Embed presentation




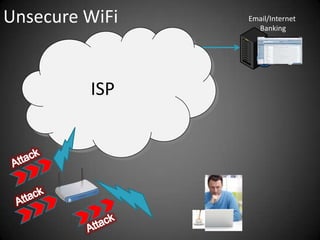
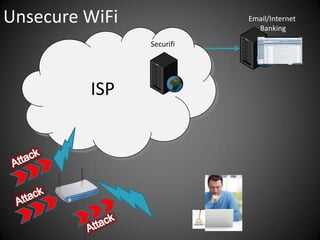
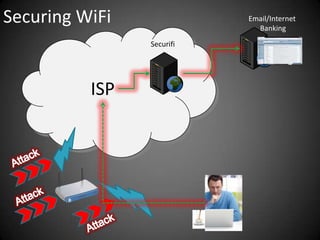
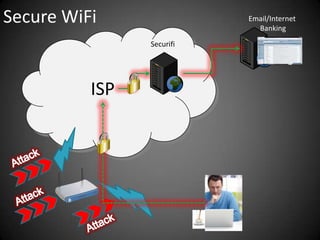

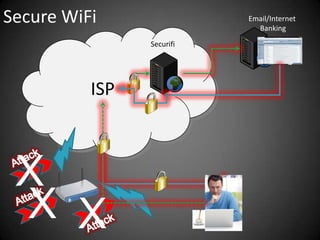
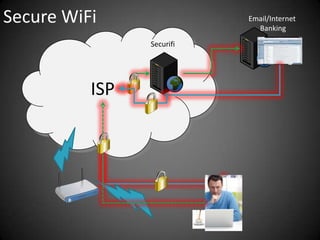







This document discusses the risks of using unsecured WiFi networks and introduces Securifi as a solution. When connecting to open hotspots, a user's data is vulnerable to interception and their security can be compromised. Securifi provides a secure "tunnel" to protect data and allow users to surf with confidence by securing WiFi connections, email, internet banking and preventing attacks. Most people are unaware of the risks and benefits of using Securifi to enhance their internet security.

















