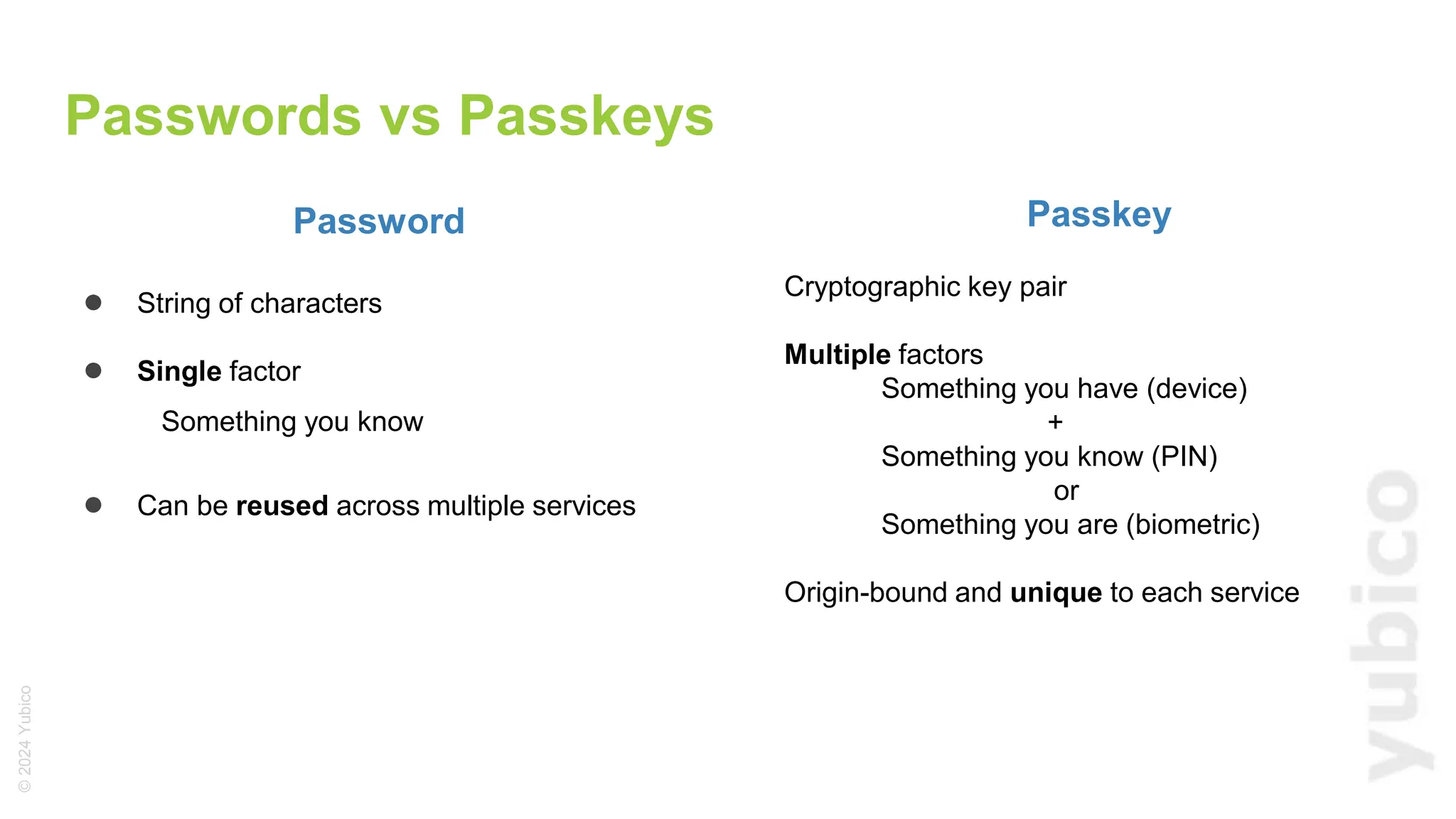
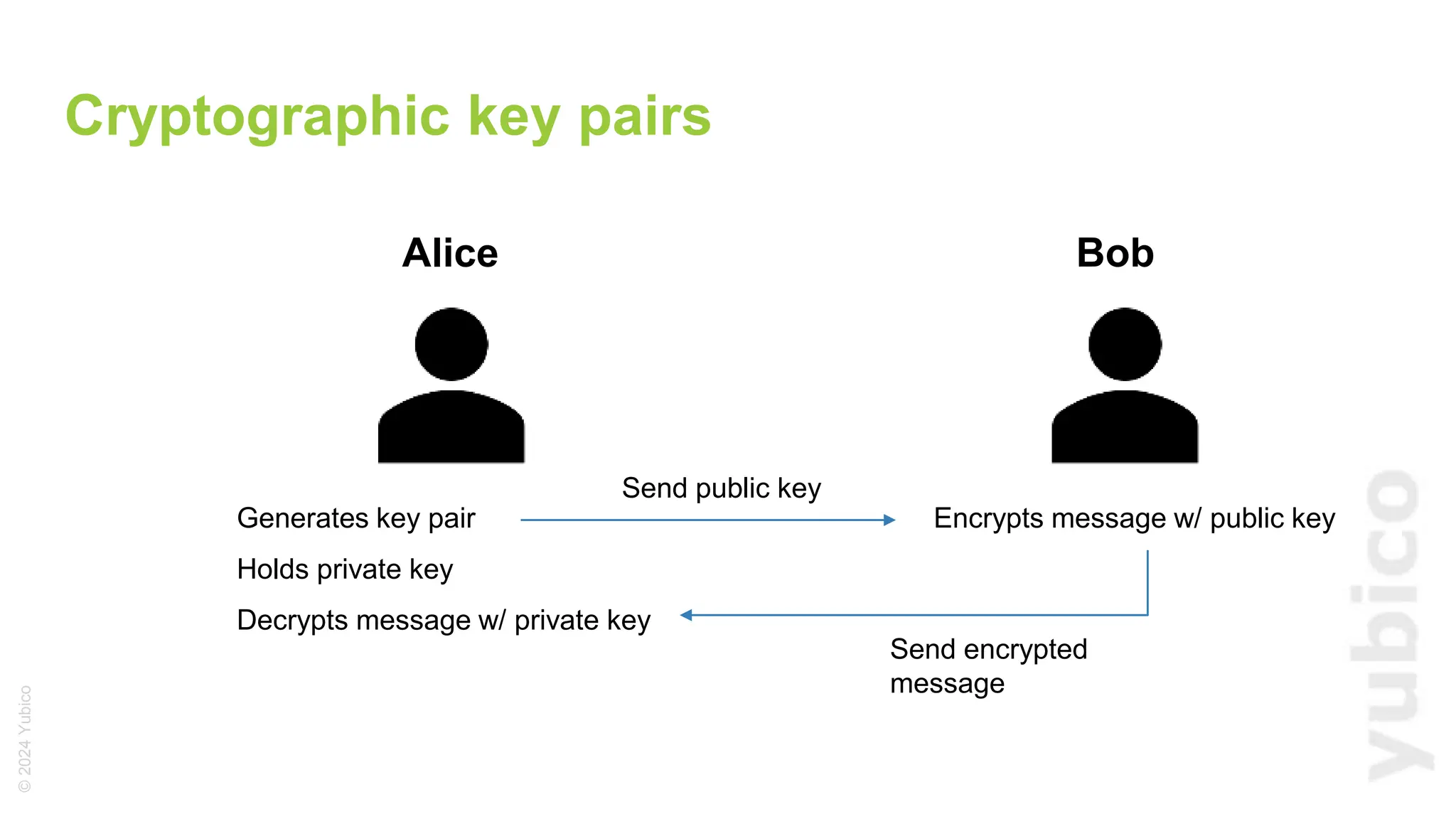
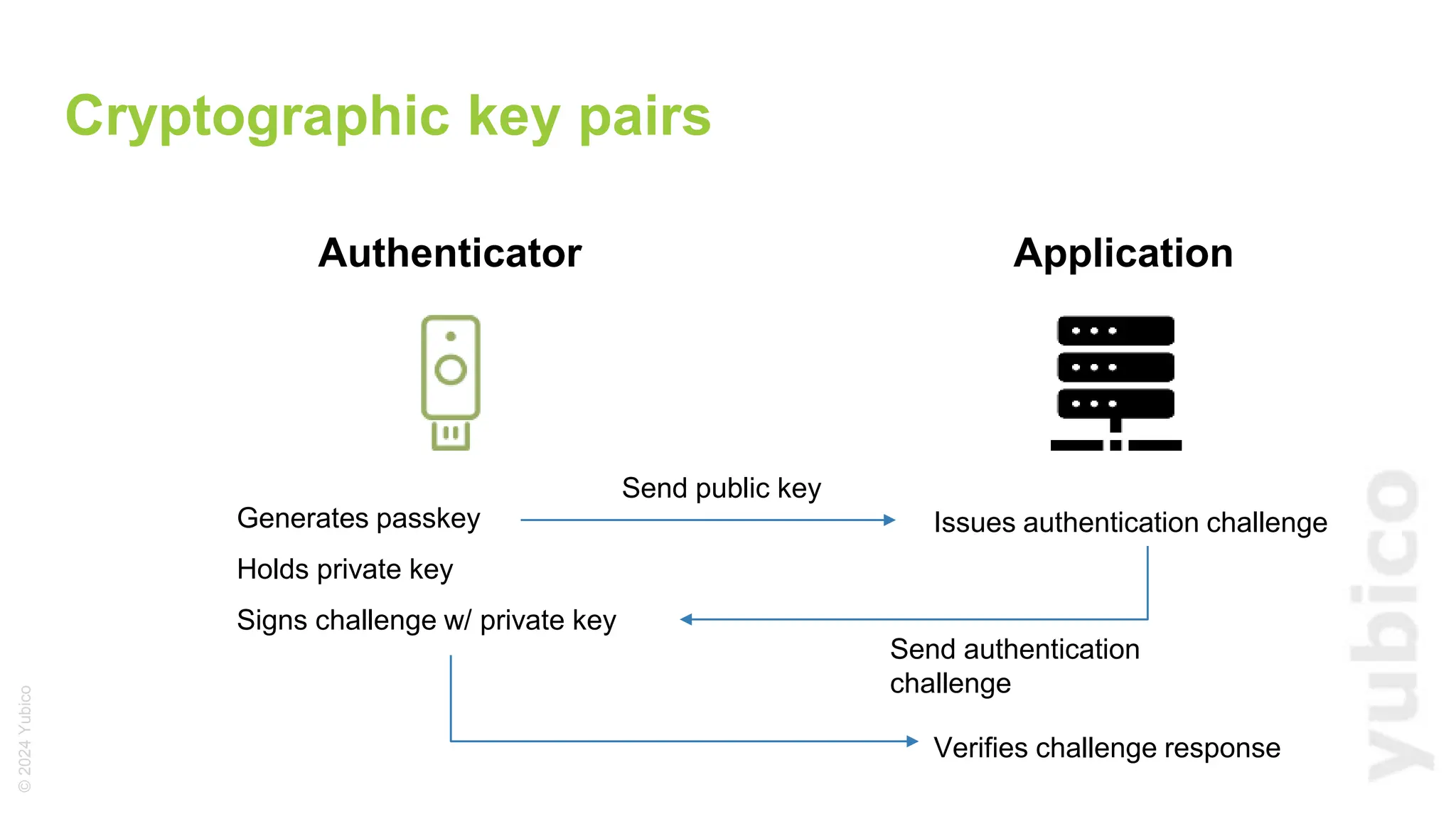
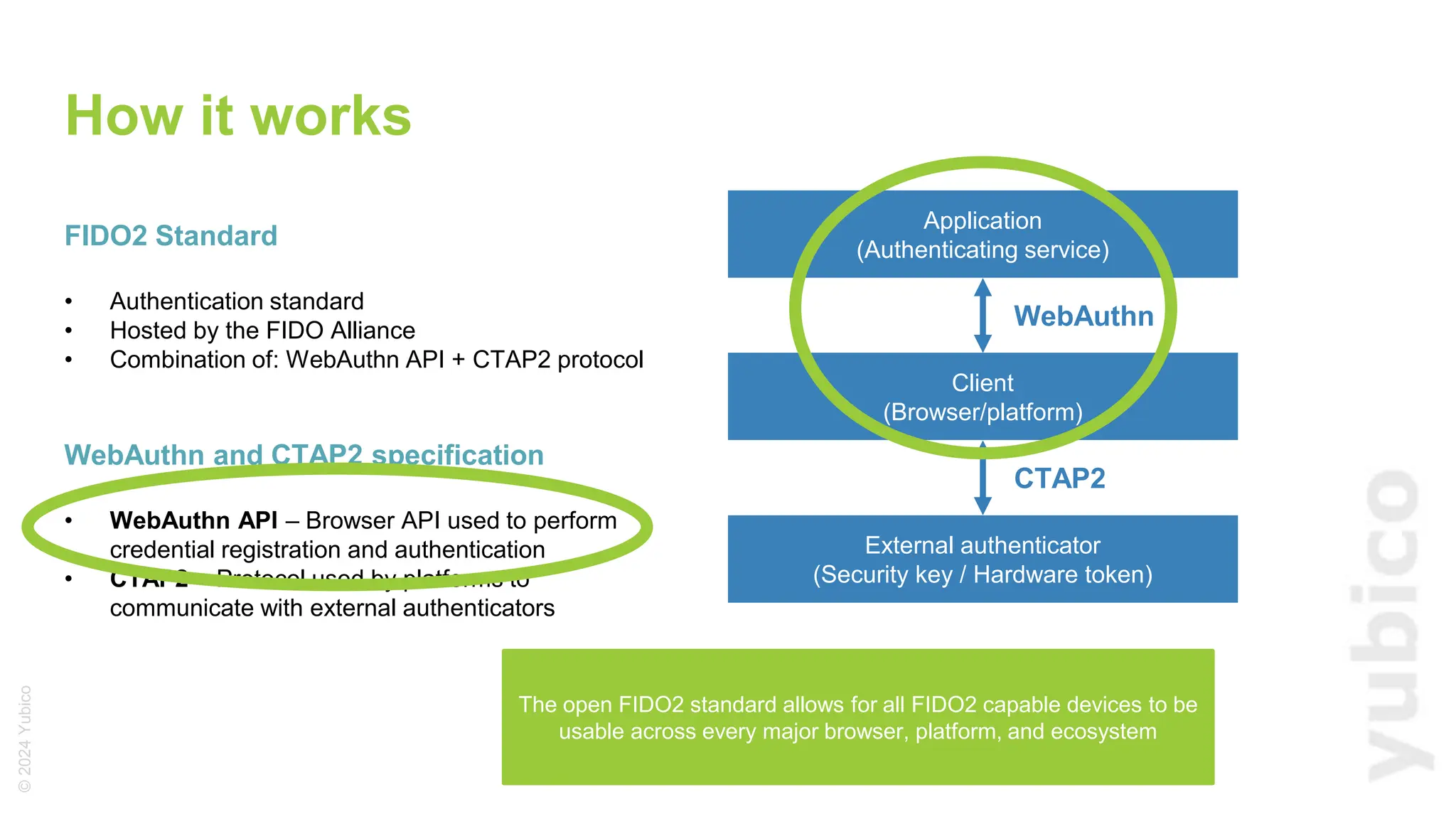
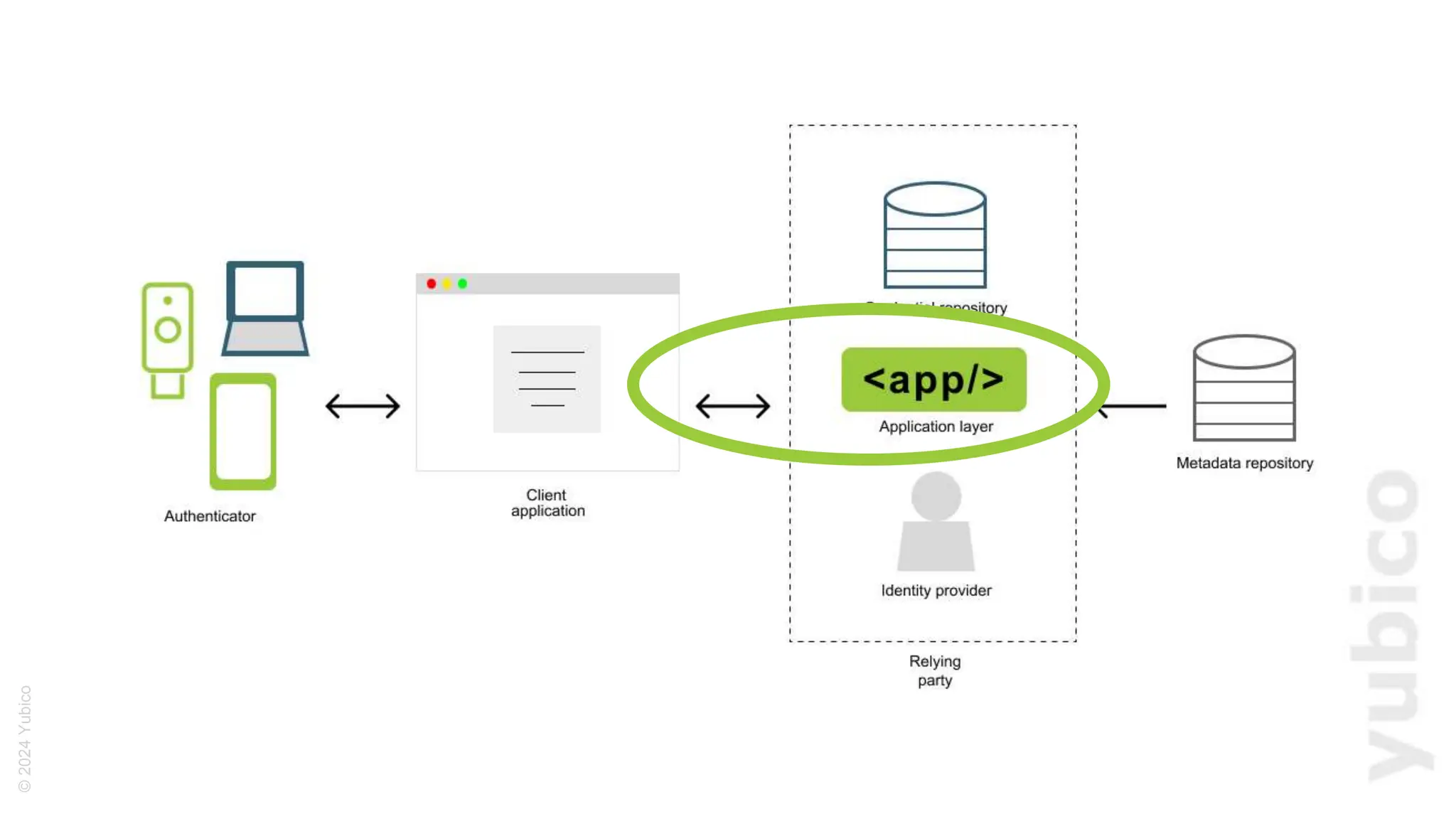
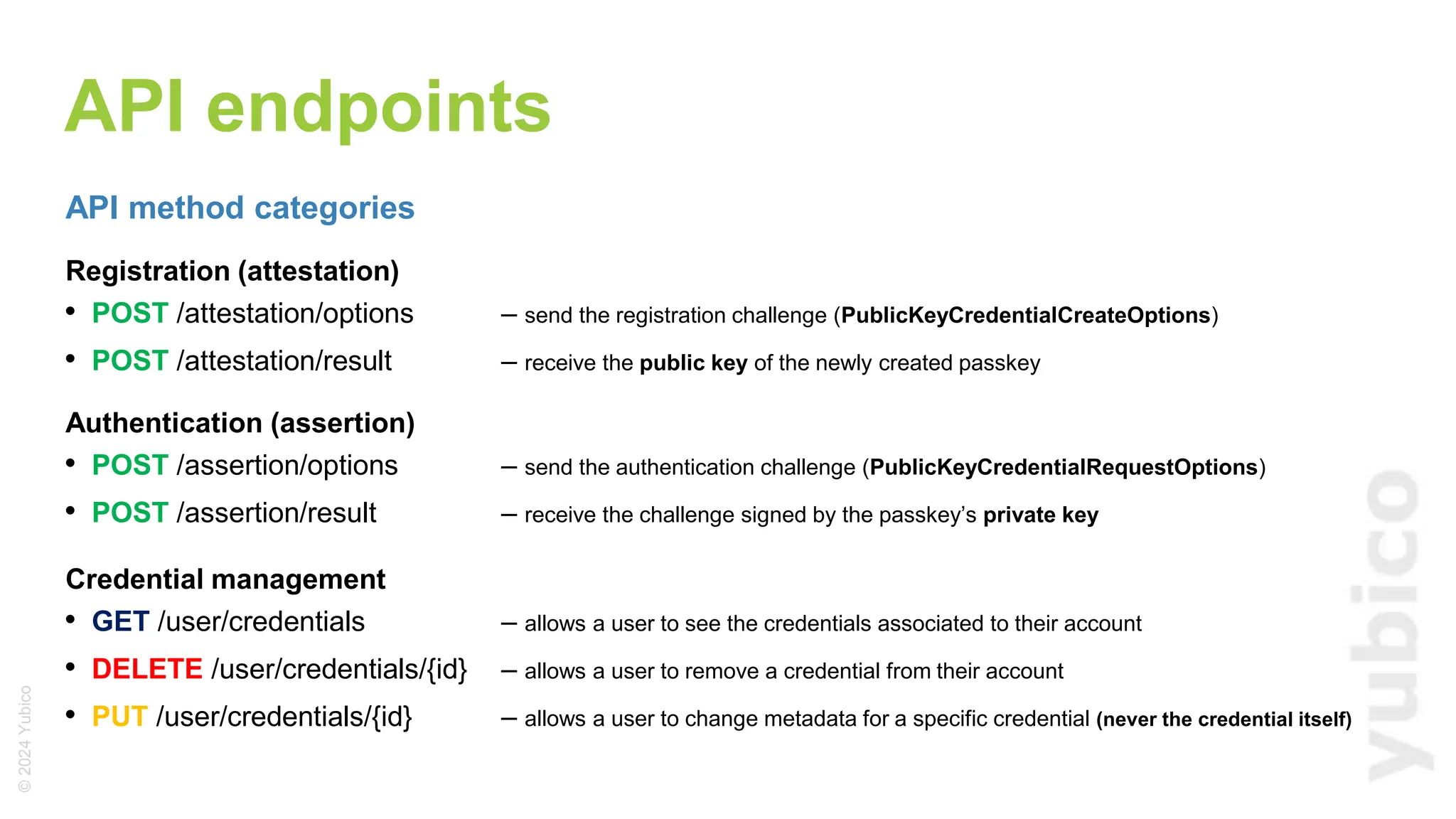
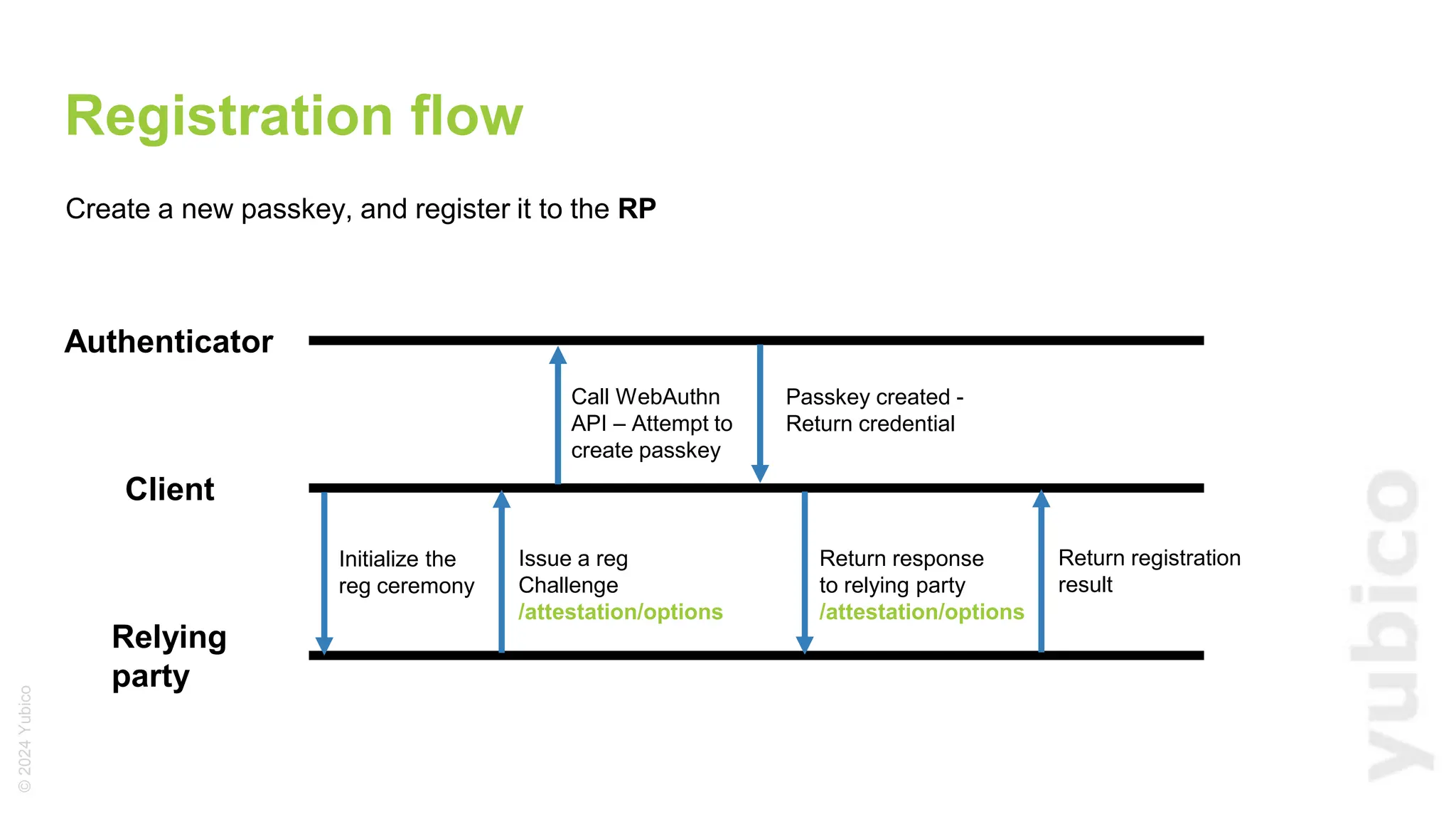
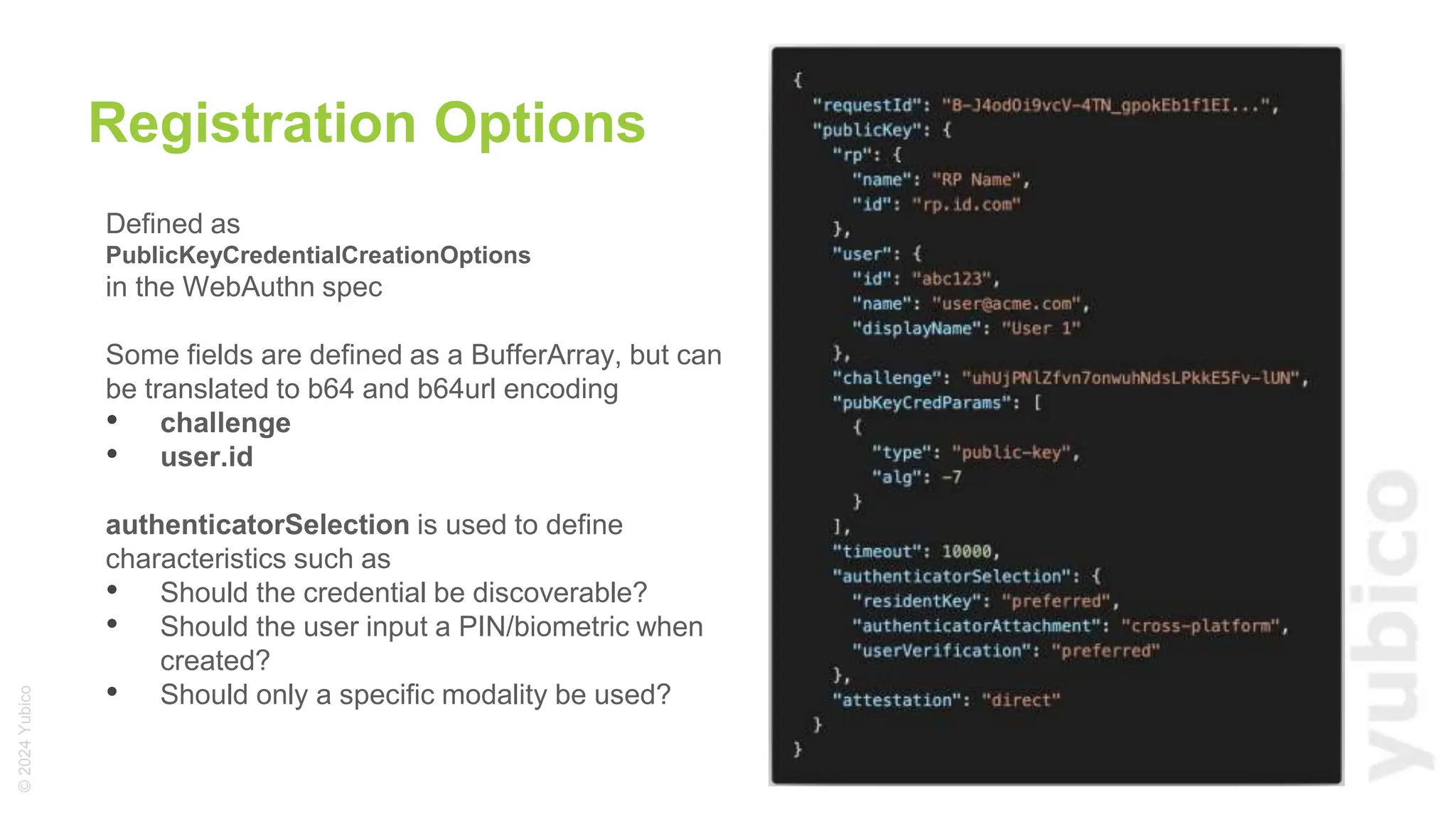
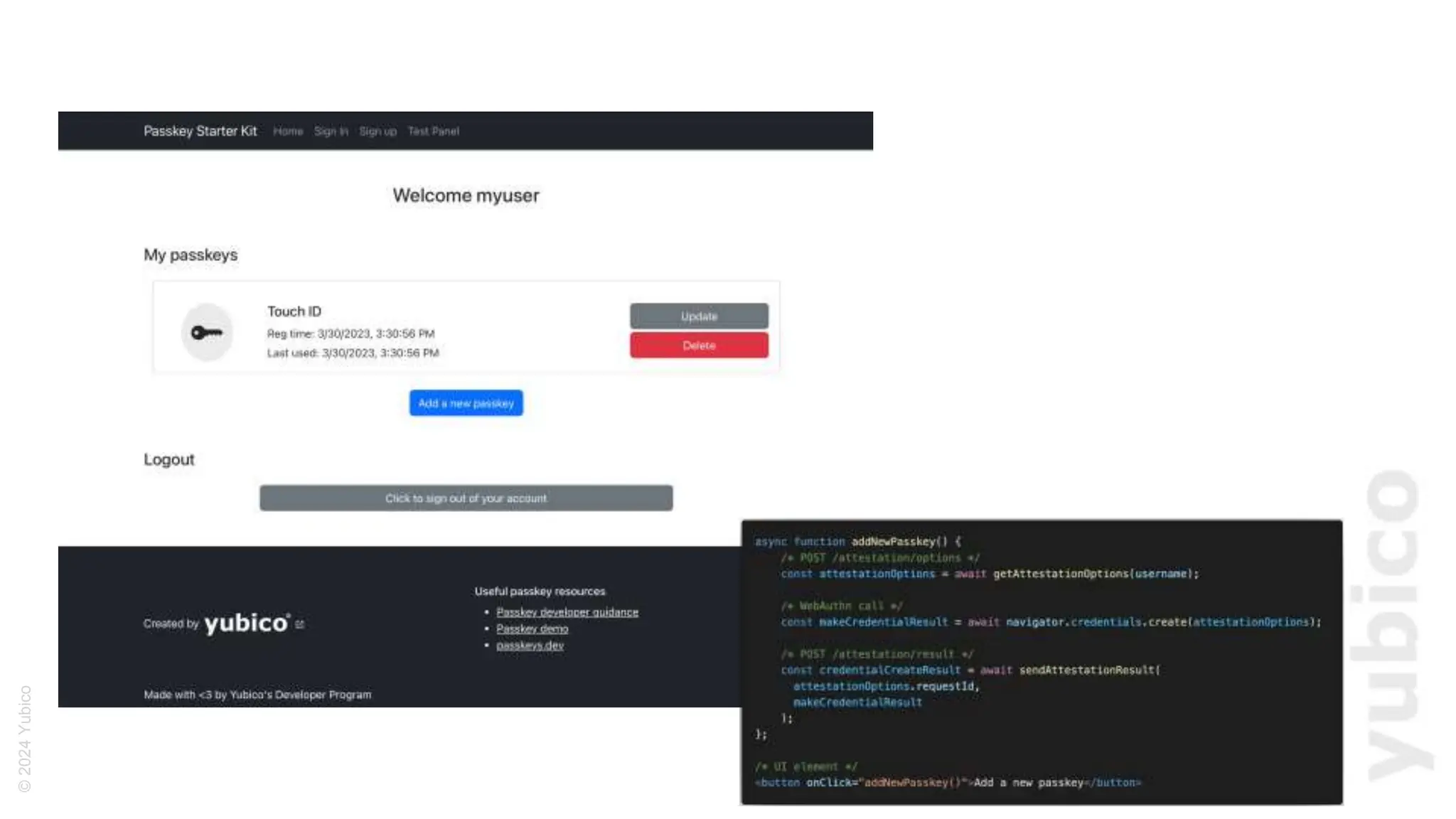
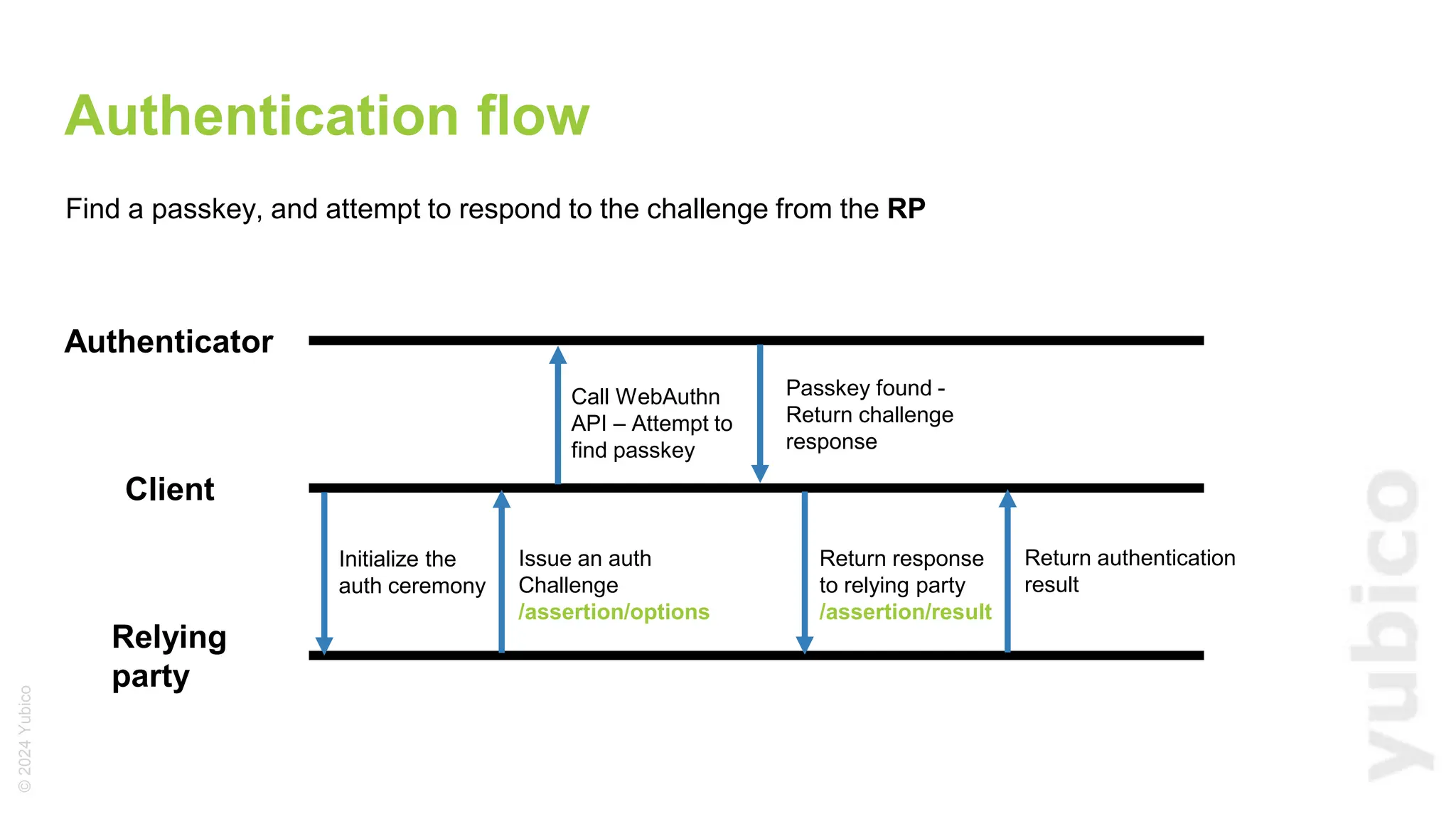
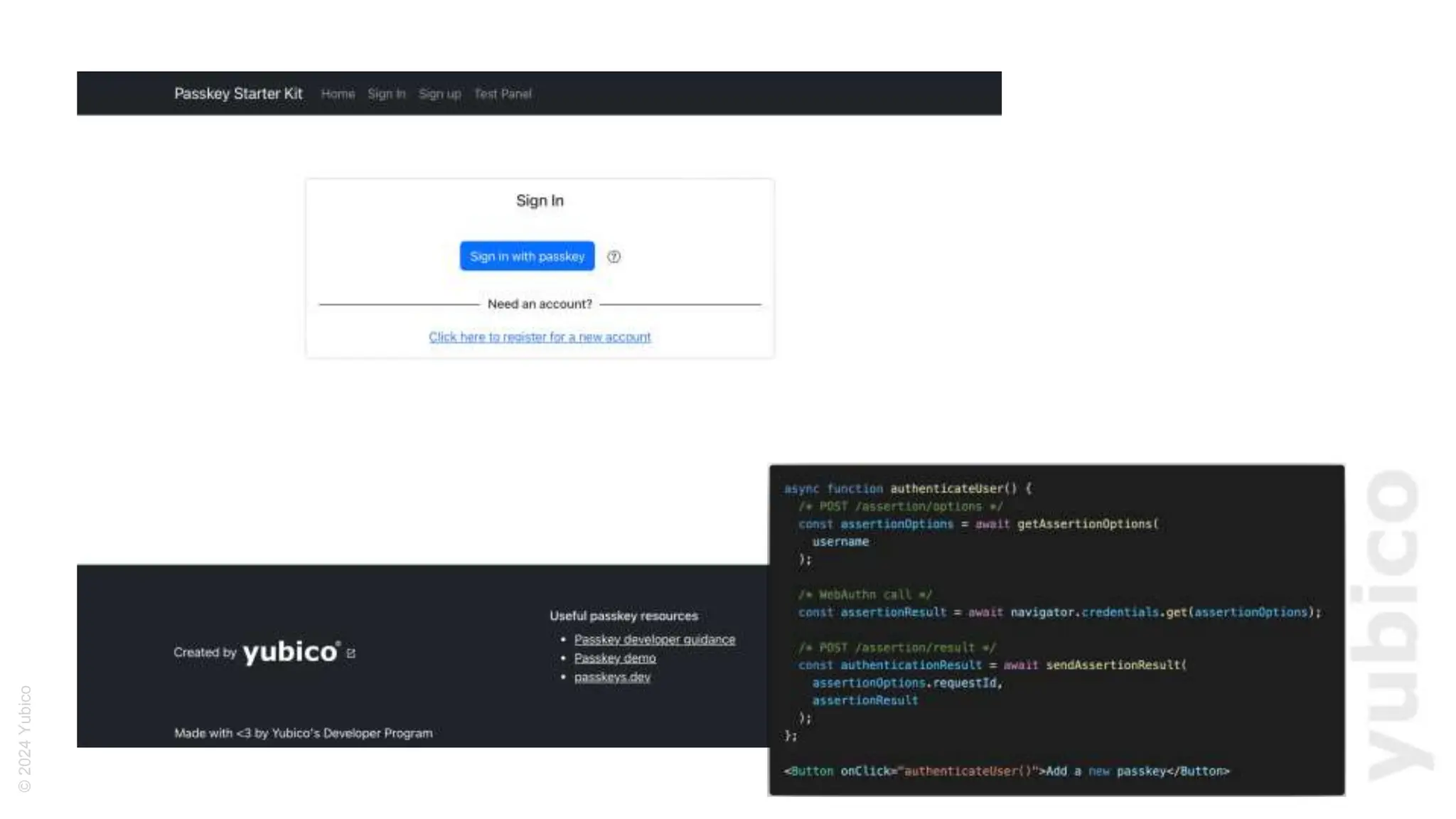
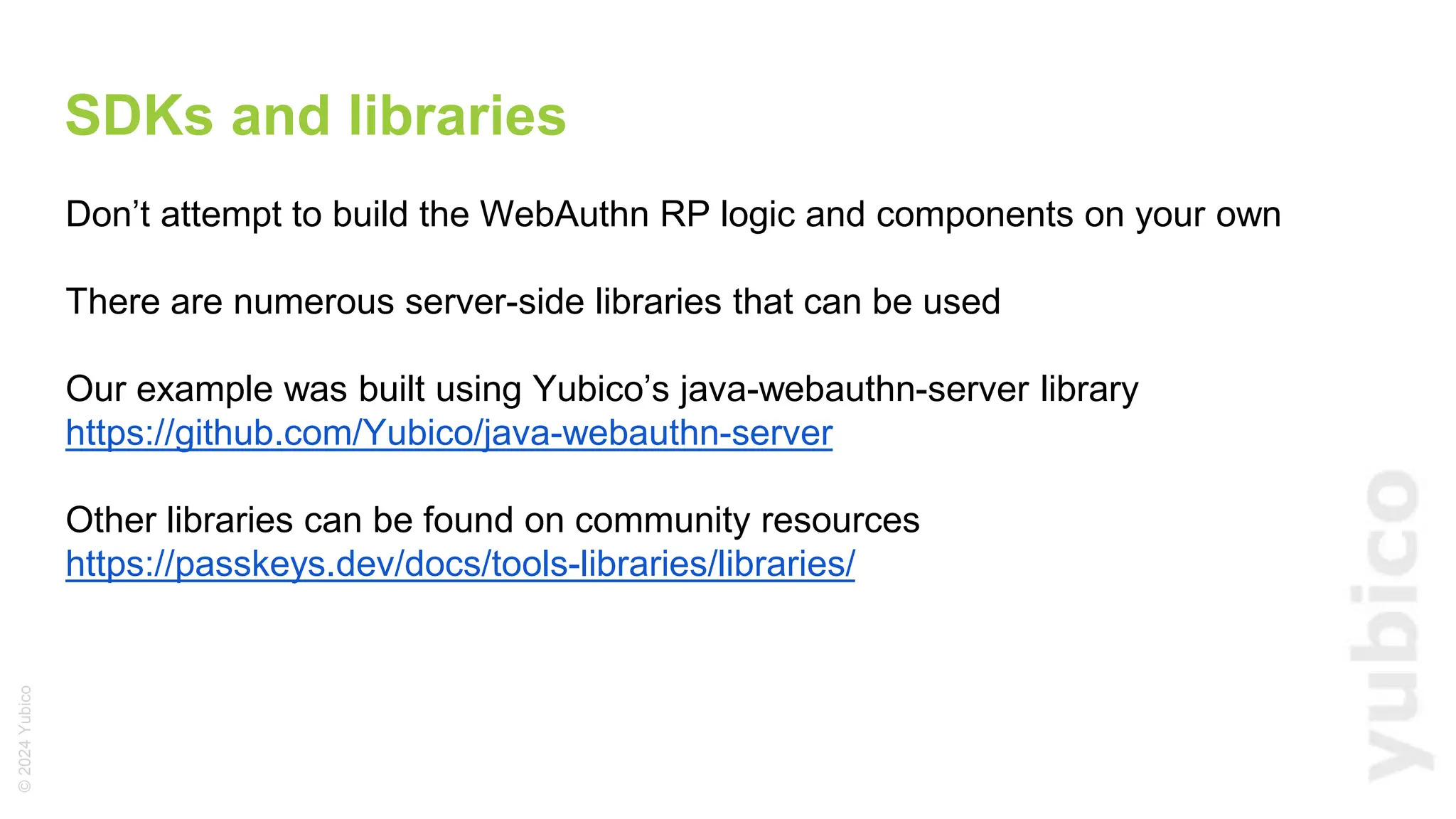
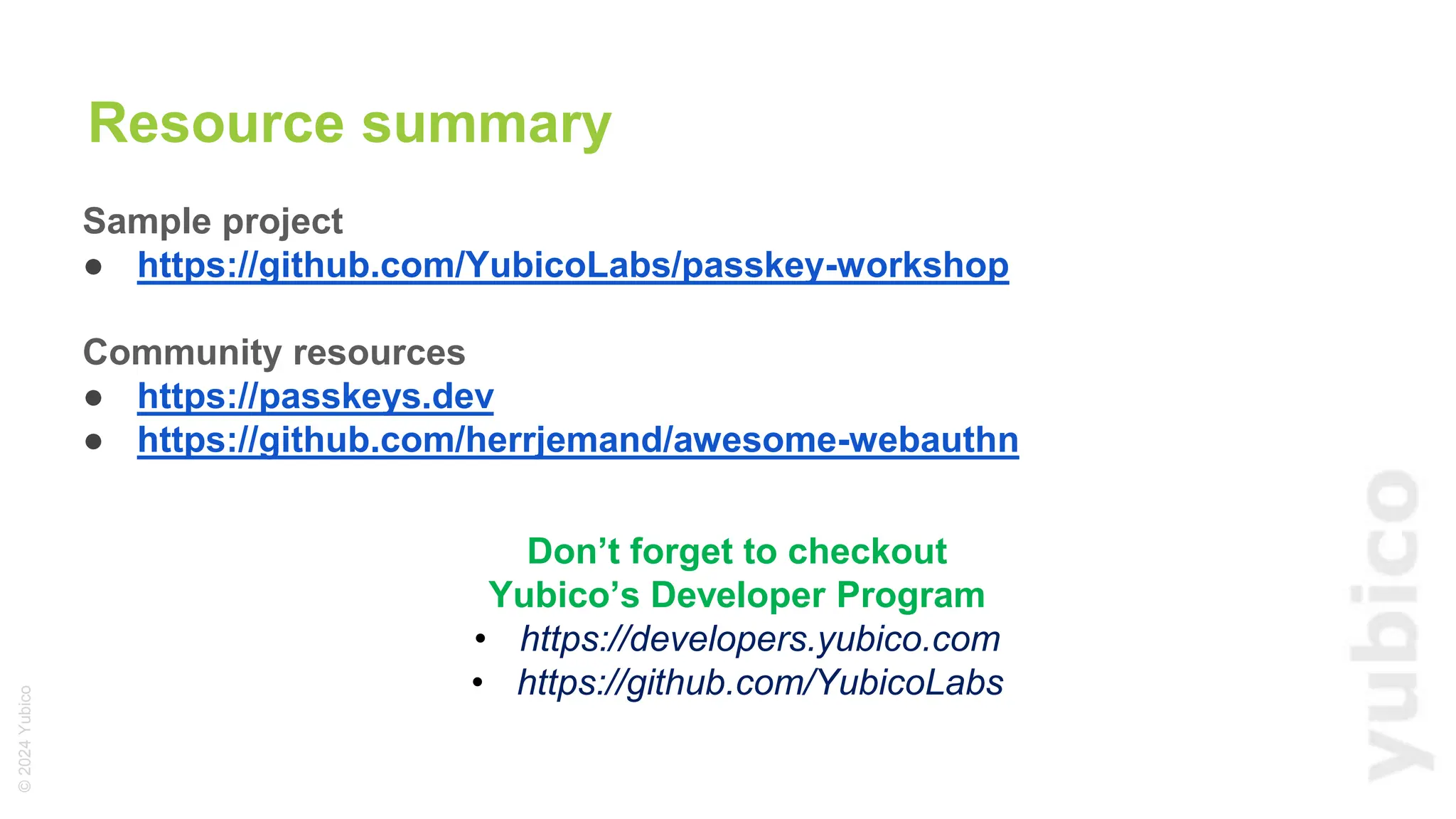
The document discusses passkeys as a secure alternative to traditional passwords, highlighting their cryptographic nature and phishing resistance. It explains the components of passkeys, including key pairs and the FIDO2 standard, as well as the roles of relying parties and the authentication process. Additionally, it provides resources for developers on implementing passkey authentication and emphasizes the importance of using established libraries for security.