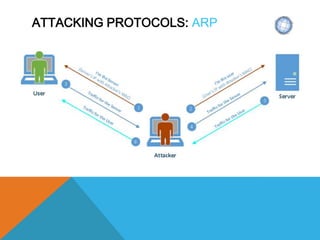
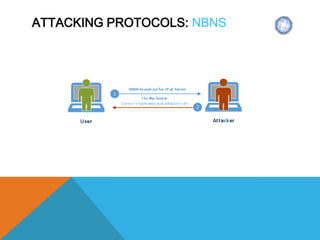
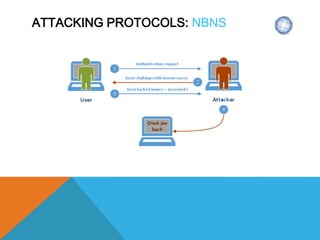
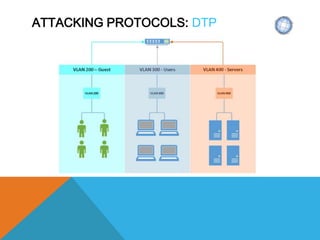
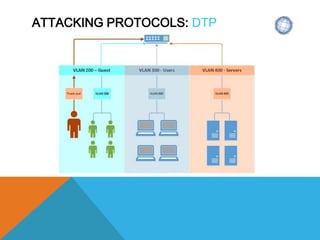
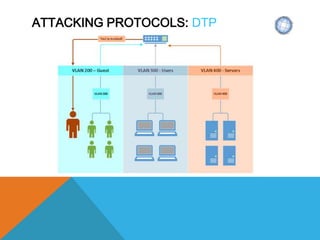
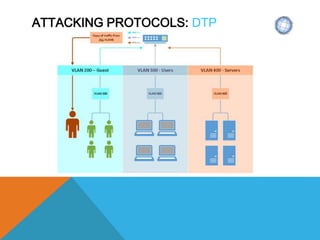
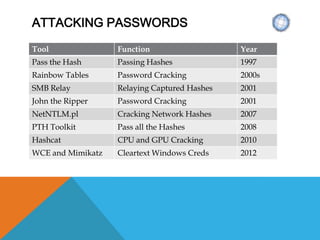
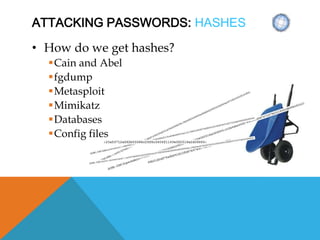
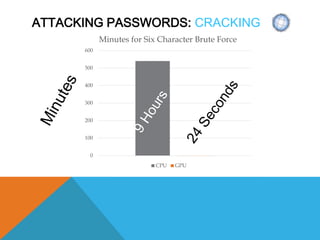
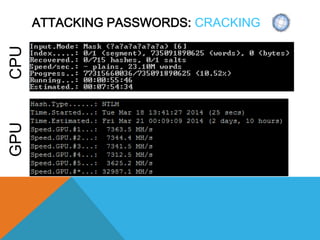
The document presents a comprehensive overview of penetration testing, focusing on the rationale behind it, various attack vectors such as protocols, passwords, and applications, and techniques for bypassing endpoint protection and achieving privilege escalation. It discusses the implications of compliance requirements, risk evaluation, and preventive controls, while detailing common attacks and mitigation strategies associated with protocols like ARP, NBNS, SMB, and DTP. Additionally, it explores password cracking methods, common vulnerabilities in applications, and tactics for bypassing security measures, concluding that many networks and protocols have inherent vulnerabilities.