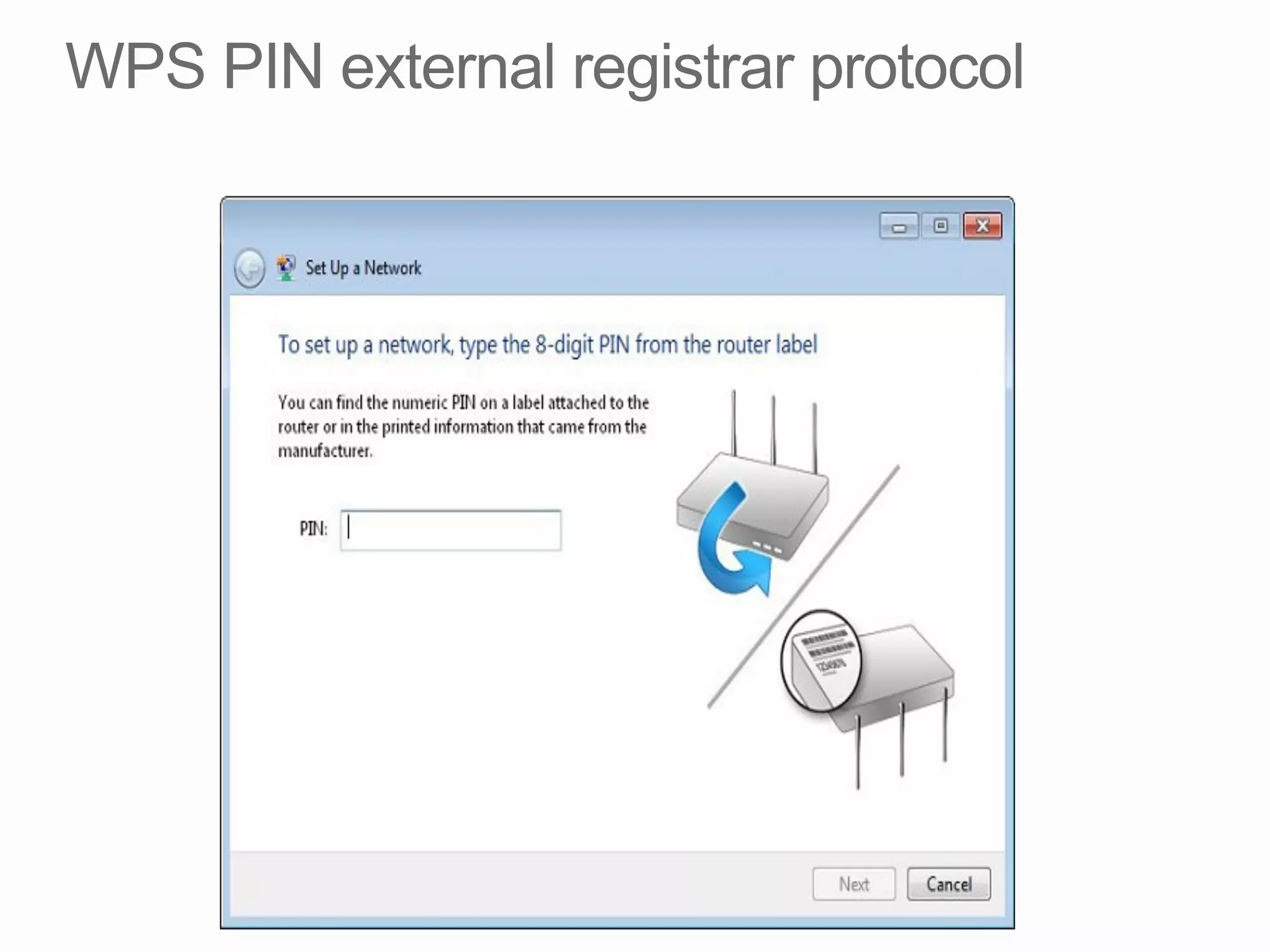
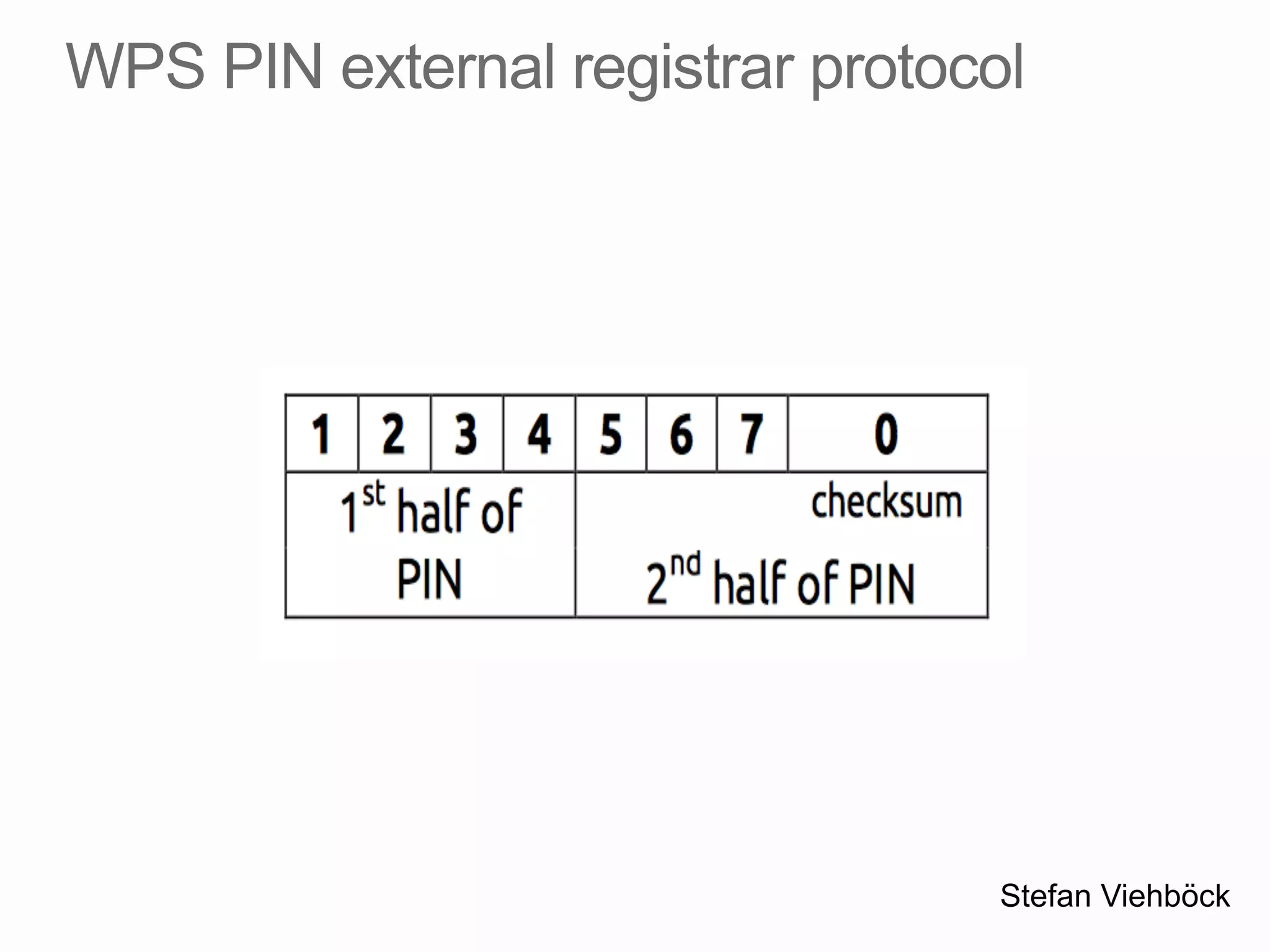
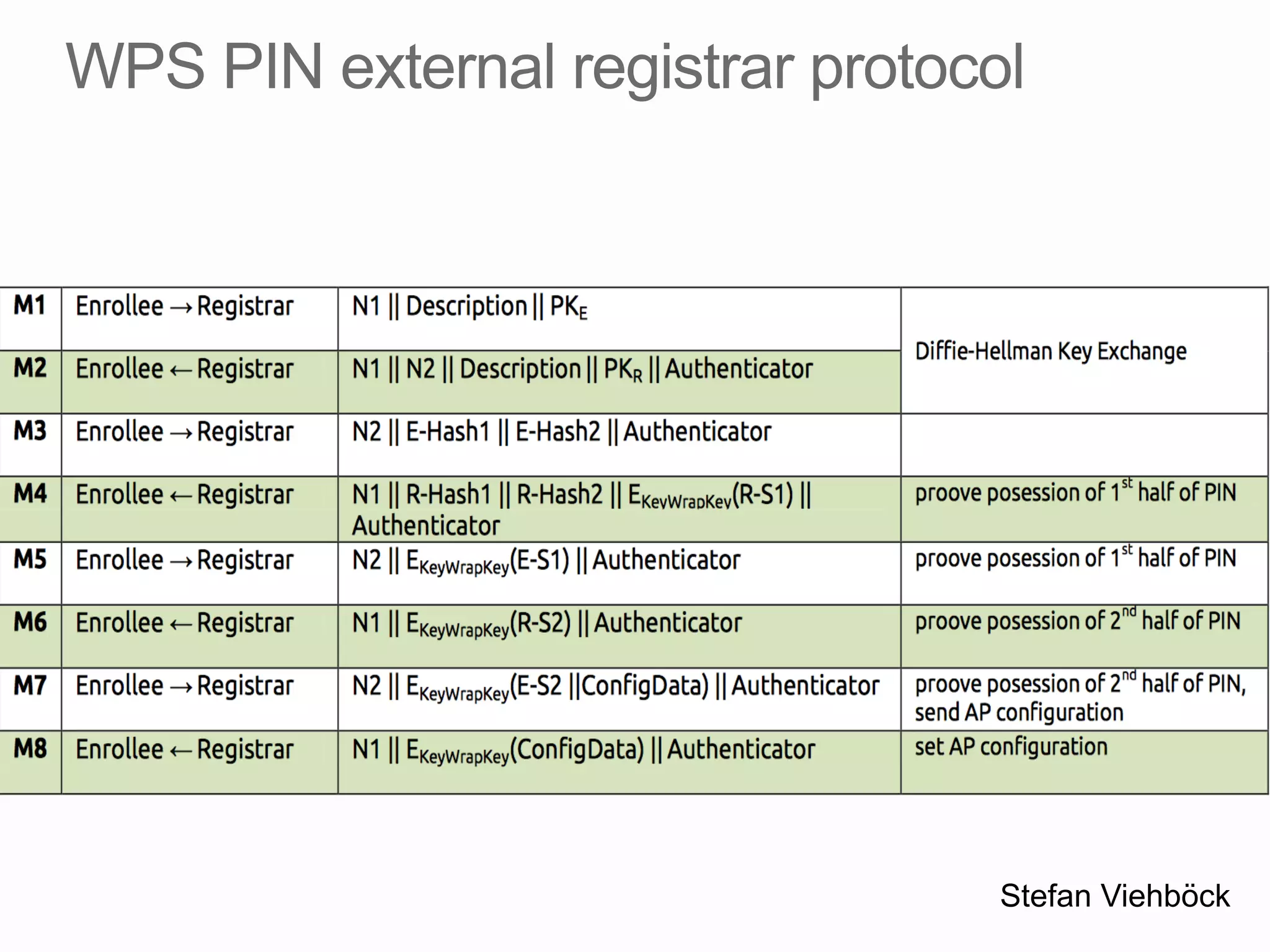
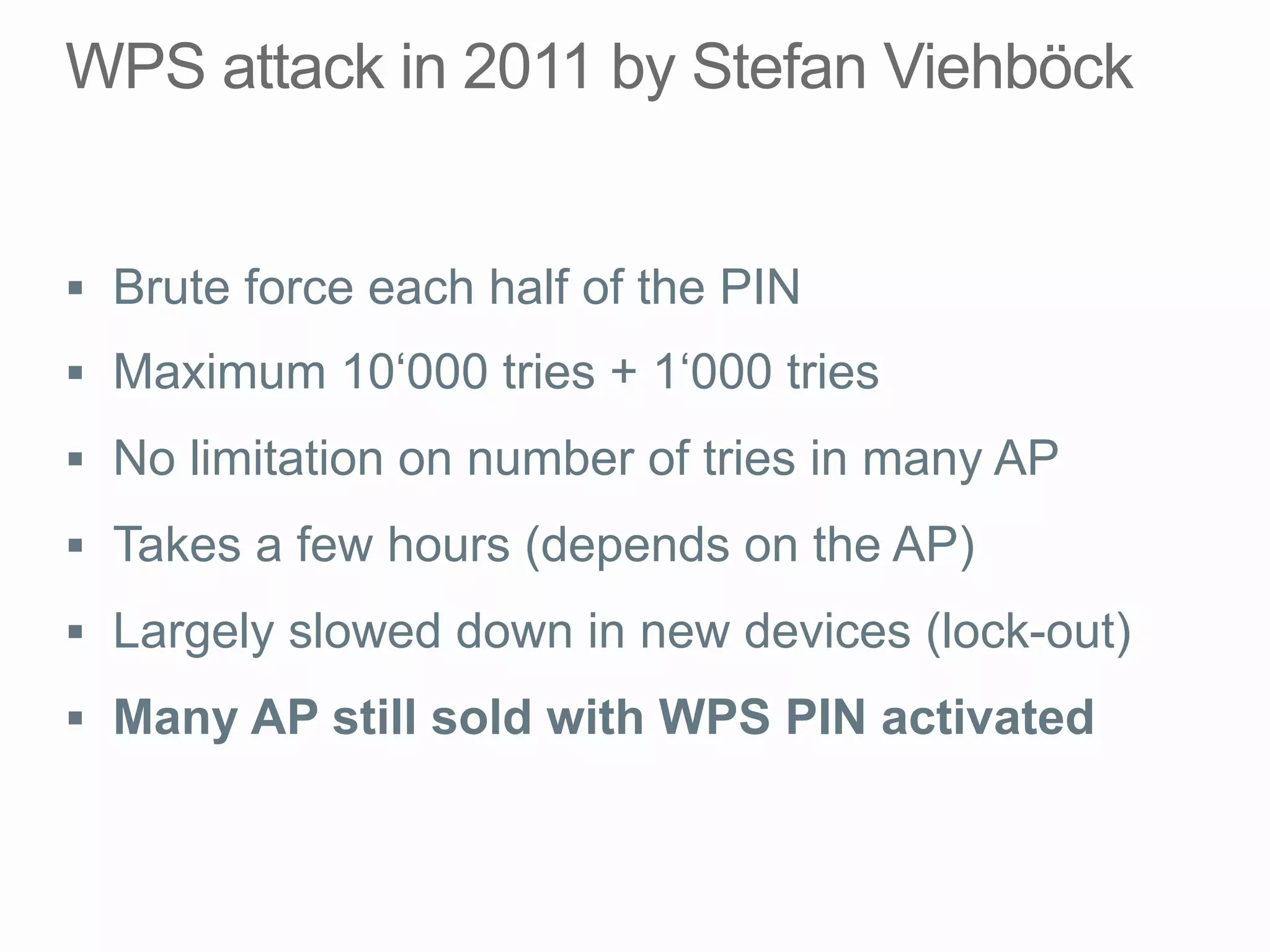
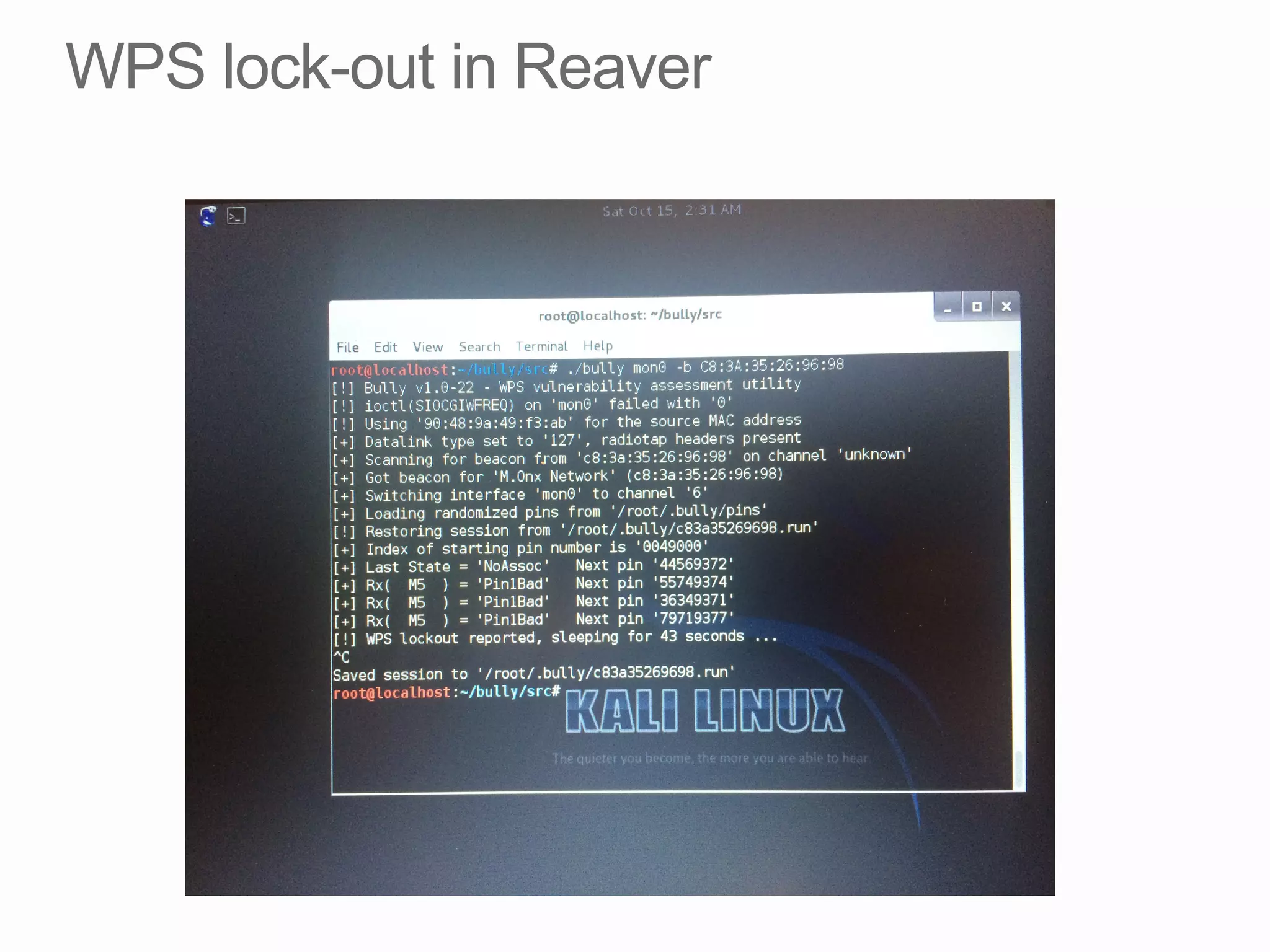
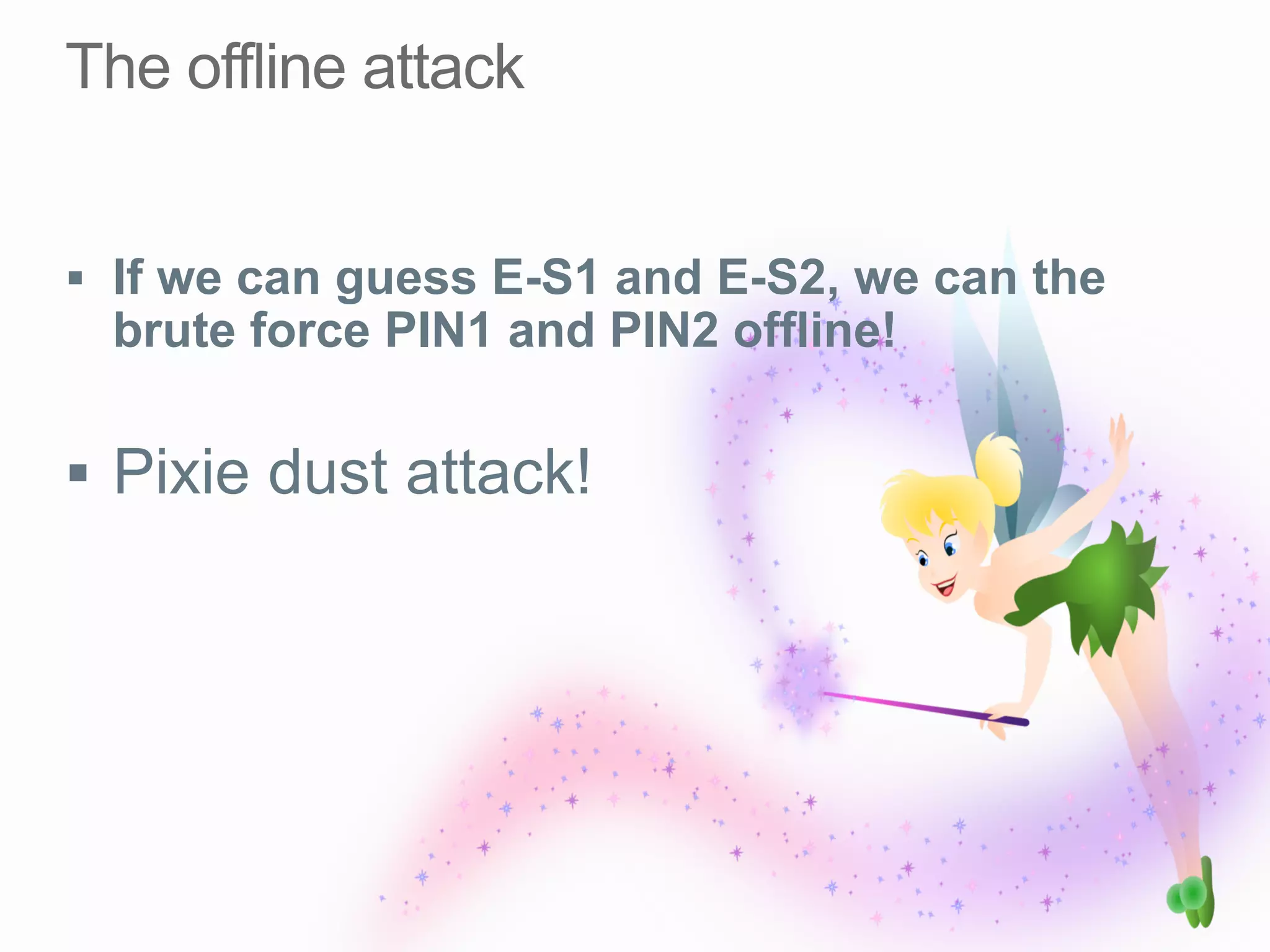
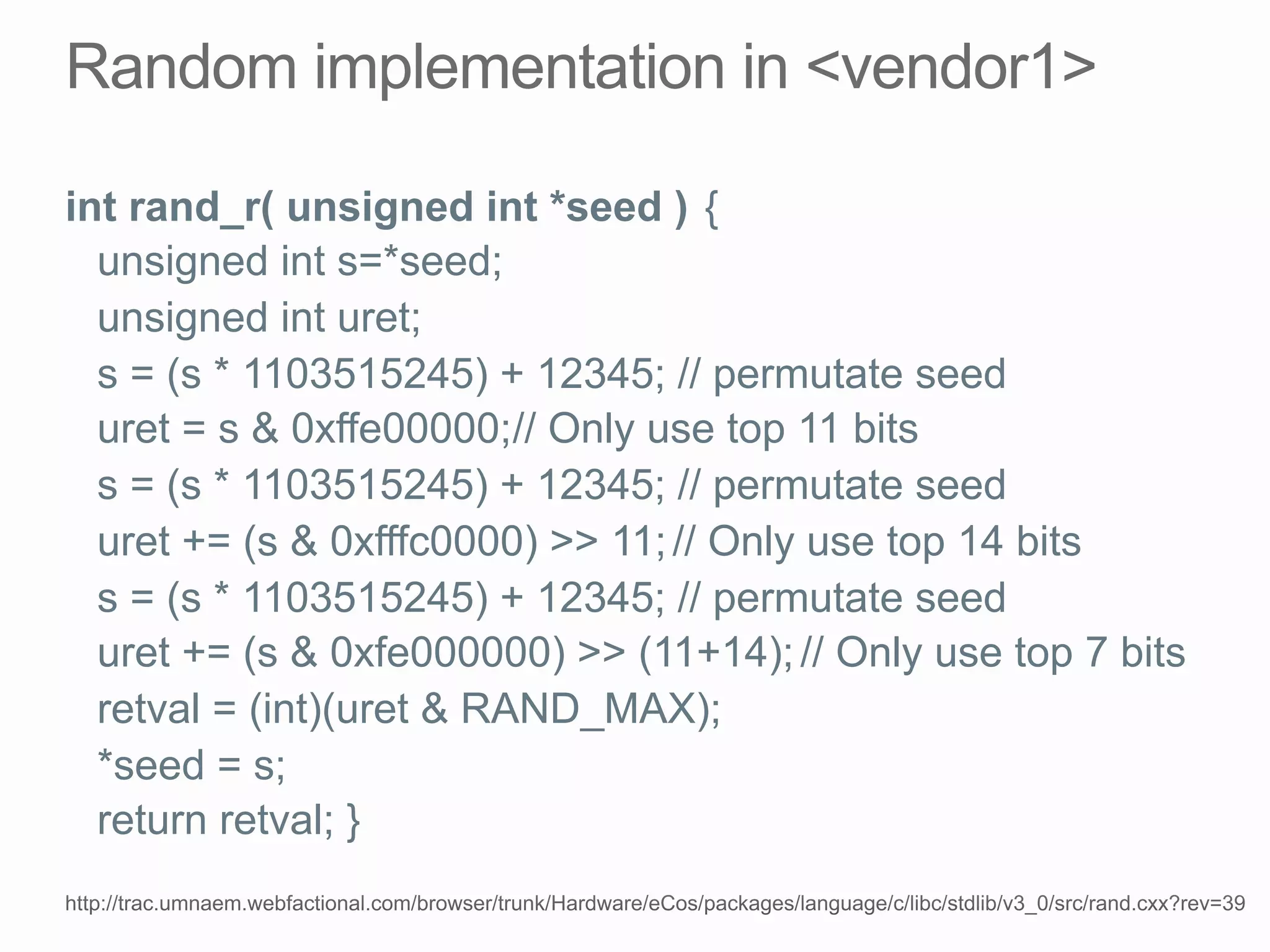
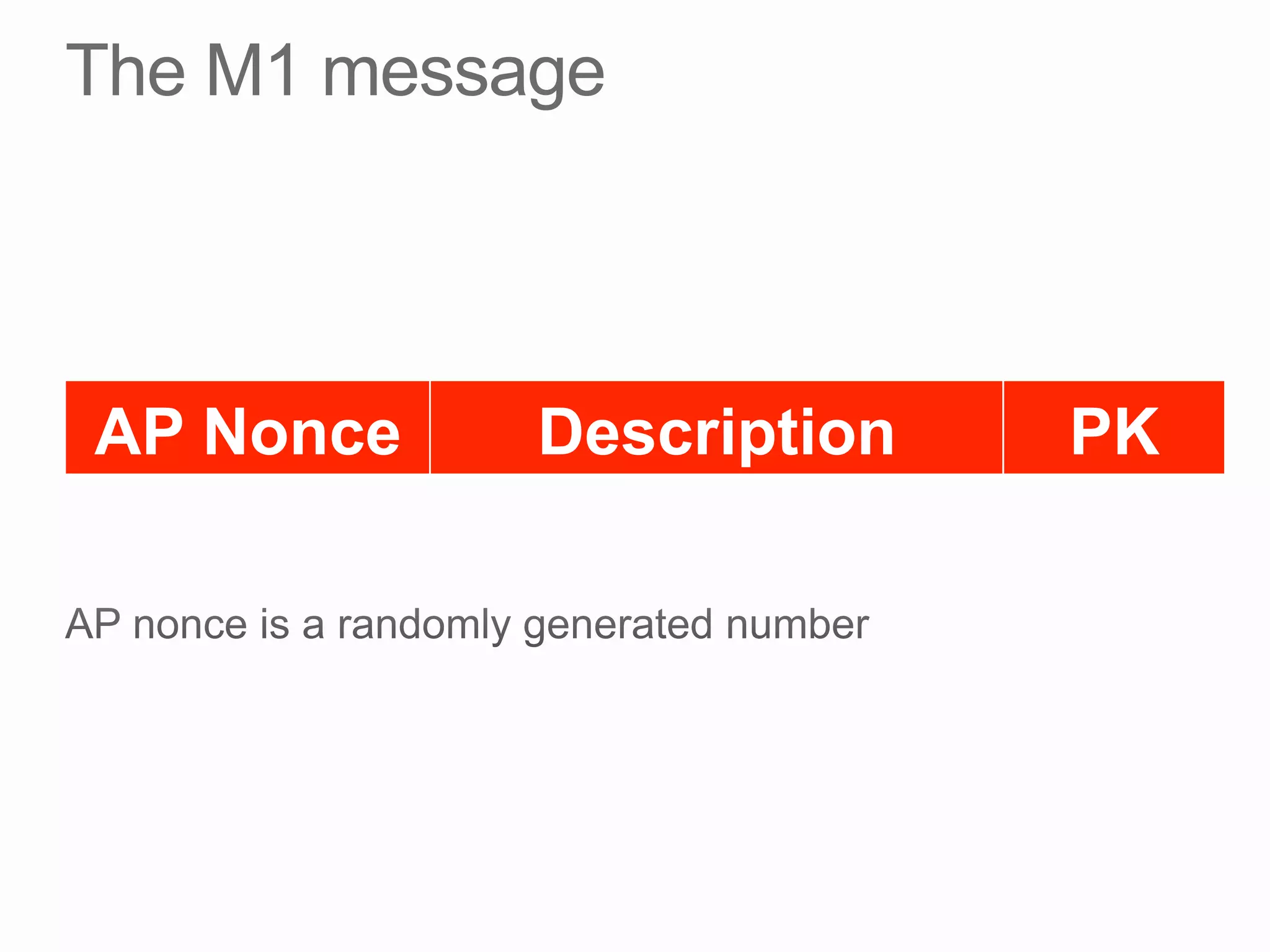
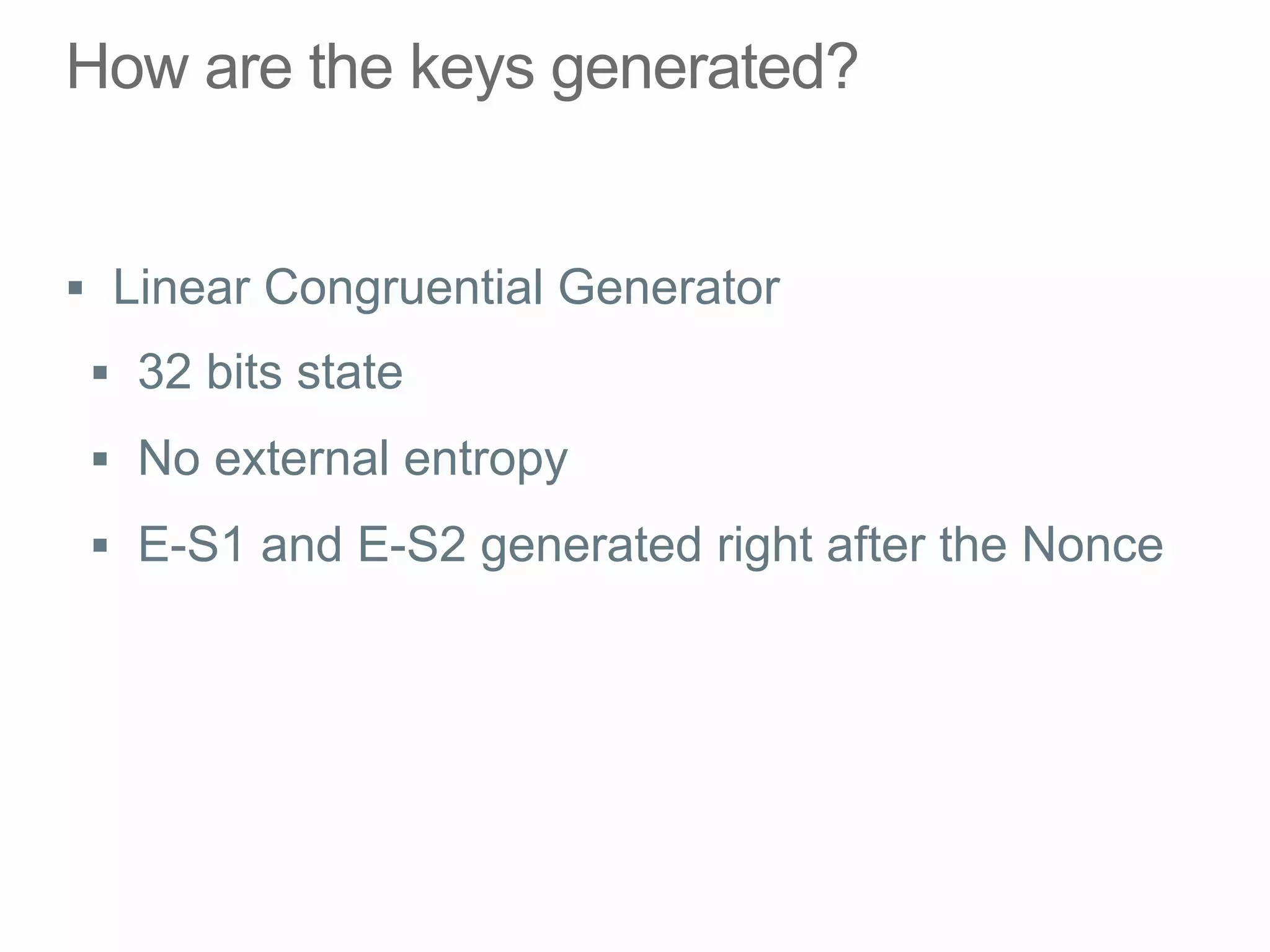
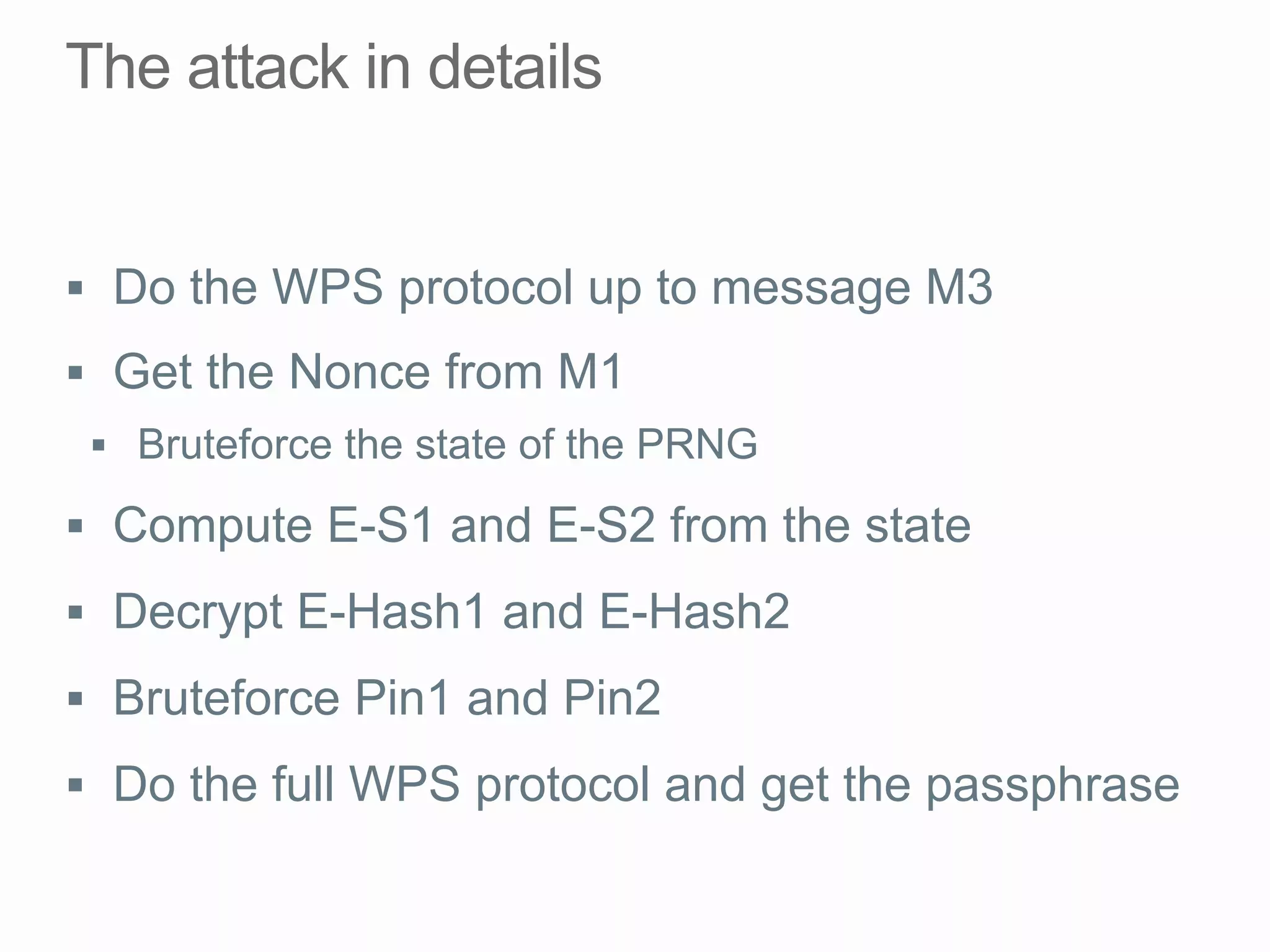
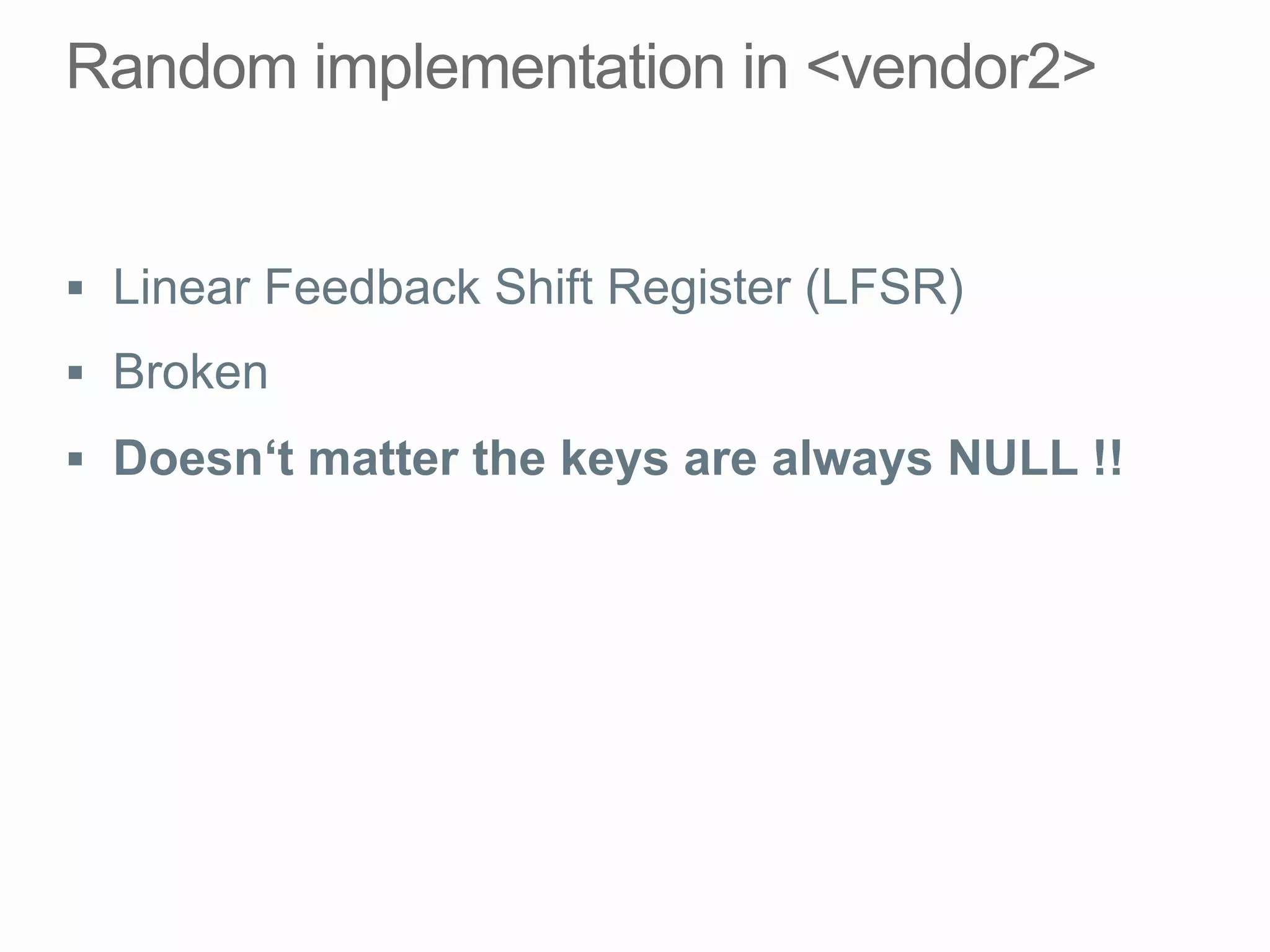
This document discusses offline brute force attacks on WiFi Protected Setup (WPS). It describes how WPS uses an 8-digit PIN code that can be cracked through brute force attacks. It also details the "Pixie Dust" attack method, which recovers the pseudorandom number generator state used by WPS to determine the encryption keys, allowing offline cracking of the PIN and recovery of the WiFi passphrase. The document warns that many access points still have vulnerable WPS implementations and recommends disabling WPS to prevent such attacks.