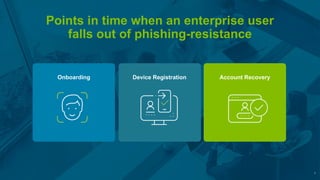
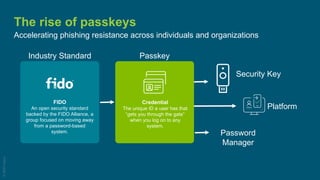
Yubico outlines strategies to accelerate the adoption of passkeys, emphasizing improvements in user experience and security against phishing attacks. The approach includes leveraging existing tools, focusing on user experience, and implementing a phased move towards passwordless systems. Key components involve enhancing the security lifecycle, reducing reliance on traditional measures, and ensuring efficient use of resources to protect sensitive data.