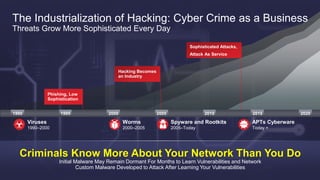
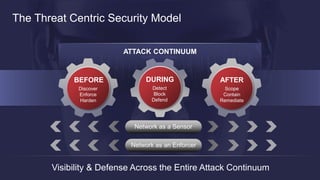
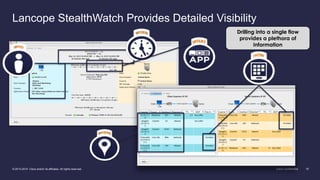
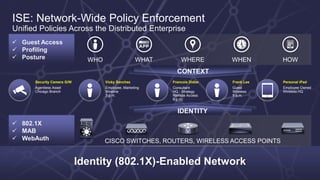
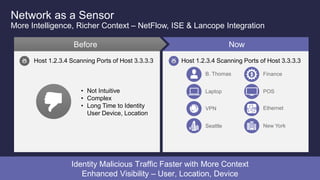
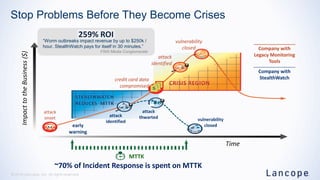
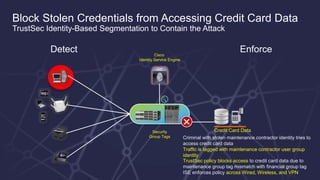
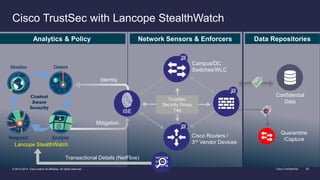
The document discusses the increasing sophistication of cyber threats and the need for a threat-centric security model within enterprise networks. It emphasizes the role of the network as a sensor, enforcer, and mitigation accelerator, highlighting the necessity of detection, segmentation, and rapid response to anomalies and attacks. Cisco's strategic advice focuses on integrating advanced malware protection with security solutions to enhance visibility and control over network traffic and user activity.