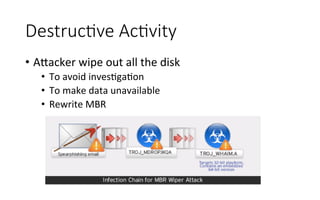
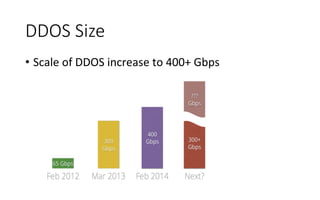
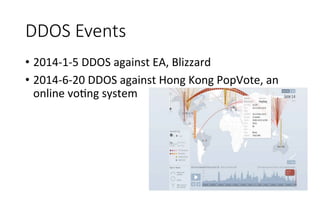
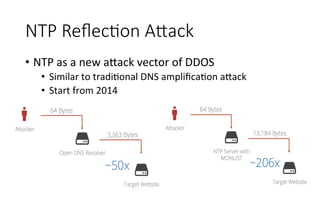
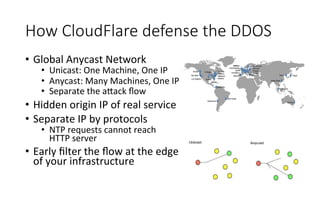
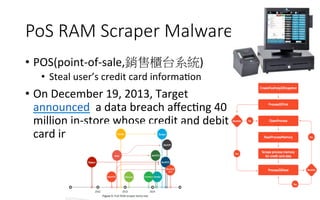
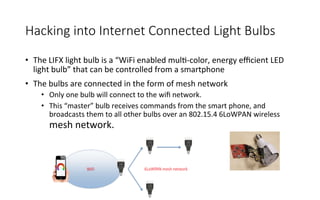
This document summarizes several major security events that occurred in 2014, including large DDOS attacks against gaming companies and a Hong Kong voting system, as well as the discovery of vulnerabilities and malware. The Hong Kong DDOS attack reached 300 Gbps using reflection techniques like NTP amplification and involved a coordinated attack from botnets, floods, and other vectors. The document also discusses growing security issues involving the Internet of Things, including vulnerabilities found in routers and devices like IP cameras that can enable remote access, as well as malware targeting point-of-sale systems and the potential use of IoT devices in botnets.















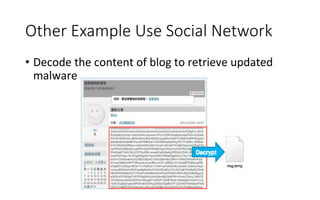
![RTLO obfuscated
• The
malicious
file
is
zipped
with
7z
• RTLO
is
“Right
to
Leg
override”
• xxx.[RTLO]fdp.scr
-‐>
xxx.rcs.pdf
• Ager
executable
trigger,
an
fake
ppt
file
is
dropped
and
displayed.](https://image.slidesharecdn.com/securityeventsin2014-150503114725-conversion-gate01/85/Security-events-in-2014-25-320.jpg)
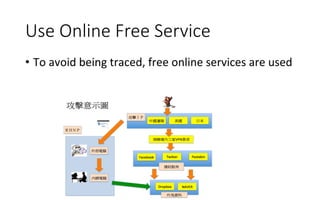
![Use Legal Website for C&C
• Use
legal
website
as
C&C
channel
• h=p://blog.sina.com[.]cn/rss/2050950612.xml](https://image.slidesharecdn.com/securityeventsin2014-150503114725-conversion-gate01/85/Security-events-in-2014-27-320.jpg)